Proper study guides for 70-412 Configuring Advanced Windows Server 2012 Services certified begins with 70 412 exam dumps preparation products which designed to deliver the mcsa 70 412 by making you pass the 70-412 test at your first time. Try the free mcsa 70 412 right now.
Online 70-412 free questions and answers of New Version:
NEW QUESTION 1
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Federation Services server role installed.
You need to make configuration changes to the Windows Token-based Agent role service. Which tool should you use?
To answer, select the appropriate tool in the answer area.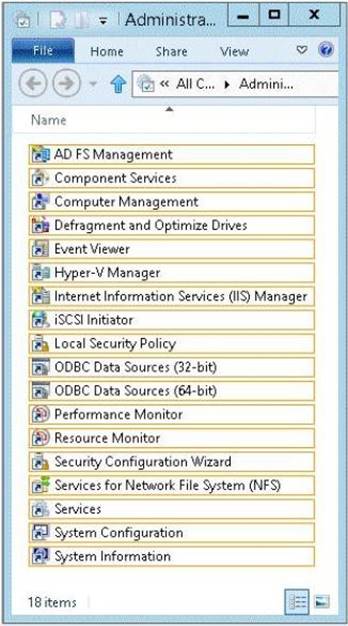
Answer:
Explanation: To configure the Windows token-based agent
✑ ClickStart, point toAdministrative Tools, and then clickInternet Information Services (IIS) Manager.
Etc.
NEW QUESTION 2
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2.
Server1 is an enterprise root certification authority (CA) for contoso.com.
You need to ensure that the members of a group named Group1 can request code signing certificates. The certificates must be issued automatically to the members.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
- A. From Certificate Templates, modify the certificate template.
- B. From Certification Authority, add a certificate template to be issued.
- C. From Certificate Authority, modify the CA properties.
- D. From Certificate Templates, duplicate a certificate template.
- E. From Certificate Authority, stop and start the Active Directory Certificate Services (AD CS) service.
Answer: AD
Explanation:
Best Practices include: Duplicate new templates from existing templates closest in function to the intended template.
New certificate templates are duplicated from existing templates. Many settings are copied from the original template. Because of this, duplicating one template to another of a totally different type may carry over some unintended settings. When duplicating a template, examine the subject type of the original template and ensure that you duplicate one that has a similar function to that of the intended template. Although most settings for certificate templates can be edited once the template is duplicated, the subject type cannot be changed.
Reference: Deploying Certificate Templates https://technet.microsoft.com/en-us/library/cc770794%28v=ws.10%29.aspx
NEW QUESTION 3
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. DC1 has the DNS Server server role installed.
The network contains client computers that run either Linux, Windows 7, or Windows 8. You have a standard primary zone named adatum.com as shown in the exhibit. (Click the Exhibit button.)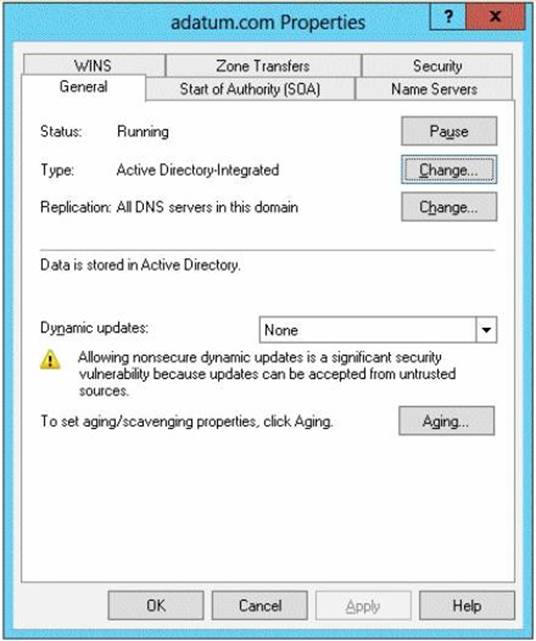
You plan to configure Name Protection on all of the DHCP servers.
You need to configure the adatum.com zone to support Name Protection.
Which two configurations should you perform from DNS Manager? (Each correct answer presents part of the solution. Choose two.)
