It is impossible to pass 156-215.80 exam without any help in the short term. Come to us soon and find the most advanced, correct and guaranteed 156-215.80 Exam Dumps. You will get a surprising result by our 156-215.80 Braindumps.
Online 156-215.80 free questions and answers of New Version:
NEW QUESTION 1
You are about to test some rule and object changes suggested in an R77 news group. Which backup solution should you use to ensure the easiest restoration of your Security Policy to its previous configuration after testing the changes?
- A. Manual copies of the directory $FWDIR/conf
- B. upgrade_export command
- C. Database Revision Control
- D. GAiA backup utilities
Answer: C
NEW QUESTION 2
Jack works for a managed service provider and he has been tasked to create 17 new policies for several new customers. He does not have much time. What is the BEST way to do this with R80 security management?
- A. Create a text-file with mgmt_cli script that creates all objects and policie
- B. Open the file in SmartConsole Command Line to run it.
- C. Create a text-file with Gaia CLI -commands in order to create all objects and policie
- D. Run the file in CLISH with command load configuration.
- E. Create a text-file with DBEDIT script that creates all objects and policie
- F. Run the file in the command line of the management server using command dbedit -f.
- G. Use Object Explorer in SmartConsole to create the objects and Manage Policies from the menu to create the policies.
Answer: A
Explanation: Did you know: mgmt_cli can accept csv files as inputs using the --batch option.
The first row should contain the argument names and the rows below it should hold the values for these parameters.
So an equivalent solution to the powershell script could look like this:
data.csv: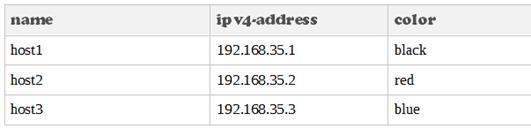
mgmt_cli add host --batch data.csv -u <username> -p <password> -m <management server>
This can work with any type of command not just "add host" : simply replace the column names with the ones relevant to the command you need.
NEW QUESTION 3
To ensure that VMAC mode is enabled, which CLI command you should run on all cluster members? Choose the best answer.
- A. fw ctl set int fwha vmac global param enabled
- B. fw ctl get int fwha vmac global param enabled; result of command should return value 1
- C. cphaprob –a if
- D. fw ctl get int fwha_vmac_global_param_enabled; result of command should return value 1
Answer: B
NEW QUESTION 4
What is the default time length that Hit Count Data is kept?
- A. 3 month
- B. 4 weeks
- C. 12 months
- D. 6 months
Answer: A
Explanation: Keep Hit Count data up to - Select one of the time range options. The default is 6 months. Data is kept in the Security Management Server database for this period and is shown in the Hits column.
NEW QUESTION 5
Fill in the blank: In order to install a license, it must first be added to the ______ .
- A. User Center
- B. Package repository
- C. Download Center Web site
- D. License and Contract repository
Answer: B
NEW QUESTION 6
When launching SmartDashboard, what information is required to log into R77?
- A. User Name, Management Server IP, certificate fingerprint file
- B. User Name, Password, Management Server IP
- C. Password, Management Server IP
- D. Password, Management Server IP, LDAP Server IP
Answer: B
NEW QUESTION 7
Which one of the following is the preferred licensing model? Select the Best answer.
- A. Local licensing because it ties the package license to the IP-address of the gateway and has no dependency of the Security Management Server.
- B. Central licensing because it ties the package license to the IP-address of the Security Management Server and has no dependency of the gateway.
- C. Local licensing because it ties the package license to the MAC-address of the gateway management interface and has no Security Management Server dependency.
- D. Central licensing because it ties the package license to the MAC-address of the Security Management Server Mgmt-interface and has no dependency of the gateway.
Answer: B
Explanation: Central License
A Central License is a license attached to the Security Management server IP address, rather than the gatewa IP address. The benefits of a Central License are:
Only one IP address is needed for all licenses.
A license can be taken from one gateway and given to another.
The new license remains valid when changing the gateway IP address. There is no need to create and install a new license.
