Certleader offers free demo for 210-065 exam. "Implementing Cisco Video Network Devices v1.0", also known as 210-065 exam, is a Cisco Certification. This set of posts, Passing the Cisco 210-065 exam, will help you answer those questions. The 210-065 Questions & Answers covers all the knowledge points of the real exam. 100% real Cisco 210-065 exams and revised by experts!
Free demo questions for Cisco 210-065 Exam Dumps Below:
NEW QUESTION 1
Refer to the exhibit.
Which system does this web user interface refer to?
- A. Cisco Unified Communications Manager
- B. Cisco Video Communications Server
- C. Cisco Digital Media Manager
- D. Cisco TelePresence Management Suite
Answer: D
NEW QUESTION 2
What is the min distance for 52" monitor?
- A. 1.5m
- B. 2m
- C. 2.5 m
- D. 3m
Answer: B
NEW QUESTION 3
Refer to the exhibit.
When this alarm is seen, what is the maximum number of registrations that a Cisco VCS can support?
- A. 2500
- B. 50
- C. 3
Answer: C
NEW QUESTION 4
A company just acquired a Cisco MCU 5300 for multi videoconferencing. The networking engineer must create a conference. To which tab does the engineer go to create a conference?
- A. Endpoints
- B. Conferences
- C. Network
- D. Settings
Answer: B
Explanation:
In this tutorial the instruction ‘Go to Conferences > Move participants’ means click the Conferences link on the menu bar and then click the Move participants tab.
https://www.cisco.com/c/dam/en/us/td/docs/telepresence/infrastructure/mcu/user_guide/Cisco_TelePresence_M
NEW QUESTION 5
An engineer is configuring mobile and remote access. Which three configuration tasks should the engineer perform? (Choose three.)
- A. Manually configure a Cisco Unified Communications Manager neighbor zone on the Cisco Expressway Core.
- B. Add the Cisco Unified Communications Manager root certificate to the Cisco Expressway Core CTL.
- C. Enable TLS verify mode for the traversal zone.
- D. Add the Cisco Unified Communications domain before enabling services on the Cisco Expressway Core.
- E. Enable H.323 on the Cisco Unified Communications Manager neighbor zone.
- F. Add the Cisco Expressway Edge root certificate to the Cisco Unified Communications Manager CTL.
Answer: BCD
NEW QUESTION 6
When you are on a call that is hosted on a Cisco TelePresence MCU, which function is enabled when you enter the numeric sequence *6?
- A. request the floor
- B. mute/unmute audio
- C. merge another call
- D. cycle layout options
Answer: B
NEW QUESTION 7
A technician is trying to troubleshoot real-time call information from the CLI of a VCS. Which command should the technician enter?
- A. xstatus
- B. xconfiguration
- C. xfeedback
- D. xhistory
- E. xcommand
Answer: C
NEW QUESTION 8
Which two features are available on a Cisco TelePresence Server that are not available on a Cisco TelePresence MCU? (Choose two.)
- A. auto-attendant conference menu
- B. automatic lecture mode
- C. virtualization
- D. multiscreen endpoint support
- E. multiple layouts
Answer: CE
Explanation:
https://supportforums.cisco.com/t5/telepresence/what-is-the-difference-between-mcu-cisco-telepresence-server/t
NEW QUESTION 9
Refer to the exhibit.
Which option enables you to create a system snapshot?
- A. Status
- B. System
- C. Configuration
- D. Applications
- E. Users
- F. Maintenance
Answer: F
NEW QUESTION 10
Which component of the Cisco Digital Media Suite is responsible for transcoding and transrating?
- A. Cisco DMD
- B. Cisco TMS
- C. Cisco MXE
- D. Cisco DMM
Answer: C
NEW QUESTION 11
ACisco SX20 is registered to Cisco Unified Communications Manager. It cannot place calls. It is configured with SIP URI 1007 and when traces are run, SIP Forbidden and Unknown calling DN errors are found. Which statement describes the problem?
- A. The wrong network IP address is assigned to device.
- B. The ACL is blocking port 5060 from device.
- C. H.323 is not configured correctly.
- D. SIP URI does not contain IP address or hostname.
Answer: D
NEW QUESTION 12
Which option is the Cisco recommended layout if cascading is being used?
