Master the 70 412 vce content and be ready for exam day success quickly with this 70 412 pdf. We guarantee it!We make it a reality and give you real 70 412 dumps in our Microsoft 70-412 braindumps. Latest 100% VALID mcsa 70 412 at below page. You can use our Microsoft 70-412 braindumps and pass your exam.
Also have 70-412 free dumps questions for you:
NEW QUESTION 1
Your network contains an Active Directory domain named contoso.com.
The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. On Dc1, you open DNS Manager as shown in the exhibit. (Click the Exhibit button.)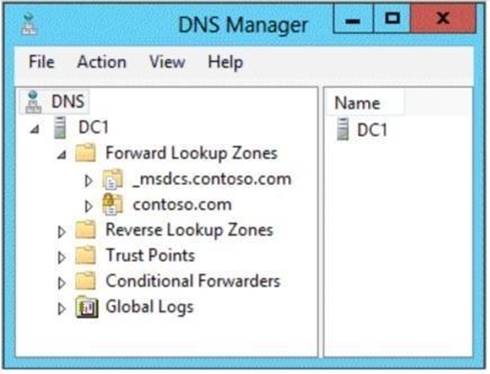
You need to change the replication scope of the contoso.com zone. What should you do before you change the replication scope?
- A. Modify the Zone Transfers settings.
- B. Add DC1 to the Name Servers list.
- C. Add your user account to the Security settings of the zone.
- D. Unsign the zone.
Answer: D
Explanation: Lock icon signifies that the Zone has been signed. Changes to the zone are blocked when signed
http://www.microsoft.com/en-us/download/dlx/ThankYou.aspx?id=29018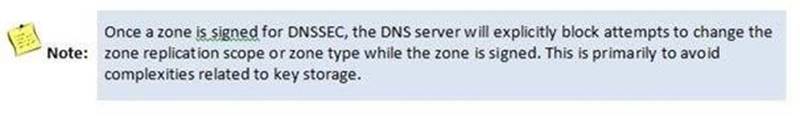
NEW QUESTION 2
You have a DHCP server named Server1.
Server1 has an IP address 192.168.1.2 is located on a subnet that has a network ID of 192.168.1.0/24.
On Server1, you create the scopes shown in the following table.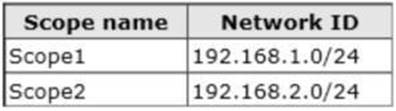
You need to ensure that Server1 can assign IP addresses from both scopes to the DHCP clients on the local subnet.
What should you create on Server1?
- A. A scope
- B. A superscope
- C. A split-scope
- D. A multicast scope
Answer: B
Explanation: A. A scope is an administrative grouping of IP addresses for computers on a subnet that use the Dynamic Host Configuration Protocol (DHCP) service. The administrator first creates a scope for each physical subnet and then uses the scope to define the parameters used by clients.
B. A superscope is an administrative feature of Dynamic Host Configuration Protocol (DHCP) servers running Windows Server 2008 that you can create and manage by using the DHCP Microsoft Management Console (MMC) snap-in. By using a superscope, you can group multiple scopes as a single administrative entity.
D. Multicasting is the sending of network traffic to a group of endpointsdestination hosts. Only those members in the group of endpoints hosts that are listening for the multicast
traffic (the multicast group) process the multicast traffic.
http://technet.microsoft.com/en-us/library/dd759168.aspx http://technet.microsoft.com/en-us/library/dd759152.aspx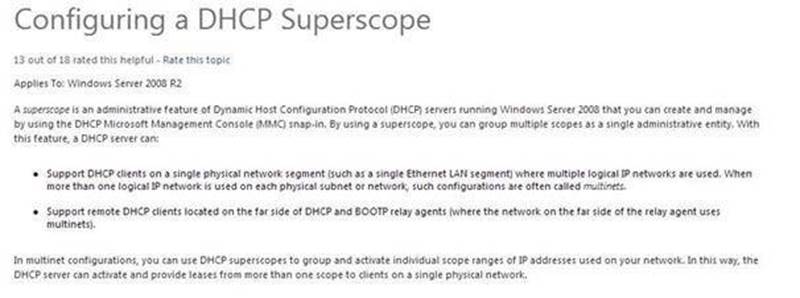
NEW QUESTION 3
You have a server named Server1 that runs Windows Server 2012 R2. You suspect that some protected system files are corrupt.
