Your success in programming in c# 70 483 is our sole target and we develop all our exam ref 70 483 programming in c# in a way that facilitates the attainment of this target. Not only is our exam ref 70 483 material the best you can find, it is also the most detailed and the most updated. 70 483 pdf for Microsoft 70-483 are written to the highest standards of technical accuracy.
Online Microsoft 70-483 free dumps demo Below:
NEW QUESTION 1
DRAG DROP
You are developing a class named ExtensionMethods.
You need to ensure that the ExtensionMethods class implements the IsEmail() extension method on string objects.
You have the following code: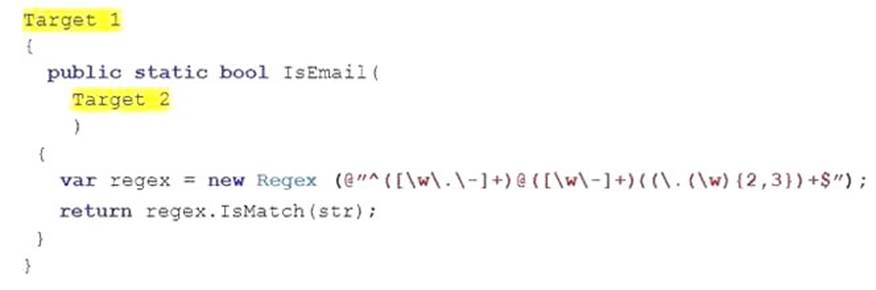
Which code segments should you include in Target 1 and Target 2 to complete the code? (To answer, drag the appropriate code segments to the correct targets in the answer area. Each code segment
may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)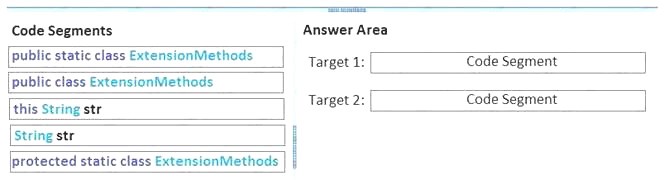
Answer:
Explanation: 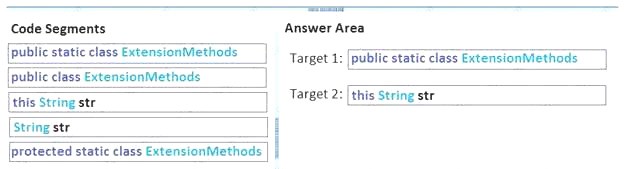
NEW QUESTION 2
You are developing an application that includes the following code segment. (Line numbers are included for reference only.)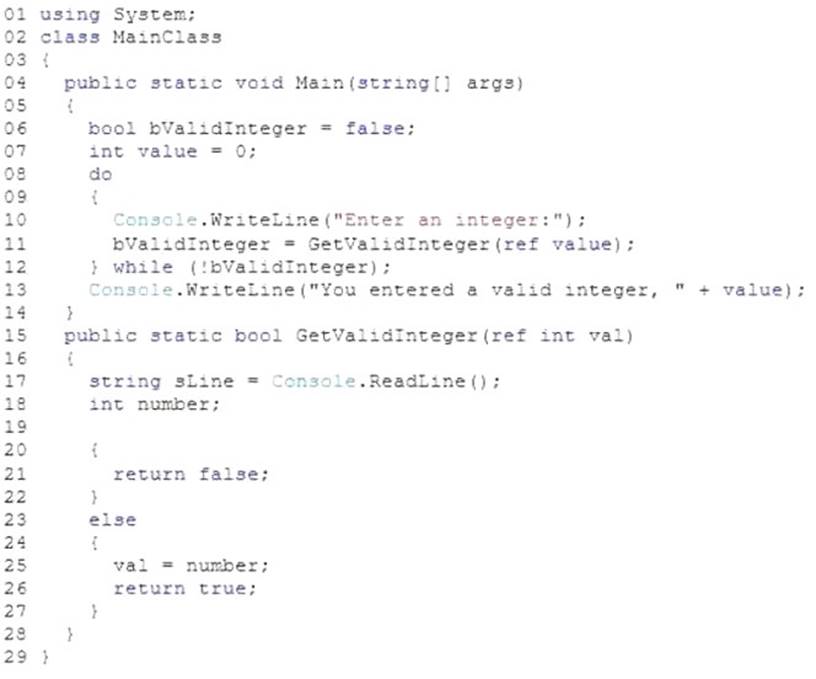
You need to ensure that the application accepts only integer input and prompts the user each time non-integer input is entered.
