We provide 70 411 administering windows server 2012 r2 pdf in two formats. Download PDF & Practice Tests. Pass Microsoft 70-411 Exam quickly & easily. The 70-411 PDF type is available for reading and printing. You can print more and practice many times. With the help of our 70 411 exam dumps pdf product and material, you can easily pass the 70-411 exam.
Free demo questions for Microsoft 70-411 Exam Dumps Below:
NEW QUESTION 1
Your company has a main office and a branch office.
The network contains an Active Directory domain named contoso.com.
The main office contains a domain controller named DC1 that runs Windows Server 2012 R2. DC1 is a DNS server and hosts a primary zone for contoso.com. The branch office contains a member server named Server1 that runs Windows Server 2012 R2. Server1 is a DNS server and hosts a secondary zone for contoso.com.
The main office connects to the branch office by using an unreliable WAN link.
You need to ensure that Server1 can resolve names in contoso.com if the WAN link in unavailable for three days.
Which setting should you modify in the start of authority (SOA) record?
- A. Retry interval
- B. Refresh interval
- C. Expires after
- D. Minimum (default) TTL
Answer: C
Explanation: Used by other DNS servers that are configured to load and host the zone to determine when zone data expires if it is not renewed
NEW QUESTION 2
You deploy a Windows Server Update Services (WSUS) server named Server01.
You plan to use a Group Policy object (GPO) to configure all client computers to use Server01 as a Microsoft Update server and to assign the client computers to computer groups.
You need to ensure that the computers are assigned to the correct computer groups automatically when the GPO is deployed.
Which two actions should you perform before you deploy the GPO? Each correct answer presents part of the solution.
- A. From Windows PowerShell, run the Approve-WSUSUpdate cmdlet.
- B. From the Update Services console, modify the Computers option.
- C. From Windows PowerShell, run the Add-WSUSUComputer cmdlet.
- D. From the Update Services console, manually create the computer groups.
- E. From the Update Services console, modify the Products and Classifications options.
Answer: BD
Explanation: References:
https://technet.microsoft.com/en-us/library/dd939829(v=ws.10).aspx
NEW QUESTION 3
Your network contains an Active Directory domain named contoso.com. Network Policy Server (NPS) is deployed to the domain.
You plan to deploy Network Access Protection (NAP).
You need to configure the requirements that are validated on the NPS client computers. What should you do?
- A. From the Network Policy Server console, configure a network policy.
- B. From the Network Policy Server console, configure a health policy.
- C. From the Network Policy Server console, configure a Windows Security Health Validator (WSHV) policy.
- D. From a Group Policy object (GPO), configure the NAP Client Configuration security setting.
- E. From a Group Policy object (GPO), configure the Network Access Protection Administrative Templates setting.
Answer: C
NEW QUESTION 4
Your network contains a Hyper-V host named Server1 that hosts 20 virtual machines.
You need to view the amount of memory resources and processor resources each virtual machine uses currently.
Which tool should you use on Server1?
- A. Hyper-V Manager
- B. Task Manager
- C. Windows System Resource Manager (WSRM)
- D. Resource Monitor
Answer: A
NEW QUESTION 5
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Remote Access server role installed.
On Server1, you create a network policy named Policy1.
You need to configure Policy1 to ensure that users are added to a VLAN. Which attributes should you add to Policy1?
- A. Tunnel-Tag, Tunnel-Password, Tunnel-Medium-Type, and Tunnel-Preference
- B. Tunnel-Tag, Tunnel-Server-Auth-ID, Tunnel-Preference, and Tunnel-Pvt-Group-ID
- C. Tunnel-Type, Tunnel-Tag, Tunnel-Medium-Type, and Tunnel-Pvt-Group-ID
- D. Tunnel-Type, Tunnel-Password, Tunnel-Server-Auth-ID, and Tunnel-Pvt-Group-ID
Answer: C
Explanation: VLAN attributes used in network policy
When you use network hardware, such as routers, switches, and access controllers that support virtual local area networks (VLANs), you can configure Network Policy Server (NPS) network policy to instruct the access servers to place members of Active Directory® groups on VLANs.