- A. Enhanced Continuous Presence
- B. Full Participant
- C. Continuous Presence
- D. Active Speaker
Answer: C
NEW QUESTION 13
In this item, you will need to use all information presented to you to successfully answer the question.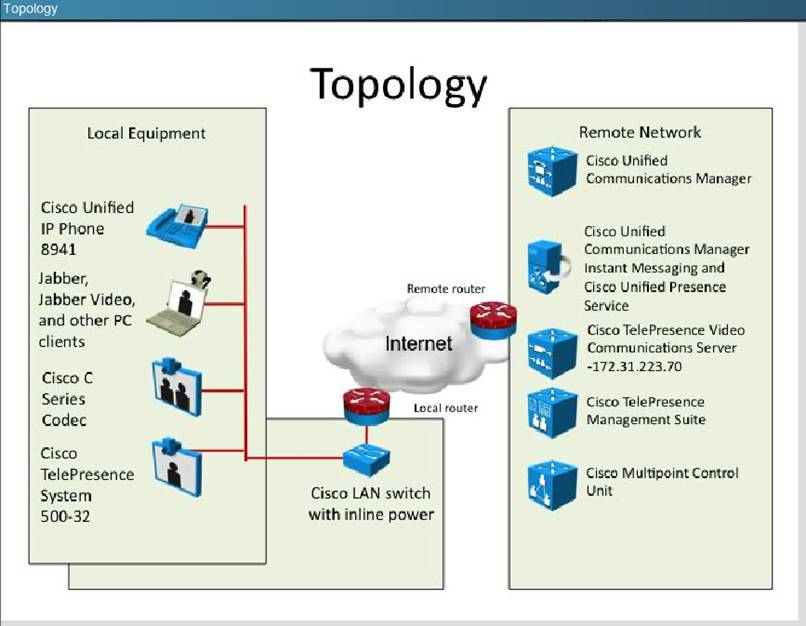
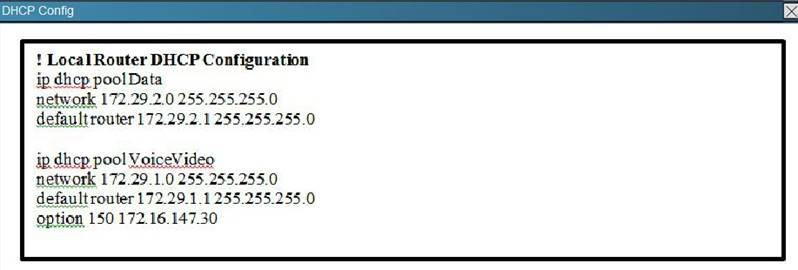
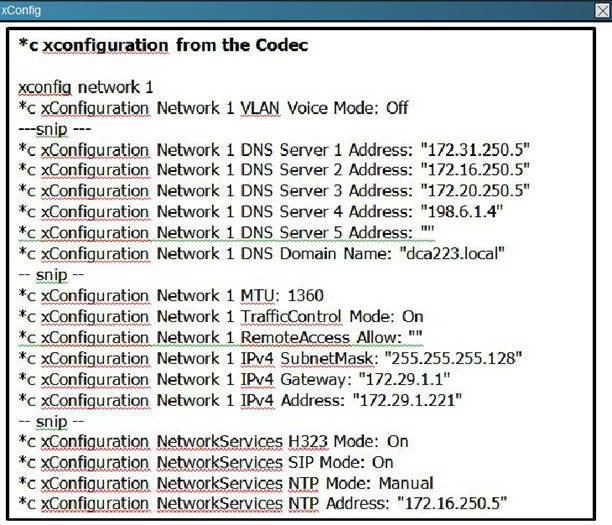
The C-Series endpoint (codec) does not register with the Video Communication Server that is located in a different network. Based on the exhibits, what could be causing the issue?
- A. The subnet mask on the codec is incorrect.
- B. The ip address of the codec is incorrect.
- C. The interface that the codec is in is in the wrong VLAN.
- D. The codec did not receive a DHCP address from the DHCP server.
Answer: A
Explanation:
The subnet mask configured on the codec is 255.255.255.128, when it should be 255.255.255.0.
NEW QUESTION 14
When placing a call from Cisco Jabber Video for TelePresence to the Cisco TelePresence System Codec C40, which FECCs are available?
- A. Only zoom-in and zoom-out are available.
- B. Only left and right are available.
- C. Only up and down are available.
- D. No FECC is available.
- E. Left, right, up, down, zoom-in, and zoom-out are all available.
Answer: E
NEW QUESTION 15
Which statement is true about the Cisco TelePresence System 500-32 system regarding the HVAC needs for the room where it is installed?
- A. The system does not require any additional requirements above the normal HVAC requirements for the room.
- B. You must supply additional cooling requirements for the room.
- C. You must supply a room that has energy-efficient lighting to reduce the temperature of the room.
- D. The temperature of the room will be 10 to 20 degrees warmer than the rest of the building.
Answer: A
NEW QUESTION 16
Which two of these support an ad-hoc conference call? (Choose two.)
- A. Cisco TelePresence Multiway with Cisco TelePresence Multipoint Control Unit and Cisco TelePresenceVideo Communications Server
- B. using the Cisco TelePresence Management Suite Scheduler to schedule a conference call to start in 5 minutes
- C. using the Booking tab in the Cisco TelePresence Management Suite to configure a new conference
- D. using the tab Administrative Tools > Configuration > Conference Settings in the Cisco TelePresence Management Suite
- E. pressing the conference button on a Cisco Unified IP Phone 8941 to conference in a third call
Answer: AE
NEW QUESTION 17
A company acquired immersive Cisco TelePresence devices and they are setting them up in a dedicated Cisco TelePresence room. Which two options are recommendations for the lighting of the room? (Choose two.)