You need to verify the protected system files on Server1 and replace files that have incorrect versions.
Which tool should you use?
- A. Sfc
- B. Repair-volume
- C. Repair-FileIntegrity
- D. Fsutil
Answer: A
Explanation: Sfc scans and verifies the integrity of all protected system files and replaces incorrect versions with correct versions.
Examples:
To verify the kernel32.dll file, type:
sfc /verifyfile=c:windowssystem32kernel32.dll
To setup offline repair of the kernel32.dll file with an offline boot directory set to d: and offline windows directory set to d:windows, type:
sfc /scanfile=d:windowssystem32kernel32.dll /offbootdir=d: /offwindir=d:windows
Reference: Technet, sfc
https://technet.microsoft.com/en-us/library/ff950779.aspx
NEW QUESTION 4
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. DC1 has the DHCP Server server role installed.
DHCP is configured as shown in the exhibit. (Click the Exhibit button.)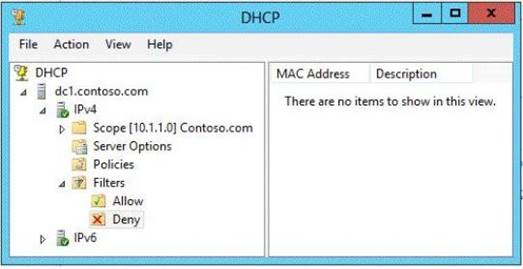
You discover that client computers cannot obtain IPv4 addresses from DC1.
You need to ensure that the client computers can obtain IPv4 addresses from DC1. What should you do?
- A. Activate the scope.
- B. Authorize DC1.
- C. Disable the Allow filters.
- D. Disable the Deny filters.
Answer: C
Explanation: You have enabled the Allow list but haven't entered any MAC addresses, thus everyone is denied. Either Disable the Allow filters or start adding MAC addresses to the Allow filter.
Note: MAC address based filtering allows specific control over which clients have access to DHCP addresses. You can create a list of computers that are allowed to obtain DHCP addresses from the server by adding the client MAC address to the list of allowed client computers. By enabling the allow list, you automatically deny access to the DHCP server addresses to any client computer not on the list.
Reference: DHCP: If the allow list is enabled, MAC address filtering should be populated https://technet.microsoft.com/en-us/library/ee956897(v=ws.10)
NEW QUESTION 5
Your network contains an Active Directory forest. The forest contains one domain named adatum.com. The domain contains three domain controllers. The domain controllers are
configured as shown in the following table.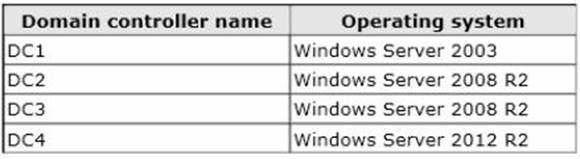
DC2 has all of the domain-wide operations master roles. DC3 has all of the forest-wide operation master roles.
You need to ensure that you can use Password Settings objects (PSOs) in the domain. What should you do first?
- A. Uninstall Active Directory from DC1.
- B. Change the domain functional level.
- C. Transfer the domain-wide operations master roles.
- D. Transfer the forest-wide operations master roles.
Answer: A
Explanation: In Windows Server 2008 and later, you can use fine-grained password policies to specify multiple password policies and apply different password restrictions and account lockout policies to different sets of users within a single domain.
Note: In Microsoft Windows 2000 and Windows Server 2003 Active Directory domains, you could apply only one password and account lockout policy, which is specified in the domain's Default Domain Policy, to all users in the domain. As a result, if you wanted different password and account lockout settings for different sets of users, you had to either create a password filter or deploy multiple domains. Both options were costly for different reasons.
Reference: AD DS Fine-Grained Password and Account Lockout Policy Step-by-Step Guide
NEW QUESTION 6
You have an enterprise certification authority (CA) named CA1. You configure a recovery agent for CA1.
On CA1, you create a new certificate template named CertTemplate1, and then you configure CA1 to allow certificates to be requested based on CertTemplate1.
You need to ensure that new certificates issued based on CertTemplate1 can be recovered.
What should you do?
- A. From the Certificate Templates console, modify the Issuance Requirements settings of CertTemplate1.
- B. From the Certification Authority console, modify the enrollment agents of CA1.
- C. From the Certificate Templates console, modify the Request Handling settings of CertTemplate1.
- D. From the Certification Authority console, modify the certificate managers of CA1.