- A. Sign the zone.
- B. Store the zone in Active Directory.
- C. Modify the Security settings of the zone.
- D. Configure Dynamic updates.
- E. Add a DNS key record
Answer: BD
Explanation: Name protection requires secure update to work. Without name protection DNS names may be hijacked.
You can use the following procedures to allow only secure dynamic updates for a zone. Secure dynamic update is supported only for Active Directory–integrated zones. If the zone type is configured differently, you must change the zone type and directory-integrate the zone before securing it for Domain Name System (DNS) dynamic updates.
1. (B) Convert primary DNS server to Active Directory integrated primary
2. (D) Enable secure dynamic updates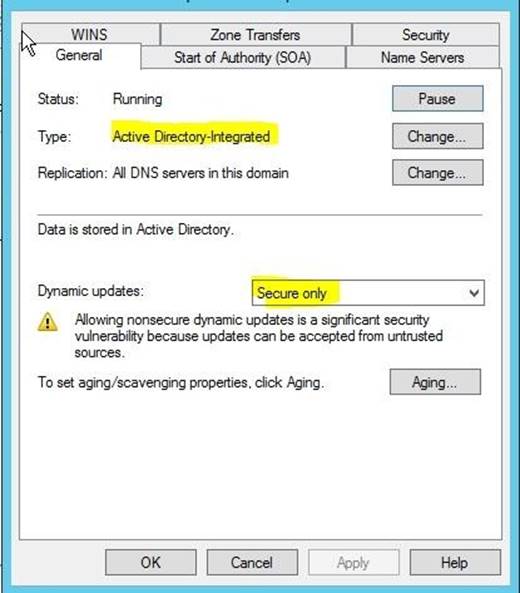
Reference: DHCP: Secure DNS updates should be configured if Name Protection is enabled on any IPv4 scope
http://technet.microsoft.com/en-us/library/ee941152(v=ws.10).aspx
NEW QUESTION 4
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The relevant servers in the domain are configured as shown in the following table.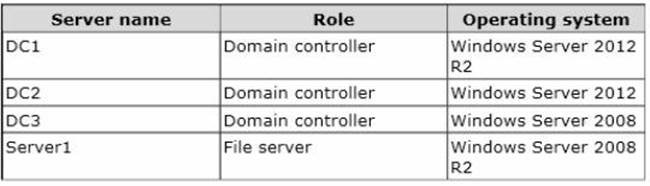
You plan to create a shared folder on Server1 named Share1. Share1 must only be accessed by users who are using computers that are joined to the domain.
You need to identify which servers must be upgraded to support the requirements of Share1.
In the table below, identify which computers require an upgrade and which computers do not require an upgrade. Make only one selection in each row. Each correct selection is worth one point.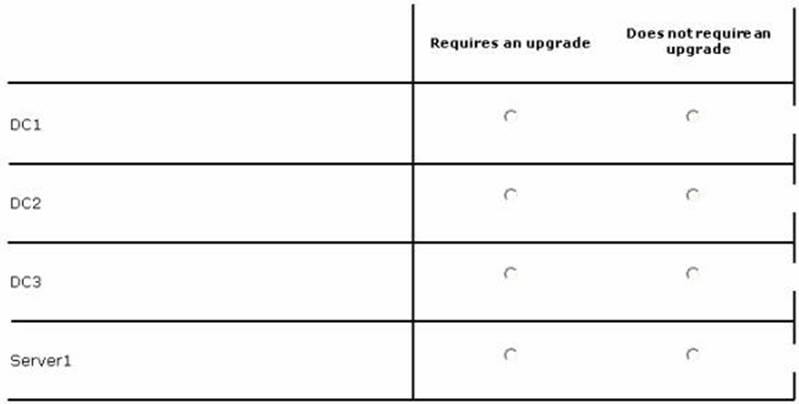
Answer:
Explanation: There is new file server functionality in Windows Server 2012. The file server should be upgraded to Windows Server 2012.
NEW QUESTION 5
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the DHCP Server server role installed.
An administrator installs the IP Address Management (IPAM) Server feature on a server named Server2. The administrator configures IPAM by using Group Policy based provisioning and starts server discovery.
