It is more faster and easier to pass the GIAC GCIA exam by using Accurate GIAC GIAC Certified Intrusion Analyst questuins and answers. Immediate access to the Down to date GCIA Exam and find the same core area GCIA questions with professionally verified answers, then PASS your exam with a high score now.
Also have GCIA free dumps questions for you:
NEW QUESTION 1
Which of the following NETSH commands for interface Internet protocol version 4 (IPv4) is used to add a DNS server to a list of DNS servers for a specified interface?
- A. net dnsserver
- B. add address
- C. add dnsserver
- D. add neighbors
Answer: C
NEW QUESTION 2
Which of the following switches is used with Pslist command on the command line to show the statistics for all active threads on the system, grouping these threads with their owning process?
- A. Pslist -x
- B. Pslist -m
- C. Pslist -t
- D. Pslist -d
Answer: D
NEW QUESTION 3
Andrew, a bachelor student of Faulkner University, creates a gmail account. He uses 'Faulkner' as the password for the gmail account. After a few days, he starts receiving a lot of e-mails stating that his gmail account has been hacked. He also finds that some of his important mails have been deleted by someone. Which of the following methods has the attacker used to crack Andrew's password?
Each correct answer represents a complete solution. Choose all that apply.
- A. Zero-day attack
- B. Dictionary-based attack
- C. Rainbow attack
- D. Denial-of-service (DoS) attack
- E. Brute force attack
- F. Buffer-overflow attack
- G. Password guessing
- H. Social engineering
Answer: BCEGH
NEW QUESTION 4
Which of the following is a signature-based intrusion detection system (IDS) ?
- A. Snort
- B. StealthWatch
- C. RealSecure
- D. Tripwire
Answer: A
NEW QUESTION 5
The following output is generated by running the show ip route command:
RouterA#show ip route
< - - Output Omitted for brevity - -> 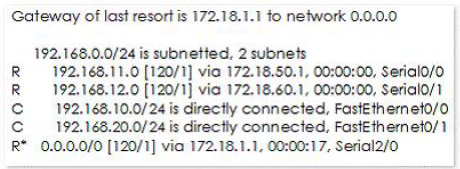
Which next hop address will RouterA use in forwarding traffic to 10.10.100.0/24?
- A. 172.18.50.1
- B. 192.168.10.0
- C. 172.18.1.1
- D. 172.18.60.1
Answer: C
NEW QUESTION 6
Which of the following password cracking tools can work on the Unix and Linux environment?
- A. Brutus
- B. John the Ripper
- C. Cain and Abel
- D. Ophcrack
Answer: B
NEW QUESTION 7
Which of the following is a correct sequence of different layers of Open System Interconnection (OSI) model?
- A. Physical layer, data link layer, network layer, transport layer, session layer, presentation layer, and application layer
- B. Physical layer, data link layer, network layer, transport layer, presentation layer, session layer, and application layer
- C. application layer, presentation layer, network layer, transport layer, session layer, data link layer, and physical layer
- D. Physical layer, network layer, transport layer, data link layer, session layer, presentation layer, and application layer
Answer: A
NEW QUESTION 8
You work as a Security Professional for CertLeader Inc. The company has a Linux-based network. You want to analyze the network traffic with Snort. You run the following command:
snort -v -i eth 0
Which of the following information will you get using the above command?
Each correct answer represents a complete solution. Choose all that apply.
- A. Protocol statistics
- B. Date stamp on the packets
- C. Number of packets received and dropped
- D. Application layer data
Answer: ABC
NEW QUESTION 9
Which of the following distributes incorrect IP address to divert the traffic?
- A. IP spoofing
- B. Domain name server (DNS) poisoning
- C. Reverse Address Resolution Protocol
- D. Route table poisoning
Answer: B
NEW QUESTION 10
An attacker wants to launch an attack on a wired Ethernet. He wants to accomplish the following tasks:
Sniff data frames on a local area network.
Modify the network traffic.
Stop the network traffic frequently.
Which of the following techniques will the attacker use to accomplish the task?
- A. IP spoofing
- B. Eavesdropping
- C. ARP spoofing
- D. Session hijacking
Answer: C
NEW QUESTION 11
What does a firewall check to prevent certain ports and applications from getting the packets into an Enterprise?
- A. The application layer port numbers and the transport layer headers
- B. The presentation layer headers and the session layer port numbers
- C. The network layer headers and the session layer port numbers
- D. The transport layer port numbers and the application layer headers
Answer: D
NEW QUESTION 12
Distributed Checksum Clearinghouse (DCC) is a hash sharing method of spam email detection.
Which of the following protocols does the DCC use?
- A. TCP
- B. TELNET
- C. ICMP
- D. UDP
Answer: D
NEW QUESTION 13
Which of the following intrusion detection systems (IDS) produces the false alarm because of the abnormal behavior of users and network?
- A. Application protocol-based intrusion detection system (APIDS)
- B. Protocol-based intrusion detection system (PIDS)
- C. Network intrusion detection system (NIDS)
- D. Host-based intrusion detection system (HIDS)
Answer: D
NEW QUESTION 14
Which of the following image file formats uses a lossy data compression technique?
- A. GIF
- B. JPG
- C. PNG
- D. TIF
Answer: B
NEW QUESTION 15
Which of the following commands in MQC tool matches IPv4 and IPv6 packets when IP parameter is missing?
- A. Match access-group
- B. Match fr-dlci
- C. Match IP precedence
- D. Match cos
Answer: C
NEW QUESTION 16
Peter, a malicious hacker, wants to perform an attack. He first compromises computers distributed across the internet and then installs specialized software on these computers. He then instructs the compromised hosts to execute the attack. Every host can then be used to launch its own attack on the target computers. Which of the following attacks is Peter performing?
- A. Ping of Death attack
- B. DDoS attack
- C. SYN flood attack
- D. Teardrop attack
Answer: B
NEW QUESTION 17
Which of the following is the default port for POP3?
- A. 21
- B. 110
- C. 80
- D. 25
Answer: B
NEW QUESTION 18
You work as a Network Administrator for McRobert Inc. Your company has a TCP/IP-based network. You want to get the protocol statistics and the active TCP/IP network connections of your computer. Which of the following will you use?
- A. IPSTAT
- B. SNMP
- C. ARP
- D. NBTSTAT
- E. NETSTAT
Answer: E
NEW QUESTION 19
Maria works as the Chief Security Officer for CertLeader Inc. She wants to send secret messages to the CEO of the company. To secure these messages, she uses a technique of hiding a secret message within an ordinary message. The technique provides 'security through obscurity'. What technique is Maria using?
- A. Encryption
- B. Public-key cryptography
- C. Steganography
- D. RSA algorithm
Answer: C
NEW QUESTION 20
ORRECT TEXT
Fill in the blank with the appropriate term.
___________is the practice of monitoring and potentially restricting the flow of information outbound from one network to another
- A. Egress filtering
Answer: A
NEW QUESTION 21
......
Recommend!! Get the Full GCIA dumps in VCE and PDF From Dumps-hub.com, Welcome to Download: https://www.dumps-hub.com/GCIA-dumps.html (New 508 Q&As Version)
