It is more faster and easier to pass the microsoft 70 412 by using examcollection 70 412. Immediate access to the examcollection 70 412 and find the same core area 70 412 dumps with professionally verified answers, then PASS your exam with a high score now.
Online 70-412 free questions and answers of New Version:
NEW QUESTION 1
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the IP Address Management (IPAM) Server feature installed.
IPAM is configured currently for Group Policy- based provisioning. You need to change the IPAM provisioning method on Server1.
What should you do?
- A. Run the ipamgc.exe command.
- B. Run the Set-IPAMConfiguration cmdlet.
- C. Reinstall the IP Address Management (IPAM) Server feature.
- D. Delete IPAM Group Policy objects (GPOs) from the domain.
Answer: C
Explanation: You cannot change the provisioning method after completing the initial setup.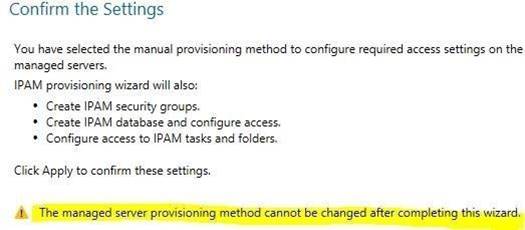
NEW QUESTION 2
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Certificate Services server role installed and configured.
For all users, you are deploying smart cards for logon. You are using an enrollment agent
to enroll the smart card certificates for the users.
You need to configure the Contoso Smartcard Logon certificate template to support the use of the enrollment agent.
Which setting should you modify? To answer, select the appropriate setting in the answer area.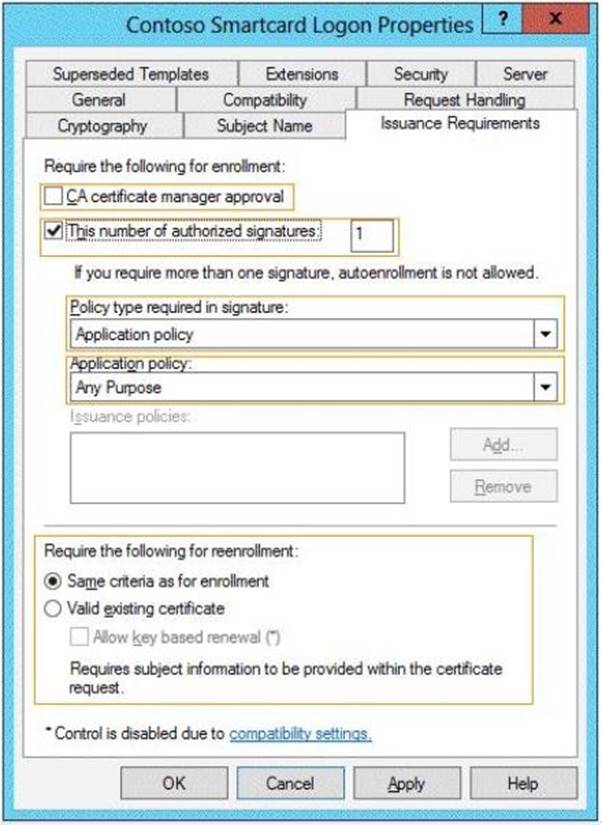
Answer:
Explanation: / In application policy drop-down list select Certificate Request Agent.
/ The Issuance Requirements Tab
* Application policy. This option specifies the application policy that must be included in the signing certificate used to sign the certificate request. It is enabled when Policy type required in signature is set to either Application policy or Both application and issuance policy.
NEW QUESTION 3
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1 that runs Windows Server 2012 R2. All client computers run Windows 8.
You need to configure a custom Access Denied message that will be displayed to users when they are denied access to folders or files on Server1.
What should you configure?
- A. A classification property
- B. The File Server Resource Manager Options
- C. A file management task
- D. A file screen template
Answer: B
Explanation: Access-denied assistance can be configured by using the File Server Resource Manager console on the file server.
Note: Access-denied assistance is a new feature in Windows Server 2012, which provides the following ways to troubleshoot issues that are related to access to files and folders:
* Self-assistance. If a user can determine the issue and remediate the problem so that they can get the requested access, the impact to the business is low, and no special exceptions are needed in the central access policy. Access-denied assistance provides an access- denied message that file server administrators can customize with information specific to their organizations. For example, an administrator could set the message so that users can request access from a data owner without involving the file server administrator.