Answer: C
Explanation: The key archival process takes place when a certificate is issued. Therefore, a certificate template must be modified to archive keys before any certificates are issued based on this template.
See step 7 below.
To configure a certificate template for key archival and recovery
✑ Open the Certificate Templates snap-in.
✑ In the details pane, right-click the certificate template that you want to change, and then click Duplicate Template.
✑ In the Duplicate Template dialog box, click Windows Server 2003
Enterprise unless all of your certification authorities (CAs) and client computers are running Windows Server 2008 R2, Windows Server 2008, Windows 7, or Windows Vista.
✑ In Template, type a new template display name, and then modify any other
optional properties as needed.
✑ On the Security tab, click Add, type the name of the users or groups you want to issue the certificates to, and then click OK.
✑ Under Group or user names, select the user or group names that you just added.
Under Permissions, select the Read and Enroll check boxes, and if you want to automatically issue the certificate, also select the Autoenroll check box.
✑ On the Request Handling tab, select the Archive subject's encryption private
key check box.
✑ If users already have EFS certificates that are not configured for key archival and recovery, click the Superseded Templates tab, clickAdd, and then click the name of the template that you want to replace.
✑ Click OK.
Reference: Configure a Certificate Template for Key Archival https://technet.microsoft.com/en-us/library/cc753826.aspx
NEW QUESTION 7
You have a Hyper-V host named Server1 that runs Windows Server 2012 R2. Server1 contains a virtual machine named VM1 that runs Windows Server 2012 R2.
You fail to start VM1 and you suspect that the boot files on VM1 are corrupt.
On Server1, you attach the virtual hard disk (VHD) of VM1 and you assign the VHD a drive letter of F.
You need to repair the corrupt boot files on VM1. What should you run?
- A. bootrec.exe /rebuildbcd
- B. bootrec.exe /scanos
- C. bcdboot.exe f:windows /s c:
- D. bcdboot.exe c:windows /s f:
Answer: D
Explanation: Enables you to quickly set up a system partition, or to repair the boot environment located on the system partition. The system partition is set up by copying a simple set of Boot Configuration Data (BCD) files to an existing empty partition.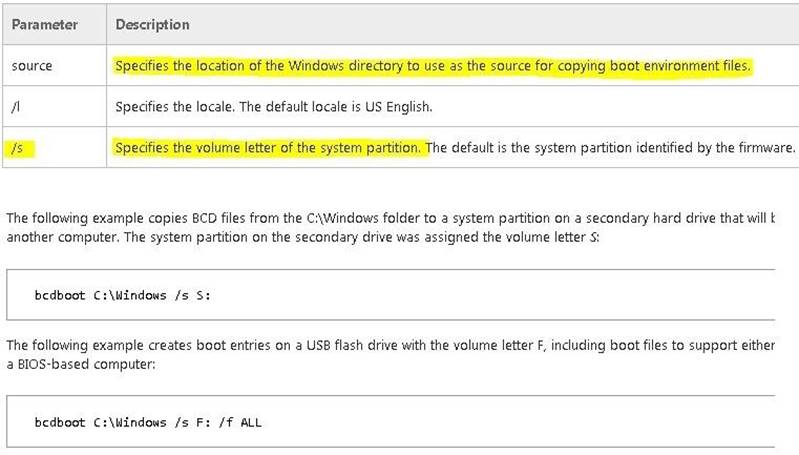
Reference: BCDboot Command-Line Options
NEW QUESTION 8
You have two Windows Server Update Services (WSUS) servers named Server01 and Server02. Server01 synchronizes from Microsoft Update. Server02 synchronizes updates from Server01. Both servers are members of the same Active Directory domain.
You configure Server01 to require SSL for all WSUS metadata by using a certificate issued by an enterprise root certification authority (CA).
You need to ensure that Server02 synchronizes updates from Server01. What should you do on Server02?
- A. From a command prompt, runwsusutil.exe configuresslproxy server02 44.3
- B. From a command prompt, runwsusutil.exe configuressl server01.
- C. From a command prompt, runwsusutil.exe configuresslproxy server01 44.3
- D. From the Update Services console, modify the Update Source and Proxy Server options.
Answer: C
Explanation: We configure server02 to use server01 as an proxy for the updates through the wsusutil.exe configuresslproxy <ssl_proxy_ip_or_name> <port>
Server01 is the ssl_proxy and the port is 443 (the sll port).
