It is impossible to pass Microsoft mb-300 exam without any help in the short term. Come to Passleader soon and find the most advanced, correct and guaranteed Microsoft mb-300 practice questions. You will get a surprising result by our Up to the immediate present Microsoft Dynamics 365 Unified Operations Core practice guides.
NEW QUESTION 1
You assign security roles to users in your company. The security roles contain one or more duty assignments. The purchasing manager role must be able to view payment journals. You need to edit the security configuration to meet the requirement. What should you do?
- A. Create a new security rol
- B. Create a purchasing manager duty and assign it to that rol
- C. Then assign the duty to the user.
- D. Create a new privileg
- E. Assign the View only permission to the privileg
- F. Then assign the privilege to the user.
- G. Edit the existing role and assign the View payment journal transactions permission level.
- H. Edit the duty to view only on the payment journa
- I. The duty is assigned to the purchasing manager role.
Answer: C
NEW QUESTION 2
You need to configure check printing for Munson’s.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.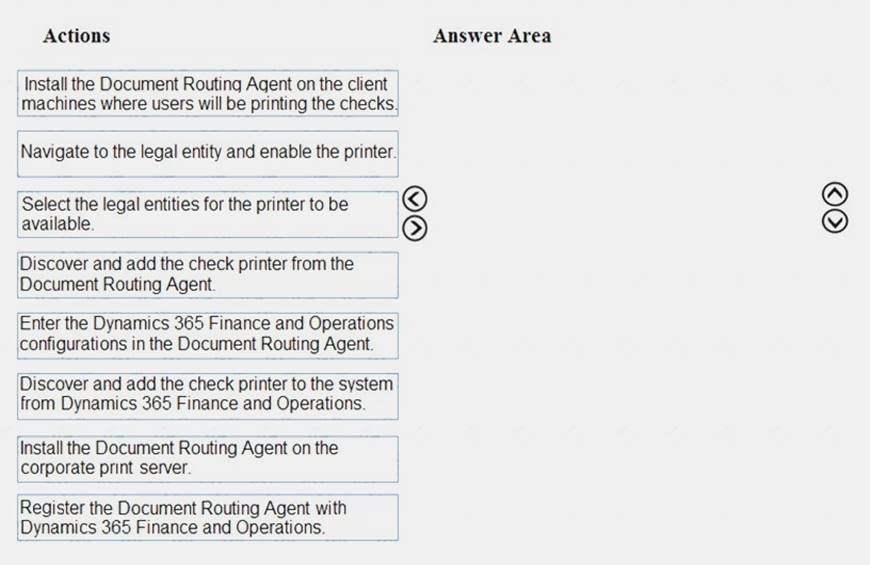
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Reference:
https://docs.microsoft.com/en-us/dynamics365/unified-operations/dev-itpro/analytics/install-document-routing-a
NEW QUESTION 3
A company implements Dynamics 365 for Finance and Operations and uses Lifecycle Services (LCS). The company uses both standard and customized functionality.
Testers have reported problems using the recent User Acceptance Testing (UAT) round.
You need to resolve these issues before UAT can proceed.
