Proper study guides for Leading GIAC GIAC Certified Incident Handler certified begins with GIAC GCIH preparation products which designed to deliver the Certified GCIH questions by making you pass the GCIH test at your first time. Try the free GCIH demo right now.
Free GCIH Demo Online For GIAC Certifitcation:
NEW QUESTION 1
Which of the following provides packet-level encryption between hosts in a LAN?
- A. PPTP
- B. IPsec
- C. PFS
- D. Tunneling protocol
Answer: B
NEW QUESTION 2
Address Resolution Protocol (ARP) spoofing, also known as ARP poisoning or ARP Poison Routing (APR), is a technique used to attack an Ethernet wired or wireless network. ARP spoofing may allow an attacker to sniff data frames on a local area network (LAN), modify the traffic, or stop the traffic altogether. The principle of ARP spoofing is to send fake ARP messages to an Ethernet LAN. What steps can be used as a countermeasure of ARP spoofing?
Each correct answer represents a complete solution. Choose all that apply.
- A. Using smash guard utility
- B. Using ARP Guard utility
- C. Using static ARP entries on servers, workstation and routers
- D. Using ARP watch utility
- E. Using IDS Sensors to check continually for large amount of ARP traffic on local subnets
Answer: BCDE
NEW QUESTION 3
You work as a Network Administrator for Marioxnet Inc. You have the responsibility of handling two routers with BGP protocol for the enterprise's network. One of the two routers gets flooded with an unexpected number of data packets, while the other router starves with no packets reaching it. Which of the following attacks can be a potential cause of this?
- A. Packet manipulation
- B. Denial-of-Service
- C. Spoofing
- D. Eavesdropping
Answer: B
NEW QUESTION 4
Which of the following types of attacks come under the category of hacker attacks?
Each correct answer represents a complete solution. Choose all that apply.
- A. Smurf
- B. IP address spoofing
- C. Teardrop
- D. Password cracking
Answer: BD
NEW QUESTION 5
Adam works as a Network administrator for Umbrella Inc. He noticed that an ICMP ECHO requests is coming from some suspected outside sources. Adam suspects that some malicious hacker is trying to perform ping sweep attack on the network of the company. To stop this malicious activity, Adam blocks the ICMP ECHO request from any outside sources.
What will be the effect of the action taken by Adam?
- A. Network turns completely immune from the ping sweep attacks.
- B. Network is still vulnerable to ping sweep attack.
- C. Network is protected from the ping sweep attack until the next reboot of the server.
- D. Network is now vulnerable to Ping of death attack.
Answer: B
NEW QUESTION 6
Which of the following programs can be used to detect stealth port scans performed by a malicious hacker?
Each correct answer represents a complete solution. Choose all that apply.
- A. nmap
- B. scanlogd
- C. libnids
- D. portsentry
Answer: BCD
NEW QUESTION 7
Which of the following are open-source vulnerability scanners?
- A. Nessus
- B. Hackbot
- C. NetRecon
- D. Nikto
Answer: ABD
NEW QUESTION 8
Firewalking is a technique that can be used to gather information about a remote network protected by a firewall. This technique can be used effectively to perform information gathering attacks. In this technique, an attacker sends a crafted packet with a TTL value that is set to expire one hop past the firewall. Which of the following are pre-requisites for an attacker to conduct firewalking?
Each correct answer represents a complete solution. Choose all that apply.
- A. An attacker should know the IP address of a host located behind the firewall.
- B. ICMP packets leaving the network should be allowed.
- C. There should be a backdoor installed on the network.
- D. An attacker should know the IP address of the last known gateway before the firewall.
Answer: ABD
NEW QUESTION 9
Victor wants to send an encrypted message to his friend. He is using certain steganography technique to accomplish this task. He takes a cover object and changes it accordingly to hide information. This secret information is recovered only when the algorithm compares the changed cover with the original cover.
Which of the following Steganography methods is Victor using to accomplish the task?
