70 412 exam are updated and 70 412 dumps are verified by experts. Once you have completely prepared with our 70 412 dumps you will be ready for the real 70-412 exam without a problem. We have 70 412 exam dumps. PASSED 70 412 exam dumps First attempt! Here What I Did.
Free 70-412 Demo Online For Microsoft Certifitcation:
NEW QUESTION 1
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Certificate Services server role installed and is configured to support key archival and recovery.
You create a new Active Directory group named Group1.
You need to ensure that the members of Group1 can request a Key Recovery Agent certificate.
The solution must minimize the permissions assigned to Group1.
Which two permissions should you assign to Group1? (Each correct answer presents part of the solution. Choose two.)
- A. Read
- B. Auto enroll
- C. Write
- D. Enroll
- E. Full control
Answer: AD
Explanation: See step 6 below.
To configure the Key Recovery Agent certificate template
✑ Open the Certificate Templates snap-in.
✑ In the console tree, right-click theKey Recovery Agentcertificate template.
✑ ClickDuplicate Template.
✑ InTemplate, type a new template display name, and then modify any other optional properties as needed.
✑ On theSecuritytab, clickAdd, type the name of the users you want to issue the key recovery agent certificates to, and then clickOK.
✑ UnderGroup or user names, select the user names that you just added.
UnderPermissions, select theReadandEnrollcheck boxes, and then clickOK. Reference: Identify a Key Recovery Agent
NEW QUESTION 2
HOTSPOT
You run Get-ISCSIServerTarget and you receive the following output.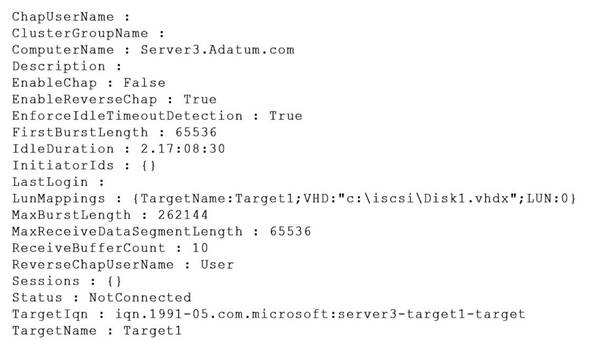
Use the drop-down menus to select the answer choice that completes each statement.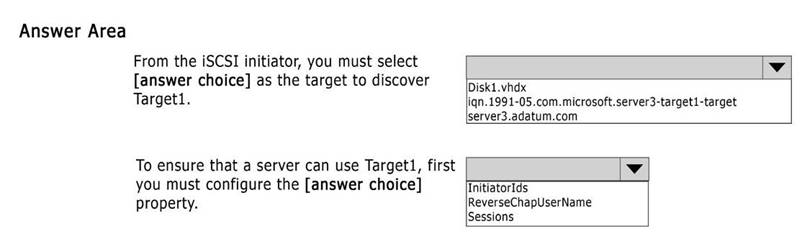
Answer:
Explanation: The Get-IscsiServerTarget command obtains iSCSI targets and their associated properties.
* Usually, an iSCSI participant can be defined by three or four fields:
✑ Hostname or IP Address (e.g., "iscsi.example.com")
✑ Port Number (e.g., 3260)
✑ iSCSI Name (e.g., the IQN "iqn.2003-01.com.ibm:00.fcd0ab21.shark128")
✑ An optional CHAP Secret (e.g., "secretsarefun")
-iSCSI Qualified Name (IQN) the fields are:
literal iqn (iSCSI Qualified Name)
date (yyyy-mm) that the naming authority took ownership of the domain
reversed domain name of the authority (e.g. org.alpinelinux, com.example, to.yp.cr) Optional ":" prefixing a storage target name specified by the naming authority.
* -InitiatorId<InitiatorId>
Specifies the iSCSI initiator identifiers (IDs) to which the iSCSI target is assigned.
Use this parameter to filter out the iSCSI Server Target object which can be accessed by the given iSCSI initiator.
The format of this parameter is IdType:Value.
The acceptable values for this parameter are: DNSName, IPAddress, IPv6Address, IQN, or MACAddress.