Which tools should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.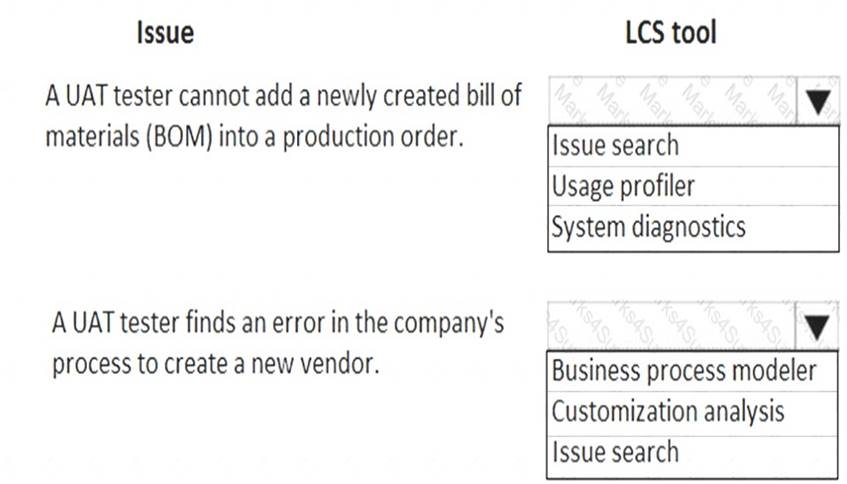
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 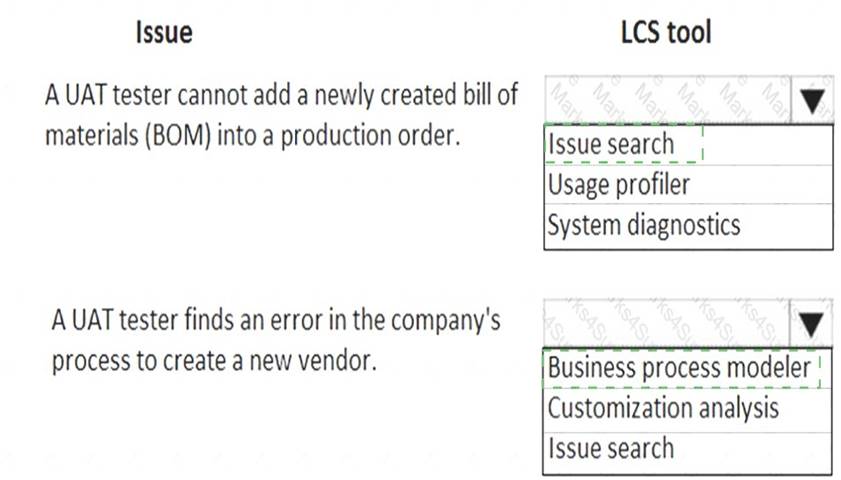
NEW QUESTION 4
You plan a data migration from Dynamics AX 2009 to a Dynamics 365 for Finance and Operations environment.
You need to ensure that you can perform the data migration. What should you do first?
- A. Upgrade the existing on-premises environment to Dynamics 365 for Finance and Operations online
- B. Migrate content to Dynamics POS (Point-of-Sale) 2009
- C. Upgrade the existing on-premises environment to Dynamics AX 2012 R2
- D. Migrate content to Dynamics 365 Business Central
Answer: C
NEW QUESTION 5
You are a system administrator using Dynamics 365 for Finance and Operations. You are responsible for troubleshooting workflows.
You need to determine where workflows are failing based on error messages.
Which runtime is raising the error when the following activity and error occurs? To answer, select the appropriate runtime in the answer area.
NOTE: Each correct selection is worth one point.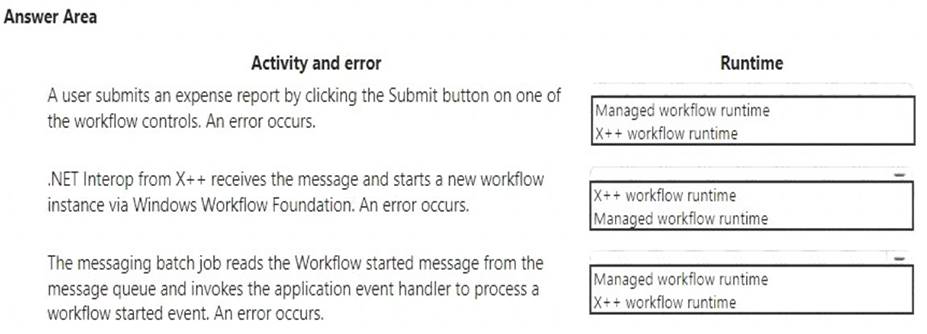
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
References:
https://docs.microsoft.com/en-us/dynamics365/unified-operations/fin-and-ops/organization-administration/work
NEW QUESTION 6
You want to enhance usability in the Dynamics 365 for Finance and Operations deployment for your organization.
Your environment has been configured using default components. You set up filters on the channel deployment workspace.
You need to use the correct UI filter.
