156-215.80 Dumps are updated and 156-215.80 Dumps are verified by experts. Once you have completely prepared with our 156-215.80 Dumps you will be ready for the real 156-215.80 exam without a problem. We have 156-215.80 Exam Questions. PASSED 156-215.80 Exam Dumps First attempt! Here What I Did.
Online 156-215.80 free questions and answers of New Version:
NEW QUESTION 1
You want to reset SIC between smberlin and sgosaka.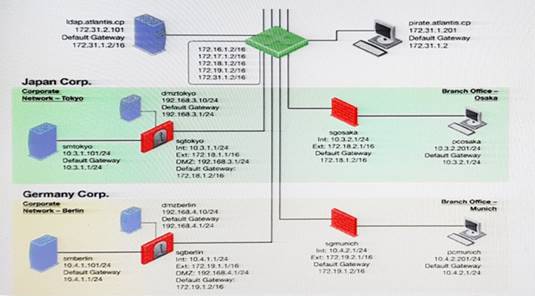
In SmartDashboard, you choose sgosaka, Communication, Reset. On sgosaka, you start cpconfig, choose Secure Internal Communication and enter the new SIC Activation Key. The screen reads The SIC was successfully initialized and jumps back to the menu. When trying to establish a connection, instead of a working connection, you receive this error message: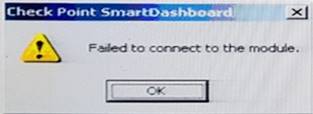
What is the reason for this behavior?
- A. The Gateway was not rebooted, which is necessary to change the SIC key.
- B. You must first initialize the Gateway object in SmartDashboard (i.e., right-click on the object, choose Basic Setup > Initialize).
- C. The check Point services on the Gateway were not restarted because you are still in the cpconfig utility.
- D. The activation key contains letters that are on different keys on localized keyboard
- E. Therefore, the activation can not be typed in a matching fashion.
Answer: C
NEW QUESTION 2
Your boss wants you to closely monitor an employee suspected of transferring company secrets to the competition. The IT department discovered the suspect installed a WinSCP client in order to use encrypted
communication. Which of the following methods is BEST to accomplish this task?
- A. Use SmartView Tracker to follow his actions by filtering log entries that feature the WinSCP destination por
- B. Then, export the corresponding entries to a separate log file for documentation.
- C. Use SmartDashboard to add a rule in the firewall Rule Base that matches his IP address, and those of potential targets and suspicious protocol
- D. Apply the alert action or customized messaging.
- E. Watch his IP in SmartView Monitor by setting an alert action to any packet that matches your Rule Base and his IP address for inbound and outbound traffic.
- F. Send the suspect an email with a keylogging Trojan attached, to get direct information about his wrongdoings.
Answer: A
NEW QUESTION 3
In Logging and Monitoring, the tracking options are Log, Detailed Log and Extended Log. Which of the following options can you add to each Log, Detailed Log and Extended Log?
- A. Accounting
- B. Suppression
- C. Accounting/Suppression
- D. Accounting/Extended
Answer: C
NEW QUESTION 4
Tom has connected to the R80 Management Server remotely using SmartConsole and is in the process of making some Rule Base changes, when he suddenly loses connectivity. Connectivity is restored shortly afterward. What will happen to the changes already made:
- A. Tom’s changes will have been stored on the Management when he reconnects and he will not lose any of this work.
- B. Tom will have to reboot his SmartConsole computer, and access the Management cache store on that computer, which is only accessible after a reboot.
- C. Tom’s changes will be lost since he lost connectivity and he will have to start again.
- D. Tom will have to reboot his SmartConsole computer, clear the cache and restore changes.
Answer: A
NEW QUESTION 5
Which of the following Automatically Generated Rules NAT rules have the lowest implementation priority?