NEW QUESTION 3
HOTSPOT
You build a test environment. The test environment contains one Active Directory forest. The forest contains a single domain named contoso.com. The domain contains the servers configured as shown in the following table.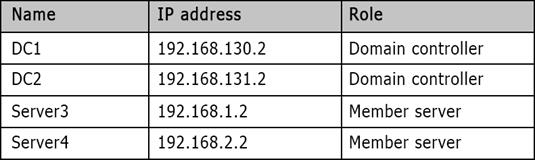
You run the following commands. New-ADReplicationSite Site1
New-ADReplicationSite Site2
New-ADReplicationSubnet -Name “192.168.1.0/24” -Site Site1 New-ADReplicationSubnet -Name “192.168.2.0/24” -Site Site2
New-ADReplicationSiteLink -Name “SiteLink1” –SitesIncluded Site1,Site2 -Cost 100 - ReplicationFrequencyInMinutes 15
You promote Server3 and Server4 to domain controllers by using the default options. Use the drop-down menus to select the answer choice that completes each statement.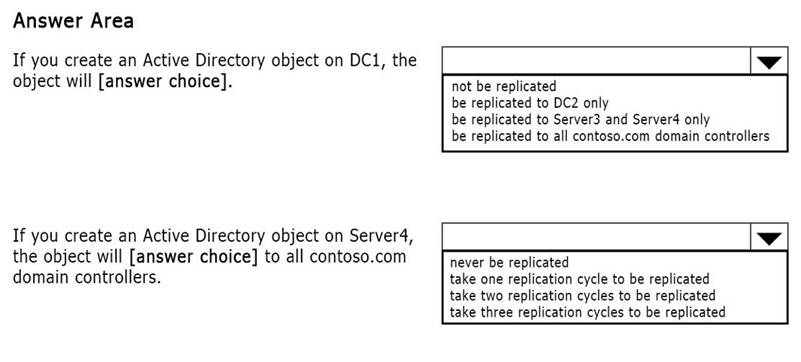
Answer:
Explanation: *Replication will only occur between Server3 and Server4.
* Values that can be transferred in one replication cycle (replication of the current set of updates between a source and destination domain controller): no limit.
NEW QUESTION 4
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2.
Server1 and Server2 have the Hyper-V server role installed. The servers are configured as shown in the following table.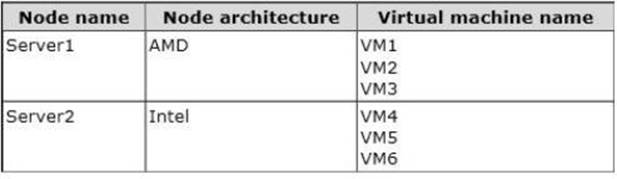
You add a third server named Server3 to the network. Server3 has Intel processors.
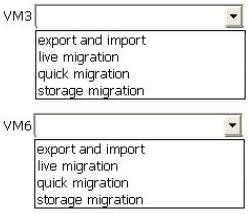
You need to move VM3 and VM6 to Server3. The solution must minimize downtime on the virtual machines.
Which method should you use to move each virtual machine?
To answer, select the appropriate method for each virtual machine in the answer area.
Answer:
Explanation: VM3: export/import is the only option due to different processor manufacturers VM6: Live migration can be used as both have Intel CPU's Live Storage Migration requires same processor manufacturers Live migration requires same processor manufacturers
Incorrect:
Quick migration has downtime
NEW QUESTION 5
HOTSPOT
Your network contains one Active Directory forest named contoso.com. The forest contains the domain controllers configured as shown in the following table.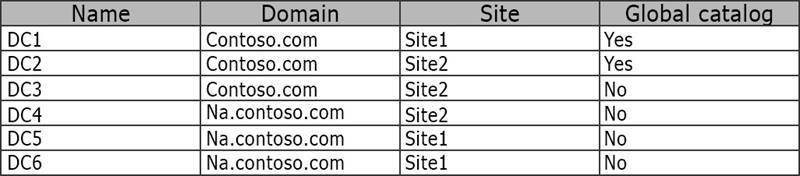
You perform the following actions:
✑ Create a file named File1.txt in the SYSVOL folder on DC1.
✑ Create a user named User1 on DC4.
You need to identify on which domain controller or controllers a copy of each object is stored.