Before configuring network policy in NPS for VLANs, create groups of users in Active Directory Domain Services (AD DS) that you want to assign to specific VLANs. Then when you run the New Network Policy wizard, add the Active Directory group as a condition of the network policy.
You can create a separate network policy for each group that you want to assign to a VLAN. For more information, see Create a Group for a Network Policy. When you configure network policy for use with VLANs, you must configure the RADIUS standard attributes Tunnel-Medium-Type, Tunnel-Pvt-Group-ID, and Tunnel-Type. Some hardware vendors also require the use of the RADIUS standard attribute Tunnel-Tag.
To configure these attributes in a network policy, use the New Network Policy wizard to create a network policy. You can add the attributes to the network policy settings while running the wizard or after you have successfully created a policy with the wizard.
✑ Tunnel-Medium-Type. Select a value appropriate to the previous selections you
made while running the New Network Policy wizard. For example, if the network policy you are configuring is a wireless policy, in Attribute Value, select 802 (Includes all 802 media plus Ethernet canonical format).
✑ Tunnel-Pvt-Group-ID. Enter the integer that represents the VLAN number to which
group members will be assigned. For example, if you want to create a Sales VLAN for your sales team by assigning team members to VLAN 4, type the number 4.
✑ Tunnel-Type. Select the value Virtual LANs (VLAN).
✑ Tunnel-Tag. Some hardware devices do not require this attribute. If your hardware device requires this attribute, obtain this value from your hardware documentation.
NEW QUESTION 6
Your network contains two Active Directory forests named contoso.com and dev.contoso.com. The contoso.com forest contains a domain controller named DC1. The dev.contoso.com forest contains a domain controller named DC2. Each domain contains an organizational unit (OU) named OU1.
Dev.contoso.com has a Group Policy object (GPO) named GPO1. GPO1 contains 200 settings, including several settings that have network paths. GPO1 is linked to OU1.
You need to copy GPO1 from dev.contoso.com to contoso.com. What should you do first on DC2?
- A. From the Group Policy Management console, right-click GPO1 and select Copy.
- B. Run the mtedit.exe command and specify the /Domaintcontoso.com /DC: DC 1 parameter.
- C. Run the Save-NetGpocmdlet.
- D. Run the Backup-Gpocmdlet.
Answer: A
Explanation: To copy a Group Policy object:
In the GPMC console tree, right-click the GPO that you want to copy, and then click Copy. To create a copy of the GPO in the same domain as the source GPO, right-click Group Policy objects, click Paste, specify permissions for the new GPO in the Copy GPO box, and then click OK.
For copy operations to another domain, you may need to specify a migration table.
The Migration Table Editor (MTE) is provided with Group Policy Management Console (GPMC) to facilitate the editing of migration tables. Migration tables are used for copying or importing Group Policy objects (GPOs) from one domain to another, in cases where the GPOs include domain-specific information that must be updated during copy or import. Source WS2008R2: Backup the existing GPOs from the GPMC, you need to ensure that the “Group Policy Objects” container is selected for the “Backup Up All” option to be available.
Copy a Group Policy Object with the Group Policy Management Console (GPMC)
You can copy a Group Policy object (GPO) either by using the drag-and-drop method or right-click method.
Applies To: Windows 8, Windows Server 2008 R2, Windows Server 2012
References:
http://technet.microsoft.com/en-us/library/cc785343(v=WS.10).aspx http://technet.microsoft.com/en-us/library/cc733107.aspx
NEW QUESTION 7
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Windows Deployment Services server role installed.
Server1 contains two boot images and four install images.
You need to ensure that when a computer starts from PXE, the available operating system images appear in a specific order.
What should you do?
- A. Modify the properties of the boot images.
- B. Create a new image group.
- C. Modify the properties of the install images.
- D. Modify the PXE Response Policy.
Answer: C
NEW QUESTION 8
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2.
You create an Active Directory snapshot of DC1 each day.
You need to view the contents of an Active Directory snapshot from two days ago. What should you do first?
- A. Run the dsamain.exe command.
- B. Stop the Active Directory Domain Services (AD DS) service.
- C. Start the Volume Shadow Copy Service (VSS).
- D. Run the ntdsutil.exe command.
