It is more faster and easier to pass the CompTIA SY0-601 exam by using Highest Quality CompTIA CompTIA Security+ Exam questuins and answers. Immediate access to the Update SY0-601 Exam and find the same core area SY0-601 questions with professionally verified answers, then PASS your exam with a high score now.
Free SY0-601 Demo Online For CompTIA Certifitcation:
NEW QUESTION 1
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites. INSTRUCTIONS
Click on each firewall to do the following:  Deny cleartext web traffic.
Deny cleartext web traffic. Ensure secure management protocols are used.
Ensure secure management protocols are used.  Resolve issues at the DR site.
Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.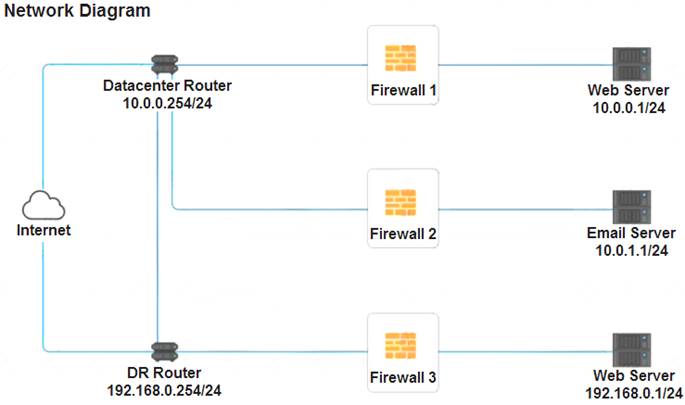