You plan to create Group Policies for IPAM provisioning.
You need to identify which Group Policy object (GPO) name prefix must be used for IPAM Group Policies.
What should you do on Server2?
- A. From Server Manager, review the IPAM overview.
- B. Run the ipamgc.exe tool.
- C. From Task Scheduler, review the IPAM tasks.
- D. Run the Get-IpamConfiguration cmdlet.
Answer: D
Explanation: Example: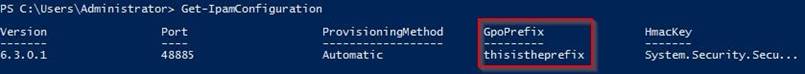
NEW QUESTION 6
You are employed as a senior network administrator at contoso.com.
contoso.com has an active directory domain named contoso.com.
All servers on the contoso.com network have Windows Server 2012 R2 installed. You are currently running at training exercise for junior network administrators. You are discussing the DNSSEC NRPT rule properly.
Which of the following describes the purpose of this rule property?
- A. It is used to indicate the namespace to which the policy applies.
- B. It is used to indicate whether the DNS client should check for DNSSEC validation in the response.
- C. It is used to indicate DNSSEC must be used to protect DNS traffic for queries belonging to the namespace.
- D. It is used to whether DNS connections over DNSSEC will use encryption
Answer: B
Explanation: A. NRPT is a table that contains rules you can configure to specify DNS settings or special behavior for names or namespaces
B. The DNS client's behavior is controlled by a policy(GPO) that determines whether the client should check for validation results for names within a given namespace.
D. DNS does not provide any mechanism for the encryption of DNS queries and responses.
http://technet.microsoft.com/en-us/library/ee649241(v=ws.10).aspx http://technet.microsoft.com/en-us/library/ee683904(v=ws.10).aspx http://technet.microsoft.com/en-us/library/ee649205(v=ws.10).aspx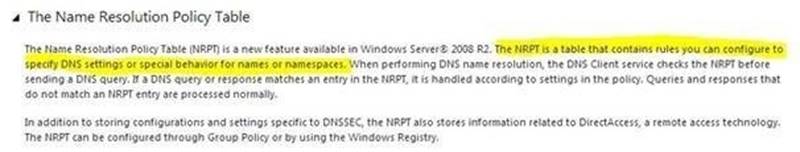
NEW QUESTION 7
You have two Hyper-V hosts named Host1 and Host2 that run Windows Server 2012 R2. Host1 hosts a virtual machine named VM1 that is replicated to Host2. VM1 hosts an
internal web application.
You need to test the failover of VM1 to Host2. The solution must ensure that clients continue to connect to VM1 on Host1.
Which cmdlet should you run?
- A. Start-VMFailover
- B. Export-VM
- C. Move-VM
- D. Test-VMReplicationConnection
- E. Compare-VM
Answer: A
Explanation: Start-VMFailover -AsTest
Creates a test virtual machine using the chosen recovery point. You can use a test virtual machine to validate a Replica virtual machine. To stop a test failover, use the Stop- VMFailover cmdlet.
The Start-VMFailover cmdlet can be used for the following tasks:
✑ Fail over a Replica virtual machine to a chosen recovery point.
✑ Start a planned failover on a primary virtual machine.
✑ Create a test virtual machine on a Replica virtual machine.
Reference: Start-VMFailover
https://technet.microsoft.com/en-us/library/jj136051(v=wps.630).aspx
NEW QUESTION 8
You are employed as a network administrator at ABC.com.
ABC.com has an Active Directory domain named ABC.com all servers on the ABC.com
network have Windows Server 2012 R2 installed.
ABC.com has a server named SERVER1 which has been configured to run the HYPER-V server role Server1 is configures to host multiple vitrual mahines.
When ABC.com acquires a server with a better hardware configuration to SERVER1 you are instructed to relocate the vitrual machines to the new server with as little interruptions as possible. Which of the following actions should you take ? (Choose all that apply.)
- A. You should consider exporting the vitrual machines from Server1.
- B. You should consider running a snapshot backup of the SERVER1.
- C. You should consider importing the vitrual machine from Server1 to the new server.