Answer: A
Explanation: Dsamain.exe exposes Active Directory data that is stored in a snapshot or backup as a Lightweight Directory Access Protocol (LDAP) server.
Reference: http://technet.microsoft.com/en-us/library/cc772168.aspx
NEW QUESTION 9
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2.
You have a Group Policy object (GPO) named GPO1 that contains hundreds of settings. GPO1 is linked to an organizational unit (OU) named OU1. OU1 contains 200 client computers.
You plan to unlink GPO1 from OU1.
You need to identify which GPO settings will be removed from the computers after GPO1 is unlinked from OU1.
Which two GPO settings should you identify? (Each correct answer presents part of the solution. Choose two.)
- A. The managed Administrative Template settings
- B. The unmanaged Administrative Template settings
- C. The System Services security settings
- D. The Event Log security settings
- E. The Restricted Groups security settings
Answer: AD
Explanation: There are two kinds of Administrative Template policy settings: Managed and Unmanaged . The Group Policy service governs Managed policy settings and removes a policy setting when it is no longer within scope of the user or computer.
References:
http: //technet. microsoft. com/en-us/library/cc778402(v=ws. 10). aspx http: //technet. microsoft. com/en-us/library/bb964258. aspx
NEW QUESTION 10
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2. Server1 has the Network Policy Server server role installed. Server2 has the DHCP Server server role installed. Both servers run Windows Server 2012 R2.
You are configuring Network Access Protection (NAP) to use DHCP enforcement. You configure a DHCP scope as shown in the exhibit. (Click the Exhibit button.)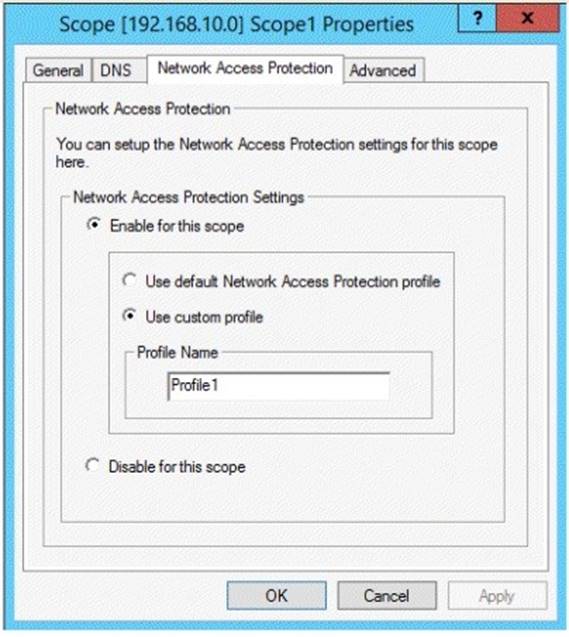
You need to ensure that non-compliant NAP clients receive different DHCP options than compliant NAP clients.
What should you configure on each server? To answer, select the appropriate options for each server in the answer area.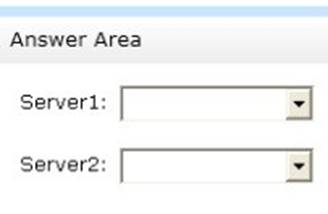

Answer:
Explanation: Health Policies Server Options
* Health policy on the NAP server.
* The DHCP server must be NAP enabled.
Note: With DHCP enforcement, a computer must be compliant to obtain an unlimited access IP address configuration from a DHCP server. For noncompliant computers, network access is limited by an IP address configuration that allows access only to the restricted network. DHCP enforcement enforces health policy requirements every time a DHCP client attempts to lease or renew an IP address configuration. DHCP enforcement also actively monitors the health status of the NAP client and renews the IPv4 address configuration for access only to the restricted network if the client becomes noncompliant.
Topic 2, Exam Set B
NEW QUESTION 11
Your network contains a Network Policy Server (NPS) server named Server1. The network contains a server named SQL1 that has Microsoft SQL Server 2008 R2 installed. All servers run Windows Server 2012 R2.
You configure NPS on Server1 to log accounting data to a database on SQL1.
You need to ensure that the accounting data is captured if SQL1 fails. The solution must minimize cost.
What should you do?
- A. Implement Failover Clustering.
- B. Implement database mirroring.