- A. Machine Hide NAT
- B. Address Range Hide NAT
- C. Network Hide NAT
- D. Machine Static NAT
Answer: BC
Explanation: SmartDashboard organizes the automatic NAT rules in this order:
Static NAT rules for Firewall, or node (computer or server) objects
Hide NAT rules for Firewall, or node objects
Static NAT rules for network or address range objects
Hide NAT rules for network or address range objects
References:
NEW QUESTION 6
When doing a Stand-Alone Installation, you would install the Security Management Server with which other Check Point architecture component?
- A. None, Security Management Server would be installed by itself.
- B. SmartConsole
- C. SecureClient
- D. SmartEvent
Answer: D
Explanation: There are different deployment scenarios for Check Point software products.
Standalone Deployment - The Security Management Server and the Security Gateway are installed on the same computer or appliance.
NEW QUESTION 7
Which of the following is an identity acquisition method that allows a Security Gateway to identify Active Directory users and computers?
- A. UserCheck
- B. Active Directory Query
- C. Account Unit Query
- D. User Directory Query
Answer: B
Explanation: AD Query extracts user and computer identity information from the Active Directory Security Event Logs. The system generates a Security Event log entry when a user or computer accesses a network resource. For example, this occurs when a user logs in, unlocks a screen, or accesses a network drive.
Reference : https://sc1.checkpoint.com/documents/R76/CP_R76_IdentityAwareness_AdminGuide/62402.htm
NEW QUESTION 8
When configuring LDAP User Directory integration, Changes applied to a User Directory template are:
- A. Reflected immediately for all users who are using template.
- B. Not reflected for any users unless the local user template is changed.
- C. Reflected for all users who are using that template and if the local user template is changed as well.
- D. Not reflected for any users who are using that template.
Answer: A
Explanation: The users and user groups are arranged on the Account Unit in the tree structure of the LDAP server. User management in User Directory is external, not local. You can change the User Directory templates. Users
associated with this template get the changes immediately. You can change user definitions manually in SmartDashboard, and the changes are immediate on the server.
NEW QUESTION 9
Which of the following is NOT a component of a Distinguished Name?
- A. Organization Unit
- B. Country
- C. Common name
- D. User container
Answer: D
Explanation: Distinguished Name Components
CN=common name, OU=organizational unit, O=organization, L=locality, ST=state or province, C=country name
NEW QUESTION 10
Which message indicates IKE Phase 2 has completed successfully?
- A. Quick Mode Complete
- B. Aggressive Mode Complete
- C. Main Mode Complete
- D. IKE Mode Complete
Answer: A
NEW QUESTION 11
What are types of Check Point APIs available currently as part of R80.10 code?
- A. Security Gateway API, Management API, Threat Prevention API and Identity Awareness Web Services API
- B. Management API, Threat Prevention API, Identity Awareness Web Services API and OPSEC SDK API
- C. OSE API, OPSEC SDK API, Threat Prevention API and Policy Editor API
- D. CPMI API, Management API, Threat Prevention API and Identity Awareness Web Services API
Answer: B
NEW QUESTION 12
What action can be performed from SmartUpdate R77?
- A. upgrade_export
- B. fw stat -1
- C. cpinfo
- D. remote_uninstall_verifier
Answer: C
NEW QUESTION 13
You have configured SNX on the Security Gateway. The client connects to the Security Gateway and the user enters the authentication credentials. What must happen after authentication that allows the client to connect to the Security Gateway's VPN domain?
- A. SNX modifies the routing table to forward VPN traffic to the Security Gateway.
- B. An office mode address must be obtained by the client.
- C. The SNX client application must be installed on the client.
- D. Active-X must be allowed on the client.
Answer: A
NEW QUESTION 14
On the following picture an administrator configures Identity Awareness: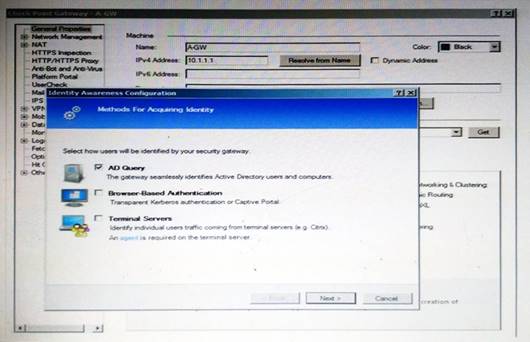
After clicking “Next” the above configuration is supported by:
- A. Kerberos SSO which will be working for Active Directory integration
- B. Based on Active Directory integration which allows the Security Gateway to correlate Active Directory users and machines to IP addresses in a method that is completely transparent to the user
- C. Obligatory usage of Captive Portal
- D. The ports 443 or 80 what will be used by Browser-Based and configured Authentication
Answer: B
Explanation: To enable Identity Awareness:
Log in to R80 SmartConsole.