- D. You shoul consider restoring the snapshot backup on the hard drives of the new server.
Answer: AC
NEW QUESTION 9
You have 30 servers that run Windows Server 2012 R2.
All of the servers are backed up daily by using Windows Azure Online Backup.
You need to perform an immediate backup of all the servers to Windows Azure Online Backup.
Which Windows PowerShell cmdlets should you run on each server?
- A. Get-OBPolicy | StartOBBackup
- B. Start-OBRegistration | StartOBBackup
- C. Get-WBPolicy | Start-WBBackup
- D. Get-WBBackupTarget | Start-WBBackup
Answer: A
Explanation: This example starts a backup job using a policy. Windows PowerShell
PS C:> Get-OBPolicy | Start-OBBackup
Incorrect:
Not B. Registers the current computer to Windows Azure Backup. Not C. Not using Azure
Not D. Not using Azure
Reference: Start-OBBackup
http://technet.microsoft.com/en-us/library/hh770406(v=wps.620).aspx
NEW QUESTION 10
Your network contains an Active Directory domain named contoso.com.
The network contains a file server named Server1 that runs Windows Server 2012 R2. You create a folder named Folder1.
You share Folder1 as Share1.
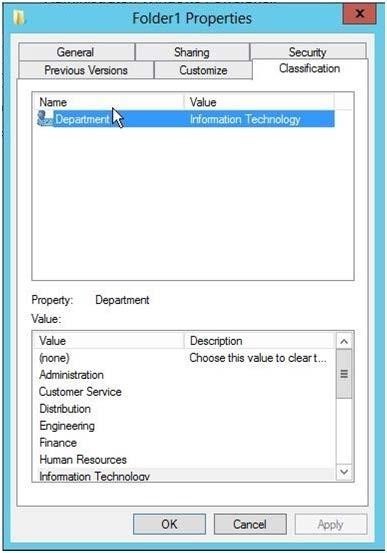
The NTFS permissions on Folder1 are shown in the Folder1 exhibit. (Click the Exhibit button.)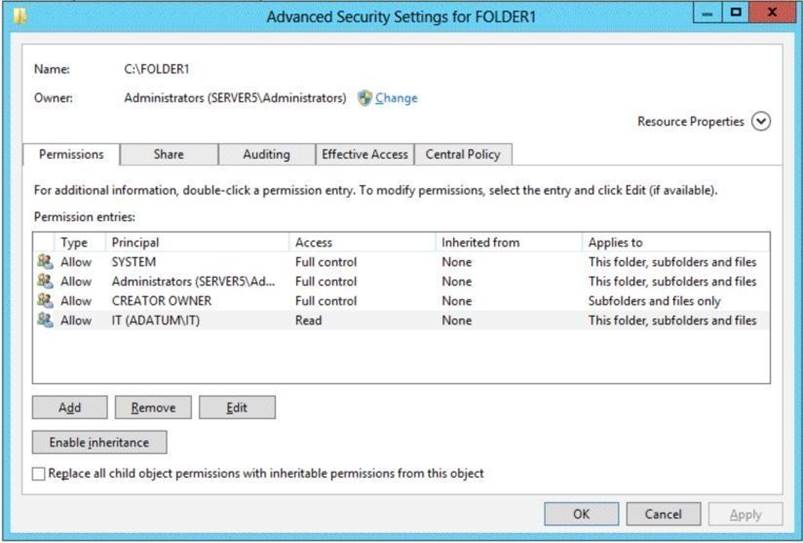
The Everyone group has the Full control Share permission to Folder1.