Reference: Scenario: Access-Denied Assistance
NEW QUESTION 4
Your network contains one Active Directory domain named contoso.com. The domain contains an IP Address Management (IPAM)
Server named Server1. Server1 manages several DHCP and DNS servers. From server Manager on Server1, you create a custom role for IPAM.
You need to assign the role to a group named IP_Admins.
What should you do?
- A. From Windows PowerShell, run theAdd-Membercmdlet.
- B. From Server Manager, create an access policy.
- C. From Windows PowerShell, run theSet-IpamConfigurationcmdlet.
- D. From Server Manager, create an access scope.
Answer: B
Explanation: A role is a collection of IPAM operations. You can associate a role with a user or group in Windows using an access policy. Several built-in roles are provided, but you can also create customized roles to meet your business requirements.
Reference: Manage IPAM, Access Control https://technet.microsoft.com/en-us/library/dn741281.aspx
NEW QUESTION 5
Your network contains two Active Directory forests named contoso.com and
corp.contoso.com.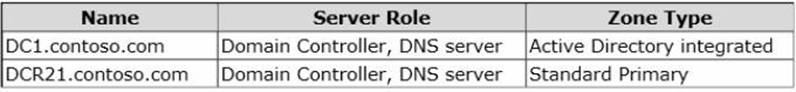
User1 is a member of the DnsAdmins domain local group in contoso.com.
User1 attempts to create a conditional forwarder to corp.contoso.com but receive an error message shown in the exhibit. (Click the Exhibit button.)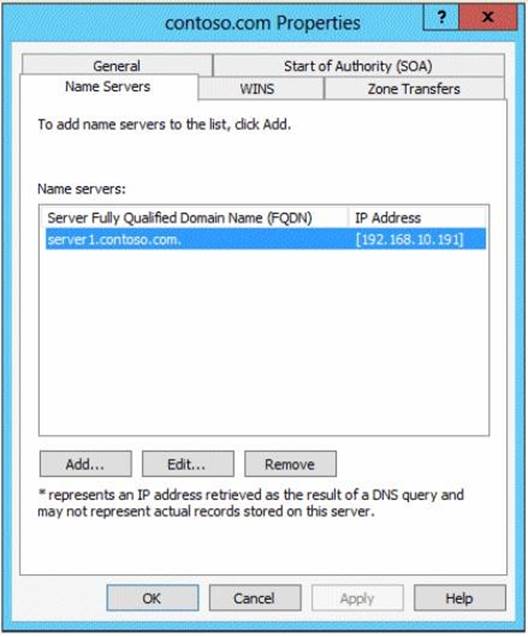
You need to configure bi-directional name resolution between the two forests. What should you do first?
- A. Add User1 to the DnsUpdateProxy group.
- B. Configure the zone to be Active Directory-integrated.
- C. Enable the Advanced view from DNS Manager.
- D. Run the New Delegation Wizard.
Answer: B
Explanation: The zone must be Active Directory-integrated.
NEW QUESTION 6
Your network contains one Active Directory forest named contoso.com. The forest contains two child domains and six domain controllers.
The domain controllers are configured as shown in the following table.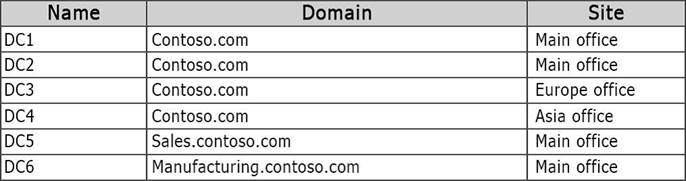
You need to add an additional UPN Suffix. What should you use?
- A. Set-ADSite
- B. Set-ADReplicationSite
- C. Set-ADDomain
- D. Set-ADReplicationSiteLink
- E. Set-ADGroup
- F. Set-ADForest
- G. Netdom
Answer: F
Explanation: https://technet.microsoft.com/en-us/library/dd391925(v=ws.10).aspx
NEW QUESTION 7
Your network contains an Active Directory domain named contoso.com.
A previous administrator implemented a Proof of Concept installation of Active Directory Rights Management Services (AD RMS).