Which code segment should you add at line 19?
- A. If (!int.TryParse(sLine, out number))
- B. If ((number = Int32.Parse(sLine)) == Single.NaN)
- C. If ((number = int.Parse(sLine)) > Int32.MaxValue)
- D. If (Int32.TryParse(sLine, out number))
Answer: A
Explanation:
Incorrect:
Not B, not C: These will throw exception when user enters non-integer value. Not D: This is exactly the opposite what we want to achieve.
Int32.TryParse - Converts the string representation of a number to its 32-bit signed integer equivalent. A return value indicates whether the conversion succeeded. http://msdn.microsoft.com/en-us/library/f02979c7.aspx
NEW QUESTION 3
You develop an application by using C#. The application counts the number of times a specific word appears within a set of text files. The application includes the following code. (Line numbers are included for reference only.)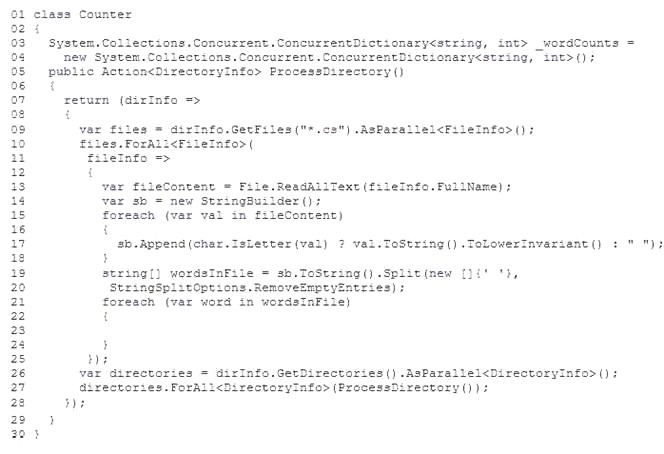
You have the following requirements:
Populate the _wordCounts object with a list of words and the number of occurrences of each word. Ensure that updates to the ConcurrentDictionary object can happen in parallel.
You need to complete the relevant code.
Which code segment should you insert at line 23?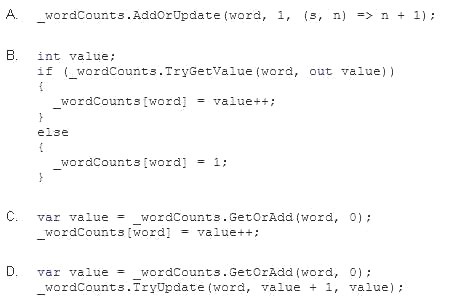
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: A
Explanation: The ConcurrentDictionary<TKey,TValue>.AddOrUpdate method adds a key/value pair to the ConcurrentDictionary<TKey,TValue> if the key does not already exist, or updates a key/value pair in the ConcurrentDictionary<TKey,TValue> if the key already exists.
Example:
// Construct a ConcurrentDictionary
ConcurrentDictionary<int, int> cd = new ConcurrentDictionary<int, int>();
// Bombard the ConcurrentDictionary with 10000 competing AddOrUpdates Parallel.For(0, 10000, i =>
{
// Initial call will set cd[1] = 1.