- C. Run the Accounting Configuration Wizard.
- D. Modify the SQL Server Logging properties.
Answer: C
Explanation: In Windows Server 2008 R2, an accounting configuration wizard is added to the Accounting node in the NPS console. By using the Accounting Configuration wizard, you
can configure the following four accounting settings:
✑ SQL logging only. By using this setting, you can configure a data link to a SQL Server that allows NPS to connect to and send accounting data to the SQL server. In addition, the wizard can configure the database on the SQL Server to ensure that the database is compatible with NPS SQL server logging.
✑ Text logging only. By using this setting, you can configure NPS to log accounting data to a text file.
✑ Parallel logging. By using this setting, you can configure the SQL Server data link and database. You can also configure text file logging so that NPS logs simultaneously to the text file and the SQL Server database.
✑ SQL logging with backup. By using this setting, you can configure the SQL Server data link and database. In addition, you can configure text file logging that NPS uses if SQL Server logging fails.
NEW QUESTION 12
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2.
You enable and configure Routing and Remote Access (RRAS) on Server1. You create a user account named User1.
You need to ensure that User1 can establish VPN connections to Server1. What should you do?
- A. Modify the members of the Remote Management Users group.
- B. Add a RADIUS client.
- C. Modify the Dial-in setting of User1.
- D. Create a connection request policy.
Answer: C
Explanation: Access permission is also granted or denied based on the dial-in properties of each user account.
http://technet.microsoft.com/en-us/library/cc772123.aspx
NEW QUESTION 13
Your network contains an Active Directory domain named contoso.com. The domain contains a member server named Server1. Server1 runs Windows Server 2012 R2 and has the Hyper-V server role installed.
Server1 hosts 10 virtual machines. A virtual machine named VM1 runs Windows Server 2012 R2 and hosts a processor-intensive application named App1.
Users report that App1 responds more slowly than expected.
You need to monitor the processor usage on VM1 to identify whether changes must be made to the hardware settings of VM1.
Which performance object should you monitor on Server1?
- A. Processor
- B. Hyper-V Hypervisor Virtual Processor
- C. Hyper-V Hypervisor Logical Processor
- D. Hyper-V Hypervisor Root Virtual Processor
- E. Process
Answer: C
Explanation: In the simplest way of thinking the virtual processor time is cycled across the available logical processors in a round-robin type of fashion. Thus all the processing power gets used over time, and technically nothing ever sits idle.
To accurately measure the processor utilization of a guest operating system, use the “Hyper-V Hypervisor Logical Processor (Total)% Total Run Time” performance monitor counter on the Hyper-V host operating system.
NEW QUESTION 14
HOTSPOT
Your network contains an Active Directory domain named contoso.com.
You have several Windows PowerShell scripts that execute when users log on to their client computer.
You need to ensure that all of the scripts execute completely before the users can access their desktop.
Which setting should you configure? To answer, select the appropriate setting in the answer area.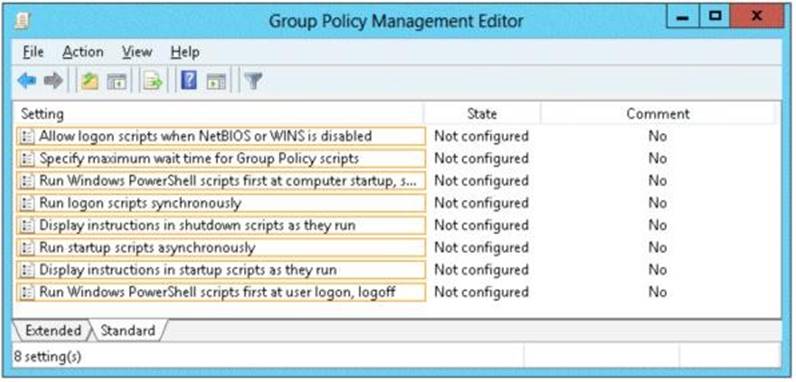
Answer:
Explanation: http: //technet. microsoft. com/en-us/library/cc738773(v=ws. 10). aspx Run logon scripts synchronously
Directs the system to wait for logon scripts to finish running before it starts the Windows Explorer interface program and creates the desktop.
