Act now and download your AZ-202 Exam Dumps today! Do not waste time for the worthless AZ-202 Dumps Questions tutorials. Download AZ-202 Exam Questions and Answers with real questions and answers and begin to learn AZ-202 Exam Questions with a classic professional.
Free AZ-202 Demo Online For Microsoft Certifitcation:
NEW QUESTION 1
You develop software solutions for a web services company. You have the following code. (Line numbers are for reference only.)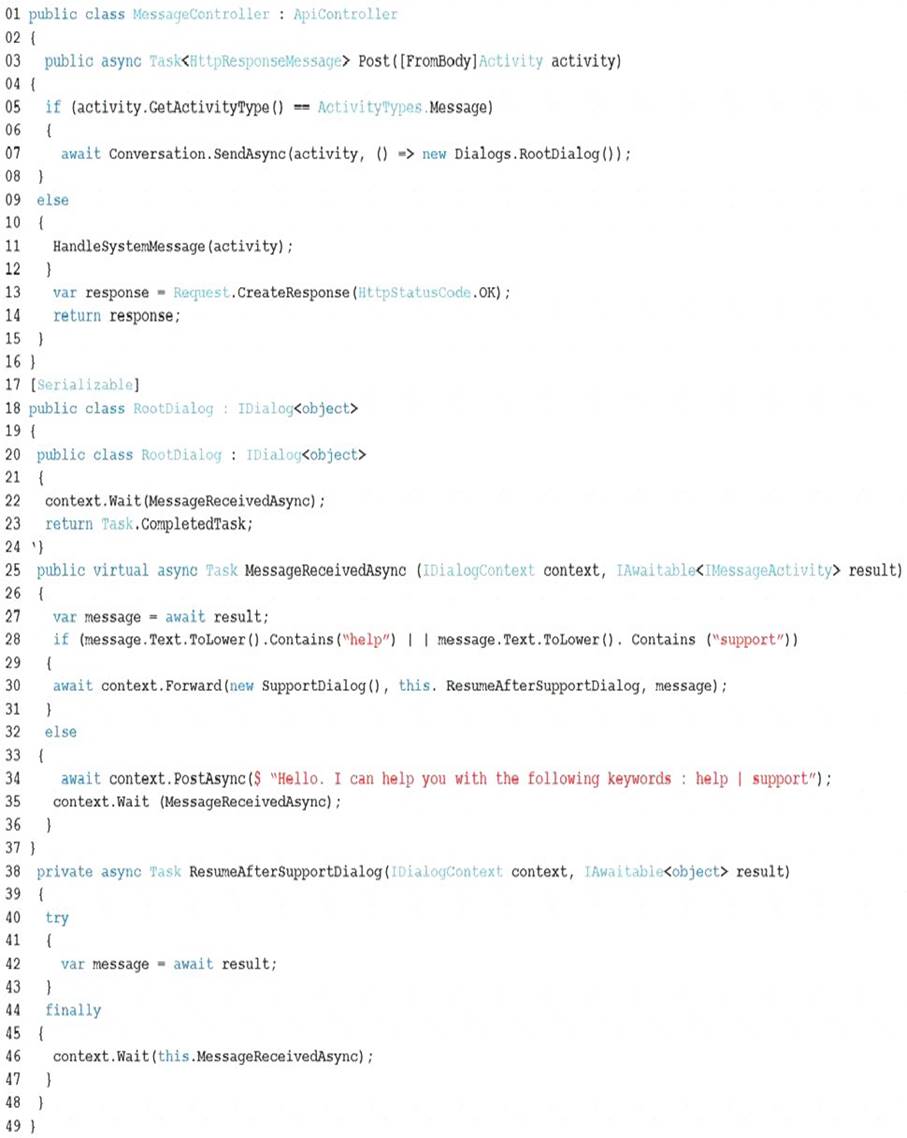
You need to implement an immediate response customer support solution for the company’s website. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.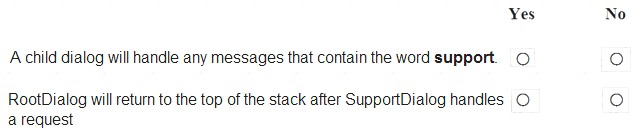
Answer:
Explanation: 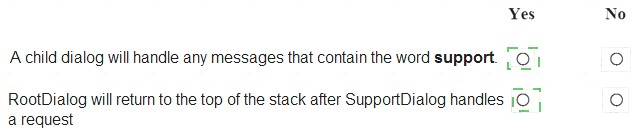
NEW QUESTION 2
You need to tool code at line LE03 of Login Event to ensure that all authentication events are processed correctly. How should you complete the code? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.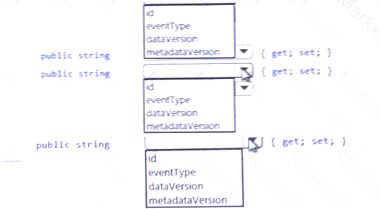
Answer:
Explanation: 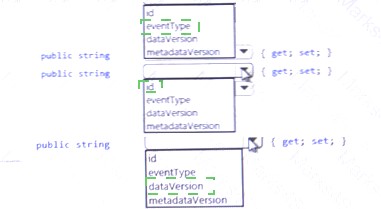
Topic 5, Coho WineryLabelMaker app
Coho Winery produces, bottles, and distributes a variety of wines globally. You are a developer implementing highly scalable and resilient applications to support online order processing by using Azure solutions.