From the Awareness.
Gateway&s
Servers
view, double-click the Security Gateway on which to enable Identity
On the Network Security tab, select Identity Awareness.
The Identity Awareness
Configuration wizard opens.
Select one or more options. These options set the methods for acquiring identities of managed and unmanaged assets.
AD Query - Lets the Security Gateway seamlessly identify Active Directory users and computers
Browser-Based Authentication - Sends users to a Web page to acquire identities from unidentified users. If Transparent Kerberos Authentication is configured, AD users may be identified transparently.
Terminal Servers - Identify users in a Terminal Server environment (originating from one IP address).
NEW QUESTION 15
Which application should you use to install a contract file?
- A. SmartView Monitor
- B. WebUI
- C. SmartUpdate
- D. SmartProvisioning
Answer: C
Explanation: Using SmartUpdate: If you already use an NGX R65 (or higher) Security Management / Provider-1 /
Multi-Domain Management Server, SmartUpdate allows you to import the service contract file that you have downloaded in Step #3.
Open SmartUpdate and from the Launch Menu select 'Licenses & Contracts' -> 'Update Contracts' -> 'From File...' and provide the path to the file you have downloaded in Step #3: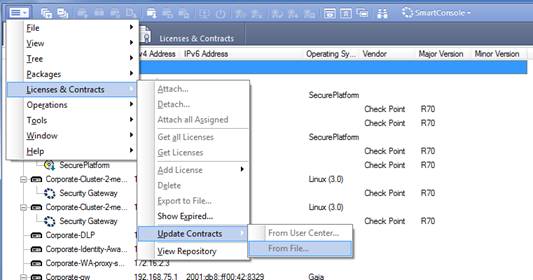
Note: If SmartUpdate is connected to the Internet, you can download the service contract file directly from the UserCenter without going through the download and import steps.
NEW QUESTION 16
Where can administrator edit a list of trusted SmartConsole clients in R80?
- A. cpconfig on a Security Management Server, in the WebUI logged into a Security Management Server.
- B. Only using SmartConsole: Manage and Settings > Permissions and Administrators > Advanced > Trusted Clients.
- C. In cpconfig on a Security Management Server, in the WebUI logged into a Security Management Server, in SmartConsole: Manage and Settings>Permissions and Administrators>Advanced>Trusted Clients.
- D. WebUI client logged to Security Management Server, SmartDashboard: Manage and Settings>Permissions and Administrators>Advanced>Trusted Clients, via cpconfig on a Security Gateway.
Answer: C
NEW QUESTION 17
Which of the completed statements is NOT true? The WebUI can be used to manage user accounts and:
- A. assign privileges to users.
- B. edit the home directory of the user.
- C. add users to your Gaia system.
- D. assign user rights to their home directory in the Security Management Server
Answer: D
Explanation: Users
Use the WebUI and CLI to manage user accounts. You can:
Add users to your Gaia system.
Edit the home directory of the user.
Edit the default shell for a user.
Give a password to a user.
Give privileges to users.
NEW QUESTION 18
Which is NOT an encryption algorithm that can be used in an IPSEC Security Association (Phase 2)?
- A. AES-GCM-256
- B. AES-CBC-256
- C. AES-GCM-128
Answer: B
P.S. Surepassexam now are offering 100% pass ensure 156-215.80 dumps! All 156-215.80 exam questions have been updated with correct answers: https://www.surepassexam.com/156-215.80-exam-dumps.html (440 New Questions)