If you enable this policy, Windows Explorer does not start until the logon scripts have finished running. This setting assures that logon script processing is complete before the user starts working, but it can delay the appearance of the desktop.
If you disable this policy or do not configure it, the logon scripts and Windows Explorer are not synchronized and can run simultaneously.
NEW QUESTION 15
DRAG DROP
Your network contains an Active Directory forest named contoso.com. All domain controllers run Windows Server 2008 R2.
The schema is upgraded to Windows Server 2012 R2.
Contoso.com contains two servers. The servers are configured as shown in the following table.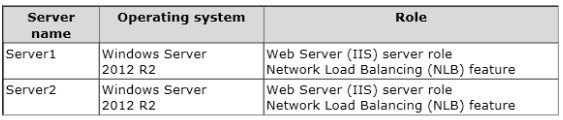
Server1 and Server2 host a load-balanced application pool named AppPool1.
You need to ensure that AppPool1 uses a group Managed Service Account as its identity. Which three actions should you perform?
To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.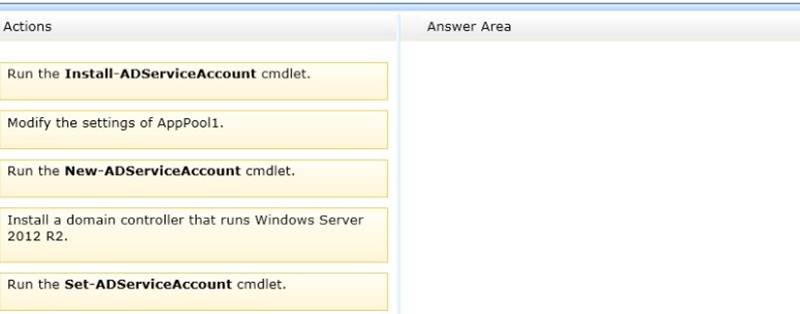
Answer:
Explanation: Note: Box 1:
Group Managed Service Accounts Requirements:
At least one Windows Server 2012 Domain Controller
A Windows Server 2012 or Windows 8 machine with the ActiveDirectory PowerShell module, to create/manage the gMSA.
A Windows Server 2012 or Windows 8 domain member to run/use the gMSA. Box 2:
To create a new managed service account
✑ On the domain controller, click Start, and then click Run. In the Open box, type dsa. msc, and then click OK to open the Active Directory Users and Computers snap-in. Confirm that the Managed Service Account container exists.
✑ Click Start, click All Programs, click Windows PowerShell 2.0, and then click the Windows PowerShell icon.
✑ Run the following command: New-ADServiceAccount [- SAMAccountName<String>] [-Path <String>].
Box 3:
Configure a service account for Internet Information Services
Organizations that want to enhance the isolation of IIS applications can configure IIS application pools to run managed service accounts.
To use the Internet Information Services (IIS) Manager snap-in to configure a service to use a managed service account
✑ Click Start, point to Administrative Tools, and then click Internet Information
Services (IIS) Manager.
✑ Double-click <Computer name>, double-click Application Pools, right-click <Pool
Name>, and click Advanced Settings.
✑ In the Identity box, click …, click Custom Account, and then click Set.
✑ Type the name of the managed service account in the format domainnameaccountname.
NEW QUESTION 16
HOTSPOT
Your network contains one Active Directory domain named contoso.com. The domain contains two servers named Server01 and Server02 that run Windows Server 2012 R2.
Server01 is a member of a Distributed File System (DFS) replication group named RG01 that replicates to a folder named RF01.
You plan to replicate RF01 to Server02. RF01 will be pre-staged on Server02. You need export the DFS files and the DFS database from Server01.