Coho Winery has a LabelMaker application that prints labels for wine bottles. The application sends data to several printers. The application consists of five modules that run independently on virtual machines (VMs). Coho Winery plans to move the application to Azure and continue to support label creation.
External partners send data to the LabelMaker application to include artwork and text for custom label designs.
Requirements Data
You identify the following requirements for data management and manipulation:
• Order data is stored as nonrelational JSON and must be queried using Structured Query Language (SQL).
• Changes to the Order data must reflect immediately across all partitions. All reads to the Order data must fetch the most recent writes.
Security
You have the following security requirements:
• Users of Coho Winery applications must be able to provide access to documents, resources, and applications to external partners.
• External partners must use their own credentials and authenticate with their organization's identity management solution.
• External partner logins must be audited monthly for application use by a user account administrator to maintain company compliance.
• Storage of e-commerce application settings must be maintained in Azure Key Vault.
• E-commerce application sign-ins must be secured by using Azure App Service authentication and Azure Active Directory (AAD).
• Conditional access policies must be applied at the application level to protect company content.
• The LabelMaker application must be secured by using an AAD account that has full access to all namespaces of the Azure Kubernetes Service (AKS) cluster.
LabelMaker app
Azure Monitor Container Health must be used to monitor the performance of workloads that are deployed to
Kubernetes environments and hosted on Azure Kubernetes Service (AKS).
You must use Azure Container Registry to publish images that support the AKS deployment.
Architecture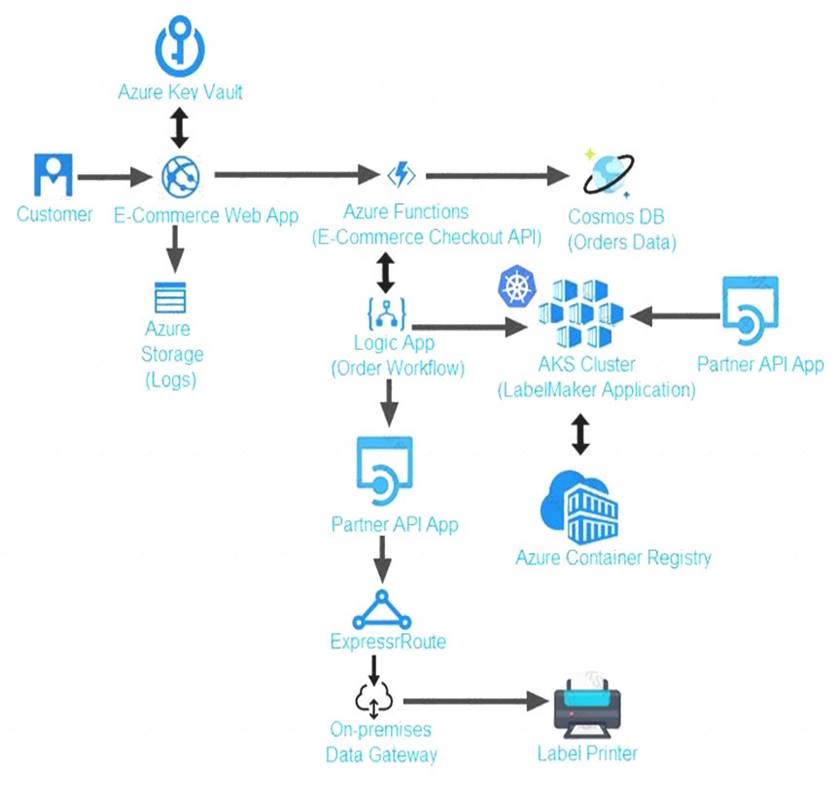
Issues
Calls to the Printer API App fall periodically due to printer communication timeouts.