What should you identify? To answer, select the appropriate options in the answer area.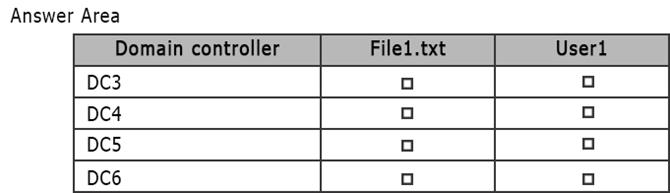
Answer:
Explanation: 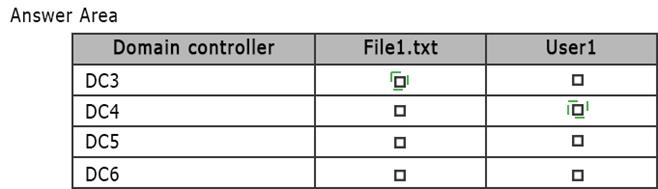
NEW QUESTION 6
You have a server named LON-DC1 that runs Windows Server 2012 R2.
An iSCSI virtual disk named VirtuahSCSIl.vhd exists on LON-DC1 as shown in the exhibit. (Click the Exhibit button.)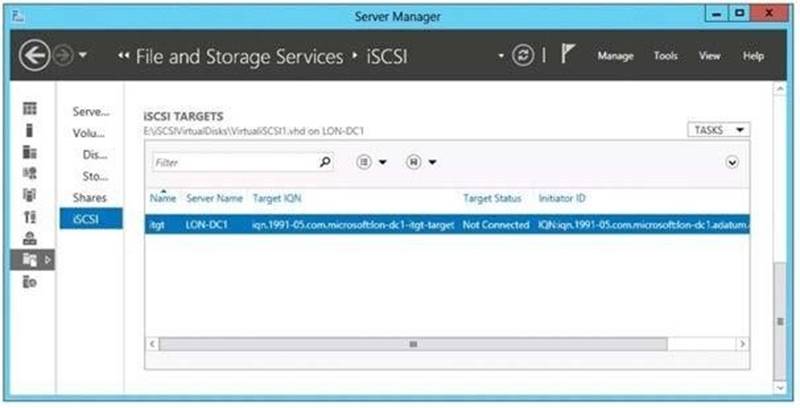
You create a new iSCSI virtual disk named VirtualiSCSI2.vhd by using the existing itgt iSCSI target.
VirtualiSCSIl.vhd is removed from LON-DC1.
You need to assign VirtualiSCSI2.vhd a logical unit value of 0. What should you do?
- A. Run the Set-IscsiVirtualDisk cmdlet and specify the -DevicePath parameter.
- B. Run the iscsicpl command and specify the virtualdisklun parameter.
- C. Modify the properties of the itgt ISCSI target.
- D. Run the Set-VirtualDisk cmdlet and specify the -Uniqueld parameter.
Answer: D
Explanation: Set-VirtualDisk
Modifies the attributes of an existing virtual disk. Applies To: Windows Server 2012 R2
-UniqueId<String>
Specifies an ID used to uniquely identify a Disk object in the system. The ID persists through restarts.
Note: Logical unit numbers (LUNs) created on an iSCSI disk storage subsystem are not directly assigned to a server. For iSCSI, LUNs are assigned to logical entities called targets.
Incorrect:
Not A: Set-IscsiVirtualDisk
Modifies the settings for the specified iSCSI virtual disk.
-Path<String> (alias: DevicePath)
Specifies the path of the virtual hard disk (VHD) file that is associated with the iSCSI virtual disk. Filter the iSCSI Virtual Disk object using this parameter. Not B: iscsicpl.exe could is the Microsoft iSCSI Initiator Configuration Tool. Microsoft Internet iSCSI Initiator enables you to connect a host computer that is running Windows 7 or Windows Server 2008 R2 to an external iSCSI-based storage array through an Ethernet network adapter.
NEW QUESTION 7
You have five servers that run Windows Server 2012 R2. The servers have the Failover Clustering feature installed. You deploy a new cluster named Cluster1. Cluster1 is configured as shown in the following table.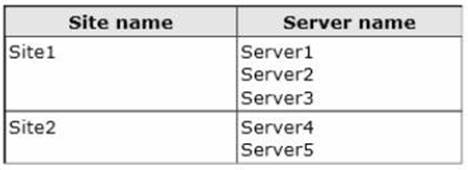
Server1, Server2, and Server3 are configured as the preferred owners of the cluster roles. Dynamic quorum management is disabled.