You configure a central access policy as shown in the Central Access Policy exhibit. (Click the Exhibit button.)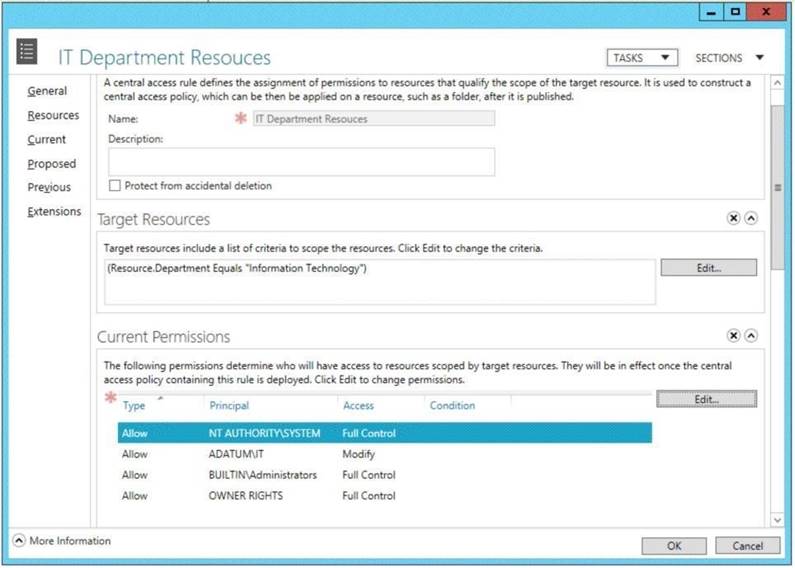
Members of the IT group report that they cannot modify the files in Folder1.
You need to ensure that the IT group members can modify the files in Folder1. The solution must use central access policies to control the permissions.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
- A. On the Classification tab of Folder1, set the classification to Information Technology.
- B. On the Security tab of Folder1, add a conditional expression to the existing permission entry for the IT group.
- C. On Share1, assign the Change Share permission to the IT group.
- D. On the Security tab of Folder1, remove the permission entry for the IT group.
- E. On the Security tab of Folder1, assign the Modify permission to the Authenticated Users group.
Answer: AE
Explanation: Central access policies for files enable organizations to centrally deploy and manage authorization policies that include conditional expressions that use user groups, user claims, device claims, and resource properties. (Claims are assertions about the attributes of the object with which they are associated). For example, to access high-business-impact (HBI) data, a user must be a full-time employee, obtain access from a managed device, and log on with a smart card. These policies are defined and hosted in Active Directory Domain Services (AD DS).
http://technet.microsoft.com/en- us/library/hh846167.aspx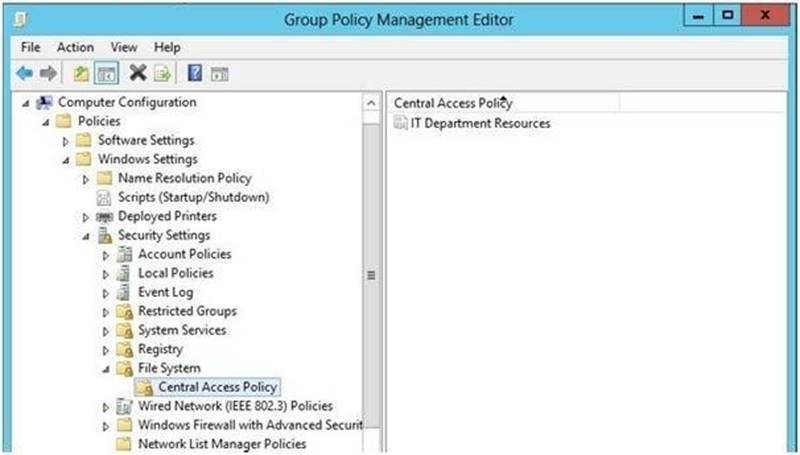
NEW QUESTION 11
Your network contains an Active Directory domain named adatum.com.
The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. On Dc1, you open DNS Manager as shown in the exhibit. (Click the Exhibit button.)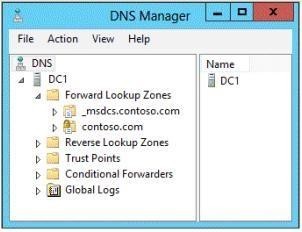
You need to change the zone type of the contoso.com zone from an Active Directory- integrated zone to a standard primary zone.
What should you do before you change the zone type?
- A. Unsign the zone.
- B. Modify the Zone Signing Key (ZSK).
- C. Modify the Key Signing Key (KSK).
- D. Change the Key Master.
Answer: A
Explanation: A. Lock icon indicating that it is currently signed with DNSSEC, zone must be unsignes
B. An authentication key that corresponds to a private key used to sign a zone.
C. The KSK is an authentication key that corresponds to a private key used to sign one or more other signing keys for a given zone.
