Cause all that matters here is passing the Cisco 300-635 exam. Cause all that you need is a high score of 300-635 Automating and Programming Cisco Data Center Solutions (DCAUTO) exam. The only one thing you need to do is downloading Exambible 300-635 exam study guides now. We will not let you down with our money-back guarantee.
Cisco 300-635 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Which two capabilities apply to the DCNM API? (Choose two.)
- A. DCNM provides an XML-based SOAP API.
- B. DCNM requires a license to use the API.
- C. Some features of DCNM must be configured through the GUI.
- D. All API operations can be performed using the DCNM GUI.
- E. DCNM provides a REST-based API.
Answer: AE
NEW QUESTION 2
Which statement about synchronous and asynchronous API calls is true?
- A. Synchronous API calls wait to return until a response has been received.
- B. Synchronous communication is harder to follow and troubleshoot.
- C. Synchronous API calls must always use a proxy server.
- D. Asynchronous communication uses more overhead for client authentication.
Answer: C
NEW QUESTION 3
Refer to the exhibit.
Which action does the execution of this ACI Cobra Python code perform?
- A. It prints all LLDP neighbor MAC and IP addresses.
- B. It prints all Cisco Discovery Protocol neighbor MAC and IP addresses.
- C. It prints all endpoint MAC and IP addresses.
- D. It prints all APIC MAC and IP addresses.
Answer: C
NEW QUESTION 4
How should the Kubernetes manifests be modified to allow Kubernetes environment integration with Cisco ACI?
- A. The metadata section must contain the Cisco APIC management IP.
- B. The manifest does not have to be changed, but the Kubernetes object is not discovered by Cisco ACI if this is not defined in the manifest.
- C. The manifests must include ACI EPG reference.
- D. No change is needed to perform this action.
Answer: D
NEW QUESTION 5
A server profile with the string "WEST15" in its name must have the string "WEST15" changed to "LXT14". For example, server profile "VMHOST-WEST15-01" would need to be changed to "VMHOST-LXT14-01".
Using the Cisco Intersight REST API in a Python script, which two GET API requests are used to retrieve just the server profile with the string "WEST15" in the name and the correct body for the API request to update the name? Assume the variable "sp_name" contains the name of the retrieved server profile. (Choose two.)
- A. GET https://intersight.com/api/v1/server/Profiles?$select=Name&$filter=contains(Name, 'WEST15')
- B. GET https://intersight.com/api/v1/server/Profiles?$select=Name&$filter=Name in('WEST15')
- C. BODY = { "Name": sp_name.format('WEST15', 'LXT14') }
- D. GET https://intersight.com/api/v1/server/Profiles?$select=Name&$filter=startswith(Name, 'WEST15')
- E. BODY = { "Name": sp_name.replace('WEST15','LXT14') }
Answer: AE
NEW QUESTION 6
Which step must be taken to enable the REST API browser within Cisco UCS Director?
- A. Edit the user profile and enable developer options.
- B. Raise a case with TAC.
- C. The REST API browser is automatically enabled in Cisco UCS Director when a Power User is created.
- D. Log in as the user "REST".
Answer: A
NEW QUESTION 7
Which two benefits of using network configuration tools such as Ansible and Puppet to automate data center platforms are valid? (Choose two.)
- A. consistency of systems configuration
- B. automation of repetitive tasks
- C. ability to create device and interface groups
- D. ability to add VLANs and routes per device
- E. removal of network protocols such as Spanning Tree
Answer: AB
NEW QUESTION 8
Which Cisco UCS PowerTool commands initiate a Cisco UCS Manager connection?
- A.
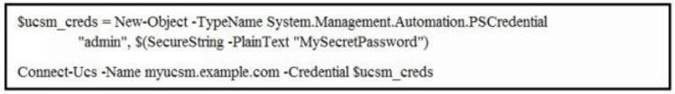
- B.

- C.
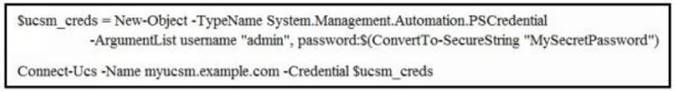
- D.

Answer: B
NEW QUESTION 9
Which Ansible playbook fragment returns the fewest queried ACI endpoint groups?
- A.
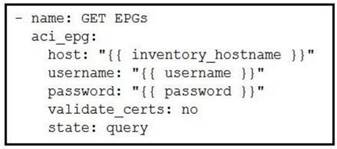
- B.
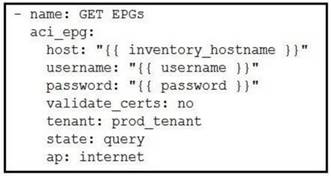
- C.
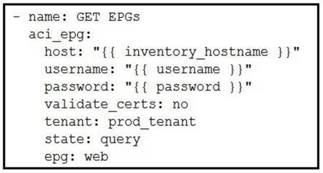
- D.
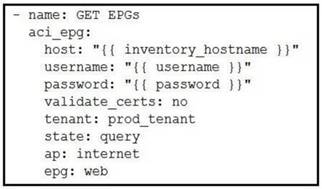
Answer: D
NEW QUESTION 10
Which two statements describe the authentication method used with Cisco Intersight REST API Requests? (Choose two.)
- A. The REST API request contains a base64-encoded signature of the message content and headers.
- B. The REST API request message body is encoded as a SHA384 hash and then signed with the API Key ID.
- C. The Cisco Intersight Web service verifies the signature of incoming request with the RSA public key for the API Key ID.
- D. The incoming REST API request is challenged by the Cisco Intersight Web service with a request for the RSA private key.
- E. The message body is encoded as a SHA256 hash if the message body is not empty and then signed with the API Key ID.
