Your success in Cisco 200-201 is our sole target and we develop all our 200-201 braindumps in a way that facilitates the attainment of this target. Not only is our 200-201 study material the best you can find, it is also the most detailed and the most updated. 200-201 Practice Exams for Cisco 200-201 are written to the highest standards of technical accuracy.
Cisco 200-201 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Refer to the exhibit.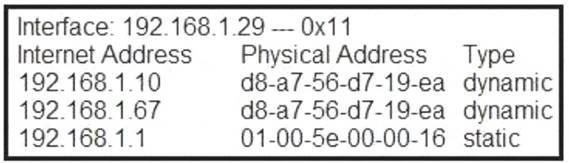
What is occurring in this network?
- A. ARP cache poisoning
- B. DNS cache poisoning
- C. MAC address table overflow
- D. MAC flooding attack
Answer: A
NEW QUESTION 2
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
- A. queries Linux devices that have Microsoft Services for Linux installed
- B. deploys Windows Operating Systems in an automated fashion
- C. is an efficient tool for working with Active Directory
- D. has a Common Information Model, which describes installed hardware and software
Answer: D
NEW QUESTION 3
What is a difference between inline traffic interrogation and traffic mirroring?
- A. Inline inspection acts on the original traffic data flow
- B. Traffic mirroring passes live traffic to a tool for blocking
- C. Traffic mirroring inspects live traffic for analysis and mitigation
- D. Inline traffic copies packets for analysis and security
Answer: B
NEW QUESTION 4
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
- A. Untampered images are used in the security investigation process
- B. Tampered images are used in the security investigation process
- C. The image is tampered if the stored hash and the computed hash match
- D. Tampered images are used in the incident recovery process
- E. The image is untampered if the stored hash and the computed hash match
Answer: BE
NEW QUESTION 5
One of the objectives of information security is to protect the CIA of information and systems. What does CIA mean in this context?
- A. confidentiality, identity, and authorization
- B. confidentiality, integrity, and authorization
- C. confidentiality, identity, and availability
- D. confidentiality, integrity, and availability
Answer: D
NEW QUESTION 6
Refer to the exhibit.
Which type of log is displayed?
- A. IDS
- B. proxy
- C. NetFlow
- D. sys
Answer: D
NEW QUESTION 7
What are the two characteristics of the full packet captures? (Choose two.)
- A. Identifying network loops and collision domains.
- B. Troubleshooting the cause of security and performance issues.
- C. Reassembling fragmented traffic from raw data.
- D. Detecting common hardware faults and identify faulty assets.
- E. Providing a historical record of a network transaction.
Answer: CE
NEW QUESTION 8
What are two social engineering techniques? (Choose two.)
- A. privilege escalation
- B. DDoS attack
- C. phishing
- D. man-in-the-middle
- E. pharming
Answer: CE
NEW QUESTION 9
Drag and drop the access control models from the left onto the correct descriptions on the right.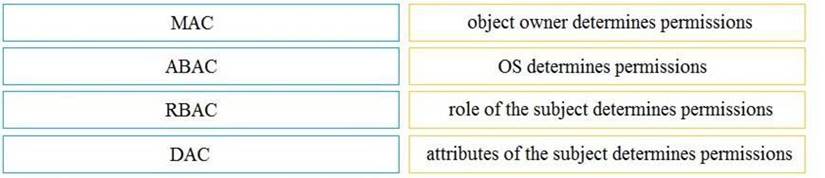
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 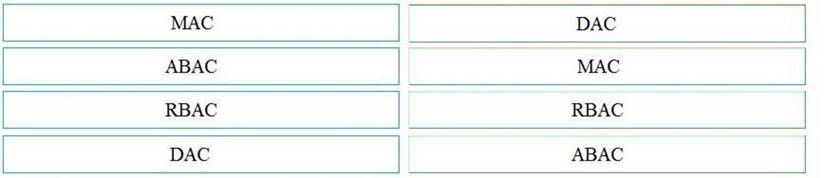
NEW QUESTION 10
What is the difference between a threat and a risk?
- A. Threat represents a potential danger that could take advantage of a weakness in a system
- B. Risk represents the known and identified loss or danger in the system
- C. Risk represents the nonintentional interaction with uncertainty in the system
- D. Threat represents a state of being exposed to an attack or a compromise either physically or logically
Answer: A
NEW QUESTION 11
An analyst discovers that a legitimate security alert has been dismissed. Which signature caused this impact on network traffic?
- A. true negative
- B. false negative
- C. false positive
- D. true positive
Answer: B
NEW QUESTION 12
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header.
Which technology makes this behavior possible?
- A. encapsulation
- B. TOR
- C. tunneling
- D. NAT
Answer: D
NEW QUESTION 13
At which layer is deep packet inspection investigated on a firewall?
- A. internet
- B. transport
- C. application
- D. data link
Answer: C
NEW QUESTION 14
Which event is user interaction?
- A. gaining root access
- B. executing remote code
- C. reading and writing file permission
- D. opening a malicious file
Answer: D
NEW QUESTION 15
An investigator is examining a copy of an ISO file that is stored in CDFS format. What type of evidence is this file?
- A. data from a CD copied using Mac-based system
- B. data from a CD copied using Linux system
- C. data from a DVD copied using Windows system
- D. data from a CD copied using Windows
Answer: B
NEW QUESTION 16
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
- A. least privilege
- B. need to know
- C. integrity validation
- D. due diligence
Answer: A
NEW QUESTION 17
Which action prevents buffer overflow attacks?
- A. variable randomization
- B. using web based applications
- C. input sanitization
- D. using a Linux operating system
Answer: C
NEW QUESTION 18
Which attack method intercepts traffic on a switched network?
- A. denial of service
- B. ARP cache poisoning
- C. DHCP snooping
- D. command and control
Answer: C
NEW QUESTION 19
Refer to the exhibit.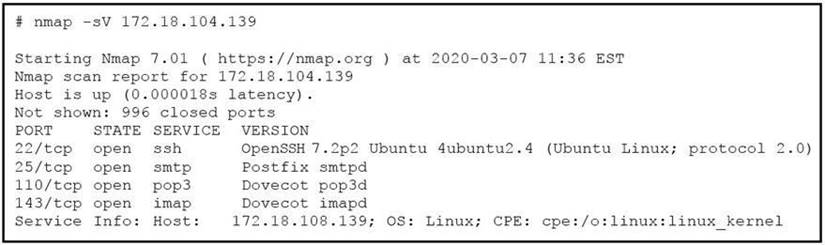
What does the output indicate about the server with the IP address 172.18.104.139?
- A. open ports of a web server
- B. open port of an FTP server
- C. open ports of an email server
- D. running processes of the server
Answer: C
NEW QUESTION 20
What makes HTTPS traffic difficult to monitor?
- A. SSL interception
- B. packet header size
- C. signature detection time
- D. encryption
Answer: D
NEW QUESTION 21
......
Thanks for reading the newest 200-201 exam dumps! We recommend you to try the PREMIUM Allfreedumps.com 200-201 dumps in VCE and PDF here: https://www.allfreedumps.com/200-201-dumps.html (98 Q&As Dumps)