- A. direct lighting
- B. lighting of 5000K to 5100K
- C. color rendering index of 82 and above
- D. lighting of 4000K to 4100K
- E. facial lighting between 400 to 600 lux
Answer: CD
NEW QUESTION 18
Refer to the exhibit.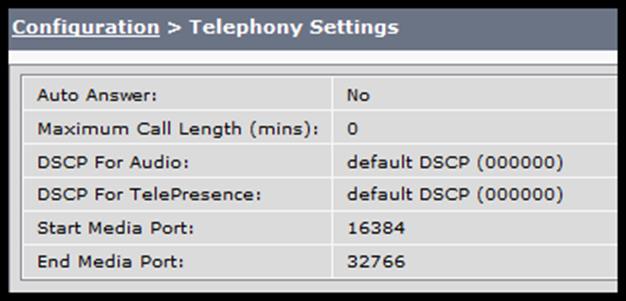
Users in a Cisco TelePresence room report audio and video quality issues. You have been asked to troubleshoot the issue. You log in to the endpoint GUI and check telephony settings. Which option would you recommend to resolve the issue?
- A. Audio/video quality issues are generally due to low bandwidt
- B. Contact your carrier to increase the bandwidth.
- C. "DSCP For TelePresence" is not correc
- D. Configure the correct value via codec GUI.
- E. "DSCP For Audio" is not correc
- F. Configure the correct value via codec GUI.
- G. DSCP values are correc
- H. Check the QoS configuration on the router.
- I. The "DSCP For TelePresence" and "DSCP For Audio" values are not correc
- J. Configure the correct value in codec GUI.
- K. The "DSCP For TelePresence" and "DSCP For Audio" values are not correc
- L. Configure the correct value in the Cisco Unified Communications Manager service parameter.
Answer: F
NEW QUESTION 19
Which well-known port is used to access the Cisco IP Video Surveillance Operations Manager via a secure, ActiveX web session?
- A. 20
- B. 80
- C. 421
- D. 434
- E. 443
- F. 8080
Answer: E
NEW QUESTION 20
In a Multiway call escalation, which SIP message is sent from the Multiway initiator to the participants to provide the bridge URI?
- A. TRANSFER
- B. REFER
- C. REDIRECT
- D. 200 OK
Answer: B
NEW QUESTION 21
Refer to the exhibit.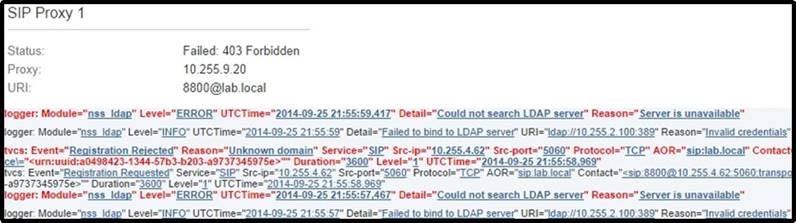
A network engineer is attempting to register a Cisco TelePresence endpoint to a Cisco VCS. What is the most likely cause of this failure?
- A. The lab.local SIP domain is not configured in the Cisco VCS allow list for registration.
- B. The Cisco VCS failed to bind to the LDAP server, which is where the lab.local SIP domain is learned.
- C. The lab.local SIP domain does not exist on the Cisco VCS.
- D. The endpoint does not have the proper port assignments configured for SIP signaling.
- E. The endpoint uses the TCP protocol and the Cisco VCS is configured to allow only TLS for SIP registrations.
Answer: C
NEW QUESTION 22
ACisco engineer needs to provide digital media for the lobby of a company. Which Cisco Digital Media component should the engineer use?
- A. Cisco Cast
- B. Cisco Digital Signs
- C. Cisco DMP
- D. Cisco Show and Share
- E. Cisco IP TV
Answer: B
NEW QUESTION 23
Which three options can initiate scheduled or rendezvous meetings hosted on a Cisco TelePresence Server? (Choose three.)
- A. video endpoint
- B. Cisco TMS
- C. Cisco Unified Communications Manager
- D. Cisco TelePresence Server
- E. Cisco VCS
- F. Cisco TelePresence Manager
Answer: ABD
NEW QUESTION 24
Refer to the exhibit. An SX80 endpoint has been deployed using dual screens and a third display is being added. To which connector must the third display be connected?
- A. A
- B. B
- C. C
- D. D
- E. E
- F. F
Answer: C
NEW QUESTION 25
An engineer is reviewing a SIP syslog on a TC software-based endpoint. Which area in the syslog indicates the start of the SDP session?
- A. a=
- B. v=
- C. b=
- D. m=
Answer: C
NEW QUESTION 26
An engineer is consistently seeing tickets in the Cisco TMS that are generated when a video endpoint is powered off each day. Which menu path allows the engineer to prevent this type of ticket from being created?
- A. TMS > Clear this ticket
- B. TMS > Acknowledge ticket
- C. TMS > Ignore ticket type for this system
- D. TMS > Ticket management
- E. TMS > Manage ticket error levels
Answer: C
NEW QUESTION 27
......
P.S. Easily pass 210-065 Exam with 425 Q&As Simply pass Dumps & pdf Version, Welcome to Download the Newest Simply pass 210-065 Dumps: https://www.simply-pass.com/Cisco-exam/210-065-dumps.html (425 New Questions)