Printer communication timeouts occur after 10 seconds. The label printer must only receive up to 5 attempts within one minute
The order workflow fails to run upon initial deployment to Azure.
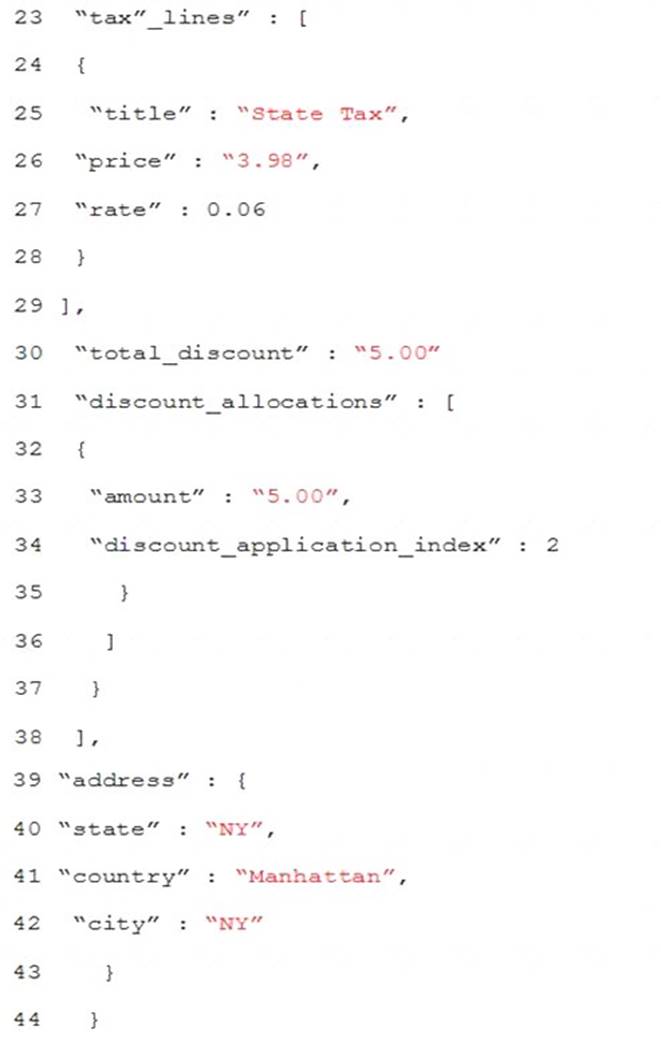
Order.Json
Relevant portions oi the app files are shown below. Line numbers are included for reference only. The JSON file contains a representation of the data for an order that includes a single item.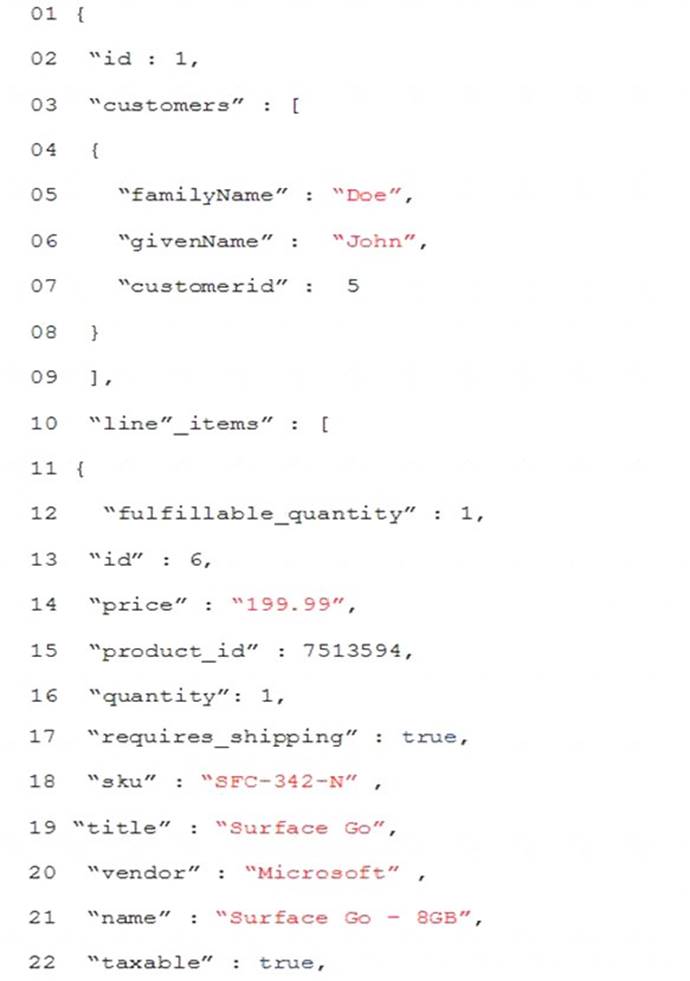
NEW QUESTION 3
You need to implement the purchase requirement. What should you do?
