Your success in Cisco 350-501 is our sole target and we develop all our 350-501 braindumps in a way that facilitates the attainment of this target. Not only is our 350-501 study material the best you can find, it is also the most detailed and the most updated. 350-501 Practice Exams for Cisco Cisco Other Exam 350-501 are written to the highest standards of technical accuracy.
Online Cisco 350-501 free dumps demo Below:
NEW QUESTION 1
Refer to the exhibit. This output is included at the end of an output that was provided by a device using NETCONF. What does the code show?
- A. It shows that the full configuration is being modeled by YANG.
- B. It shows NETCONF uses remote procedure calls.
- C. It shows the hostname of the device as rpc-reply.
- D. It shows that the running configuration is blank.
Answer: B
NEW QUESTION 2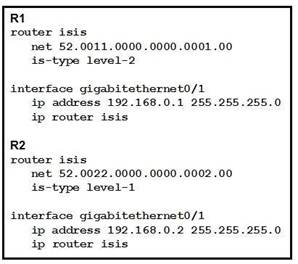
Refer to the exhibit. Which statement about the status of the neighbor relationship between R1 and R2 is true?
- A. The neighbor relationship is down because the two routers are configured with different area types.
- B. The neighbor relationship is down because the two routers are in the same subnet.
- C. The neighbor relationship is up because R2 is level 1 and Ievel 2 router.
- D. The neighbor relationship is down because R2 is operating as a Level 1 router and the two routers are in different areas.
Answer: A
NEW QUESTION 3
A customer of an ISP requests support to setup a BGP routing policy. Which BGP attribute should be configured to choose specific BGP speakers as preferred points for the customer AS?
- A. lowest multi-exit discriminator
- B. highest local preference outbound
- C. lowest local preference inbound
- D. highest local preference inbound
Answer: B
NEW QUESTION 4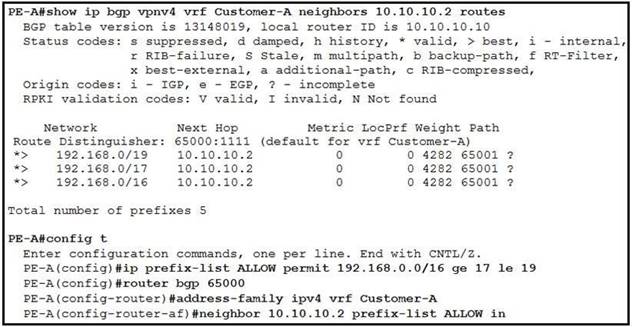
Refer to the exhibit. Which three outcomes occur if the prefix list is added to the neighbor? (Choose three.)
- A. 192.168.0.0/16 is denied.
- B. 192.168.0.0/16 is permitted.
- C. 192.168.0.0/19 is permitted
- D. 192.168.0.0/19 is denied.
- E. 192.168.0.0/17 is permitted
- F. 192.168.0.0/17 is denied.
Answer: ACF
NEW QUESTION 5
How much must the MTU be increased when configuring the 802.1q VLAN tag?
- A. 2 bytes
- B. 4 bytes
- C. 8 bytes
- D. 12 bytes
Answer: B
NEW QUESTION 6
Which service is a VNF role?
- A. Network
- B. Firewall
- C. Storage
- D. Compute
Answer: A
NEW QUESTION 7
Which utility can you use to locate MPLS faults?
- A. MPLS LSP ping
- B. QoS
- C. MPLS traceroute
- D. EEM
Answer: C
NEW QUESTION 8
How can a network administrator secure rest APIs?
- A. They can have a general administrator login for multiple users to access that has command entries logged.
- B. They can authenticate user sessions and provide the appropriate privilege level.
- C. They can ensure that user sessions are authenticated using TACACS+ only.
- D. They can allow read and write privileges to all users.
Answer: B
NEW QUESTION 9
A regional MPLS VPN provider operates in two regions and wants to provide MPLS L3VPN service for a customer with two sites in these separate locations. The VPN provider approaches another organization to provide backbone carrier services so that the provider can connect to these two locations.
Which statement about this scenario is true?
- A. When edge routers at different regional sites are connected over the global carrier backbone, MP-eBGP must run between the routers to exchange the customer VPNv4 routes.
- B. When eBGP is used for label exchange using the send-label option, MPLS-BGP forwarding is configured under the global ABC CSC PE-to-CE interface.
- C. When BGP is used for both route and label exchange, the neighbor a.b.c.d send-label command is used under the address-family VPNv4 command mode.
- D. When IGP is used for route exchange and LDP for label exchange, MPLS is enabled only on the VRF interface on the backbone-carrier PE side.
Answer: B
NEW QUESTION 10
Refer to the exhibit Which effect of this configuration is true?
- A. R1 can support a peer that is configured for LDP SSO/NSF as the peer recovers from an outage.