Reference: A work-around when using different proxies for HTTP and SSL in WSUS 3.0 SP1
http://blogs.technet.com/b/craigf/archive/2009/05/04/a-work-around-when-using-different- proxies-for-http-and-ssl-in-wsus-3-0-sp1.aspx
NEW QUESTION 9
HOTSPOT
Your company has a main office and a branch office. An Active Directory site exists for each office.
The network contains an Active Directory forest named contoso.com. The contoso.com domain contains three member servers named Server1, Server2, and Server3. All servers run Windows Server 2012 R2.
In the main office, you configure Server1 as a file server that uses BranchCache.
In the branch office, you configure Server2 and Server3 as BranchCache hosted cache servers.
You are creating a Group Policy for the branch office site. Which two Group Policy settings should you configure?
To answer, select the appropriate two settings in the answer area.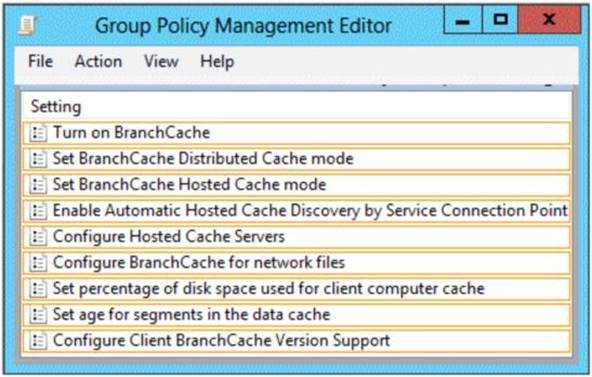
Answer:
Explanation: To use Group Policy to configure clients for hosted cache mode
Step x: In the Turn on BranchCache dialog box, click Enabled, and then click OK.
Step x+1: In the Group Policy Management Editor console, ensure that BranchCache is still selected, and then in the details pane double-click Set BranchCache Hosted Cache mode. The Set BranchCache Hosted Cache mode dialog box opens.
NEW QUESTION 10
Your network contains an Active Directory forest. The forest contains one domain named contoso.com. The domain contains three domain controllers. The domain controllers are configured as shown in the following table.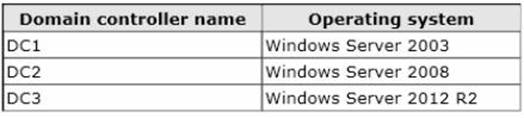
DC1 has all of the operations master roles installed.
You transfer all of the operations master roles to DC2, and then you uninstall Active Directory from DC1.
You need to ensure that you can use Password Settings objects (PSOs) in the domain. What should you do?
- A. Change the domain functional level.
- B. Upgrade DC2.
- C. Run the dcgpofix.exe command.
- D. Transfer the schema master role.
Answer: A
Explanation: The domain functional level must be Windows Server 2008 to use PSO's
Requirements and special considerations for fine-grained password and account lockout policies:
* Domain functional level: The domain functional level must be set to Windows Server 2008 or higher.
Etc.
Incorrect:
Not B. DC2 is also Windows Server 2008.
Not C. Recreates the default Group Policy Objects (GPOs) for a domain Not D. Schema isn't up to right level
Reference: AD DS: Fine-Grained Password Policies http://technet.microsoft.com/en-us/library/cc770394(v=ws.10).aspx
NEW QUESTION 11
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains two DHCP servers named Server1 and Server2. Both servers have multiple IPv4 scopes.
Server1 and Server2 are used to assign IP addresses for the network IDs of 172.20.0.0/16 and 131.107.0.0/16.
You install the IP Address Management (IPAM) Server feature on a server named IPAM1 and configure IPAM1 to manage Server1 and Server2.
Some users from the 172.20.0.0 network report that they occasionally receive an IP address conflict error message.
You need to identify whether any scopes in the 172.20.0.0 network ID conflict with one another.
What Windows PowerShell cmdlet should you run?