You plan to perform hardware maintenance on Server3.
You need to ensure that if the WAN link between Site1 and Site2 fails while you are performing maintenance on Server3, the cluster resource will remain available in Site1.
What should you do?
- A. Add a file share witness in Site1.
- B. Enable DrainOnShutdown on Cluster1.
- C. Remove the node vote for Server4 and Server5.
- D. Remove the node vote for Server3.
Answer: C
Explanation: Recommended Adjustments to Quorum Voting
When enabling or disabling a given WSFC (Windows Server Failover Clustering) node’s vote, follow these guidelines:
* Exclude secondary site (here site2) nodes (here server4 and server5). In general, do not give votes to WSFC nodes that reside at a secondary disaster recovery site. You do not want nodes in the secondary site to contribute to a decision to take the cluster offline when there is nothing wrong with the primary site.
Reference: WSFC Quorum Modes and Voting Configuration (SQL Server)
NEW QUESTION 8
DRAG DROP
You have a server that runs Windows Server 2012 R2. You create a new work folder named Share1.
You need to configure Share1 to meet the following requirements:
✑ Ensure that all synchronized copies of Share1 are encrypted.
✑ Ensure that clients synchronize to Share1 every 30 minutes.
✑ Ensure that Share1 inherits the NTFS permissions of the parent folder.
Which cmdlet should you use to achieve each requirement?
To answer, drag the appropriate cmdlets to the correct requirements. Each cmdlet may be
used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.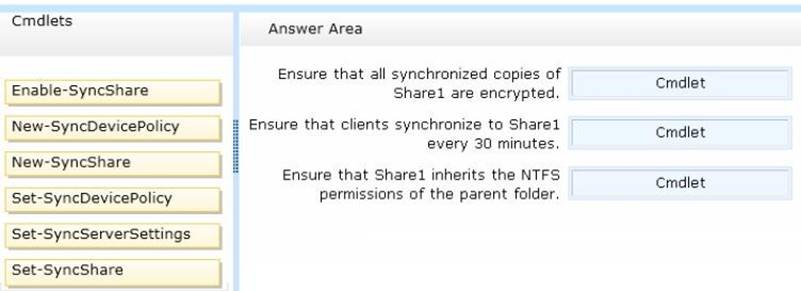
Answer:
Explanation: * (box 1) Set-SyncShare
The Set-SyncShare cmdlet modifies the settings for a sync share.
/ parameter: -RequireEncryption<Boolean>
Indicates whether the sync server requests that the contents of Work Folders be encrypted
on each PC and device that accesses the sync share.
* (box 2) Set-SyncServerSettings
Parameter: -MinimumChangeDetectionMins<UInt32>
Specifies the time, in minutes, before the Sync Share server detects changes on devices and syncs the client and server.
* (box 3): Example: Modify a sync share to enable inherited permissions This command modifies settings on the share named Share01, and sets
KeepParentFolderPermission to enable the share to inherit permissions from the parent folder.
Windows PowerShell
PS C:> Set-SyncShare Share01 -KeepParentFolderPermission
NEW QUESTION 9
Your network contains two Web servers named Server1 and Server2. Both servers run Windows Server 2012 R2.
Server1 and Seiver2 are nodes in a Network Load Balancing (NLB) cluster. The NIB cluster contains an application named App1 that is accessed by using the URL http://app1.contoso.com.
You plan to perform maintenance on Server1.
You need to ensure that all new connections to App1 are directed to Server2. The solution must not disconnect the existing connections to Server1.
What should you run?
- A. The Stop-NlbCluster cmdlet
- B. The nlb.exe stop command
- C. The Suspend-NlbCluster cmdlet
- D. The nlb.exe suspend command
Answer: A
Explanation: The Stop-NlbClusterNode cmdlet stops a node in an NLB cluster. When you use the stop the nodes in the cluster, client connections that are already in progress are interrupted. To avoid interrupting active connections, consider using the -drain parameter, which allows the node to continue servicing active connections but disables all new traffic to that node.
NEW QUESTION 10
You have a file server named FS1 that runs Windows Server 8. Data Deduplication is enabled on FS1.