- A. Use the Bot FrameworkREST API attachment operations to send the user's voice and the Speech Service API to recognize intents.
- B. Use the Direct line REST API to send the user's voice and the Speech Service API to recognize intents.
- C. Use the Speech Service API to send the user's voice and the Bot Framework REST API conversation operations to recognize intents.
- D. Use the Bot Framework REST API conversation operations to send the user's voice and the Speech Service API to recognize intents.
Answer: D
Explanation: Scenario: Enable users to place an order for delivery or pickup by using their voice.
You must develop a chatbot by using the Bot Builder SDK and Language Understanding Intelligence Service (LUIS). The chatbot must allow users to order food for pickup or delivery.
The Bot Framework REST APIs enable you to build bots that exchange messages with channels configured in the Bot Framework Portal, store and retrieve state data, and connect your own client applications to your bots. All Bot Framework services use industry-standard REST and JSON over HTTPS.
The Speech Service API is used to recognize intents. References:
https://docs.microsoft.com/en-us/azure/bot-service/rest-api/bot-framework-rest-connector-concepts?view=azure- https://docs.microsoft.com/en-us/azure/cognitive-services/speech-service/how-to-recognize-intents-from-speech
NEW QUESTION 4
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution. Determine whether the solution meets the stated goals.
You develop an entertainment application where users can buy and trade virtual real estate. The application must scale to support thousands of users.
The current architecture includes five Azure Virtual Machines (VM) that connect to an Azure SQL Database for account information and Azure Table Storage for backend services. A user interacts with these components in the cloud at any given time
- Routing Service – Routes a request to the appropriate service and must not persist data across sessions
- Account Service – Stores and manages all account information and authentication and requires data to persist across sessions.
- User Service – Stores and manages all user information and requires data to persist across sessions.
- Housing Network Service – Stores and manages the current real-estate economy and requires data to persist across sessions.
- Trade Service – Stores and manages virtual trade between accounts and requires data to persist across sessions.
Due to volatile user traffic, a microservices solution is selected for scale agility.
You need to migrate to a distributed microservices solution on Azure Service Fabric.
Solution: Create a Service Fabric Cluster with a stateful Reliable Service for Routing Service. Deploy a Guest Executable to Service Fabric for each component.
Does the solution meet the goal?
- A. YES
- B. NO
Answer: B
Explanation: We should use stateful services when we want data to persist, and stateless service when data must not persist. References:
https://docs.microsoft.com/en-us/azure/service-fabric/service-fabric-reliable-services-introduction
NEW QUESTION 5
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution. Determine whether the solution meets the stated goals.
You need to ensure that authentication events are triggered and processed according to the policy. Solution: Create a new Azure Event Grid topic and add a subscription for the events.
Does the solution meet the goal?
- A. Yes
- B. No
Answer: B
Explanation: Use a separate Azure Event Grid topics and subscriptions for sign-in and sign-out events.
Scenario: Authentication events are used to monitor users signing in and signing out. All authentication events must be processed by Policy service. Sign outs must be processed as quickly as possible.
NEW QUESTION 6
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution Determine whether the solution meets the stated goals.
You need to ensure that the SecurityPin security requirements are met.
Solution: Enable Always Encrypted for the SecurityPin column using a certificate based on a trusted certificate authority. Update the Getting Started document with instruction to ensure that the certificate is installed on user machines.
Does the solution meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 7
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result these questions
will not appear in the review screen.
You use ASP.NET Core MVC with ADO.NET to develop an application. You implement database sharding for the application by using Azure SQL Database. You establish communication links between the shard databases.
You need to implement a strategy that allows a group of operations that are performed on multiple Azure databases to be rolled back on all databases if any of the operations fail.
Solution:
• Deploy a SQL database instance in an Azure Virtual Machine (VM).
• Establish linked servers to each Azure SQL Database instance from the SQL Server instance in the VM.
• Create a stored procedure in the VM that performs the update operations using a distributed transaction and commits them if successful.
• Run the SQL stored procedure on the SQL Server instance in the VM. Does the solution meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 8
You need to implement the Log policy.