Which UI filter should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.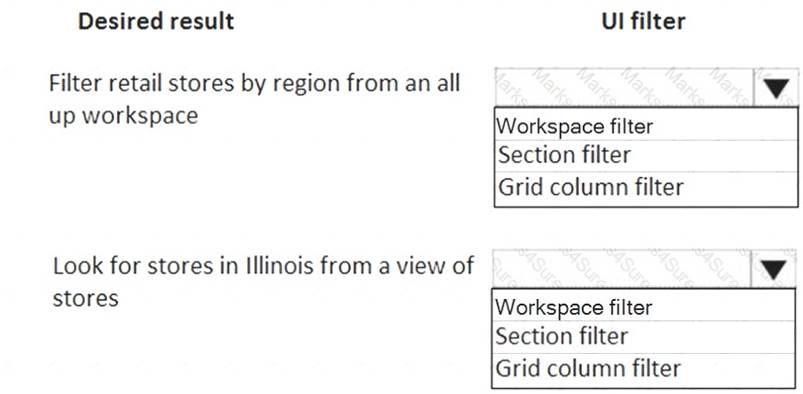
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
References:
https://docs.microsoft.com/en-us/dynamics365/unified-operations/fin-and-ops/get-started/configure-filter-works
NEW QUESTION 7
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring a Dynamics 365 for Finance and Operations environment. You must set up Microsoft Excel data exports.
You need to verify that the solution will result in a successful export of data to Excel.
Solution: Use Workbook Designer to build an editable custom export of customer data that includes only postal code, city, and state.
Does the solution meet the goal?
- A. Yes
- B. No
Answer: A
NEW QUESTION 8
A company plans to use Dynamics 365 for Finance and Operations. You need to implement the security architecture.
Which component should you use for each requirement? To answer, select the appropriate security component in the answer area.
NOTE: Each correct selection is worth one point.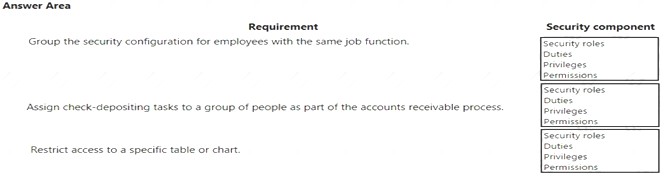
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 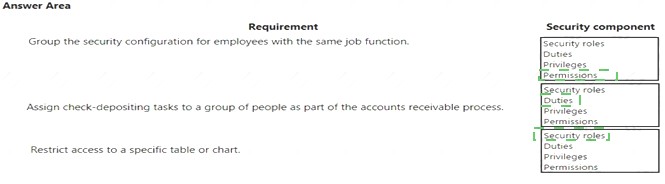
NEW QUESTION 9
A company plans to set up an organizational hierarchy to manage organizational relationships. You need to identify which organizational purpose to use. What purpose can you assign to an organizational hierarchy?
- A. Centralized payments
- B. Financial reason code
- C. Cost center
- D. Price models
Answer: A
Explanation:
Reference:
https://docs.microsoft.com/en-us/dynamics365/unified-operations/financials/cash-bank-management/set-up-cent
NEW QUESTION 10
You are a systems administrator at a company that has implemented Dynamics 365 for Finance and Operations.
New employees are starting at the company.
You need to extend the electronic signatures functionality to them.
Which two actions should you perform? Each answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. On the Email parameters page, specify that SSL is required
- B. Specify the user’s email address
- C. In License configuration, enable Maintenance mode
- D. Select the Electronic signature check box
Answer: CD
Explanation:
Reference:
https://docs.microsoft.com/en-us/dynamics365/unified-operations/fin-and-ops/organization-administration/tasks
NEW QUESTION 11
You manage a Dynamics 365 for Finance and Operations environment. Users report slow queries, deadlocks, and crashes. You need identify which tool to use to troubleshoot. What should you use?
- A. System diagnostics
- B. Environment monitoring
- C. DirectQuery
- D. Microsoft Azure Active Directory Connect Health Agent
Answer: B
Explanation:
Reference:
https://blogs.msdn.microsoft.com/axsa/2021/06/05/how-to-use-environment-monitoring-view-raw-logs/
NEW QUESTION 12
You are a Dynamics 365 for Finance and Operations implementation consultant.
You plan to use automated regression testing in a company's environment, as the system will be updated frequently until automatic updates can be applied.