Typically, the private key corresponding to a KSK will sign a ZSK, which in turn has a corresponding private key that will sign other zone data.
D.
http://technet.microsoft.com/en-us/library/hh831411.aspx http://technet.microsoft.com/en-us/library/ee649132(v=ws.10).aspx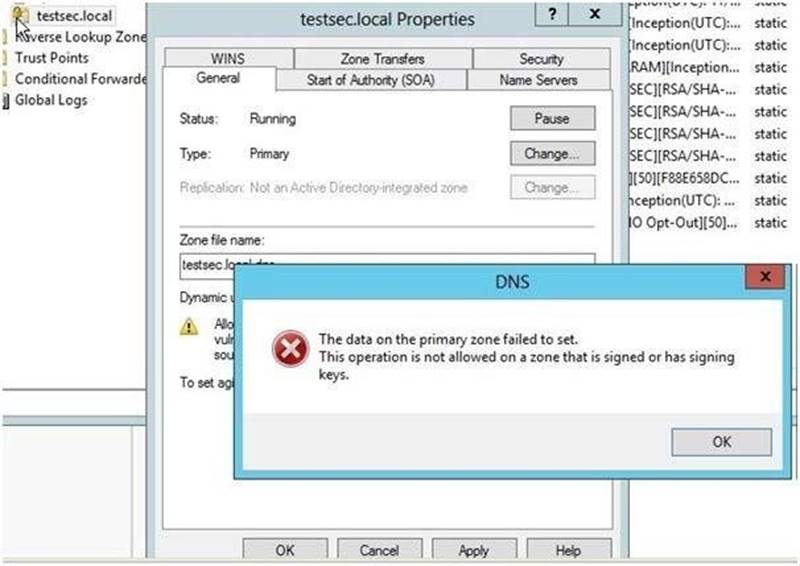
NEW QUESTION 12
Your network contains one Active Directory domain named contoso.com. The forest functional level is Windows Server 2012. All servers run Windows Server 2012 R2. All client computers run Windows 8.1.
The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01. All domain controllers and RODCs are hosted on a Hyper-V host that runs Windows Server 2012 R2.
You need to identify which security principals are authorized to have their password cached on RODC01.
Which cmdlet should you use?
- A. Get-ADGroupMember
- B. Get-ADDomainControllerPasswordReplicationPolicy
- C. Get-ADDomainControllerPasswordReplicationPolicyUsage
- D. Get-ADDomain
Answer: B
Explanation: The Get-ADDomainControllerPasswordReplicationPolicy gets the users, computers, service accounts and groups that are members of the applied list or denied list for a read- only domain controller's (RODC) password replication policy. To get the members of the applied list, specify the AppliedList parameter. To get the members of the denied list, specify the DeniedList parameter.
Example: Get from an RODC domain controller password replication policy the allowed accounts showing the name and object class of each:
Get-ADDomainControllerPasswordReplicationPolicy -Identity "FABRIKAM-RODC1" - Allowed | ft Name,ObjectClass
Reference: Get-ADDomainControllerPasswordReplicationPolicy https://technet.microsoft.com/en-us/library/ee617207.aspx
NEW QUESTION 13
Your network contains one Active Directory forest named contoso.com. The forest contains a single domain.
The domain contains the domain controllers is configured as shown in the following table.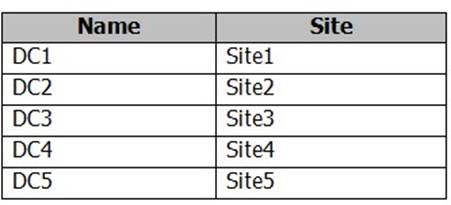

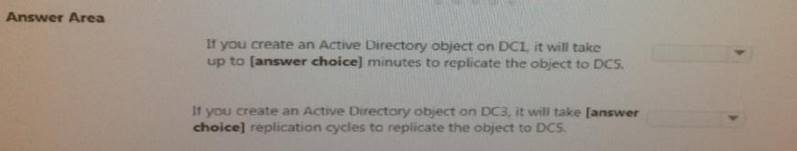
- A. DC1 120 DC3 60
Answer: A
NEW QUESTION 14
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2.
