We provide 156-215.80 Exam Questions and Answers in two formats. Download PDF & Practice Tests. Pass 156-215.80 Exam quickly & easily. The 156-215.80 PDF type is available for reading and printing. You can print more and practice many times. With the help of our 156-215.80 Study Guides product and material, you can easily pass the 156-215.80 exam.
Online 156-215.80 free questions and answers of New Version:
NEW QUESTION 1
What are the three essential components of the Check Point Security Management Architecture?
- A. SmartConsole, Security Management Server, Security Gateway
- B. SmartConsole, SmartUpdate, Security Gateway
- C. Security Management Server, Security Gateway, Command Line Interface
- D. WebUI, SmartConsole, Security Gateway
Answer: A
Explanation: Standalone deployment - Security Gateway and the Security Management server are installed on the same machine.
Distributed deployment - Security Gateway and the Security Management server are installed on different machines.
Deployments
Basic deployments: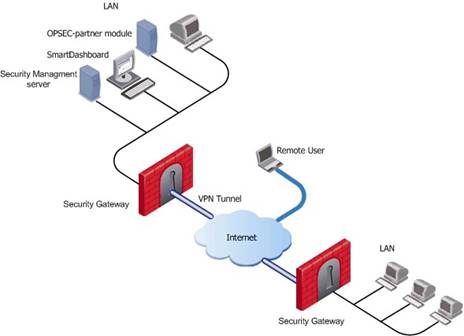
Assume an environment with gateways on different sites. Each Security Gateway connects to the Internet on one side, and to a LAN on the other.
You can create a Virtual Private Network (VPN) between the two Security Gateways, to secure all communication between them.
The Security Management server is installed in the LAN, and is protected by a Security Gateway. The Security Management server manages the Security Gateways and lets remote users connect securely to the corporate network. SmartDashboard can be installed on the Security Management server or another computer.
There can be other OPSEC-partner modules (for example, an Anti-Virus Server) to complete the network security with the Security Management server and its Security Gateways.
NEW QUESTION 2
How would you determine the software version from the CLI?
- A. fw ver
- B. fw stat
- C. fw monitor
- D. cpinfo
Answer: A
NEW QUESTION 3
Which Check Point software blade prevents malicious files from entering a network using virus signatures and anomaly-based protections from ThreatCloud?
- A. Firewall
- B. Application Control
- C. Anti-spam and Email Security
- D. Antivirus
Answer: D
Explanation: The enhanced Check Point Antivirus Software Blade uses real-time virus signatures and anomaly-based protections from ThreatCloud™, the first collaborative network to fight cybercrime, to detect and block malware at the gateway before users are affected.
NEW QUESTION 4
Which SmartConsole tab shows logs and detects security threats, providing a centralized display of potential attack patterns from all network devices?
- A. Gateway and Servers
- B. Logs and Monitor
- C. Manage Seeting
- D. Security Policies
Answer: B
NEW QUESTION 5
Joey wants to configure NTP on R80 Security Management Server. He decided to do this via WebUI. What is the correct address to access the Web UI for Gaia platform via browser?
- A. https://<Device_IP_Address>
- B. https://<Device_IP_Address>:443
- C. https://<Device_IP_Address>:10000
- D. https://<Device_IP_Address>:4434
Answer: A
Explanation: Access to Web UI Gaia administration interface, initiate a connection from a browser to the default administration IP address: Logging in to the WebUI
Logging in
To log in to the WebUI:
Enter this URL in your browser: https://<Gaia IP address>
Enter your user name and password. References:
NEW QUESTION 6
MyCorp has the following NAT rules. You need to disable the NAT function when Alpha-internal networks try to reach the Google DNS (8.8.8.8) server.
What can you do in this case?
- A. Use manual NAT rule to make an exception
- B. Use the NAT settings in the Global Properties
- C. Disable NAT inside the VPN community
- D. Use network exception in the Alpha-internal network object
Answer: D
NEW QUESTION 7
Which of these components does NOT require a Security Gateway R77 license?
- A. Security Management Server
- B. Check Point Gateway
- C. SmartConsole
- D. SmartUpdate upgrading/patching
Answer: C
NEW QUESTION 8
After the initial installation the First Time Configuration Wizard should be run. Select the BEST answer.
- A. First Time Configuration Wizard can be run from the Unified SmartConsole.