Answer: AD
NEW QUESTION 11
Which two items are types of application isolation options available when Kubernetes is deployed with the ACI CNI plug-in? (Choose two.)
- A. VM Isolation
- B. Cluster Isolation
- C. Server Isolation
- D. Process Isolation
- E. Namespace Isolation
Answer: BE
NEW QUESTION 12
What is a description of a Cisco UCS Director script module?
- A. function to convert internal workflow tasks into Python scripts
- B. place to store custom workflow scripts, jars, and custom lists of values for use in custom workflow tasks
- C. place to store external scripts that are not related to Cisco UCS Director
- D. place to store imported scripts, Bash, and custom Python code for use in custom workflow tasks
Answer: B
NEW QUESTION 13
Refer to the exhibit.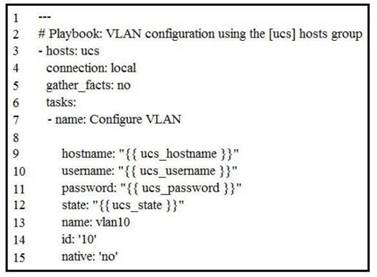
Which Ansible module is needed in line 8 to create a new VLAN 10 on the hosts defined in the "ucs" group?
- A. vlan
- B. ucs_vlans
- C. vlans
- D. nxos_vlans
Answer: B
NEW QUESTION 14
Refer to the exhibit.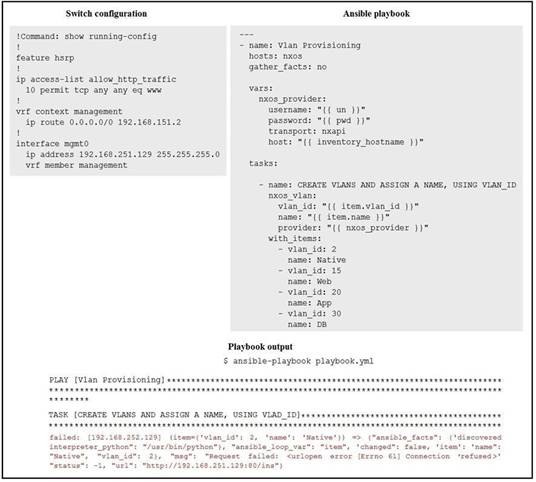
The exhibit shows a Cisco NX-OS switch configuration, an Ansible playbook, and the output of running this playbook. The playbook failed due to error "msg' 'Request failed <urlopen error [Errno 61] Connection refused>', 'status' -1, "url" "http://192.168.251.129:80/ins".
Which Cisco NX-OS configuration command resolves this failure?
- A. feature nxapi
- B. http-server enabled
- C. interface mgmt0; ip access-group allow_http_traffic in
- D. feature http
Answer: A
NEW QUESTION 15
Which two statements about gRPC are true? (Choose two.)
- A. It is an IETF draft.
- B. It is an IETF standard.
- C. It runs over SSH.
- D. It is an open source initiative.
- E. It runs over HTTPS.
Answer: AE
NEW QUESTION 16
Refer to the exhibit.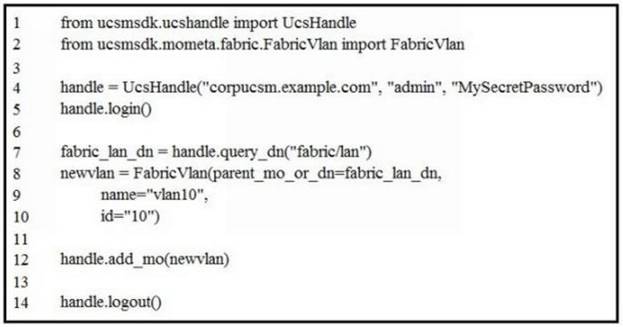
Which change allows the code to configure VLAN 10 in the Cisco UCS?
- A. Lines 8 and 9 should have a line continuation at the end.
- B. Line 13 should include "handle.commit()".
- C. Line 4 should include transport 443 option.
- D. Line 3 should add an import for query_dn.
Answer: C
NEW QUESTION 17
Which Kubernetes container network interface provides intent-based networking from the same pane of glass that VMs and bare-metal servers are managed?
- A. ACI CNI plug-in
- B. Contiv CNI plug-in
- C. Ingress CNI plug-in
- D. Calico CNI plug-in
Answer: A
NEW QUESTION 18
DRAG DROP
Drag and drop the correct YAML components from the bottom onto the correct blanks within the Ansible playbook to create a new application profile called "DbApp" using the Ansible ACI module. Not all options are used.
Select and Place:
- A. Mastered
- B. Not Mastered
Answer: A
NEW QUESTION 19
During the process of starting a Python network telemetry collector, which command starts the Cisco bigmuddy-network-telemetry-collector from GitHub?
- A. model driven telemetry
- B. telemetry_receiver.py --ip-address <addr> --port <port>
- C. telemetry_receiver.py --destination <port> --url <url>
- D. streaming telemetry
Answer: B
NEW QUESTION 20
Which two statements apply to authentication when using the Cisco Intersight API? (Choose two.)
- A. Each API Key can be assigned specific roles but not privileges.
- B. Secret Key is only available at API Key creation time.
- C. An API Key is composed of a Key ID and Secret Key.
- D. The user credentials for the cisco.com accounts are shared with the Cisco Intersight Web Service.
- E. An API Key is composed of a keyId and sessionCookie.
Answer: BC
NEW QUESTION 21
......
100% Valid and Newest Version 300-635 Questions & Answers shared by Dumps-files.com, Get Full Dumps HERE: https://www.dumps-files.com/files/300-635/ (New 0 Q&As)