Which tools should you use? To answer, select the appropriate options in the answer area.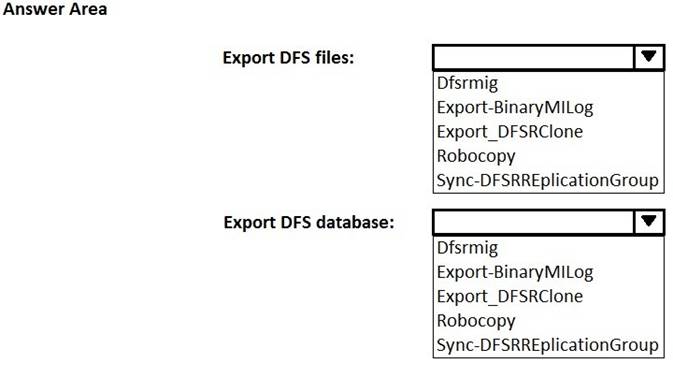
Answer:
Explanation: References: https://technet.microsoft.com/en-us/library/dn495044(v=ws.11).aspx https://technet.microsoft.com/en-us/library/dn482443(v=ws.11).aspx
NEW QUESTION 17
Your network contains an Active Directory forest. The forest contains two domains named contoso.com and fabrikam.com. All of the DNS servers in both of the domains run Windows Server 2012 R2.
The network contains two servers named Server1 and Server2. Server1 hosts an Active Directory-integrated zone for contoso.com. Server2 hosts an Active Directory-integrated zone for fabrikam.com. Server1 and Server2 connect to each other by using a WAN link.
Client computers that connect to Server1 for name resolution cannot resolve names in fabrikam.com.
You need to configure Server1 to resolve names in fabrikam.com. The solution must NOT require that changes be made to the fabrikam.com zone on Server2.
What should you create?
- A. A trust anchor
- B. A stub zone
- C. A zone delegation
- D. A secondary zone
Answer: B
Explanation: A stub zone is a copy of a zone that contains only those resource records necessary to identify the authoritative Domain Name System (DNS) servers for that zone. A stub zone is used to resolve names between separate DNS namespaces. This type of resolution may be necessary when a corporate merger requires that the DNS servers for two separate DNS namespaces resolve names for clients in both namespaces.
NEW QUESTION 18
You have a server named Server1 that runs Windows Server 2012 R2. You create a Data Collector Set (DCS) named DCS1.
You need to configure DCS1 to log data to D:logs.
What should you do?
- A. Right-click DCS1 and click Properties.
- B. Right-click DCS1 and click Export list.
- C. Right-click DCS1 and click Data Manager.
- D. Right-click DCS1 and click Save template.
Answer: A
Explanation: The Root Directory will contain data collected by the Data Collector Set. Change this setting if you want to store your Data Collector Set data in a different location than the default. Browse to and select the directory, or type the directory name.
To view or modify the properties of a Data Collector Set after it has been created, you can:
* Select the Open properties for this data collector set check box at the end of the Data Collector Set Creation Wizard.
* Right-click the name of a Data Collector Set, either in the MMC scope tree or in the console window, and click Properties in the context menu.
Directory tab:
In addition to defining a root directory for storing Data Collector Set data, you can specify a single Subdirectory or create a Subdirectory name format by clicking the arrow to the right of the text entry field.
NEW QUESTION 19
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains 30 user accounts that are used for network administration. The user accounts are members of a domain global group named Group1.
You identify the security requirements for the 30 user accounts as shown in the following table.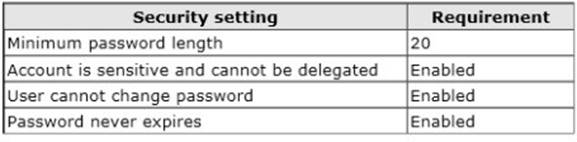
You need to identify which settings must be implemented by using a Password Settings object (PSO) and which settings must be implemented by modifying the properties of the user accounts.