To answer, select the appropriate options in the answer area.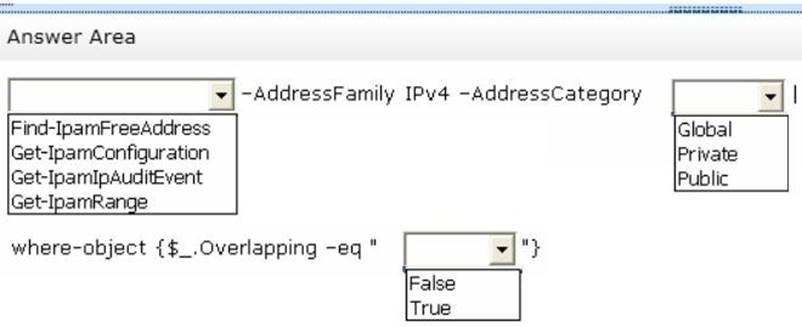
Answer:
Explanation: Type the following command at a Windows PowerShell prompt and press ENTER:
PS C:> Get-IpamRange –AddressFamily IPv4 –AddressCategory Private|where-object
{$_.Overlapping –eq “True”}
The previous command will display any overlapping IP address ranges, if they exist.
NEW QUESTION 12
DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain contains four member servers named Server1, Server2, Servers, and Server4. All servers run Windows Server 2012 R2.
Server1 and Server2 are located in a site named Site1. Server3 and Server4 are located in a site named Site2. The servers are configured as nodes in a failover cluster named Cluster1.
Cluster1 is configured to use the Node Majority quorum configuration.
You need to ensure that Server1 is the only server in Site1 that can vote to maintain quorum.
What should you run from Windows PowerShell?
To answer, drag the appropriate commands to the correct location. Each command may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.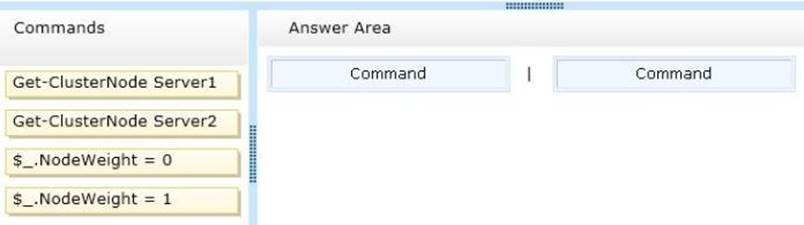
Answer:
Explanation: We remove Server2 from quorum vote by setting it's NodeWeight to 0.
NodeWeight settings are used during quorum voting to support disaster recovery and multi- subnet scenarios for AlwaysOn Availability Groups and SQL Server Failover Cluster Instances.
Example (Powershell)
The following example changes the NodeWeight setting to remove the quorum vote for the “AlwaysOnSrv1” node.
Import-Module FailoverClusters
$node = “AlwaysOnSrv1”
(Get-ClusterNode $node).NodeWeight = 0
NEW QUESTION 13
Your network contains an Active Directory domain named contoso.com.
All servers run Windows Server 2012 R2. The domain contains a file server named Server1.
The domain contains a domain controller named DC1. Server1 contains three shared folders.
The folders are configured as shown in the following table.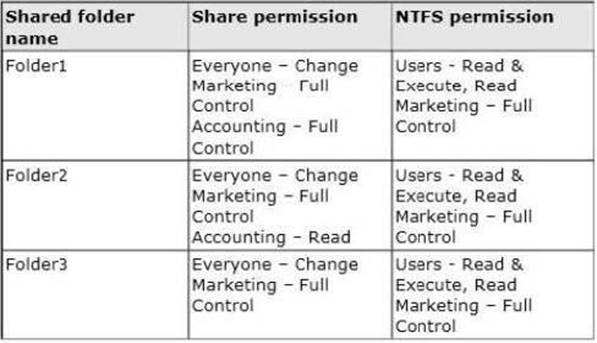
Folder2 has a conditional expression of User.Department= = MMarketing".
You discover that a user named User1 cannot access \Server1folder2. User1 can access
\Server1folderl and \Server1folder3.