An organizational unit (OU) named OU1 contains 200 client computers that run Windows 8 Enterprise.
A Group Policy object (GPO) named GPO1 is linked to OU1. You make a change to GPO1.
You need to force all of the computers in OU1 to refresh their Group Policy settings immediately.
The solution must minimize administrative effort. Which tool should you use?
- A. The Set-AdComputercmdlet
- B. Group Policy Object Editor
- C. Active Directory Users and Computers
- D. Group Policy Management Console (GPMC)
Answer: D
Explanation: In the previous versions of Windows, this was accomplished by having the user run GPUpdate.exe on their computer. Starting with Windows Server?2012 and Windows?8, you can now remotely refresh Group Policy settings for all computers in an OU from one central location through the Group Policy Management Console (GPMC). Or you can use the Invoke-GPUpdate cmdlet to refresh Group Policy for a set of computers, not limited to the OU structure, for example, if the computers are located in the default computers container.
Note: Group Policy Management Console (GPMC) is a scriptable Microsoft Management Console (MMC) snap-in, providing a single administrative tool for managing Group Policy across the enterprise. GPMC is the standard tool for managing Group Policy.
Incorrect:
Not B: Secedit configures and analyzes system security by comparing your current configuration to at least one template.
Reference: Force a Remote Group Policy Refresh (GPUpdate)
NEW QUESTION 15
You have a test server named Server1 that is configured to dual-boot between Windows Server 2008 R2 and Windows Server 2012 R2.
You start Server1 and you discover that the boot entry for Windows Server 2008 R2 no longer appears on the boot menu.
You start Windows Server 2012 R2 on Server1 and you discover the disk configurations shown in the following table.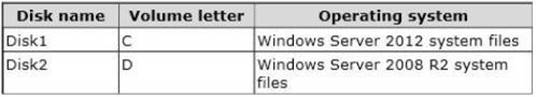
You need to restore the Windows Server 2008 R2 boot entry on Server1. What should you do?
- A. Run bcdedit.exe and specify the /createstore parameter
- B. Run bootrec.exe and specify the /scanos parameter
- C. Run bcdboot.exe d:windows.
- D. Run bootrec.exe and specify the /rebuildbcd parameter
Answer: D
Explanation: A. BCDEdit is a command-line tool for managing BCD stores.
It can be used for a variety of purposes, including creating new stores, modifying existing stores, adding boot menu options, /Createstore Creates a new empty boot configuration data store.
The created store is not a system store.
B. Bootrec.exe tool to troubleshoot "Bootmgr Is Missing" issue.
The /ScanOs option scans all disks for installations that are c mpatible with Windows Vista or Windows 7.
Additionally, this option displays the entries that are currently not in the BCD store. Use this option when there are Windows Vista or Windows 7 installations that the Boot Manager menu does not list.
C.
D. Bootrec.exe tool to troubleshoot "Bootmgr Is Missing" issue. The /ScanOs option scans all disks for installations that are compatible with Windows Vista or Windows 7. Additionally, this option displays the entries that are currently not in the BCD store. Use this option when there are Windows Vista or Windows 7 installations that the Boot Manager menu does not list.
http://technet.microsoft.com/en-us/library/cc709667(v=ws.10).aspx http://support.microsoft.com/kb/927392/en-us
NEW QUESTION 16
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the DHCP Server server role installed. Server1 has an IPv6 scope named Scope1.
You implement an additional DHCP server named Server2 that runs Windows Server 2012 R2.
You need to provide high availability for Scope1. The solution must minimize administrative effort.
What should you do?
- A. Install and configure Network Load Balancing (NLB) on Server1 and Server2.
- B. Create a scope on Server2.
- C. Configure DHCP failover on Server1.
- D. Install and configure Failover Clustering on Server1 and Server2.
