Passleader offers free demo for 312-50v11 exam. "Certified Ethical Hacker Exam (CEH v11)", also known as 312-50v11 exam, is a EC-Council Certification. This set of posts, Passing the EC-Council 312-50v11 exam, will help you answer those questions. The 312-50v11 Questions & Answers covers all the knowledge points of the real exam. 100% real EC-Council 312-50v11 exams and revised by experts!
Free 312-50v11 Demo Online For EC-Council Certifitcation:
NEW QUESTION 1
Gavin owns a white-hat firm and is performing a website security audit for one of his clients. He begins by running a scan which looks for common misconfigurations and outdated software versions. Which of the following tools is he most likely using?
- A. Nikto
- B. Nmap
- C. Metasploit
- D. Armitage
Answer: B
NEW QUESTION 2
What is the way to decide how a packet will move from an untrusted outside host to a protected inside that is behind a firewall, which permits the hacker to determine which ports are open and if the packets can pass through the packet-filtering of the firewall?
- A. Session hijacking
- B. Firewalking
- C. Man-in-the middle attack
- D. Network sniffing
Answer: B
NEW QUESTION 3
As a securing consultant, what are some of the things you would recommend to a company to ensure DNS security?
- A. Use the same machines for DNS and other applications
- B. Harden DNS servers
- C. Use split-horizon operation for DNS servers
- D. Restrict Zone transfers
- E. Have subnet diversity between DNS servers
Answer: BCDE
NEW QUESTION 4
You just set up a security system in your network. In what kind of system would you find the following string of characters used as a rule within its configuration? alert tcp any any -> 192.168.100.0/24 21 (msg: ““FTP on the network!””;)
- A. A firewall IPTable
- B. FTP Server rule
- C. A Router IPTable
- D. An Intrusion Detection System
Answer: D
NEW QUESTION 5
What is a “Collision attack” in cryptography?
- A. Collision attacks try to get the public key
- B. Collision attacks try to break the hash into three parts to get the plaintext value
- C. Collision attacks try to break the hash into two parts, with the same bytes in each part to get the private key
- D. Collision attacks try to find two inputs producing the same hash
Answer: D
NEW QUESTION 6
Due to a slowdown of normal network operations, the IT department decided to monitor internet traffic for all of the employees. From a legal standpoint, what would be troublesome to take this kind of measure?
- A. All of the employees would stop normal work activities
- B. IT department would be telling employees who the boss is
- C. Not informing the employees that they are going to be monitored could be an invasion of privacy.
- D. The network could still experience traffic slow down.
Answer: C
NEW QUESTION 7
User A is writing a sensitive email message to user B outside the local network. User A has chosen to use PKI to secure his message and ensure only user B can read the sensitive email. At what layer of the OSI layer does the encryption and decryption of the message take place?
- A. Application
- B. Transport
- C. Session
- D. Presentation
Answer: D
NEW QUESTION 8
Although FTP traffic is not encrypted by default, which layer 3 protocol would allow for end-to-end encryption of the connection?
- A. SFTP
- B. Ipsec
- C. SSL
- D. FTPS
Answer: B
NEW QUESTION 9
You have gained physical access to a Windows 2008 R2 server which has an accessible disc drive. When you attempt to boot the server and log in, you are unable to guess the password. In your toolkit, you have an Ubuntu 9.10 Linux LiveCD. Which Linux-based tool can change any user’s password or activate disabled Windows accounts?
- A. John the Ripper
- B. SET
- C. CHNTPW
- D. Cain & Abel
Answer: C
NEW QUESTION 10
The Payment Card Industry Data Security Standard (PCI DSS) contains six different categories of control objectives. Each objective contains one or more requirements, which must be followed in order to achieve compliance. Which of the following requirements would best fit under the objective, "Implement strong access control measures"?
- A. Regularly test security systems and processes.
- B. Encrypt transmission of cardholder data across open, public networks.
- C. Assign a unique ID to each person with computer access.
- D. Use and regularly update anti-virus software on all systems commonly affected by malware.
Answer: C
NEW QUESTION 11
Which of the following algorithms can be used to guarantee the integrity of messages being sent, in transit, or stored?
- A. symmetric algorithms
- B. asymmetric algorithms
- C. hashing algorithms
- D. integrity algorithms
Answer: C
NEW QUESTION 12
In an internal security audit, the white hat hacker gains control over a user account and attempts to acquire access to another account's confidential files and information. How can he achieve this?
- A. Privilege Escalation
- B. Shoulder-Surfing
- C. Hacking Active Directory
- D. Port Scanning
Answer: A
NEW QUESTION 13
Which of the following represents the initial two commands that an IRC client sends to join an IRC network?
- A. USER, NICK
- B. LOGIN, NICK
- C. USER, PASS
- D. LOGIN, USER
Answer: A
NEW QUESTION 14
Take a look at the following attack on a Web Server using obstructed URL: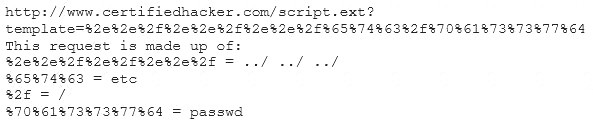
How would you protect from these attacks?