You verify the group membership of User1 as shown in the Member Of exhibit. (Click the Exhibit button.)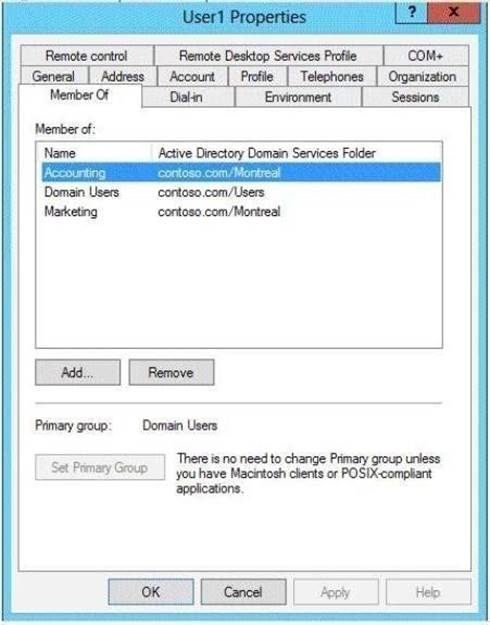
You verify the organization information of User1 as shown in the Organization exhibit. (Click the Exhibit button.)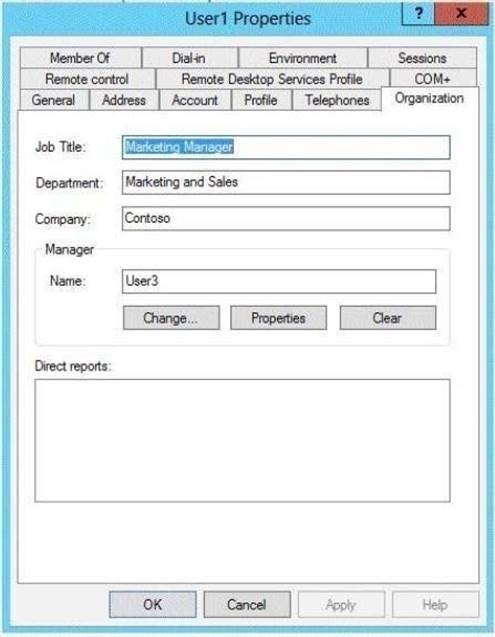
You verify the general properties of User1 as shown in the General exhibit. (Click the Exhibit button.)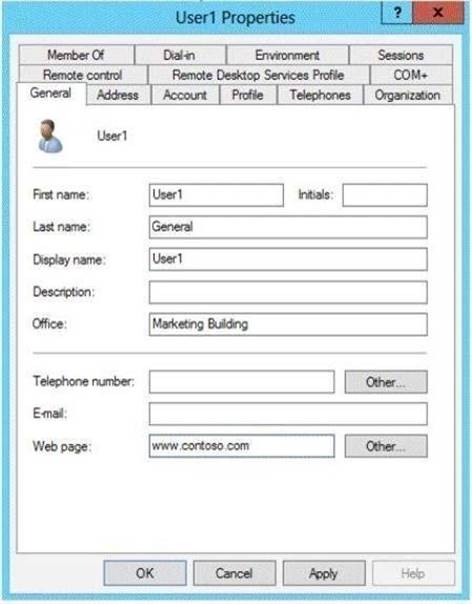
You need to ensure that User1 can access the contents of \Server1folder2. What should you do?
- A. From a Group Policy object (GPO), set the Support for Dynamic Access Control and Kerberos armoring setting to Always provide claims.
- B. Change the department attribute of User1.
- C. Grant the Full Control NTFS permissions on Folder2 to User1.
- D. Remove Userl1from the Accounting global group.
Answer: B
Explanation: Conditional Expression and users Department must match http://technet.microsoft.com/en-us/library/jj134043.aspx
NEW QUESTION 14
Your network contains three servers named HV1, HV2, and Server1 that run Windows Server 2012 R2. HV1 and HV2 have the Hyper-V server role installed. Server1 is a file server that contains 3 TB of free disk space.
HV1 hosts a virtual machine named VM1. The virtual machine configuration file for VM1 is stored in D:VM and the virtual hard disk file is stored in E:VHD.
You plan to replace drive E with a larger volume.
You need to ensure that VM1 remains available from HV1 while drive E is being replaced. You want to achieve this goal by using the minimum amount of administrative effort.
What should you do?
- A. Perform a live migration to HV2.
- B. Add HV1 and HV2 as nodes in a failover cluste
- C. Perform a storage migration to HV2.
- D. Add HV1 and HV2 as nodes in a failover cluste
- E. Perform a live migration to HV2.
- F. Perform a storage migration to Server1.
Answer: D
Explanation: One of the great new features coming in Windows Server 2012 is Storage Migration for Hyper-V. Storage Migration allows an administrator to relocate the source files that make up a virtual machine to another location without any downtime.
Storage Migration creates a copy of the file or files at the new location. Once that is finished, Server 2012 does a final replication of changes and then the virtual machine uses the files in the new location.
Reference: Windows Server 2012 Hyper-V – Part 3: Storage Migration
NEW QUESTION 15
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains two Active Directory sites named Site1 and Site2.