- B. R1can support a graceful restart operation on the peer, even if graceful restart is disabled on the peer.
- C. R1 can failover to any peer.
- D. R1 can failover only to a peer that is configured for LDF SSO/NSF.
Answer: A
NEW QUESTION 11
Which statement about segment routing prefix segments is true?
- A. It is the longest path to a node.
- B. It is linked to an adjacency SID that is globally unique within the router.
- C. It is linked to a prefix SID that is globally unique within segment routing domain.
- D. It requires using EIGRP to operate.
Answer: C
NEW QUESTION 12
Refer to the exhibit. Router 1 was experiencing a DDoS attack that was traced to interface gigabitethernet0/1. Which statement about this configuration is true?
- A. Router 1 accepts all traffic that ingresses and egresses interface gigabitethernet0/1.
- B. Router 1 drops all traffic that ingresses interface gigabitethernet0/1 that has a FIB entry that exits a different interface.
- C. Router 1 accepts source addresses that have a match in the FIB that indicates it is reachable through a real interface.
- D. Router 1 accepts source addresses on interface gigabitethernet0/1 that are private addresses.
Answer: C
NEW QUESTION 13
Refer to the exhibit. A network administrator wants to enhance the security for SNMP for this configuration. Which action can the network administrator implement?
- A. Add a community string to the existing entry.
- B. Maintain the configuration but switch to an encrypted password for device access through SSH.
- C. Re-configure to use SNMPv2 with MD5 authentication.
- D. Re-configure to use SNMPv3.
Answer: D
NEW QUESTION 14
Refer to the exhibit. Which statement describes the effect of this configuration?
- A. It matches HTTP traffic for use in a policy map.
- B. It applies a service policy to all interfaces remarking HTTP traffic.
- C. It creates an ACL named WEB that filters HTTP traffic.
- D. It modifies the default policy map to allow all HTTP traffic through the router.
Answer: A
NEW QUESTION 15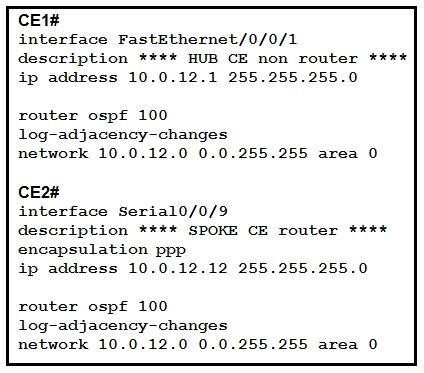
Refer to the exhibit. A network engineer is configuring customer edge routers to finalize a L2VPN over MPLS deployment. Assume that the AToM L2VPN service that connects the two CEs is configured correctly on the service provider network.
Which action causes the solution to fail?
- A. OSPF does not work with L2VPN services.
- B. The routing protocol network types are not compatible.
- C. A loopback with a /32 IP address has not been used.
- D. The xconnect statement has not been defined.
Answer: B
NEW QUESTION 16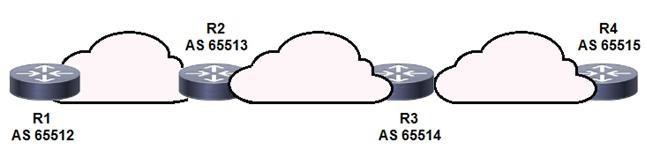
Refer to the exhibit. BGPsec is implemented on R1, R2, R3, and R4. BGP peering is established between neighboring autonomous systems. Which statement about implementation is true?
- A. BGP updates from the iBGP peers are appended with a community of local-as.
- B. BGP updates from the all BGP peers are appended with a community of no-export.
- C. BGP updates from the eBGP peers are appended with an additional AS path value that is statically set by the domain administrator.
- D. BGP updates from the eBGP peers are appended with a BGPsec attribute sequence that includes a public key hash and digital signature.
Answer: D
NEW QUESTION 17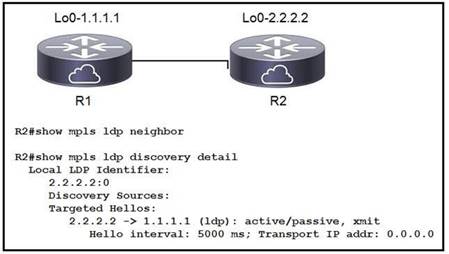
Refer to the exhibit. When implementing an LDP protocol, an engineer experienced an issue between two directly connected routers and noticed that no LDP neighbor exists for 1.1.1.1. Which factor should be the reason for this situation?
- A. LDP needs to be enabled on the R2 loopback interface.
- B. LDP needs to be enabled on the R2 physical interface.
- C. R2 does not see any hellos from R1.
- D. R2 sees the wrong type of hellos from R1.