You need to configure Data Deduplication to run at a normal priority from 20:00 to 06:00 daily.
What should you configure?
- A. File and Storage Services in Server Manager
- B. The Data Deduplication process in Task Manager
- C. Disk Management in Computer Management
- D. The properties of drive C
Answer: A
Explanation: In Windows Server 2012 R2, deduplication can be enabled locally or remotely by using Windows PowerShell or Server Manager.
http://technet.microsoft.com/en-us/library/hh831700.aspx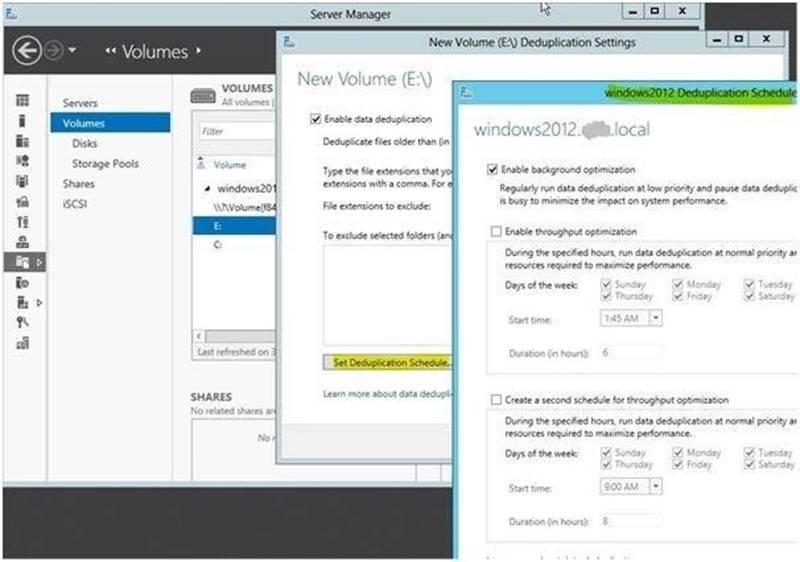
NEW QUESTION 11
Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2.
You install the DHCP Server server role on Server1 and Server2. You install the IP Address Management (IPAM) Server feature on Server1.
You notice that you cannot discover Server1 or Server2 in IPAM.
You need to ensure that you can use IPAM to discover the DHCP infrastructure.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
- A. On Server2, create an IPv4 scope.
- B. On Server1, run the Add-IpamServerInventory cmdlet.
- C. On Server2, run the Add-DhcpServerInDc cmdlet
- D. On both Server1 and Server2, run the Add-DhcpServerv4Policy cmdlet.
- E. On Server1, uninstall the DHCP Server server role.
Answer: BC
Explanation: B. The Add-IpamServerInventory cmdlet adds a new infrastructure server to the IP Address Management (IPAM) server inventory. Use the fully qualified domain name (FQDN) of the server to add to the server inventory.
C. TheAdd-DhcpServerInDCcmdlet adds the computer running the DHCP server service to the list of authorized Dynamic Host Configuration Protocol (DHCP) server services in the Active Directory (AD). A DHCP server service running on a domain joined computer needs to be authorized in AD so that it can start leasing IP addresses on the network.
Reference: Add-IpamServerInventory; Add-DhcpServerInDC
NEW QUESTION 12
You are employed as a network administrator at ABC.com. ABC.com has an active directory domain named ABC.com.
All servers including domain controllers on the ABC.com network have Windows Server 2012 R2 installed.
ABC.com has its headquarters in London and an office in paris.
The London Office has a domain controller named server1,which is configured as a writeable domain controller that servers as a Global catalog server and a DNS server.
Server1 is configured to host an Active Directory-integrated zone for ABC.com.
The Paris office has a Read-Only domain controller (RODC) named server2 which servers as a Global catalog server.
After installing the DNS server role on server2, you want to make sure that the ABC.com zone is replicated to server2 via active directory replication.
Which of the following actions should you take?
- A. You should consider making use of Active Directory Sites and Services to Configured replication
- B. You should consider making use of replmon.exe to configure replication.
- C. You should consider making use of repadmin.exe to configure replication
- D. You should consider making use of Active Directory Schema To configure replication
Answer: A
NEW QUESTION 13
HOTSPOT
Your network contains an Active Directory domain named adatum.com. All servers run Windows Server 2012 R2. All domain controllers have the DNS Server server role installed.