How should you complete the Azure Event Grid subscription? To answer, drag the appropriate JSON segments to the correct locations. Each (SON segment may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.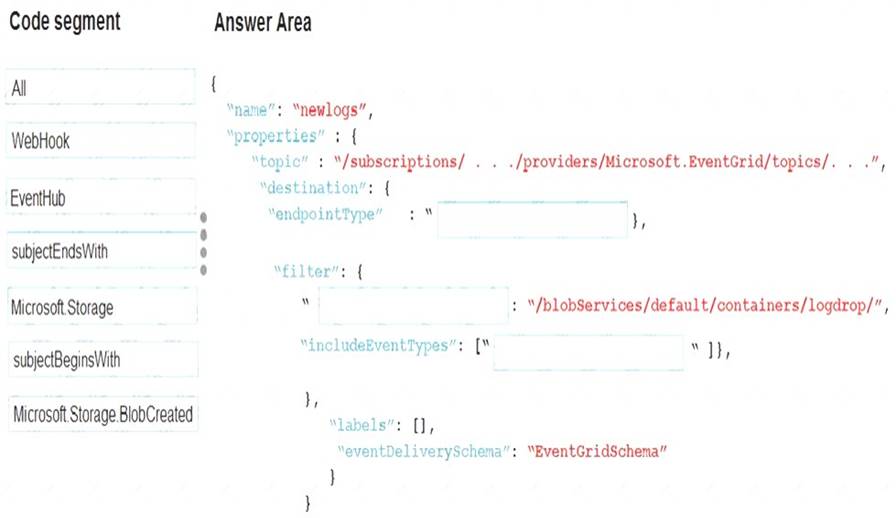
Answer:
Explanation: Box 1:WebHook
Scenario: If an anomaly is detected, an Azure Function that emails administrators is called by using an HTTP
WebHook.
endpointType: The type of endpoint for the subscription (webhook/HTTP, Event Hub, or queue). Box 2: SubjectBeginsWith
Box 3: Microsoft.Storage.BlobCreated Scenario: Log Policy
All Azure App Service Web Apps must write logs to Azure Blob storage. All log files should be saved to a container named logdrop. Logs must remain in the container for 15 days.
Example subscription schema
{
"properties": { "destination": {
"endpointType": "webhook", "properties": {
"endpointUrl": "https://example.azurewebsites.net/api/HttpTriggerCSharp1?code=VXbGWce53l48Mt8wuotr0GPmyJ/nDT4hgd
}
},
"filter": {
"includedEventTypes": [ "Microsoft.Storage.BlobCreated", "Microsoft.Storage.BlobDeleted" ], "subjectBeginsWith": "blobServices/default/containers/mycontainer/log",
"subjectEndsWith": ".jpg", "isSubjectCaseSensitive ": "true"
}
}
}
References:
https://docs.microsoft.com/en-us/azure/event-grid/subscription-creation-schema
NEW QUESTION 9
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result these questions will not appear in the review screen.
Margie’s Travel is an international travel and bookings management service. The company is expanding into restaurant bookings. You are tasked with implementing Azure Search for the restaurants listed in their solution.
You create the index in Azure Search.
You need to import the restaurant data into the Azure Search service by using the Azure Search .NET SDK. Solution:
1. Create a SearchServiceClient object to connect to the search index.
2. Create an IndexBatch that contains the documents which must be added.
3. Create a DataSource instance and set its Container property to the DataContainer.
4. Call the Documentsindex method of the SearchlndexClient to send the IndexBatch to the search index. Does the solution meet the goal?
- A. No
- B. Yes
Answer: A
NEW QUESTION 10
You are developing a project management service by using ASP.NET. The service hosts conversations, files, to-do lists, and a calendar that users can interact with at any time.
The application uses Azure Search for allowing users to search for keywords in the project data.
You need to implement code that creates the object which is used to create indexes in the Azure Search service.
