Exam Code: 156-215.80 (156-215.80 Exam Questions), Exam Name: Check Point Certified Security Administrator, Certification Provider: Certifitcation, Free Today! Guaranteed Training- Pass 156-215.80 Exam.
Free demo questions for 156-215.80 Exam Dumps Below:
NEW QUESTION 1
Study the Rule base and Client Authentication Action properties screen.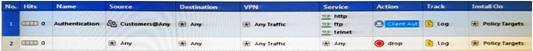
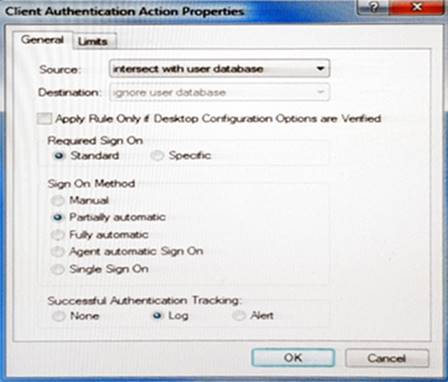
After being authenticated by the Security Gateways, a user starts a HTTP connection to a Web site. What happens when the user tries to FTP to another site using the command line? The:
- A. user is prompted for authentication by the Security Gateways again.
- B. FTP data connection is dropped after the user is authenticated successfully.
- C. user is prompted to authenticate from that FTP site only, and does not need to enter his username and password for Client Authentication
- D. FTP connection is dropped by Rule 2.
Answer: C
NEW QUESTION 2
You have successfully backed up your Check Point configurations without the OS information. What command would you use to restore this backup?
- A. restore_backup
- B. import backup
- C. cp_merge
- D. migrate import
Answer: A
NEW QUESTION 3
Fill in the blank: To build an effective Security Policy, use a _____ and _____ rule.
- A. Cleanup; stealth
- B. Stealth; implicit
- C. Cleanup; default
- D. Implicit; explicit
Answer: A
NEW QUESTION 4
Which repositories are installed on the Security Management Server by SmartUpdate?
- A. License and Update
- B. Package Repository and Licenses
- C. Update and License and Contract
- D. License and Contract and Package Repository
Answer: D
NEW QUESTION 5
Fill in the blank: The ____ collects logs and sends them to the ____.
- A. Log server; security management server
- B. Log server; Security Gateway
- C. Security management server; Security Gateway
- D. Security Gateways; log server
Answer: D
NEW QUESTION 6
Which pre-defined Permission Profile should be assigned to an administrator that requires full access to audit all configurations without modifying them?
- A. Auditor
- B. Read Only All
- C. Super User
- D. Full Access
Answer: B
Explanation: To create a new permission profile:
In SmartConsole, go to Manage & Settings > Permissions and Administrators > Permission Profiles.
Click New Profile.
The New Profile window opens.
Enter a unique name for the profile.
Select a profile type:
Read/Write All - Administrators can make changes
Auditor (Read Only All) - Administrators can see information but cannot make changes
Customized - Configure custom settings
Click OK.
NEW QUESTION 7
In what way are SSL VPN and IPSec VPN different?
- A. SSL VPN is using HTTPS in addition to IKE, whereas IPSec VPN is clientless
- B. SSL VPN adds an extra VPN header to the packet, IPSec VPN does not
- C. IPSec VPN does not support two factor authentication, SSL VPN does support this
- D. IPSec VPN uses an additional virtual adapter, SSL VPN uses the client network adapter only
Answer: D
NEW QUESTION 8
Vanessa is expecting a very important Security Report. The Document should be sent as an attachment via
e-m ail. An e-mail with Security_report.pdf file was delivered to her e-mail inbox. When she opened the PDF file, she noticed that the file is basically empty and only few lines of text are in it. The report is missing some graphs, tables and links. Which component of SandBlast protection is her company using on a Gateway?
- A. SandBlast Threat Emulation
- B. SandBlast Agent
- C. Check Point Protect
- D. SandBlast Threat Extraction
Answer: D
NEW QUESTION 9
What is true about the IPS-Blade?
- A. in R80, IPS is managed by the Threat Prevention Policy
- B. in R80, in the IPS Layer, the only three possible actions are Basic, Optimized and Strict
- C. in R80, IPS Exceptions cannot be attached to “all rules”
- D. in R80, the GeoPolicy Exceptions and the Threat Prevention Exceptions are the same
Answer: A
NEW QUESTION 10
Which of the following statements is TRUE about R80 management plug-ins?
- A. The plug-in is a package installed on the Security Gateway.
- B. Installing a management plug-in requires a Snapshot, just like any upgrade process.
- C. A management plug-in interacts with a Security Management Server to provide new features and support for new products.
- D. Using a plug-in offers full central management only if special licensing is applied to specific features of the plug-in.