After the proof of concept was complete, the Active Directory Rights Management Services server role was removed.
You attempt to deploy AD RMS.
During the configuration of AD RMS, you receive an error message indicating that an existing AD RMS Service Connection Point (SCP) was found.
You need to remove the existing AD RMS SCP. Which tool should you use?
- A. Active Directory Users and Computers
- B. Authorization Manager
- C. Active Directory Domains and Trusts
- D. Active Directory Sites and Services
- E. Active Directory Rights Management Services
Answer: E
Explanation: ADRMS will registered the Service Connection Point (SCP) in Active Directory and you will need to unregister first before you remove the ADRMS server role.
If your ADRMS server is still alive, you can easily manually remove the SCP by below: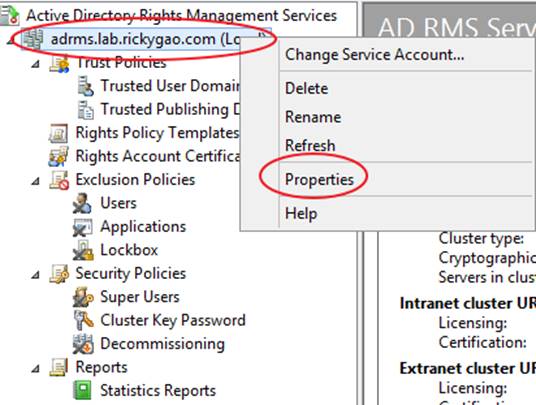
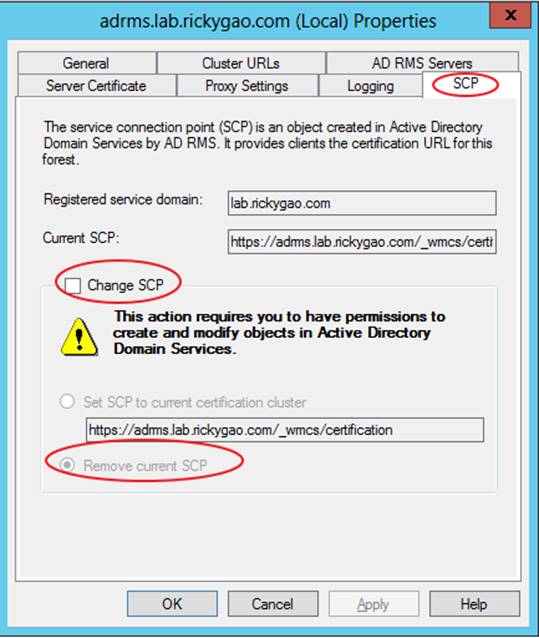
http://www.rickygao.com/wp-content/uploads/2013/08/080513_1308_Howtomanual2.png Reference: How to manually remove or reinstall ADRMS
NEW QUESTION 8
Information and details provided in a question App1y only to that question.
Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2.
Server1 and Server2 have the Network Load Balancing (NLB) feature installed. The servers are configured as nodes in an NLB cluster named Cluster1.
Cluster1 hosts a secure web Application named WebApp1. WebApp1 saves user state information locally on each node.
You need to ensure that when users connect to WebApp1, their session state is maintained.
What should you configure?
- A. Affinity-None
- B. Affinity-Single
- C. The cluster quorum settings
- D. The failover settings
- E. A file server for general use
- F. The Handling priority
- G. The host priority
- H. Live migration
- I. The possible owner
- J. The preferred owner
- K. Quick migration
- L. the Scale-Out File Server
Answer: B
Explanation: Client Affinity
NLB offers three types of client affinity to minimize response time to clients and provide generic support for preserving session state. Each affinity specifies a different method for distributing client requests.
Affinity Single: Single
Multiple requests from the same client must access the same member; useful for clusters within an intranet.
This affinity provides the best support for clients that use sessions on an intranet. These clients cannot use No affinity because their sessions could be disrupted.
Incorrect:
Not A. Affinity none: Multiple requests from the same client can access any member; useful for clusters that do not store session state information on individual members.