- A.
Answer: A
Explanation:
See explanation below.
Explanation
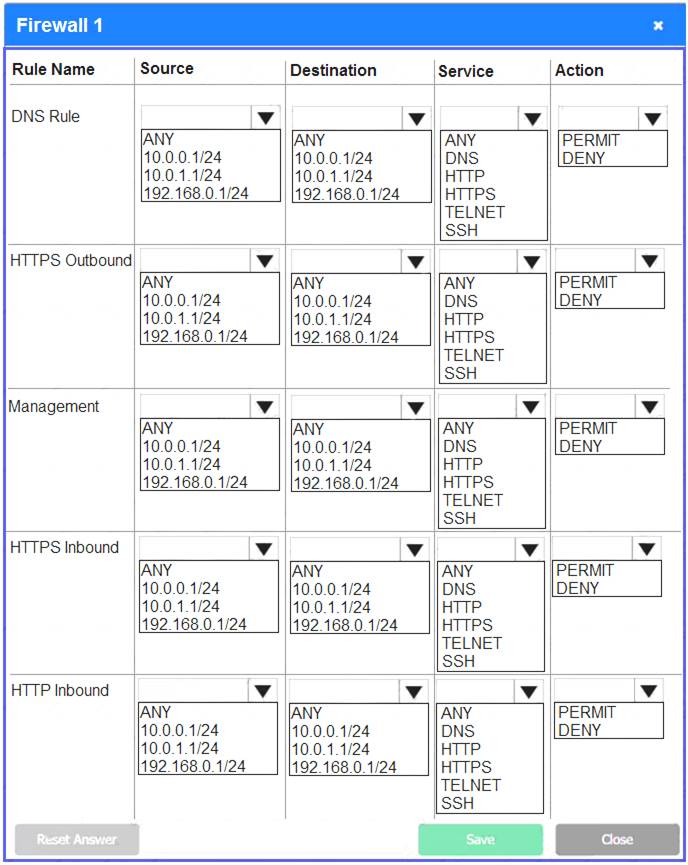
Firewall 1: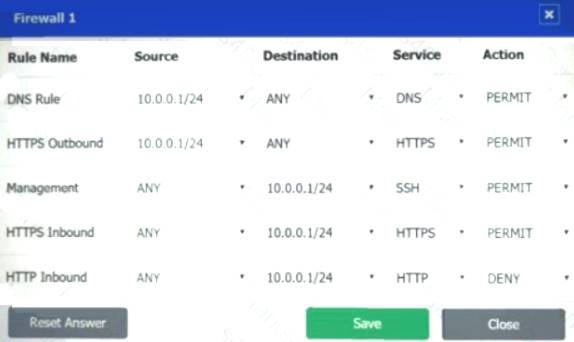
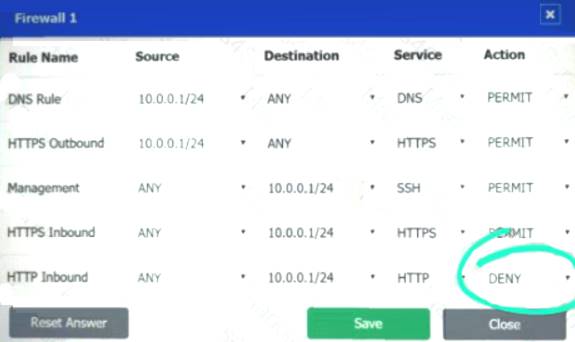
DNS Rule – ANY --> ANY --> DNS --> PERMIT
HTTPS Outbound – 10.0.0.1/24 --> ANY --> HTTPS --> PERMIT Management – ANY --> ANY --> SSH --> PERMIT
HTTPS Inbound – ANY --> ANY --> HTTPS --> PERMIT HTTP Inbound – ANY --> ANY --> HTTP --> DENY
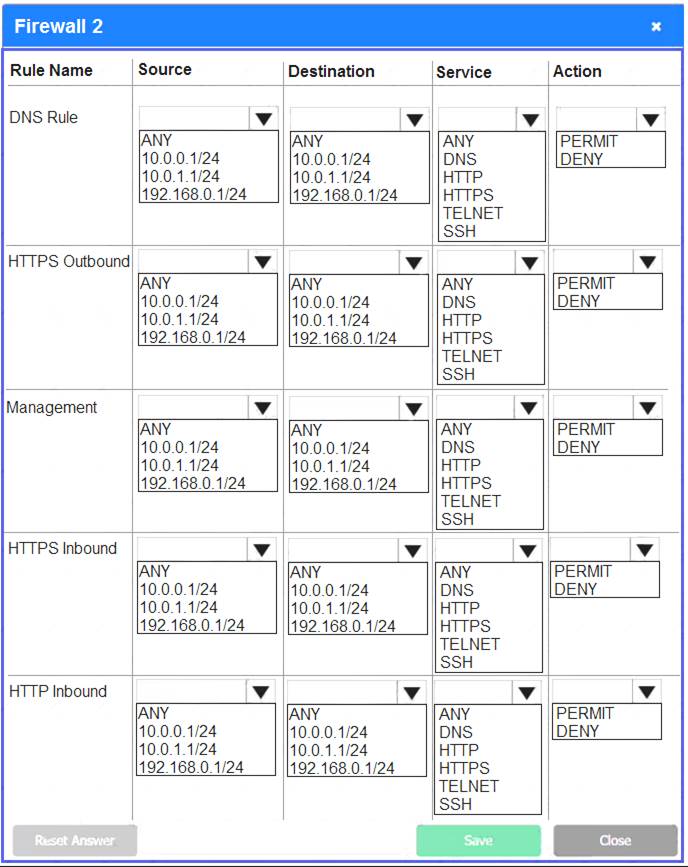
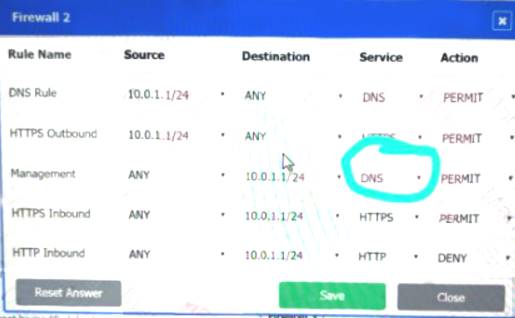
Firewall 2: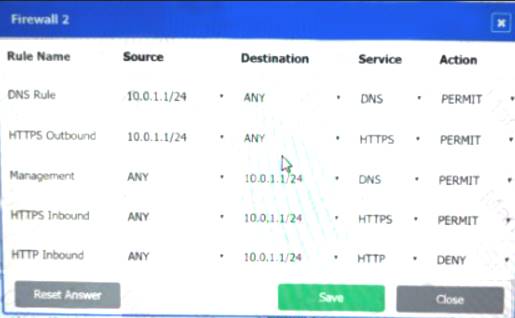
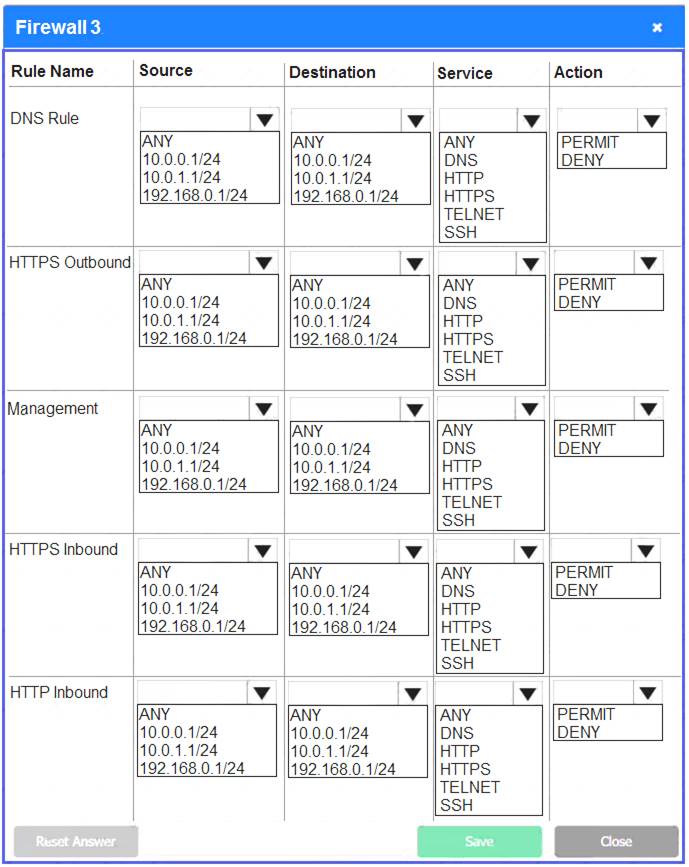
Firewall 3: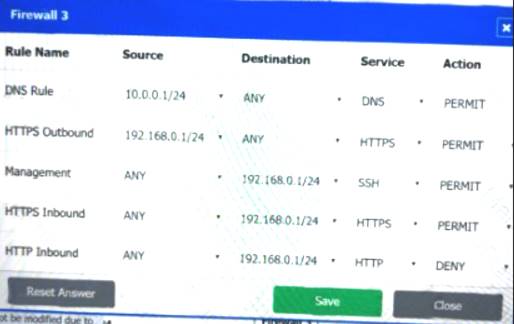
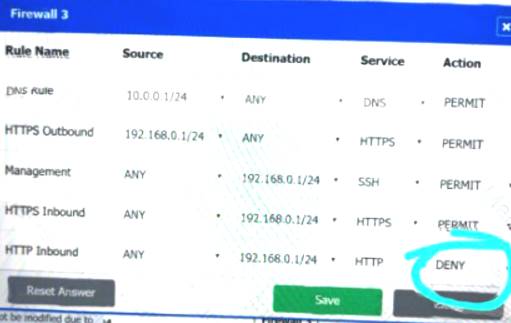
DNS Rule – ANY --> ANY --> DNS --> PERMIT
HTTPS Outbound – 192.168.0.1/24 --> ANY --> HTTPS --> PERMIT Management – ANY --> ANY --> SSH --> PERMIT
HTTPS Inbound – ANY --> ANY --> HTTPS --> PERMIT HTTP Inbound – ANY --> ANY --> HTTP --> DENY
NEW QUESTION 2
A remote user recently took a two-week vacation abroad and brought along a corporate-owned laptop. Upon returning to work, the user has been unable to connect the laptop to the VPN. Which of the following is the MOST likely reason for the user’s inability to connect the laptop to the VPN?
- A. Due to foreign travel, the user’s laptop was isolated from the network.
- B. The user’s laptop was quarantined because it missed the latest path update.
- C. The VPN client was blacklisted.
- D. The user’s account was put on a legal hold.