Answer: C
NEW QUESTION 11
Fill in the blanks: The Application Layer Firewalls inspect traffic through the ____ layer(s) of the TCP/IP model and up to and including the ____ layer.
- A. Lower; Application
- B. First two; Internet
- C. First two; Transport
- D. Upper; Application
Answer: A
NEW QUESTION 12
Where does the security administrator activate Identity Awareness within SmartDashboard?
- A. Gateway Object > General Properties
- B. Security Management Server > Identity Awareness
- C. Policy > Global Properties > Identity Awareness
- D. LDAP Server Object > General Properties
Answer: A
NEW QUESTION 13
Vanessa is firewall administrator in her company; her company is using Check Point firewalls on central and remote locations, which are managed centrally by R80 Security Management Server. One central location has an installed R77.30 Gateway on Open server. Remote location is using Check Point UTM-1 570 series appliance with R71. Which encryption is used in Secure Internal Communication (SIC) between central management and firewall on each location?
- A. On central firewall AES128 encryption is used for SIC, on Remote firewall 3DES encryption is used for SIC.
- B. On both firewalls, the same encryption is used for SI
- C. This is AES-GCM-256.
- D. The Firewall Administrator can choose which encryption suite will be used by SIC.
- E. On central firewall AES256 encryption is used for SIC, on Remote firewall AES128 encryption is used for SIC.
Answer: A
Explanation: Gateways above R71 use AES128 for SIC. If one of the gateways is R71 or below, the gateways use 3DES.
NEW QUESTION 14
What are the three authentication methods for SIC?
- A. Passwords, Users, and standards-based SSL for the creation of security channels
- B. Certificates, standards-based SSL for the creation of secure channels, and 3DES or AES128 for encryption
- C. Packet Filtering, certificates, and 3DES or AES128 for encryption
- D. Certificates, Passwords, and Tokens
Answer: B
Explanation: Secure Internal Communication (SIC)
Secure Internal Communication (SIC) lets Check Point platforms and products authenticate with each other. The SIC procedure creates a trusted status between gateways, management servers and other Check Point components. SIC is required to install polices on gateways and to send logs between gateways and management servers.
These security measures make sure of the safety of SIC:
Certificates for authentication
Standards-based SSL for the creation of the secure channel
3DES for encryption
References:
NEW QUESTION 15
DLP and Geo Policy are examples of what type of Policy?
- A. Standard Policies
- B. Shared Policies
- C. Inspection Policies
- D. Unified Policies
Answer: B
Explanation: The Shared policies are installed with the Access Control Policy.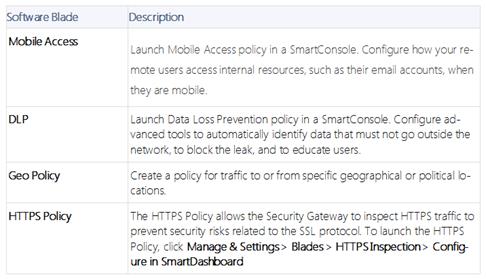
NEW QUESTION 16
SandBlast offers flexibility in implementation based on their individual business needs. What is an option for deployment of Check Point SandBlast Zero-Day Protection?
- A. Smart Cloud Services
- B. Load Sharing Mode Services
- C. Threat Agent Solution
- D. Public Cloud Services
Answer: A
NEW QUESTION 17
What will be the effect of running the following command on the Security Management Server?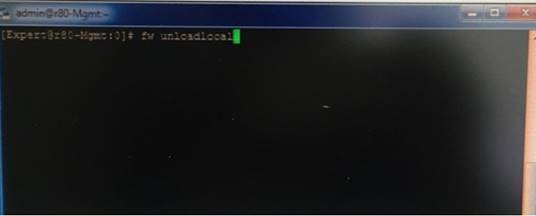
- A. Remove the installed Security Policy.
- B. Remove the local ACL lists.
- C. No effect.
- D. Reset SIC on all gateways.
Answer: A
Explanation: This command uninstall actual security policy (already installed) References:
NEW QUESTION 18
What is the purpose of Captive Portal?
- A. It provides remote access to SmartConsole
- B. It manages user permission in SmartConsole
- C. It authenticates users, allowing them access to the Internet and corporate resources
- D. It authenticates users, allowing them access to the Gaia OS
Answer: C
Explanation: Captive Portal – a simple method that authenticates users through a web interface before granting them access to Intranet resources. When users try to access a protected resource, they get a web page that
must be filled out to continue.
Reference : https://www.checkpoint.com/products/identity-awareness-software-blade/
Recommend!! Get the Full 156-215.80 dumps in VCE and PDF From Surepassexam, Welcome to Download: https://www.surepassexam.com/156-215.80-exam-dumps.html (New 440 Q&As Version)