Which two objects should you use? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A. SearchService
- B. SearchlndexCIient
- C. SearchServiceClient
- D. SearchCredentials
Answer: CD
NEW QUESTION 11
You implement Azure Redis Cache to allow .NET applications to store customer session data for cache clients. You have the following .NET Core class library. The class library defines lazyConnection as a static private variable as shown in the following code. (Line numbers are included for reference only.)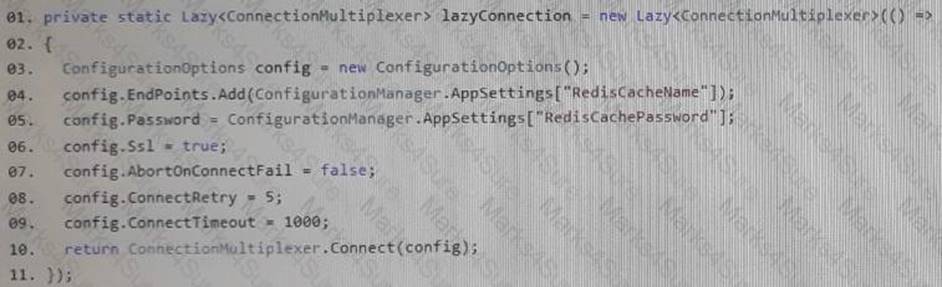
The method must update the database and invalidate the cache using the correct methods and parameters. Operations mus'&e performed asynchronously wherever possible. You must ensure that the operation in the client application does not result in another client retrieving stale cache data.
You need to implement the code.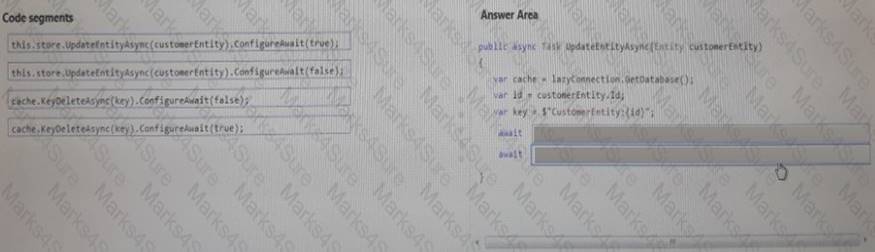
Answer:
Explanation: 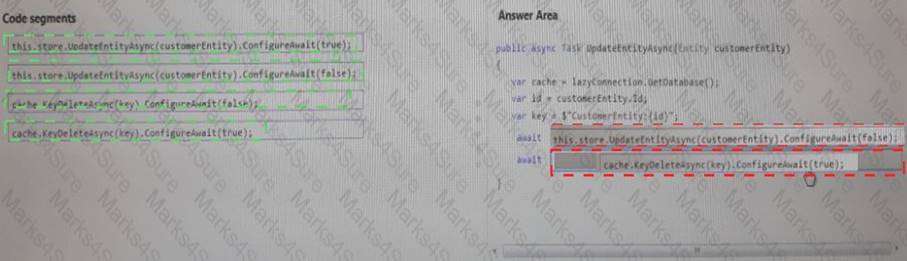
NEW QUESTION 12
You need to retrieve all order line items sorted alphabetically by the city.
How should you complete the code? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.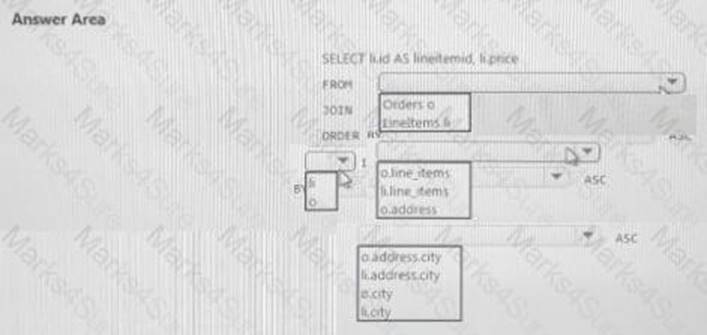
Answer:
Explanation: 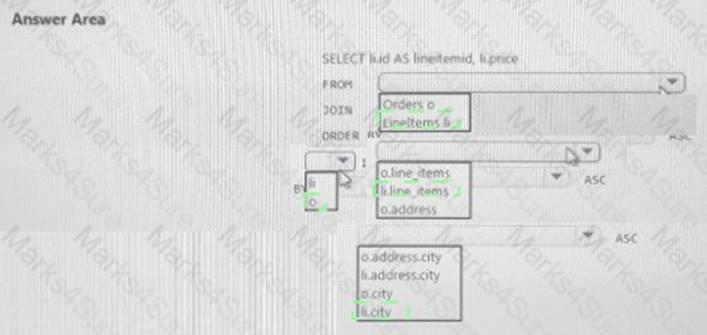
NEW QUESTION 13
You have a task that includes a WebJob that should run continuously. The WebJob Log exhibit shows the text that is displayed when the WebJob runs. (Click the WebJob Log tab.)
The WebJob is configured as shown in the WebJob Configuration exhibit. (Click the WebJob Configuration tab.)