Answer: A
NEW QUESTION 3
A security engineer needs to Implement the following requirements:
• All Layer 2 switches should leverage Active Directory tor authentication.
• All Layer 2 switches should use local fallback authentication If Active Directory Is offline.
• All Layer 2 switches are not the same and are manufactured by several vendors.
Which of the following actions should the engineer take to meet these requirements? (Select TWO).
- A. Implement RADIUS.
- B. Configure AAA on the switch with local login as secondary.
- C. Configure port security on the switch with the secondary login method.
- D. Implement TACACS+
- E. Enable the local firewall on the Active Directory server.
- F. Implement a DHCP server.
Answer: AB
NEW QUESTION 4
A retail executive recently accepted a job with a major competitor. The following week, a security analyst reviews the security logs and identifies successful logon attempts to access the departed executive's accounts. Which of the following security practices would have addressed the issue?
- A. A non-disclosure agreement
- B. Least privilege
- C. An acceptable use policy
- D. Ofboarding
Answer: D
NEW QUESTION 5
A company is adopting a BYOD policy and is looking for a comprehensive solution to protect company information on user devices. Which of the following solutions would BEST support the policy?
- A. Mobile device management
- B. Full-device encryption
- C. Remote wipe
- D. Biometrics
Answer: A
NEW QUESTION 6
A large industrial system's smart generator monitors the system status and sends alerts to third-party maintenance personnel when critical failures occur. While reviewing the network logs the company's security manager notices the generator's IP is sending packets to an internal file server's IP. Which of the following mitigations would be BEST for the security manager to implement while maintaining alerting capabilities?
- A. Segmentation
- B. Firewall whitelisting
- C. Containment
- D. isolation
Answer: A
NEW QUESTION 7
A security analyst needs to generate a server certificate to be used for 802.1X and secure RDP connections. The analyst is unsure what is required to perform the task and solicits help from a senior colleague. Which of the following is the FIRST step the senior colleague will most likely tell the analyst to perform to accomplish this task?
- A. Create an OCSP
- B. Generate a CSR
- C. Create a CRL
- D. Generate a .pfx file
Answer: B
NEW QUESTION 8
Some laptops recently went missing from a locked storage area that is protected by keyless RFID-enabled locks. There is no obvious damage to the physical space. The security manager identifies who unlocked the door, however, human resources confirms the employee was on vacation at the time of the incident. Which of the following describes what MOST likely occurred?
- A. The employee's physical access card was cloned.
- B. The employee is colluding with human resources
- C. The employee's biometrics were harvested
- D. A criminal used lock picking tools to open the door.
Answer: A
NEW QUESTION 9
Which of the following will provide the BEST physical security countermeasures to stop intruders? (Select TWO.)
- A. Alarms
- B. Signage
- C. Lighting
- D. Mantraps
- E. Fencing
- F. Sensors
Answer: DE
NEW QUESTION 10
An organization is concerned that is hosted web servers are not running the most updated version of the software. Which of the following would work BEST to help identify potential vulnerabilities?
- A. Hping3 –s comptia, org –p 80
- B. Nc -1 –v comptia, org –p 80
- C. nmp comptia, org –p 80 –aV
- D. nslookup –port=80 comtia.org
Answer: C
NEW QUESTION 11
Which of the following allows for functional test data to be used in new systems for testing and training purposes to protect the read data?
- A. Data encryption
- B. Data masking
- C. Data deduplication
- D. Data minimization
Answer: B
NEW QUESTION 12
A company has drafted an insider-threat policy that prohibits the use of external storage devices. Which of the following would BEST protect the company from data exfiltration via removable media?
- A. Monitoring large data transfer transactions in the firewall logs
- B. Developing mandatory training to educate employees about the removable media policy
- C. Implementing a group policy to block user access to system files
- D. Blocking removable-media devices and write capabilities using a host-based security tool
Answer: D
NEW QUESTION 13
An incident response technician collected a mobile device during an investigation. Which of the following should the technician do to maintain chain of custody?
- A. Document the collection and require a sign-off when possession changes.
- B. Lock the device in a safe or other secure location to prevent theft or alteration.
- C. Place the device in a Faraday cage to prevent corruption of the data.
- D. Record the collection in a blockchain-protected public ledger.