Answer: B
NEW QUESTION 18
An engineer is setting up overlapping VPNs to allow VRF ABC and XYZ to communicate with VRF CENTRAL but wants to make sure that VRF ABC and XYZ cannot communicate. Which configuration accomplishes these objectives?
- A.
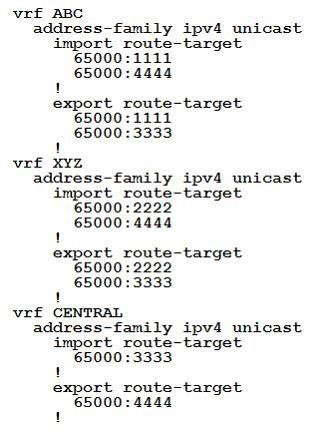
- B.
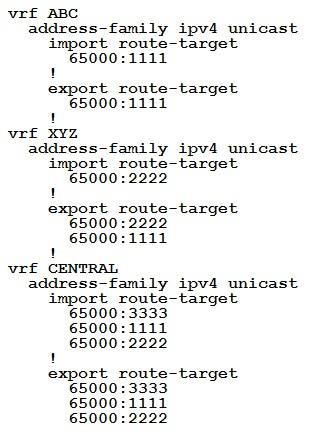
- C.
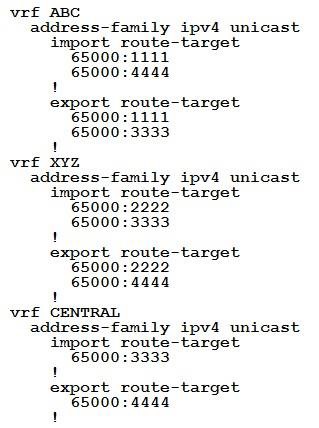
- D.
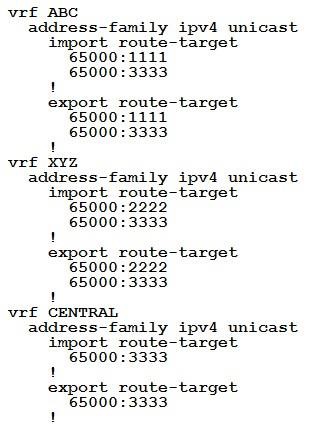
Answer: B
NEW QUESTION 19
Which two tasks must you perform when you implement LDP NSF on your network? (Choose two.)
- A. Enable NSF for BGP.
- B. Implement direct connections for LDP peers.
- C. Enable NSF for EIGRP.
- D. Disable Cisco Express Forwarding.
- E. Enable NSF for the link-state routing protocol that is in use on the network.
Answer: BE
NEW QUESTION 20
Refer to the exhibit. A network engineer is implementing QoS services. Which two statements about the qos-group keyword on Cisco IOS XR are true? (Choose two.)
- A. It marks packets for end-to-end QoS policy enforcement across the network.
- B. QoS group marking occurs on the ingress.
- C. The QoS group numbering corresponds to priority level.
- D. QoS group can be used in fabric QoS policy as match criteria.
- E. It cannot be used with priority traffic class.
Answer: BD
NEW QUESTION 21
While implementing TTL security, you issue the PE(config-router-af)#neighbor 2.2.2.2 ttl-security hops 2 command.
After you issue this command, which BGP packets does the PE accept?
- A. to 2.2.2.2, with a TTL of 2 or more
- B. from 2.2.2.2, with a TTL of less than 2
- C. to 2.2.2.2, with a TTL of less than 253
- D. from 2.2.2.2, with a TTL of 253 or more
Answer: D
NEW QUESTION 22
Which regular expression query modifier function indicates the start of a string?
- A. +
- B. ^
- C. $
- D. [^]
Answer: B
NEW QUESTION 23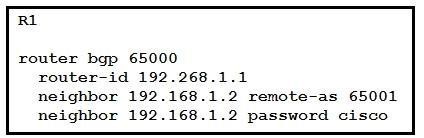
Refer to the exhibit Router R1 and its peer R2 reside on the same subnet in the network. If an engineer implements this configuration to R1, how does it make connections to R2?
- A. R1 establishes TCP connections that are authenticated with a clear-text password.
- B. R1 establishes UDP connections that are authenticated with an MD5 password.
- C. R1 establishes UDP connections that are authenticated with a clear-text password.
- D. R1 establishes TCP connections that are authenticated with an MD5 password.
Answer: D
NEW QUESTION 24
Which component is similar to an EVPN instance?
- A. router distinguisher
- B. MPLS label
- C. IGP router ID
- D. VRF
Answer: D
NEW QUESTION 25
......
Thanks for reading the newest 350-501 exam dumps! We recommend you to try the PREMIUM Downloadfreepdf.net 350-501 dumps in VCE and PDF here: https://www.downloadfreepdf.net/350-501-pdf-download.html (102 Q&As Dumps)