What should you identify? To answer, configure the appropriate settings in the dialog box in the answer area.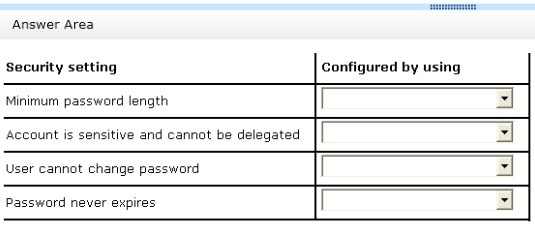
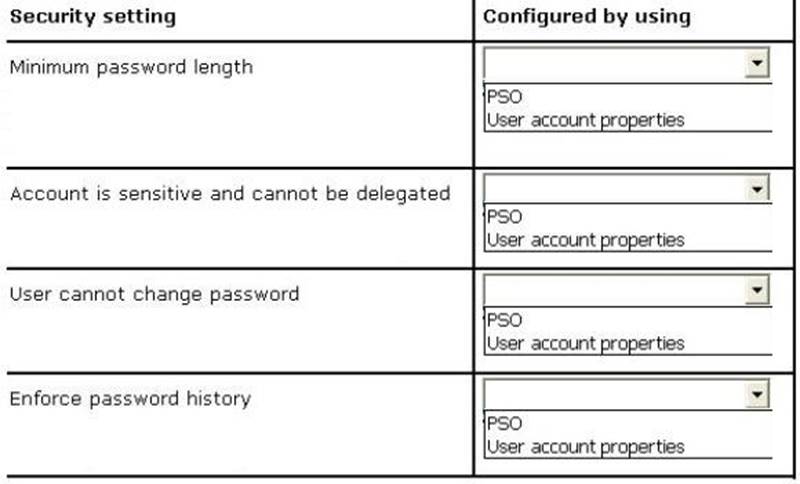
Answer:
Explanation: Box 1: PSO
Box 2: User Account Properties Box 3: User Account Properties Box 4: PSO
Note:
* Password Setting Object (PSO) is another name for Fine Grain Password Policies.
* Here you can see all the settings that go into a PSO.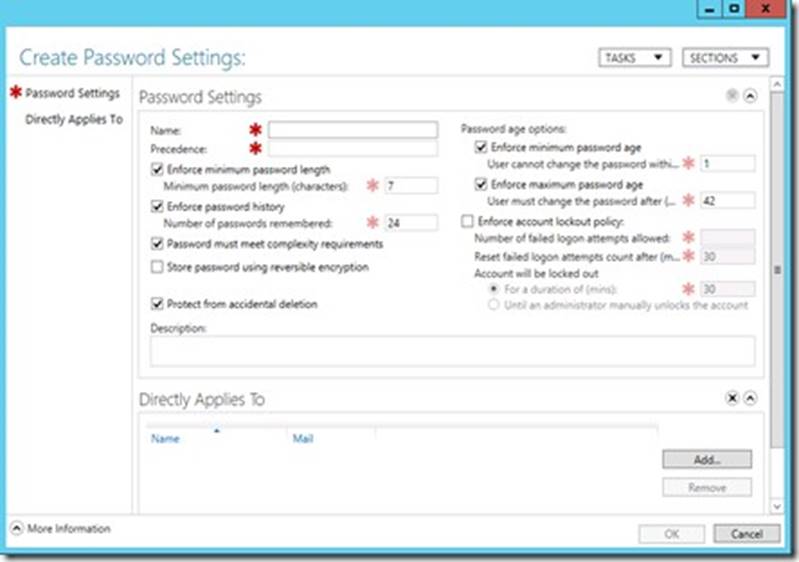
NEW QUESTION 20
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the File Server Resource Manager role service installed.
Each time a user receives an access-denied message after attempting to access a folder on Server1, an email notification is sent to a distribution list named DL1.
You create a folder named Folder1 on Server1, and then you configure custom NTFS permissions for Folder1.
You need to ensure that when a user receives an access-denied message while attempting to access Folder1, an email notification is sent to a distribution list named DL2. The solution must not prevent DL1 from receiving notifications about other access-denied messages.
What should you do?
- A. From Server Manager, run the New Share Wizard to create a share for Folder1 by selecting the SMB Share - Advanced option.
- B. From the File Server Resource Manager console, modify the Access-Denied Assistance settings.
- C. From the File Server Resource Manager console, modify the Email Notifications settings.
- D. From Server Manager, run the New Share Wizard to create a share for Folder1 by selecting the SMB Share -Applications option.
Answer: A
Explanation: When using the email model each of the file shares, you can determine whether access requests to each file share will be received by the administrator, a distribution list that represents the file share owners, or both.
The owner distribution list is configured by using the SMB Share – Advanced file share profile in the New Share Wizard in Server Manager.
100% Valid and Newest Version 70-411 Questions & Answers shared by prep-labs.com, Get Full Dumps HERE: https://www.prep-labs.com/dumps/70-411/ (New 294 Q&As)