// Ensuing calls will set cd[1] = cd[1] + 1 cd.AddOrUpdate(1, 1, (key, oldValue) => oldValue + 1);
});
Console.WriteLine("After 10000 AddOrUpdates, cd[1] = {0}, should be 10000", cd[1]); Reference: ConcurrentDictionary<TKey,TValue>.AddOrUpdate Method https://msdn.microsoft.com/en-us/library/ee378665(v=vs.110).aspx
NEW QUESTION 4
You are modifying an application that processes leases. The following code defines the Lease class. (Line numbers are included for reference only.)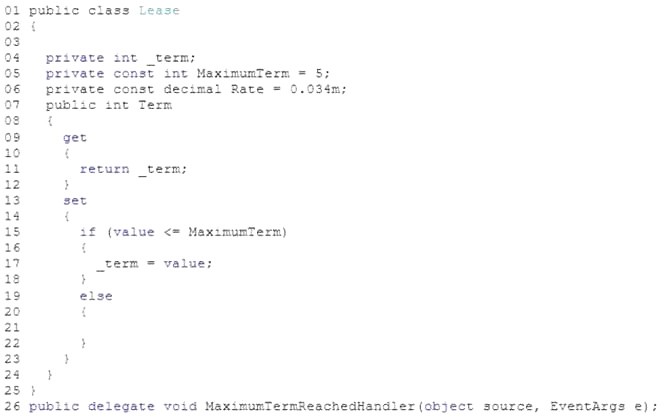
Leases are restricted to a maximum term of 5 years. The application must send a notification message if a lease request exceeds 5 years.
You need to implement the notification mechanism.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)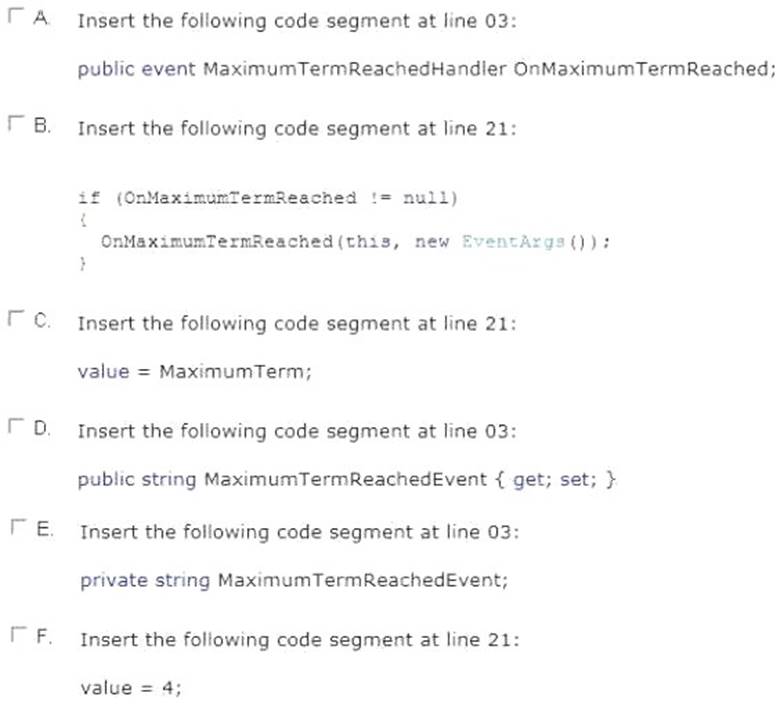
- A. Option A
- B. Option B
- C. Option C
- D. Option D
- E. Option E
- F. Option F
Answer: AB
NEW QUESTION 5
You are developing an application that will transmit large amounts of data between a client computer and a server. You need to ensure the validity of the data by using a cryptographic hashing algorithm. Which algorithm should you use?
- A. ECDsa
- B. RNGCryptoServiceProvider
- C. Rfc2898DeriveBytes
- D. HMACSHA512
Answer: D
Explanation: The HMACSHA512 class computes a Hash-based Message Authentication Code (HMAC) using the SHA512 hash function.