Reference: Using NLB
http://technet.microsoft.com/en-us/library/bb687542.aspx
NEW QUESTION 9
HOTSPOT
Your network contains two Hyper-V hosts that are configured as shown in the following table.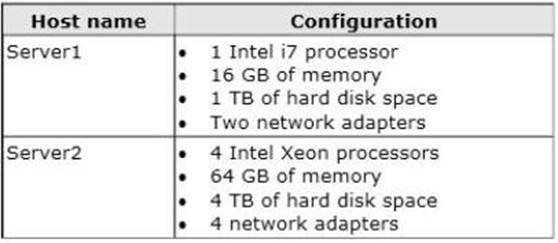
You create a virtual machine on Server1 named VM1.
You plan to export VM1 from Server1 and import VM1 to Server2.
You need to ensure that you can start the imported copy of VM1 from snapshots. What should you configure on VM1?
To answer, select the appropriate node in the answer area.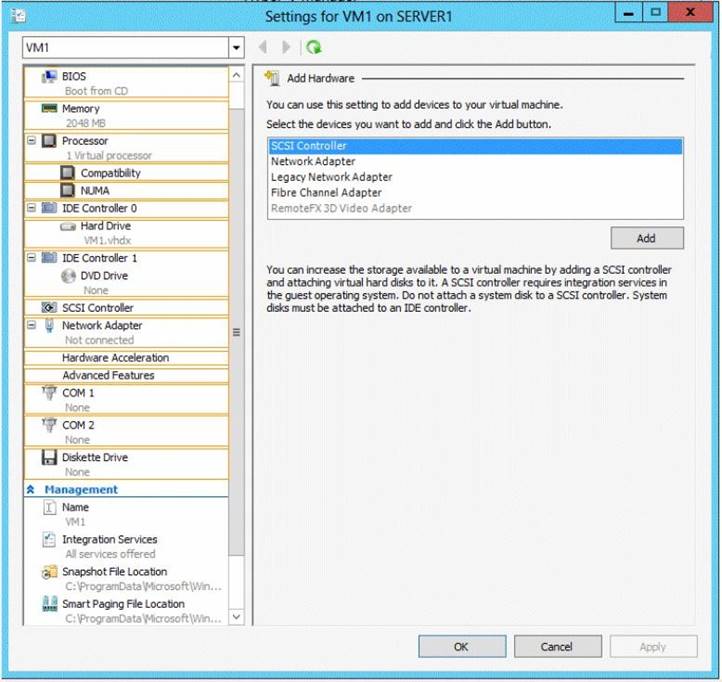
Answer:
Explanation: Note:
* If the CPUs are from the same manufacturer but not from the same type, you may need to use Processor Compatibility.
(Incorrect) The network adapter is already disconnected.
NEW QUESTION 10
Your network contains one Active Directory forest named contoso.com. The forest contains two child domains and six domain controllers. The domain controllers are configured as shown in the following table.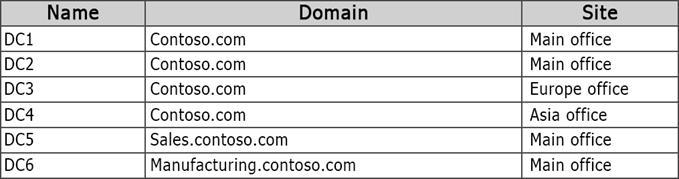
You have a trust from contoso.com to another forest named fabrikam.com. You plan to migrate users from contoso.com to fabrikam.com.
You need to ensure that the users who migrated to fabrikam.com can continue to access shared resources in contoso.com. The solution must not require administrators to modify permissions to shared resources.
What should you use?
- A. Set-ADSite
- B. Set-ADReplicationSite
- C. Set-ADDomain
- D. Set-ADReplicationSiteLink
- E. Set-ADGroup
- F. Set-ADForest
- G. Netdom
Answer: G
Explanation: The Netdom move command moves a workstation or member server to a new domain. The act of moving a computer to a new domain creates an account for the computer on the domain, if it does not already exist.
Reference: Technet, Netdom move https://technet.microsoft.com/en-us/library/cc788127.aspx
NEW QUESTION 11
Your network contains two Web servers named Server1 and Server2. Both servers run Windows Server 2012 R2.
Server1 and Server2 are nodes in a Network Load Balancing (NLB) cluster. The NLB cluster contains an application named App1 that is accessed by using the URLhttp://app1.contoso.com.
You plan to perform maintenance on Server1.
You need to ensure that all new connections to App1 are directed to Server2. The solution must not disconnect the existing connections to Server1.
