We offers 70 697 exam questions. "Configuring Windows Devices", also known as 70-697 exam, is a Microsoft Certification. This set of posts, Passing the 70-697 exam with 70 697 exam dumps, will help you answer those questions. The microsoft 70 697 covers all the knowledge points of the real exam. 100% real 70 697 braindump and revised by experts!
Online 70-697 free questions and answers of New Version:
NEW QUESTION 1
Your company has Windows 10 client computers. All of the computers are managed by using Windows Intune. You need to provide a user with the ability to deploy software to the computers by using Windows Intune.
The solution must minimize the number of permissions assigned to the user. Which role should you use?
- A. User management administrator from the Windows Intune account portal
- B. Global administrator from the Windows Intune account portal
- C. Service administrator from the Windows Intune administrator console
- D. Service administrator from the Windows Intune account portal
Answer: C
Explanation: As a service administrator, you use the Microsoft Intune administrator console to manage day-to-day tasks, such as deploying applications, for Intune.
NEW QUESTION 2
HOTSPOT
Your company has a main office and two branch offices named Branch1 and Branch2. The main office contains a file server named Server1 that has BranchCache enabled. Branch1 contains a server named Server2 that is configured as a hosted cache server. The average round trip network latency between the offices is 100 milliseconds.
All client computers run Windows 8 Enterprise. All of the computers are joined to an Active Directory domain.
The BranchCache settings of all the computers are configured as shown in the following exhibit. (Click the Exhibit button.)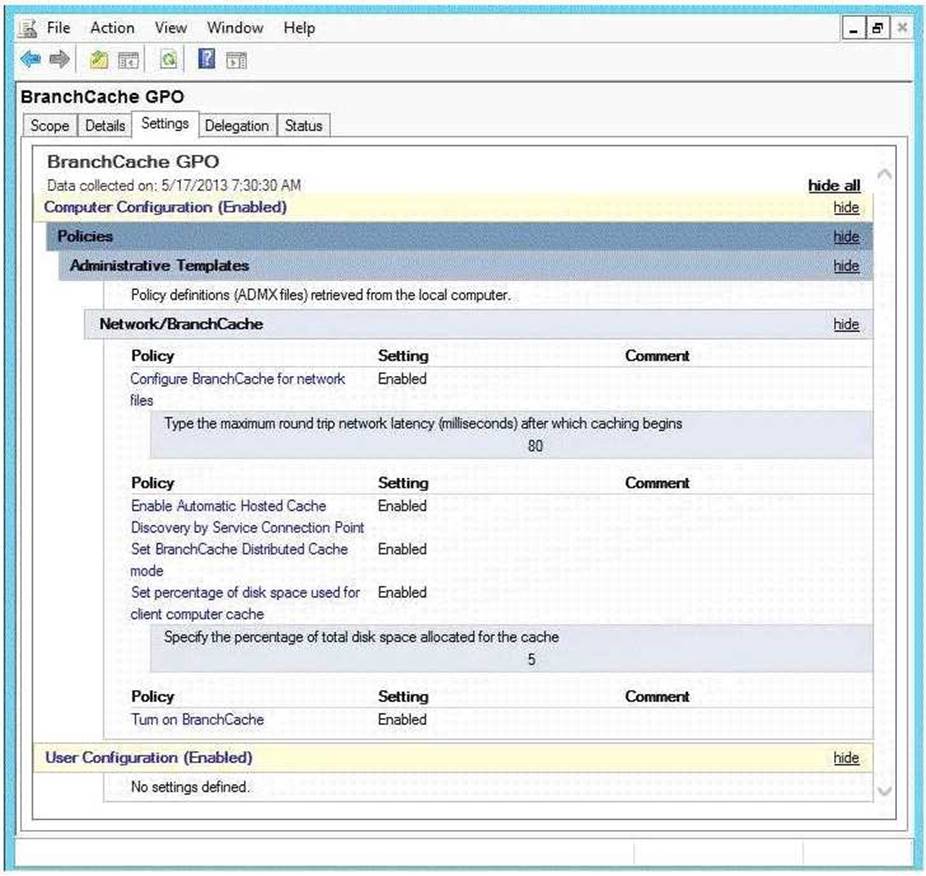
In the table below, identify the effective setting for the client computers in each branch office.
Note: Make one selection in each column. Each correct selection is worth one point.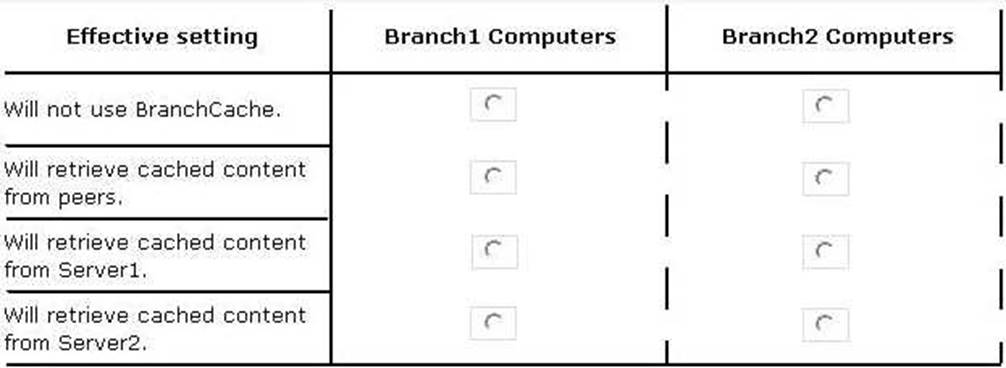
Answer:
Explanation: Both Server1 and Server2 will cache content for their local clients. Note: BranchCache has two modes of operation:
References: https://blogs.technet.microsoft.com/canitpro/2013/05/13/step-by-step- enabling-branchcache-in-microsoft-windows-server-2012/
NEW QUESTION 3
DRAG DROP
You enable Hyper-V on a company's Windows 10 Enterprise client computers.