Reference: https://msdn.microsoft.com/enus/ library/system.security.cryptography.hmacsha512(v=vs.110).aspx
NEW QUESTION 6
You are developing an application by using C#. The application includes the following code segment. (Line numbers are included for reference only.)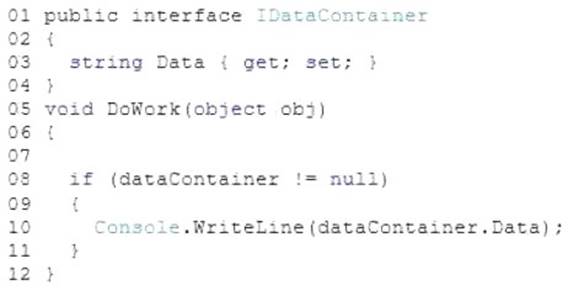
The DoWork() method must throw an InvalidCastException exception if the obj object is not of type IDataContainer when accessing the Data property.
You need to meet the requirements. Which code segment should you insert at line 07?
- A. var dataContainer = (IDataContainer) obj;
- B. var dataContainer = obj as IDataContainer;
- C. var dataContainer = obj is IDataContainer;
- D. dynamic dataContainer = obj;
Answer: A
Explanation: direct cast. If object is not of the given type, an InvalidCastException is thrown. Incorrect:
Not B: If obj is not of the given type, result is null. Not C: If obj is not of a given type, result is false.
Not D: This simply check the variable during runtime. It will not throw an exception. Reference: http://msdn.microsoft.com/en-us/library/ms173105.aspx
NEW QUESTION 7
HOTSPOT
You have the following code (line numbers are included for reference only):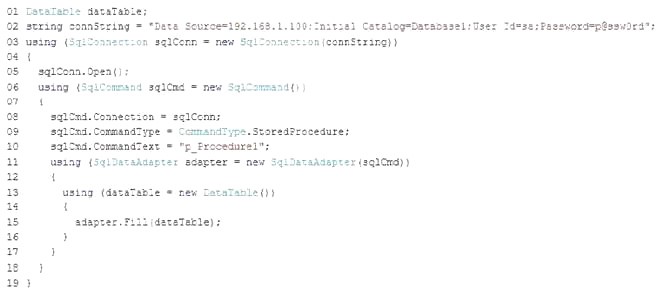
To answer, complete each statement according to the information presented in the code.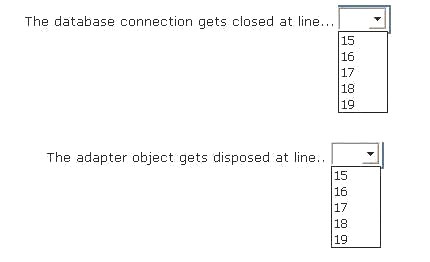
Answer:
Explanation: 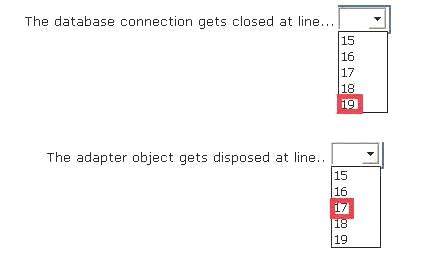
NEW QUESTION 8
You are developing an application that will transmit large amounts of data between a client computer and a server. You need to ensure the validity of the data by using a cryptographic hashing algorithm. Which algorithm should you use?
- A. RSA
- B. HMACSHA256
- C. Aes
- D. RNGCryptoServiceProvider
Answer: B
Explanation: The HMACSHA256 class computes a Hash-based Message Authentication Code (HMAC) by using the SHA256 hash function.
Reference: https://msdn.microsoft.com/enus/ library/system.security.cryptography.hmacsha256(v=vs.110).aspx
NEW QUESTION 9
You are developing an application that includes a class named Order. The application will store a collection of Order objects.
The collection must meet the following requirements: Internally store a key and a value for each collection item. Provide objects to iterators in ascending order based on the key. Ensure that item are accessible by zero-based index or by key. You need to use a collection type that meets the requirements. Which collection type should you use?