- A. Configure the Web Server to deny requests involving "hex encoded" characters
- B. Create rules in IDS to alert on strange Unicode requests
- C. Use SSL authentication on Web Servers
- D. Enable Active Scripts Detection at the firewall and routers
Answer: B
NEW QUESTION 15
Bob, a network administrator at BigUniversity, realized that some students are connecting their notebooks in the wired network to have Internet access. In the university campus, there are many Ethernet ports available for professors and authorized visitors but not for students.
He identified this when the IDS alerted for malware activities in the network. What should Bob do to avoid this problem?
- A. Disable unused ports in the switches
- B. Separate students in a different VLAN
- C. Use the 802.1x protocol
- D. Ask students to use the wireless network
Answer: C
NEW QUESTION 16
In the context of Windows Security, what is a 'null' user?
- A. A user that has no skills
- B. An account that has been suspended by the admin
- C. A pseudo account that has no username and password
- D. A pseudo account that was created for security administration purpose
Answer: C
NEW QUESTION 17
Every company needs a formal written document which spells out to employees precisely what they are allowed to use the company's systems for, what is prohibited, and what will happen to them if they break the rules. Two printed copies of the policy should be given to every employee as soon as possible after they join the organization. The employee should be asked to sign one copy, which should be safely filed by the company. No one should be allowed to use the company's computer systems until they have signed the policy in acceptance of its terms.
What is this document called?
- A. Information Audit Policy (IAP)
- B. Information Security Policy (ISP)
- C. Penetration Testing Policy (PTP)
- D. Company Compliance Policy (CCP)
Answer: B
NEW QUESTION 18
If a token and 4-digit personal identification number (PIN) are used to access a computer system and the token performs off-line checking for the correct PIN, what type of attack is possible?
- A. Birthday
- B. Brute force
- C. Man-in-the-middle
- D. Smurf
Answer: B
NEW QUESTION 19
A pen tester is configuring a Windows laptop for a test. In setting up Wireshark, what river and library are required to allow the NIC to work in promiscuous mode?
- A. Libpcap
- B. Awinpcap
- C. Winprom
- D. Winpcap
Answer: D
NEW QUESTION 20
Which of the following programming languages is most susceptible to buffer overflow attacks, due to its lack of a built-in bounds checking mechanism?
Code:
#include <string.h> int main(){char buffer[8];
strcpy(buffer, ““11111111111111111111111111111””);} Output: Segmentation fault
- A. C#
- B. Python
- C. Java
- D. C++
Answer: D
NEW QUESTION 21
What kind of detection techniques is being used in antivirus software that identifies malware by collecting data from multiple protected systems and instead of analyzing files locally it’s made on the provider’s environment?
- A. Behavioral based
- B. Heuristics based
- C. Honeypot based
- D. Cloud based
Answer: D
NEW QUESTION 22
During the process of encryption and decryption, what keys are shared? During the process of encryption and decryption, what keys are shared?
- A. Private keys
- B. User passwords
- C. Public keys
- D. Public and private keys
Answer: C
NEW QUESTION 23
ViruXine.W32 virus hides their presence by changing the underlying executable code.
This Virus code mutates while keeping the original algorithm intact, the code changes itself each time it runs, but the function of the code (its semantics) will not change at all.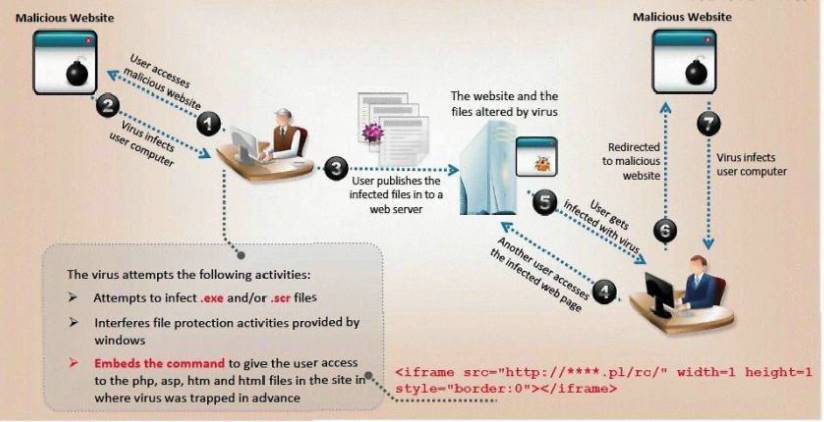
Here is a section of the Virus code: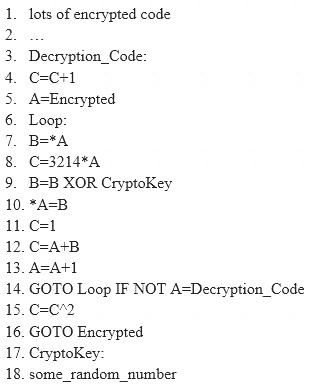
What is this technique called?
- A. Polymorphic Virus
- B. Metamorphic Virus
- C. Dravidic Virus
- D. Stealth Virus
Answer: A
NEW QUESTION 24
Identify the web application attack where the attackers exploit vulnerabilities in dynamically generated web pages to inject client-side script into web pages viewed by other users.
- A. LDAP Injection attack
- B. Cross-Site Scripting (XSS)
- C. SQL injection attack
- D. Cross-Site Request Forgery (CSRF)
Answer: B
NEW QUESTION 25
......
100% Valid and Newest Version 312-50v11 Questions & Answers shared by Downloadfreepdf.net, Get Full Dumps HERE: https://www.downloadfreepdf.net/312-50v11-pdf-download.html (New 254 Q&As)