- A. The distortion technique
- B. The spread spectrum technique
- C. The substitution technique
- D. The cover generation technique
Answer: A
NEW QUESTION 10
You want to add a netbus Trojan in the chess.exe game program so that you can gain remote access to a friend's computer. Which of the following tools will you use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
- A. Tripwire
- B. Yet Another Binder
- C. Pretator Wrapper
- D. Beast
Answer: BC
NEW QUESTION 11
Choose the items from the given list that are required to be in the response kit of an Incident Handler.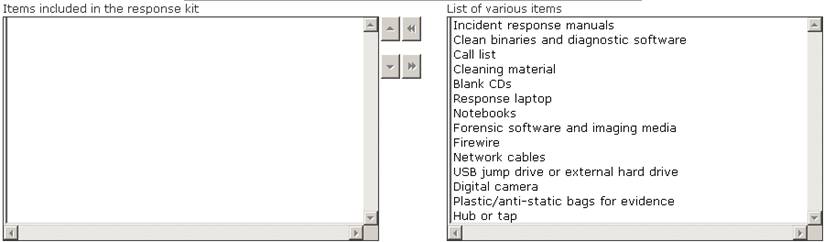
Solution:
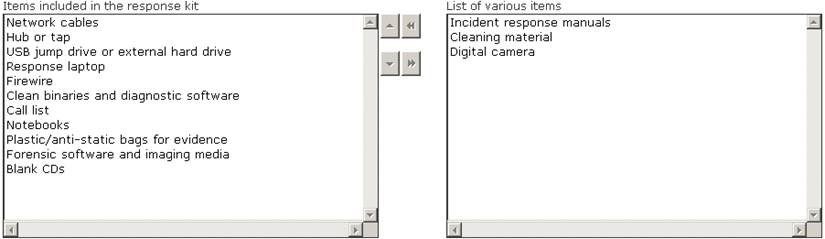
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 12
CORRECT TEXT
Fill in the blank with the appropriate term.
______ is a free Unix subsystem that runs on top of Windows.
- A.
Answer: Cygwin
NEW QUESTION 13
Which of the following IP packet elements is responsible for authentication while using IPSec?
- A. Authentication Header (AH)
- B. Layer 2 Tunneling Protocol (L2TP)
- C. Internet Key Exchange (IKE)
- D. Encapsulating Security Payload (ESP)
Answer: A
NEW QUESTION 14
Which of the following statements are true about a keylogger?
Each correct answer represents a complete solution. Choose all that apply.
- A. It records all keystrokes on the victim's computer in a predefined log file.
- B. It can be remotely installed on a computer system.
- C. It is a software tool used to trace all or specific activities of a user on a computer.
- D. It uses hidden code to destroy or scramble data on the hard disk.
Answer: ABC
NEW QUESTION 15
John works as a Penetration Tester in a security service providing firm named you-are-secure Inc. Recently, John's company has got a project to test the security of a promotional Website www.missatlanta.com and assigned the pen-testing work to John. When John is performing penetration testing, he inserts the following script in the search box at the company home page:
<script>alert('Hi, John')</script>
After pressing the search button, a pop-up box appears on his screen with the text - "Hi, John." Which of the following attacks can be performed on the Web site tested by john while considering the above scenario?
- A. Replay attack
- B. CSRF attack
- C. Buffer overflow attack
- D. XSS attack
Answer: D
NEW QUESTION 16
Which of the following ensures that a party to a dispute cannot deny the authenticity of their signature on a document or the sending of a message that they originated?
- A. OS fingerprinting
- B. Reconnaissance
- C. Non-repudiation
- D. Confidentiality
Answer: C
NEW QUESTION 17
Which of the following is a reason to implement security logging on a DNS server?
- A. For preventing malware attacks on a DNS server
- B. For measuring a DNS server's performance
- C. For monitoring unauthorized zone transfer
- D. For recording the number of queries resolved
Answer: C
NEW QUESTION 18
......
P.S. Easily pass GCIH Exam with 328 Q&As Dumpscollection.com Dumps & pdf Version, Welcome to Download the Newest Dumpscollection.com GCIH Dumps: https://www.dumpscollection.net/dumps/GCIH/ (328 New Questions)