You have a domain controller named DC1.
On DC1, you create an Active Directory-integrated zone named adatum.com and you sign the zone by using DNSSEC.
You deploy a new read-only domain controller (RODC) named RODC1. You need to ensure that the contoso.com zone replicates to RODC1. What should you configure on DC1?
To answer, select the appropriate tab in the answer area.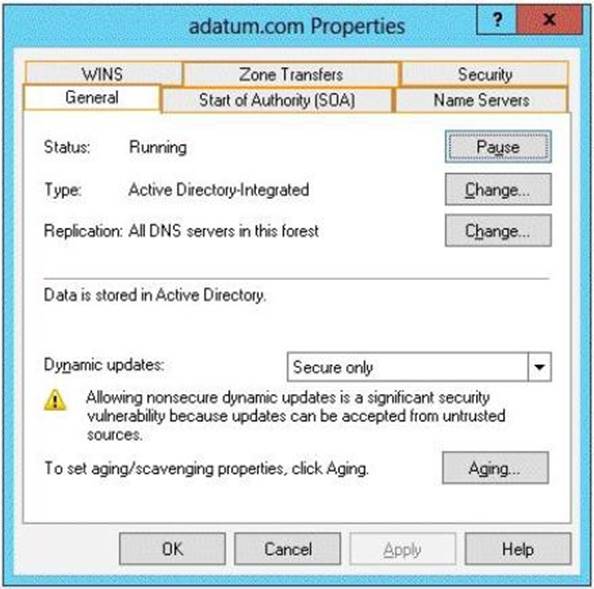
Answer:
Explanation: For additional servers to host a zone, zone transfers are required to replicate and synchronize all copies of the zone used at each server configured to host the zone.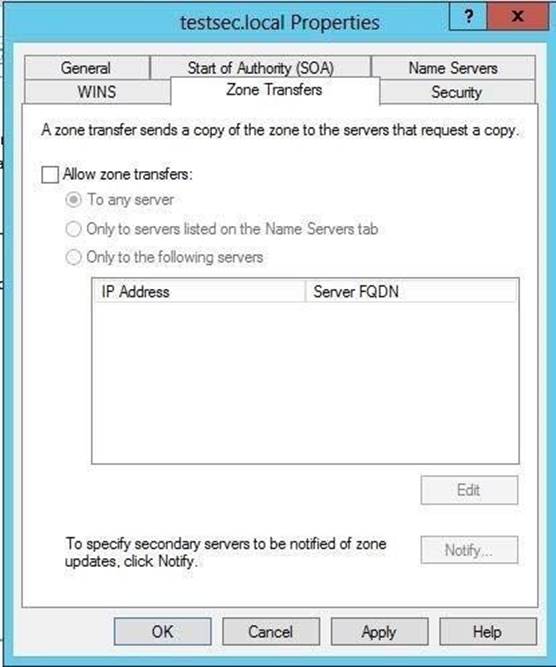
NEW QUESTION 14
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. The forest contains three Active Directory sites named SiteA, SiteB, and SiteC. The sites contain four domain controllers. The domain controllers are configured as shown in the following table.
An IP site link exits between each site.
You discover that the users in SiteC are authenticated by the domain controllers in SiteA and SiteB.
You need to ensure that the SiteC users are authenticated by the domain controllers in SiteB, unless all of the domain controllers in SiteB are unavailable.
What should you do?
- A. Create an SMTP site link between SiteB and SiteC.
- B. Decrease the cost of the site link between SiteB and SiteC.
- C. Disable site link bridging.
- D. Create additional connection objects for DC1 and DC2.
Answer: B
Explanation: By decreasing the site link cost between SiteB and SiteC the SiteC users would be authenticated by SiteB rather than by SiteA.
NEW QUESTION 15
Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 and Server2 have the Hyper-V server role installed. Server1 and Server2 are configured as Hyper-V replicas of each other.
Server2 hosts a virtual machine named VM5. VM5 is replicated to Server1.
You need to verify whether the replica of VM5 on Server1 is functional. The solution must ensure that VM5 remains accessible to clients.
What should you do from Hyper-V Manager?
- A. On Server1, execute a Planned Failover.
- B. On Server1, execute a Test Failover.