You need to identify when and what key business object should be used during the implementation. Which business objects should you use? To answer, drag the appropriate objects to the correct component
actions. Each object may be used once, more than once, or not at all. You may need to drag the split bar
between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 13
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring a Dynamics 365 for Finance and Operations environment. You must set up Microsoft Excel data exports.
You need to verify that the solution will result in a successful export of data to Excel.
Solution: Use Open in Excel to open an entity form that does not share the same root data source by implementing the ExportToExcellGeneratedCustomExport interface.
Does the solution meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 14
You need to connect the Excel instance to the Relecloud production instance. What should you do?
- A. Set the server URL to Microsoft.Dynamics.Platform.Integration.Office.UrlViewerApplet.
- B. Set the server URL to https://relecloud-prod.operations.dynamics.com.
- C. Set the App Correlation ID to https://relecloud-prod.operations.dynamics.com.
- D. Set the App Correlation ID to the App Id in the Dynamics 365 Office App Parameters.
Answer: B
Explanation:
Reference:
https://docs.microsoft.com/en-us/dynamics365/unified-operations/dev-itpro/office-integration/use-excel-add-in
NEW QUESTION 15
A company has complex security requirements. You are asked to set up security access for users. You need to identify the main attributes for security role, duty, privilege, and permissions.
Which of the following attributes does each of the security components have? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.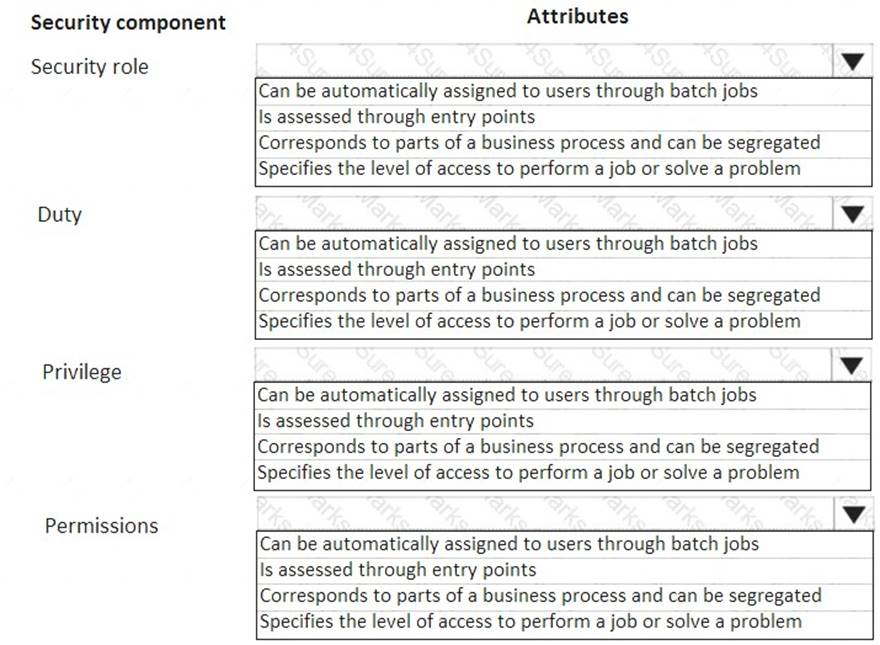
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
References:
https://docs.microsoft.com/en-us/dynamics365/unified-operations/dev-itpro/sysadmin/role-based-security
NEW QUESTION 16
A company sets up a workflow for expense reports. An employee named Sam submits an expense report totaling USD 7,000 to go through the workflow.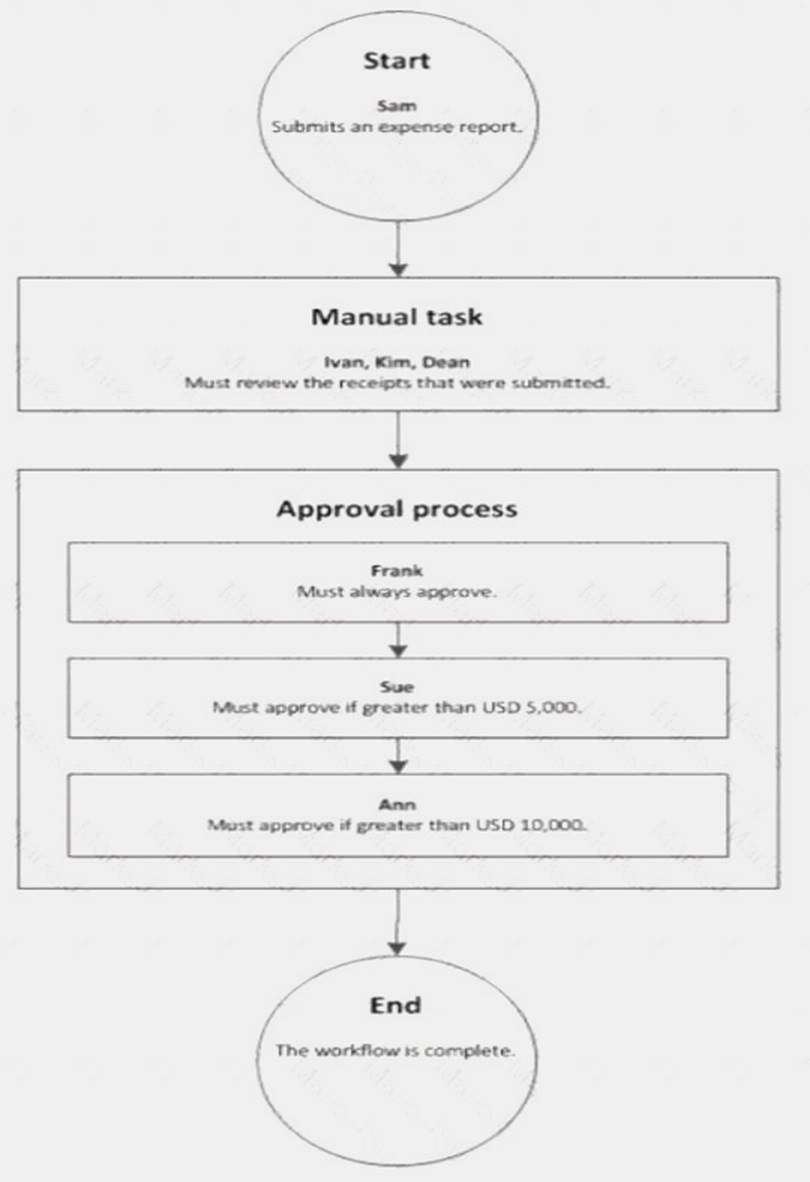
Use the drop-down menus to select the answer choice that answers each question based on the information
presented in the graphic.
NOTE: Each correct selection is worth one point.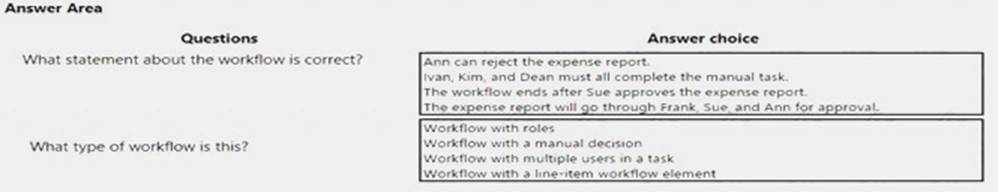
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Reference:
https://docs.microsoft.com/en-us/dynamicsax-2012/appuser-itpro/workflow-with-multiple-users-in-a-task
NEW QUESTION 17
You are a Dynamics 365 for Finance and Operations system administrator for a new implementation. You have a solution that needs to be tested using User Acceptance Testing (UAT). You have created a
Business process modeler (BPM) library.
You need to validate and support the solution.
Which three actions should you perform? Each answer presents part of the solution.
- A. Upload the saved recording to BPM.
- B. Create a new Business process library
- C. Export the task recording to Microsoft Word and upload it to BPM.
- D. Record test cases and save them to BPM.
- E. Create and save a new task recording.
Answer: ABD
NEW QUESTION 18
You set up a new installation of Dynamics 365 for Finance and Operations for a Fortune 500 company. The company is organized into divisions.
You need to design the structure in the application.
What application features should you use? To answer, drag the appropriate setting to the correct drop targets. Each source may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
References:
https://docs.microsoft.com/en-us/dynamics365/unified-operations/fin-and-ops/organization-administration/organ
NEW QUESTION 19
A company implements Dynamics 365 for Finance and Operations.