Answer: C
Explanation: Overview: Configure DHCP failover using the DHCP console
To configure DHCP failover using the DHCP console, right-click a DHCP scope or right- click IPv4 and then click Configure Failover.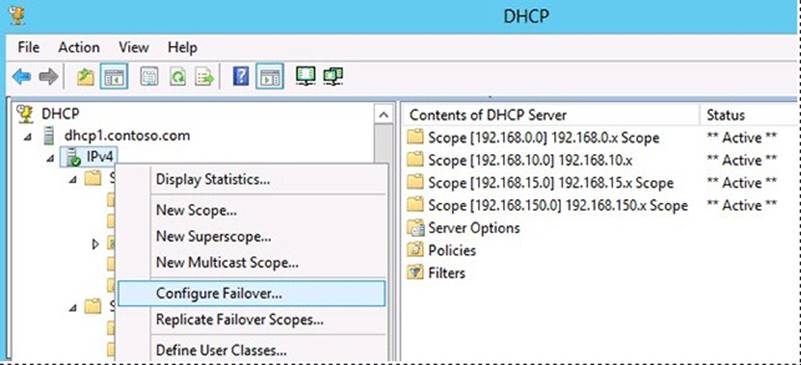
Configure Failover
TheConfigure Failoverwizard guides you through configuring DHCP failover on the selected scope.
Note: The DHCP server failover feature, available in Windows Server 2012 and later, provides the ability to have two DHCP servers provide IP addresses and option configuration to the same subnet or scope, providing for continuous availability of DHCP service to clients.
Incorrect:
Not A. NLB is not related to DHCP scope availability. Not B. DHCP failover requirements include:
DHCP Scopes requirement:
At least one IPv4 DHCP scope must be configured on the primary DHCP server.
The same DHCP scope ID, or an overlapping scope, must not be configured on the failover partner.
Not D. Failover clustering is possibly, but would not minimize administration. Reference: Deploy DHCP Failover
NEW QUESTION 17
HOTSPOT
You have a server named Server1 that runs Windows Server 2012 R2. The volumes on Server1 are configured as shown in the following table.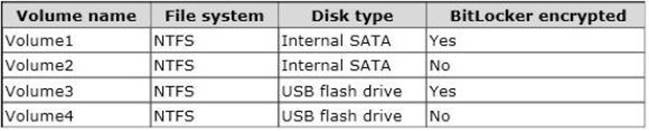
A new corporate policy states that backups must use Windows Azure Online Backup whenever possible.
You need to identify which backup methods you must use to back up Server1. The solution must use Windows Azure Online Backup whenever possible.
Which backup type should you identify for each volume?
To answer, select the appropriate backup type for each volume in the answer area.
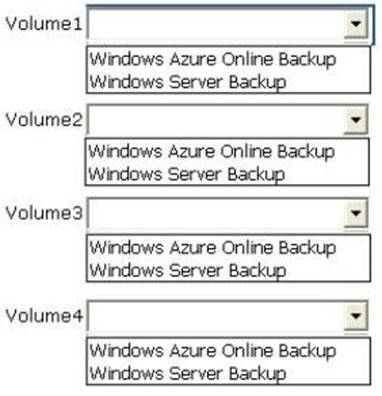
Answer:
Explanation: Box 1: Windows Server Backup
Volume1 is NTFS and on a fixed disk, but Bitlocker is used.
Windows Azure Online Backup cannot backup volume that has Bitlocker.
Box 2: Windows Azure Online Backup
Volume2 is NTFS, on a fixed disk, and Bitlocker is not used. Windows Azure Online Backup can be used.
Box 3: Windows Server Backup
Volume3 is not on a fixed disk. It is on a USB disk. Additionally bitlocker is used.
Windows Azure Online Backup cannot be used. Box 4: Windows Server Backup
Volume3 is not on a fixed disk. It is on a USB disk. Windows Azure Online Backup cannot be used.
Note: You can use Microsoft Azure Backup to back up content stored on fixed NTFS volumes. It cannot be used in the following situations:
Volume is locked by BitLocker Drive Encryption. If BitLocker is enabled on the volume, the volume must be unlocked before it can be backed up.
Drive type is not fixed.
Volume is not formatted with NTFS.
Volume is read-only.
Volume is not currently online. Volume is on a network share.
100% Valid and Newest Version 70-412 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/70-412-dumps.html (New 435 Q&As)