- C. On Server2, execute a Planned Failover.
- D. On Server2, execute a Test Failover.
Answer: B
Explanation: Test Failover (TFO) is an operation initiated on your replica virtual machine (in this scenario on Server1) which allows you to test the sanity of the virtualized workload without interrupting your production workload or ongoing replication.
TFO is performed on the replica virtual machine by right-clicking on the VM and choosing the Test Failover operation (either from the Hyper-V Manager or from the Failover Clustering Manager).
Reference: Types of failover operations in Hyper-V Replica – Part I – Test Failover.
NEW QUESTION 16
HOTSPOT
Your network contains one Active Directory domain.
The domain contains an enterprise certification authority (CA).
You need to ensure that members of a group named Group1 can issue certificates for the User certificate template only.
Which two tabs should you use to perform the configuration? To answer, select the appropriate tabs in the answer area.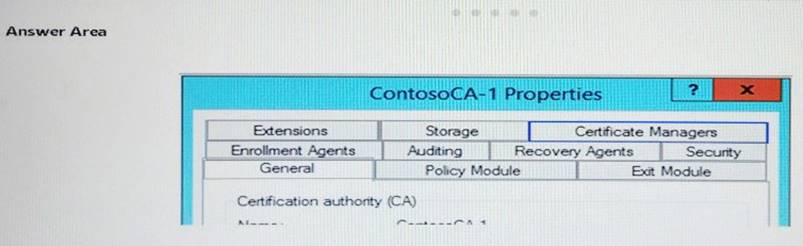
Answer:
Explanation: To configure certificate manager restrictions for a CA
✑ Open the Certification Authority snap-in, and right-click the name of the CA.
✑ Click Properties, and then click the Security tab.
✑ Verify that the user or group that you have selected has Issue and Manage Certificates permission. If they do not yet have this permission, select
the Allow check box, and then click Apply.
✑ Click the Certificate Managers tab.
✑ Click Restrict certificate managers, and verify that the name of the group or user is displayed.
✑ Under Certificate Templates, click Add, select the template for the certificates that you want this user or group to manage, and then click OK. Repeat this step until you have selected all certificate templates that you want to allow this certificate manager to manage.
✑ Under Permissions, click Add, type the name of the client for whom you want the certificate manager to manage the defined certificate types, and then click OK.
✑ If you want to block the certificate manager from managing certificates for a specific user, computer, or group, under Permissions, select this user, computer, or group, and clickDeny.
✑ When you are finished configuring certificate manager restrictions, click OK or Apply.
NEW QUESTION 17
Your network contains three servers named Server1, Server2, and Server3. All servers run Windows Server 2012 R2.
You need to ensure that Server1 can provide iSCSI storage for Server2 and Server3. What should you do on Server1?
- A. Start the Microsoft iSCSI Initiator Service and configure the iSCSI Initiator Properties.
- B. Install the iSNS Server service feature and create a Discovery Domain.
- C. Install the Multipath I/O (MPIO) feature and configure the MPIO Properties.
- D. Install the iSCSI Target Server role service and configure iSCSI targets.
Answer: D
Explanation: iSCSI Target Server: The server runs the iSCSI Target. It is also the iSCSI Target role name in Windows Server 2012.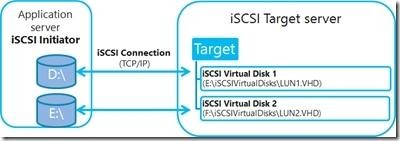
Note:
iSCSI: it is an industry standard protocol allow sharing block storage over the Ethernet. The server shares the storage is called iSCSI Target. The server (machine) consumes the storage is called iSCSI initiator. Typically, the iSCSI initiator is an application server. For example, iSCSI Target provides storage to a SQL server, the SQL server will be the iSCSI initiator in this deployment.
Target: It is an object which allows the iSCSI initiator to make a connection. The Target keeps track of the initiators which are allowed to be connected to it. The Target also keeps track of the iSCSI virtual disks which are associated with it. Once the initiator establishes the connection to the Target, all the iSCSI virtual disks associated with the Target will be accessible by the initiator.
Recommend!! Get the Full 70-412 dumps in VCE and PDF From 2passeasy, Welcome to Download: https://www.2passeasy.com/dumps/70-412/ (New 435 Q&As Version)