NEW QUESTION 8
AdminA and AdminB are both logged in on SmartConsole. What does it mean if AdminB sees a locked icon on a rule? Choose the BEST answer.
- A. Rule is locked by AdminA, because the save bottom has not been press.
- B. Rule is locked by AdminA, because an object on that rule is been edited.
- C. Rule is locked by AdminA, and will make it available if session is published.
- D. Rule is locked by AdminA, and if the session is saved, rule will be available
Answer: C
NEW QUESTION 9
When defining QoS global properties, which option below is not valid?
- A. Weight
- B. Authenticated timeout
- C. Schedule
- D. Rate
Answer: C
NEW QUESTION 10
The WebUI offers three methods for downloading Hotfixes via CPUSE. One of them is Automatic method. How many times per day will CPUSE agent check for hotfixes and automatically download them?
- A. Six times per day
- B. Seven times per day
- C. Every two hours
- D. Every three hours
Answer: D
NEW QUESTION 11
Which of the following is NOT a tracking option?
- A. Partial log
- B. Log
- C. Network log
- D. Full log
Answer: A
NEW QUESTION 12
Which Threat Prevention Profile is not included by default in R80 Management?
- A. Basic – Provides reliable protection on a range of non-HTTP protocols for servers, with minimal impact on network performance
- B. Optimized – Provides excellent protection for common network products and protocols against recent or popular attacks
- C. Strict – Provides a wide coverage for all products and protocols, with impact on network performance
- D. Recommended – Provides all protection for all common network products and servers, with impact on network performance
Answer: D
NEW QUESTION 13
Which of the following is an authentication method used for Identity Awareness?
- A. SSL
- B. Captive Portal
- C. PKI
- D. RSA
Answer: B
NEW QUESTION 14
Which of the following firewall modes DOES NOT allow for Identity Awareness to be deployed?
- A. Bridge
- B. Load Sharing
- C. High Availability
- D. Fail Open
Answer: A
NEW QUESTION 15
Fill in the blank: A ____ is used by a VPN gateway to send traffic as if it were a physical interface.
- A. VPN Tunnel Interface
- B. VPN community
- C. VPN router
- D. VPN interface
Answer: A
Explanation: Route Based VPN
VPN traffic is routed according to the routing settings (static or dynamic) of the Security Gateway operating system. The Security Gateway uses a VTI (VPN Tunnel Interface) to send the VPN traffic as if it were a physical interface. The VTIs of Security Gateways in a VPN community connect and can support dynamic routing protocols.
NEW QUESTION 16
By default, which port does the WebUI listen on?
- A. 80
- B. 4434
- C. 443
- D. 8080
Answer: C
Explanation: To configure Security Management Server on Gaia:
Open a browser to the WebUI: https:<//Gaia management IP address>
NEW QUESTION 17
Joey is using the computer with IP address 192.168.20.13. He wants to access web page “www.Check Point.com”, which is hosted on Web server with IP address 203.0.113.111. How many rules on Check Point Firewall are required for this connection?
- A. Two rules – first one for the HTTP traffic and second one for DNS traffic.
- B. Only one rule, because Check Point firewall is a Packet Filtering firewall
- C. Two rules – one for outgoing request and second one for incoming replay.
- D. Only one rule, because Check Point firewall is using Stateful Inspection technology.
Answer: D
NEW QUESTION 18
You are going to upgrade from R77 to R80. Before the upgrade, you want to back up the system so that, if there are any problems, you can easily restore to the old version with all configuration and management files intact. What is the BEST backup method in this scenario?
- A. backup
- B. Database Revision
- C. snapshot
- D. migrate export
Answer: C
Explanation: 2. Snapshot Management
The snapshot creates a binary image of the entire root (lv_current) disk partition. This includes Check Point products, configuration, and operating system.
Starting in R77.10, exporting an image from one machine and importing that image on another machine of the same type is supported.
The log partition is not included in the snapshot. Therefore, any locally stored FireWall logs will not be save
Recommend!! Get the Full 156-215.80 dumps in VCE and PDF From Surepassexam, Welcome to Download: https://www.surepassexam.com/156-215.80-exam-dumps.html (New 440 Q&As Version)