The WebJob is not functioning as expected. The WebJob Code exhibit has a comment that shows where code should be added. (Click the WebJob Code tab.)
You need to identify any issues with the WebJob.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.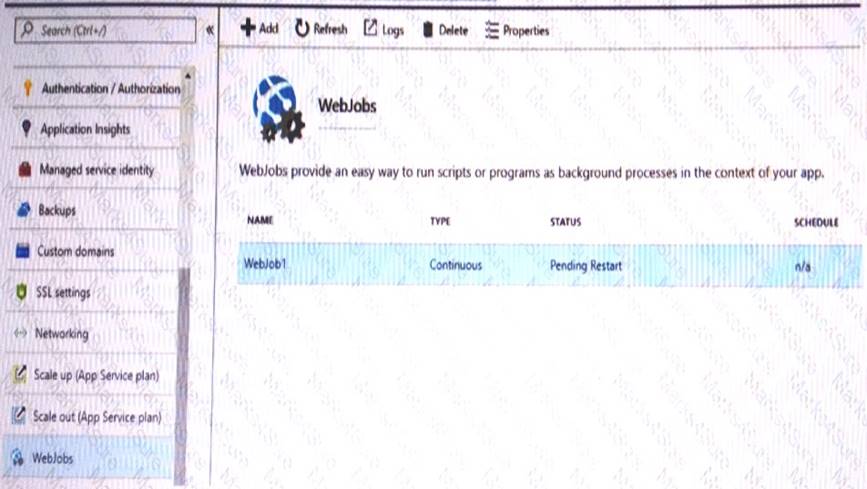
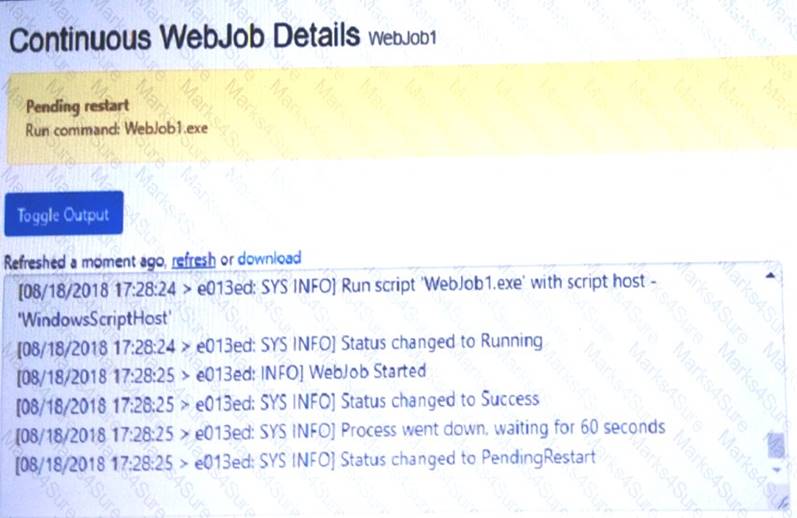
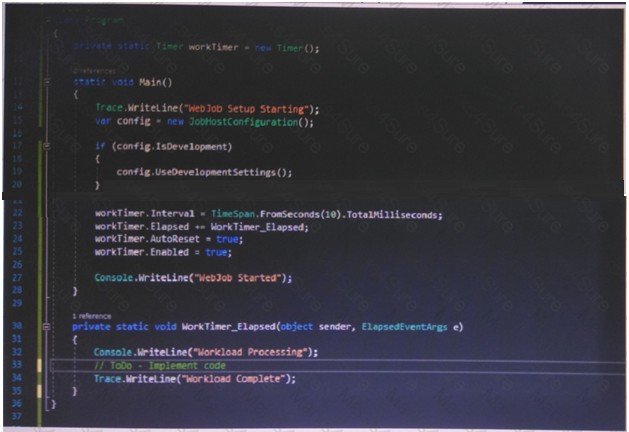

Answer:
Explanation: 
NEW QUESTION 14
You develop a website. You plan to host the website in Azure. You expect the website to experience high traffic volumes after it is published. You must ensure that the website remains available and responsive while minimizing cost. You need to deploy the website. What should you do?
- A. Deploy the website to an App Service that uses the Shared service tie
- B. Configure the App Service plan to automatically scale when the CPU load is high.
- C. Deploy the website to a virtual machin
- D. Configure the virtual machine to automatically scale when the CPU load is high.
- E. Deploy the website to an App Service that uses the Standard service tie
- F. Configure the App Service plan to automatically scale when the CPU load is high.