- B. First Time Configuration Wizard can be run from the command line or from the WebUI.
- C. First time Configuration Wizard can only be run from the WebUI.
- D. Connection to the internet is required before running the First Time Configuration wizard.
Answer: B
Explanation: Check Point Security Gateway and Check Point Security Management require running the First Time Configuration Wizard in order to be configured correctly. The First Time Configuration Wizard is available in Gaia Portal and also through CLI.
To invoke the First Time Configuration Wizard through CLI, run the config_system command from the Exp shell.
NEW QUESTION 9
Fill in the blank: RADIUS Accounting gets _____ data from requests generated by the accounting client
- A. Destination
- B. Identity
- C. Payload
- D. Location
Answer: B
Explanation: How RADIUS Accounting Works with Identity Awareness
RADIUS Accounting gets identity data from RADIUS Accounting Requests generated by the RADIUS accounting client.
NEW QUESTION 10
True or False: In R80, more than one administrator can login to the Security Management Server with write permission at the same time.
- A. False, this feature has to be enabled in the Global Properties.
- B. True, every administrator works in a session that is independent of the other administrators.
- C. True, every administrator works on a different database that is independent of the other administrators.
- D. False, only one administrator can login with write permission.
Answer: B
Explanation: More than one administrator can connect to the Security Management Server at the same time. Every administrator has their own username, and works in a session that is independent of the other administrators.
NEW QUESTION 11
Which of the following methods can be used to update the trusted log server regarding the policy and configuration changes performed on the Security Management Server?
- A. Save Policy
- B. install Database
- C. Save Session
- D. install Policy
Answer: D
NEW QUESTION 12
Which of the following is a hash algorithm?
- A. 3DES
- B. IDEA
- C. DES
- D. MD5
Answer: D
NEW QUESTION 13
Which authentication scheme requires a user to possess a token?
- A. TACACS
- B. SecurID
- C. Check Point password
- D. RADIUS
Answer: B
Explanation: SecurID
SecurID requires users to both possess a token authenticator and to supply a PIN or password References:
NEW QUESTION 14
Which of the following is NOT an advantage to using multiple LDAP servers?
- A. You achieve a faster access time by placing LDAP servers containing the database at remote sites
- B. Information on a user is hidden, yet distributed across several servers
- C. You achieve compartmentalization by allowing a large number of users to be distributed across several servers
- D. You gain High Availability by replicating the same information on several servers
Answer: B
NEW QUESTION 15
Which of the following is NOT a valid deployment option for R80?
- A. All-in-one (stand-alone)
- B. Log Server
- C. SmartEvent
- D. Multi-domain management server
Answer: D
NEW QUESTION 16
In R80 Management, apart from using SmartConsole, objects or rules can also be modified using:
- A. 3rd Party integration of CLI and API for Gateways prior to R80.
- B. A complete CLI and API interface using SSH and custom CPCode integration.
- C. 3rd Party integration of CLI and API for Management prior to R80.
- D. A complete CLI and API interface for Management with 3rd Party integration.
Answer: B
NEW QUESTION 17
You work as a security administrator for a large company. CSO of your company has attended a security conference where he has learnt how hackers constantly modify their strategies and techniques to evade detection and reach corporate resources. He wants to make sure that his company has the right protections in place. Check Point has been selected for the security vendor. Which Check Point products protects BEST against malware and zero-day attacks while ensuring quick delivery of safe content to your users?
- A. IPS and Application Control
- B. IPS, anti-virus and anti-bot
- C. IPS, anti-virus and e-mail security
- D. SandBlast
Answer: D
Explanation: SandBlast Zero-Day Protection
Hackers constantly modify their strategies and techniques to evade detection and reach corporate resources. Zero-day exploit protection from Check Point provides a deeper level of inspection so you can prevent more malware and zero-day attacks, while ensuring quick delivery of safe content to your users.
NEW QUESTION 18
Fill in the blanks: In the Network policy layer, the default action for the Implied last rule is ___ all traffic. However, in the Application Control policy layer, the default action is _____ all traffic.
- A. Accept; redirect
- B. Accept; drop
- C. Redirect; drop
- D. Drop; accept
Answer: D
Recommend!! Get the Full 156-215.80 dumps in VCE and PDF From 2passeasy, Welcome to Download: https://www.2passeasy.com/dumps/156-215.80/ (New 440 Q&As Version)