You discover that when the account of a user in Site1 is locked out, the user can still log on to the servers in Site2 for up to 15 minutes by using Remote Desktop Services (RDS).
You need to reduce the amount of time it takes to synchronize account lockout information across the domain.
Which attribute should you modify?
To answer, select the appropriate attribute in the answer area.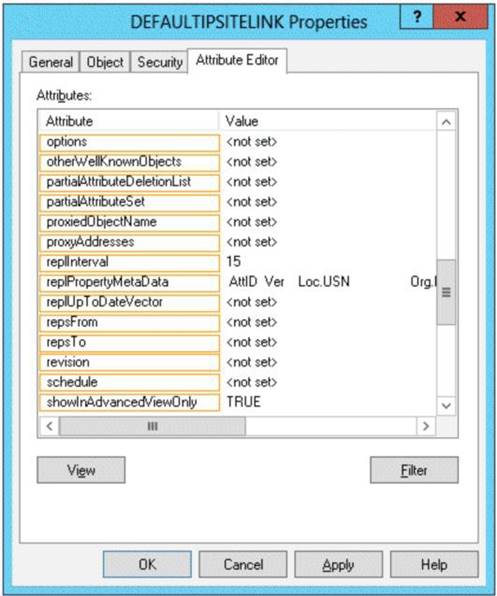
Answer:
Explanation: Explanation/Reference:
Enabling reciprocal replication between two sites involves modifying the options attribute value on the site link object. With this attribute set on the site link, the KCC creates the connections across the link with the appropriate setting that is in effect. Use ADSI Edit to enable reciprocal replication.
NEW QUESTION 16
The root domain of the Adatum forest is Adatum.local. The contoso.com domain tree is part of the Adatum forest.
Don has an account in the australia.contoso.com domain and is signing on to a computer that is a member of the computers.adatum.local domain.
No additional UPNs have been configured.
Which UPN suffix will Don use to sign on to this computer?
- A. @adatum.com
- B. @adatum.local
- C. @computers.adatum.local
- D. @australia.contoso.com
Answer: B
NEW QUESTION 17
HOTSPOTYour network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2.
The domain contains two domain controllers. The domain controllers are configured as shown in the following table.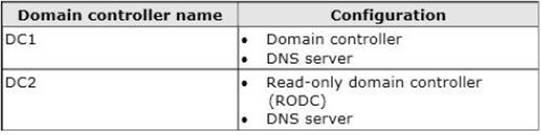
On DC1, you create an Active Directory-integrated zone named Zone1. You verify that Zone1 replicates to DC2.
You use DNSSEC to sign Zone1.
You discover that the updates to Zone1 fail to replicate to DC2. You need to ensure that Zone1 replicates to DC2.
What should you configure on DC1?
To answer, select the appropriate tab in the answer area.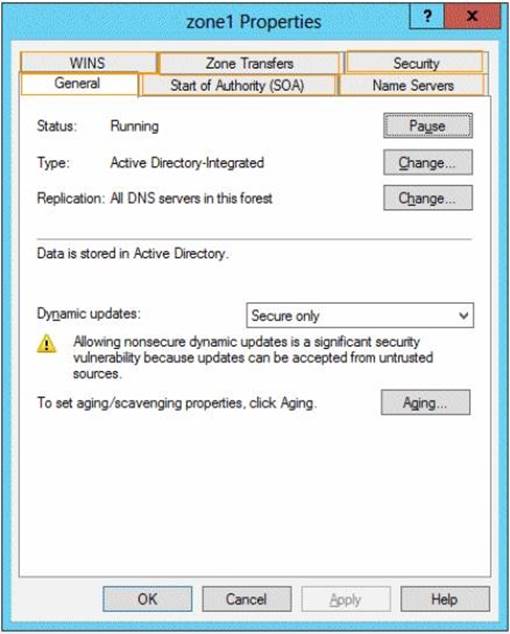
Answer:
Explanation: We most allow and configure zone transfers.
To modify zone transfer settings using the Windows interface
✑ Open DNS Manager.
✑ Right-click a DNS zone, and then clickProperties.
✑ On theZone Transferstab, do one of the following:
✑ If you allowed zone transfers, do one of the following:
100% Valid and Newest Version 70-412 Questions & Answers shared by 2passeasy, Get Full Dumps HERE: https://www.2passeasy.com/dumps/70-412/ (New 435 Q&As)