- A. LinkedList
- B. Queue
- C. Array
- D. HashTable
- E. SortedList
Answer: E
Explanation: SortedList<TKey, TValue> - Represents a collection of key/value pairs that are sorted by key based on the associated IComparer<T> implementation.
http://msdn.microsoft.com/en-us/library/ms132319.aspx
NEW QUESTION 10
HOTSPOT
You have the following code: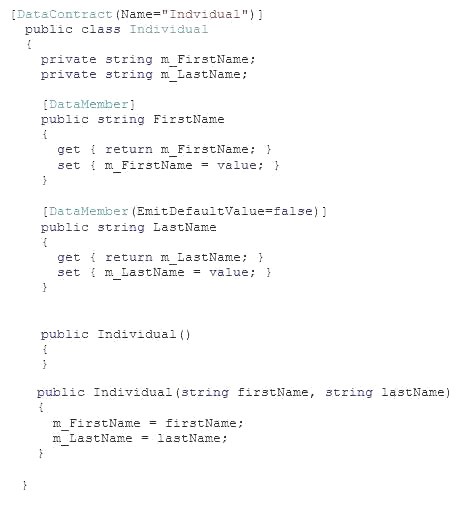
For each of the following statements, select Yes if the statement is true. Otherwise, select No.

Answer:
Explanation: Note:
* The System.Runtime.Serialization namespace contains classes that can be used for serializing and deserializing objects. Serialization is the process of converting an object or a graph of objects into a linear sequence of bytes for either storage or transmission to another location. Deserialization is the process of taking in stored information and recreating objects from it.
* EmitDefaultValue DataMemberAttribute.EmitDefaultValue Property
Gets or sets a value that specifies whether to serialize the default value for a field or property being serialized.
true if the default value for a member should be generated in the serialization stream; otherwise, false.
NEW QUESTION 11
You need to write a method that retrieves data from a Microsoft Access 2013 database. The method must meet the following requirements:
Be read-only.
Be able to use the data before the entire data set is retrieved.
Minimize the amount of system overhead and the amount of memory usage. Which type of object should you use in the method?
- A. SqlDataAdapter
- B. DataContext
- C. DbDataAdapter
- D. OleDbDataReader
Answer: D
Explanation: OleDbDataReader Class
Provides a way of reading a forward-only stream of data rows from a data source. Example:
OleDbConnection cn = new OleDbConnection(); OleDbCommand cmd = new OleDbCommand(); DataTable schemaTable;
OleDbDataReader myReader;
//Open a connection to the SQL Server Northwind database.
cn.ConnectionString = "Provider=SQLOLEDB;Data Source=server;User ID=login; Password=password;Initial Catalog=Northwind";
NEW QUESTION 12
You are developing a method named GetHash that will return a hash value for a file. The method includes the following code. (Line numbers are included for reference only.)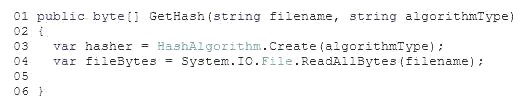
You need to return the cryptographic hash of the bytes contained in the fileBytes variable. Which code segment should you insert at line 05?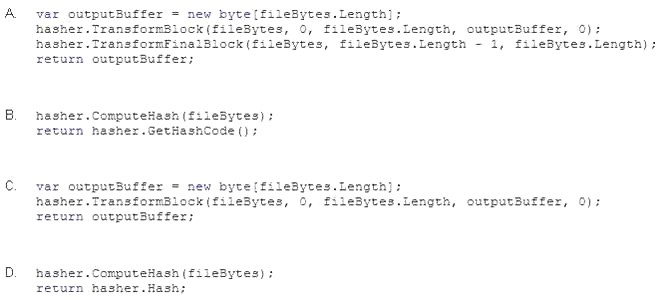
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: D
Explanation: The hashAlgorithm.ComputeHash computes the hash value for the input data. Reference: HashAlgorithm.ComputeHash Method https://msdn.microsoft.com/enus/ library/system.security.cryptography.hashalgorithm.computehash(v=vs.110).aspx
NEW QUESTION 13
DRAG DROP
You need to validate whether string strJson is a valid JSON string.