Answer: A
NEW QUESTION 14
An organization has implemented a policy requiring the use of conductive metal lockboxes for personal electronic devices outside of a secure research lab. Which of the following did the organization determine to be the GREATEST risk to intellectual property when creating this policy?
- A. The theft of portable electronic devices
- B. Geotagging in the metadata of images
- C. Bluesnarfing of mobile devices
- D. Data exfiltration over a mobile hotspot
Answer: D
NEW QUESTION 15
Company engineers regularly participate in a public Internet forum with other engineers throughout the industry. Which of the following tactics would an attacker MOST likely use in this scenario?
- A. Watering-hole attack
- B. Credential harvesting
- C. Hybrid warfare
- D. Pharming
Answer: A
NEW QUESTION 16
A small business just recovered from a ransomware attack against its file servers by purchasing the decryption keys from the attackers. The issue was triggered by a phishing email and the IT administrator wants to ensure it does not happen again. Which of the following should the IT administrator do FIRST after recovery?
- A. Scan the NAS for residual or dormant malware and take new daily backups that are tested on a frequent basis
- B. Restrict administrative privileges and patch ail systems and applications.
- C. Rebuild all workstations and install new antivirus software
- D. Implement application whitelisting and perform user application hardening
Answer: A
NEW QUESTION 17
Which of the following is a team of people dedicated testing the effectiveness of organizational security programs by emulating the techniques of potential attackers?
- A. Red team
- B. While team
- C. Blue team
- D. Purple team
Answer: A
NEW QUESTION 18
A Chief Information Security Officer (CISO) needs to create a policy set that meets international standards for data privacy and sharing. Which of the following should the CISO read and understand before writing the policies?
- A. PCI DSS
- B. GDPR
- C. NIST
- D. ISO 31000
Answer: B
NEW QUESTION 19
An organization's RPO for a critical system is two hours. The system is used Monday through Friday, from 9:00 am to 5:00 pm. Currently, the organization performs a full backup every Saturday that takes four hours to complete. Which of the following additional backup implementations would be the BEST way for the analyst to meet the business requirements?
- A. Incremental backups Monday through Friday at 6:00 p.m and differential backups hourly
- B. Full backups Monday through Friday at 6:00 p.m and incremental backups hourly.
- C. incremental backups Monday through Friday at 6:00 p.m and full backups hourly.
- D. Full backups Monday through Friday at 6:00 p.m and differential backups hourly.
Answer: A
NEW QUESTION 20
A cybersecurity analyst reviews the log files from a web server and sees a series of files that indicates a directory-traversal attack has occurred. Which of the following is the analyst MOST likely seeing?
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: B
NEW QUESTION 21
A security auditor is reviewing vulnerability scan data provided by an internal security team. Which of the following BEST indicates that valid credentials were used?
- A. The scan results show open ports, protocols, and services exposed on the target host
- B. The scan enumerated software versions of installed programs
- C. The scan produced a list of vulnerabilities on the target host
- D. The scan identified expired SSL certificates
Answer: B
NEW QUESTION 22
A network technician is installing a guest wireless network at a coffee shop. When a customer purchases an Item, the password for the wireless network is printed on the recent so the customer can log in. Which of the following will the technician MOST likely configure to provide the highest level of security with the least amount of overhead?
- A. WPA-EAP
- B. WEP-TKIP
- C. WPA-PSK
- D. WPS-PIN
Answer: A
NEW QUESTION 23
A security administrator suspects there may be unnecessary services running on a server. Which of the following tools will the administrator MOST likely use to confirm the suspicions?
- A. Nmap
- B. Wireshark
- C. Autopsy
- D. DNSEnum
Answer: A
NEW QUESTION 24
An organization is developing a plan in the event of a complete loss of critical systems and data. Which of the following plans is the organization MOST likely developing?
- A. Incident response
- B. Communications
- C. Disaster recovery
- D. Data retention
Answer: C
NEW QUESTION 25
......
P.S. Easily pass SY0-601 Exam with 218 Q&As 2passeasy Dumps & pdf Version, Welcome to Download the Newest 2passeasy SY0-601 Dumps: https://www.2passeasy.com/dumps/SY0-601/ (218 New Questions)