They need additional information and want a subledger to record information for additional reporting rather than customizing all reports.
You need to set up the posting to accommodate the need for a subledger. Which three actions should you take? Each answer presents part of the solution.
- A. Update existing reports to prevent data in the identified area from reporting
- B. Create posting profiles to post to the identified area as needed for the request
- C. Create posting definitions to post to the identified area as needed for the request
- D. Update existing reports to add data in the identified area
- E. Identify an area of the chart of accounts to record to as the subledger
Answer: BDE
NEW QUESTION 20
You are a Dynamics 365 for Finance and Operations system administrator. You have production and testing environments. You move the workflow from the testing environment to the production environment.
The workflow in the production environment is stuck in a wait state.
You need to resolve the issue with the workflow in the production environment. What should you do?
- A. Set the workflow batch job to critical
- B. Set the workflow messaging batch job group
- C. Grant the user workflow permissions
- D. Set the workflow execution account in the workflow parameters
Answer: D
NEW QUESTION 21
A company implements Dynamics 365 for Finance and Operations.
You are responsible for creating a custom feature within a solution by using Microsoft Azure DevOps. Testers have found a bug while running one of the User Acceptance Testing (UAT) scripts. However, it is not a high-severity bug and has been found to not have interconnected dependencies to other branches within the process flow.
You need to deploy the passed functionality features. What should you do?
- A. Exclude the specific package from the Business process modeler (BPM).
- B. Exclude the specific package from the data package in the Data management tool.
- C. Exclude the specific package from the deployable package in Microsoft Azure DevOps.
- D. Exclude the specific package from the deployable package in Configuration data manager.
Answer: C
NEW QUESTION 22
You work with a systems administrator for Dynamics 365 for Finance and Operations.
The system has been configured to prompt users for how they want to send emails based on the given scenario they are encountering. In certain situations, they will want to generate an email to forward to an account executive who doesn’t have access to Dynamics 365 for Finance and Operations. Other times, the emails
should be either sent as an attachment to a user email or through a generic no reply email.
You need to determine which configuration to provide to the file system administrator for the given scenario. Which option should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.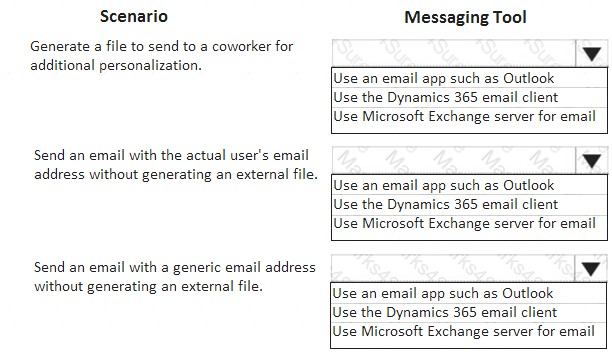
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 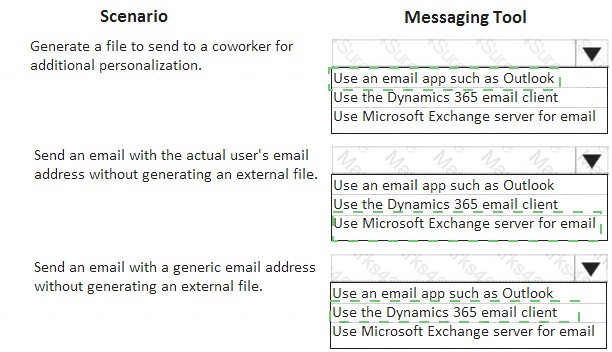
NEW QUESTION 23
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are developing a file-based integration to Dynamics 365 for Finance and Operations.
Microsoft Excel files with 15,000 or more records need to be imported into the system periodically by individual users. The records need to be imported in full within a 5-minute approved window.
You need to determine how to accomplish the import into the system.
Solution: Import the data by using the Data Management Framework's package API. Does the solution meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 24
......
Thanks for reading the newest mb-300 exam dumps! We recommend you to try the PREMIUM Certstest mb-300 dumps in VCE and PDF here: https://www.certstest.com/dumps/mb-300/ (110 Q&As Dumps)