- G. Deploy the website to a virtual machin
- H. Configure a Scale Set to increase the virtual machine instance count when the CPU load
Answer: C
NEW QUESTION 15
You are developing an Azure web application to store and archive patient medical records in Azure. You need to configure data storage to meet the following policies:
• Ensure that you can configure a retention period for patient records.
• Archived data must be readable.
• Archived data must not be modified or deleted. Which Azure storage service should you use?
- A. Azure files
- B. Azure Blobs
- C. Azure Queues
- D. Azure Tables
Answer: C
NEW QUESTION 16
A company has an app that records and processes videos. New videos are recorded daily. The videos are displayed on the company website the day after they are recorded. The company runs several servers that process data and encode the videos. The processing servers use FFmpeg and proprietary software to encode and convert the videos.
The company plans to migrate the app to Azure. Azure Batch must be used to process videos. Each task must run a command and output the result to a file on a destination storage account.
You create and assign values to the following variables:
You are reviewing code to create tasks in Azure Batch. (Line numbers are included for reference only.)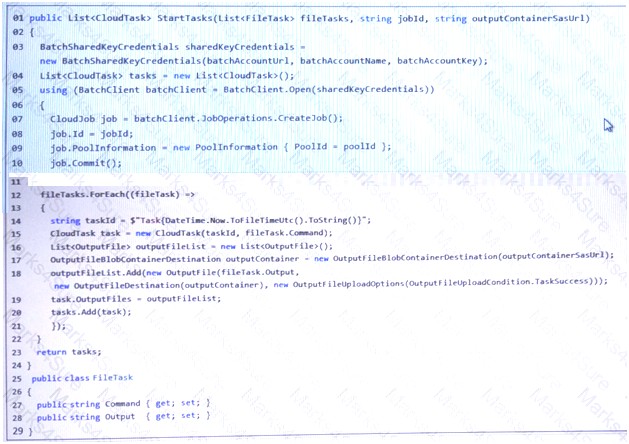
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.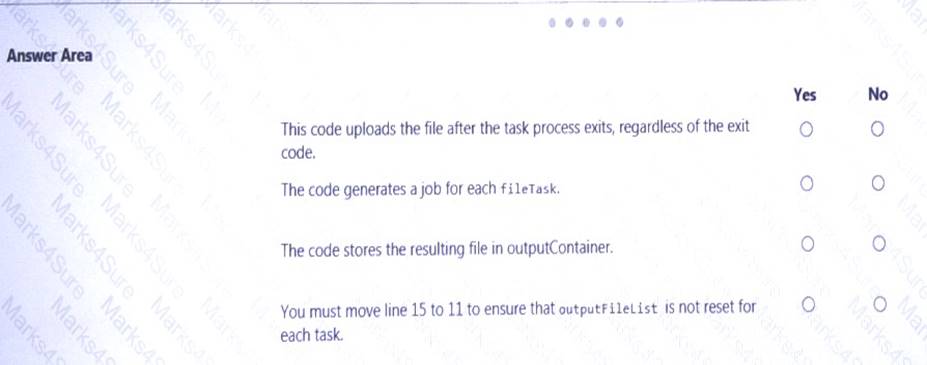
Answer:
Explanation: 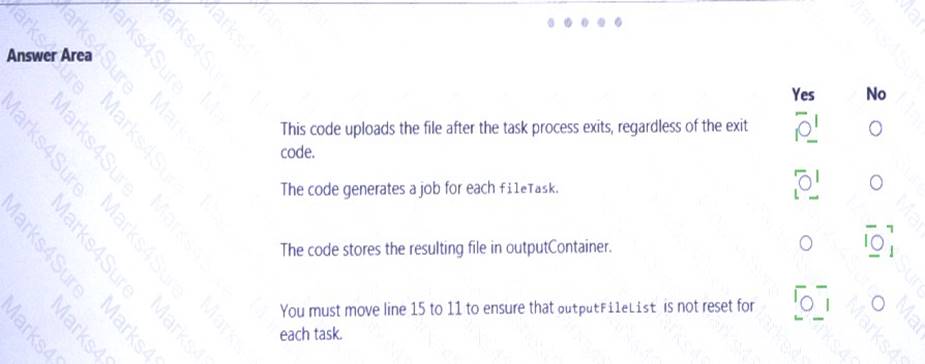
P.S. Easily pass AZ-202 Exam with 150 Q&As 2passeasy Dumps & pdf Version, Welcome to Download the Newest 2passeasy AZ-202 Dumps: https://www.2passeasy.com/dumps/AZ-202/ (150 New Questions)