What should you run?
- A. The Set-NlbCluster cmdlet
- B. The Set-NlbClusterNode cmdlet
- C. The Stop-NlbCluster cmdlet
- D. The Stop-NlbClusterNode cmdlet
Answer: D
Explanation: The Stop-NlbClusterNode cmdlet stops a node in an NLB cluster. When you use the stop the nodes in the cluster, client connections that are already in progress are interrupted. To avoid interrupting active connections, consider using the -drain parameter, which allows the node to continue servicing active connections but disables all new traffic to that node.
-Drain <SwitchParameter>
Drains existing traffic before stopping the cluster node. If this parameter is omitted, existing traffic will be dropped.
Reference: Stop-NlbClusterNode
NEW QUESTION 12
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2008 R2.
You plan to test Windows Server 2012 R2 by using native-boot virtual hard disks (VHDs). You have a Windows image file named file1.wim.
You need to add an image of a volume to file1.wim. What should you do?
- A. Runimagex.exeand specify the /appendparameter.
- B. Runimagex.exeand specify the /exportparameter.
- C. Rundism.exeand specify the /imageparameter.
- D. Rundism.exeand specify the /append-imageparameter.
Answer: D
Explanation: The Deployment Image Servicing and Management (DISM) tool is a command-line tool that enables the creation of Windows® image (.wim) files for deployment in a manufacturing or corporate IT environment. The /Append-Image option appends a volume image to an existing .wim file allowing you to store many customized Windows images in a fraction of the space. When you combine two or more Windows image files into a single .wim, any files that are duplicated between the images are only stored once.
Incorrect:
Not A, not B: ImageX has been flagged by Microsoft as a deprecated utility, and has been replaced with DISM
Reference: Append a Volume Image to an Existing Image Using DISM https://technet.microsoft.com/en-us/library/hh824916.aspx
NEW QUESTION 13
You need to verify whether a DNS response from a DNS server is signed by DNSSEC. What should you run?
- A. nslookup.exe
- B. dnscmd.exe
- C. Resolve-DNSName
- D. Get-NetIPAddress
Answer: C
Explanation: The Resolve-DnsName cmdlet performs a DNS query for the specified name. This cmdlet is functionally similar to the nslookup tool which allows users to query for names. The Resolve-DnsName cmdlet was introduced in Windows Server 2012 and Windows 8 and can be used to display DNS queries that include DNSSEC data.
Parameters include:
* -DnssecOk
Sets the DNSSEC OK bit for this query.
* -DnssecCd
Sets the DNSSEC checking-disabled bit for this query
Example: In the following example, the DO=1 flag is set by adding the dnssecok parameter.
PS C:> resolve-dnsname -name finance.secure.contoso.com -type A -server dns1.contoso.com -dnssecok
Incorrect:
Not A: Do not use the nslookup command-line tool to test DNSSEC support for a zone. The nslookup tool uses an internal DNS client that is not DNSSEC-aware.
Reference: Resolve-DnsName https://technet.microsoft.com/library/jj590781.aspx Reference: Overview of DNSSEC
https://technet.microsoft.com/en-us/library/jj200221.aspx#validation
NEW QUESTION 14
You have moved several domain controllers out of your organization's head office site to a new secondary datacenter that has its own site.
Which of the following consoles should be used to update the site association of these domain controllers?
- A. Active Directory Administrative Center
- B. Active Directory Users and Computers
- C. Active Directory Sites And Services
- D. Active Directory Domains And Trusts
Answer: C
NEW QUESTION 15
Your network contains one Active Directory forest named contoso.com. The forest contains two child domains and six domain controllers. The domain controllers are configured as shown in the following table.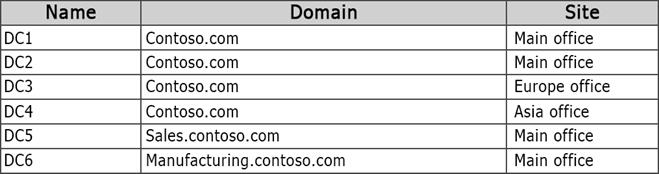
You need to prevent administrators from accidentally deleting any of the sites in the forest. What should you use?