How should you complete the code? To answer, drag the appropriate code elements to the correct targets in the answer area. Each code element may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.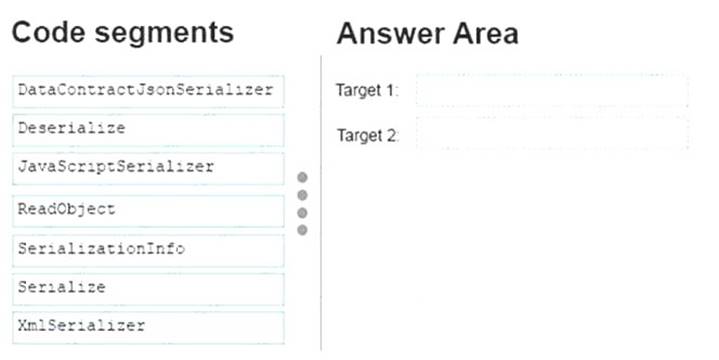
Answer:
Explanation: serializer = new DataContractJsonSerializer();
var result = serializer.ReadObject<Dictionary<string, object>>(StrJson);
NEW QUESTION 14
You are developing an application that accepts the input of dates from the user.
Users enter the date in their local format. The date entered by the user is stored in a string variable named inputDate. The valid date value must be placed in a DateTime variable named validatedDate. You need to validate the entered date and convert it to Coordinated Universal Time (UTC). The code must not cause an exception to be thrown.
Which code segment should you use?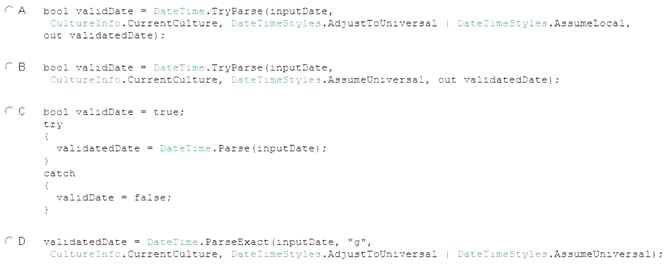
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: A
Explanation: AdjustToUniversal parses s and, if necessary, converts it to UTC.
Note: The DateTime.TryParse method converts the specified string representation of a date and time to its DateTime equivalent using the specified culture-specific format information and formatting style, and returns a value that indicates whether the conversion succeeded.
NEW QUESTION 15
You have an application that will send confidential information to a Web server. You need to ensure that the data is encrypted when it is sent across the network. Which class should you use?
- A. CryptoStream
- B. AuthenticatedStream
- C. PipeStream
- D. NegotiateStream
Answer: A
Explanation: The CryptoStream Class defines a stream that links data streams to cryptographic transformations. The common language runtime uses a stream-oriented design for cryptography. The core of this design is CryptoStream.
Reference: CryptoStream Class https://msdn.microsoft.com/enQuestions
& Answers PDF P-137 us/library/system.security.cryptography.cryptostream(v=vs.110).aspx
NEW QUESTION 16
You need to create a method that can be called by using a varying number of parameters. What should you use?
- A. Method overloading
- B. Interface
- C. Named parameters
- D. Lambda expressions
Answer: A
Explanation: Member overloading means creating two or more members on the same type that differ only in the number or type of parameters but have the same name.
Overloading is one of the most important techniques for improving usability, productivity, and readability of reusable libraries. Overloading on the number of parameters makes it possible to provide simpler versions of constructors and methods. Overloading on the parameter type makes it possible to use the same member name for members performing identical operations on a selected set of different types.
100% Valid and Newest Version 70-483 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/70-483-dumps.html (New 288 Q&As)