- A. Set-ADSite
- B. Set-ADReplicationSite
- C. Set-ADDomain
- D. Set-ADReplicationSiteLink
- E. Set-ADGroup
- F. Set-ADForest
- G. Netdom
Answer: B
Explanation: The Set-ADReplicationSite sets the replication properties for an Active Directory site. Parameter: -ProtectedFromAccidentalDeletion<Boolean>
Specifies whether to prevent the object from being deleted. When this property is set to
$True, you cannot delete the corresponding object without changing the value of the property. The acceptable values for this parameter are:
-- $False or 0
-- $True or 1
Reference: Technet, Set-ADReplicationSite https://technet.microsoft.com/en-us/library/hh852305(v=wps.630).aspx
NEW QUESTION 16
Your network contains an Active Directory forest.
The forest contains two domains named contoso.com and fabrikam.com.
The forest functional level is Windows 2000. The contoso.com domain contains domain controllers that run either Windows Server 2008 or Windows Server 2008 R2.
The domain functional level is Windows Server 2008.
The fabrikam.com domain contains domain controllers that run either Windows 2000 Server or Windows Server 2003.
The domain functional level is Windows 2000 native.
The contoso.com domain contains a member server named Server1 that runs Windows Server 2012 R2.
You need to add Server1 as a new domain controller in the contoso.com domain. What should you do first?
- A. Raise the functional level of the contoso.com domain to Windows Server 2008 R2.
- B. Upgrade the domain controllers that run Windows Server 2008 to Windows Server 2008 R2.
- C. Raise the functional level of the fabrikam.com domain to Windows Server 2003.
- D. Decommission the domain controllers that run Windows 2000.
- E. Raise the forest functional level to Windows Server 2003.
Answer: D
Explanation: D. Server 2003 is the minimum Domain Functional level for any domain in the forest Windows Server 2012 R2 requires a Windows Server 2003 forest functional level.
That is, before you can add a domain controller that runs Windows Server 2012 R2 to an existing Active Directory forest, the forest functional level must be Windows Server 2003 or higher.
http://technet.microsoft.com/en-us/library/cc771294.aspx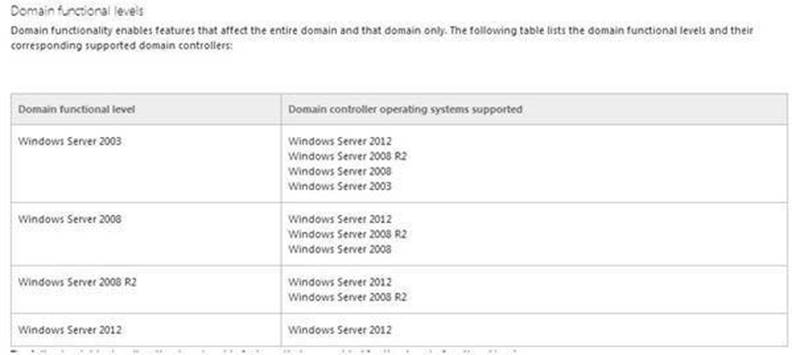
NEW QUESTION 17
DRAG DROP
You plan to deploy a failover cluster that will contain two nodes that run Windows Server 2012 R2.
You need to configure a witness disk for the failover cluster. How should you configure the witness disk?
To answer, drag the appropriate configurations to the correct location or locations. Each configuration may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.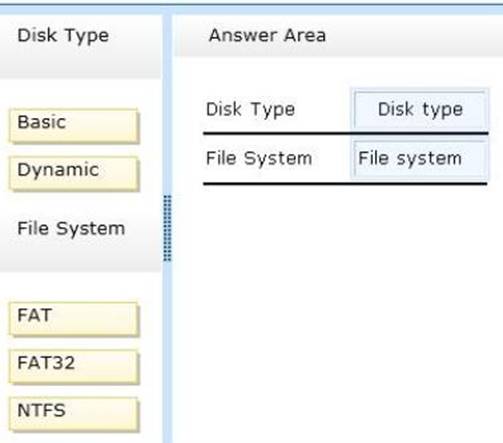
Answer:
Explanation: Disk witness requirements include:
* Basic disk with a single volume
* Can be formatted with NTFS or ReFS
100% Valid and Newest Version 70-412 Questions & Answers shared by 2passeasy, Get Full Dumps HERE: https://www.2passeasy.com/dumps/70-412/ (New 435 Q&As)