You need to configure the computers' virtual switches. You have the following requirements:
Accounting department users require that virtual machine traffic does not communicate with any client computer.
HR department users must be able to copy files only from their client computer to their virtual machines.
IT department users must be able to copy files from network servers.
Finance department virtual machines must be able to communicate only with other virtual machines on the same client computer.
Which type of virtual switch should you use in each department? To answer, drag the appropriate switch type to the corresponding department. Each switch type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.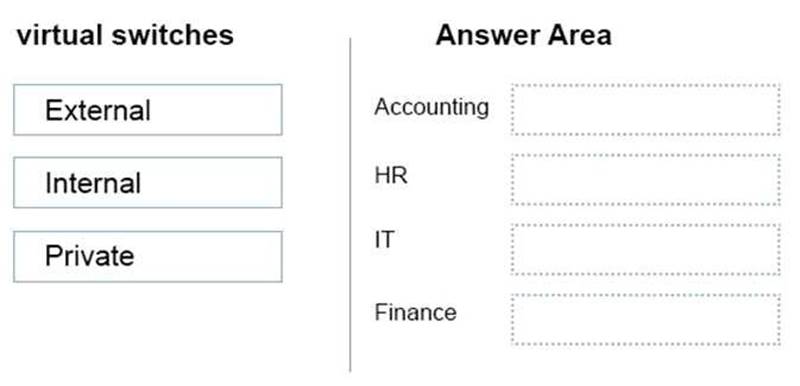
Answer:
Explanation: 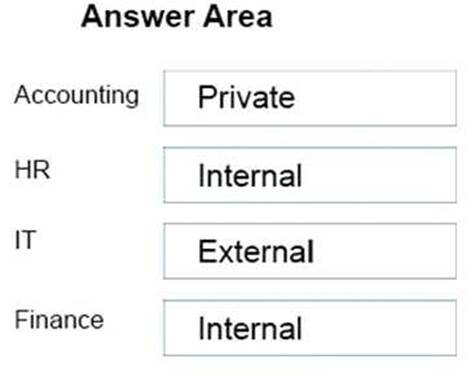
NEW QUESTION 4
You administer Windows 10 Enterprise laptops. The laptops are configured to connect to an unsecured wireless access point. You plan to configure the wireless access point to encrypt wireless traffic and turn off SSID broadcast.
You need to ensure the laptops will join the secured wireless network automatically after the configuration
changes.
What should you do?
- A. Create a network profile.
- B. Create an ad hoc network.
- C. Set Network Discovery to Enabled for the Public profile.
- D. Set the Unidentified Networks Properties User permissions to User can change location.
Answer: A
Explanation: References: http://ecross.mvps.org/howto/connect-to-wireless-network-with- windows-10.htm
NEW QUESTION 5
DRAG DROP
You have a computer that runs Windows 10 Enterprise that contains the following
folders. Each folder has its own access list and does not inherit permissions from the parent folder.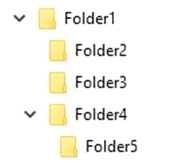
You have a local user named User1. User1 has read and execute permission to Folder1.
You need to ensure that User1 can perform the following tasks:
-Set the permissions on files in Folder2.
-Create new files in Folder5.
-Edit all files in Folder3.
The solution must use the principle of least privilege.
Which permissions should you assign to User1 on each folder? To answer, drag the appropriate permissions to the correct folders. Each permission may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Answer:
Explanation: 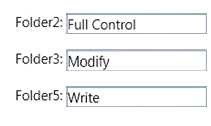
NEW QUESTION 6
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
A company has a forest trust with a partner organization. Users from both organizations log on to devices that run Windows 8.1.
You plan to replace the devices with devices running Windows 10.
You need to migrate user profiles from both forests using the least amount of administrative effort.
Solution: You migrate both profiles simultaneously by using the User State Migration Tool (USMT).
Does the solution meet the goal?
- A. Yes
- B. No
Answer: A
Explanation: References: https://docs.microsoft.com/en-us/windows/deployment/usmt/usmt-migrate-user-accounts#bkmk-migrateall
NEW QUESTION 7
You administer computers that run Windows 8 Enterprise and are members of an Active Directory domain. Some volumes on the computers are encrypted with BitLocker.
The BitLocker recovery passwords are stored in Active Directory. A user forgets the BitLocker password to local drive E: and is unable to access the protected volume. You need to provide a BitLocker recovery key to unlock the protected volume.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
- A. Ask the user to run the manage–bde–protectors–disable e: command.
- B. Ask the user for his or her logon name.
- C. Ask the user to run the manage–bde–unlock E:–pw command.
- D. Ask the user for his or her computer name.
- E. Ask the user for a recovery key ID for the protected drive.
Answer: CD
Explanation: D: To view the recovery passwords for a computer you would need the computer name:
In Active Directory Users and Computers, locate and then click the container in which the computer is located.
Right-click the computer object, and then click Properties.
In the Properties dialog box, click the BitLocker Recovery tab to view the BitLocker recovery passwords that are associated with the particular computer.
C: The Manage–bde: unlock command unlocks a BitLocker-protected drive by using a recovery password or a recovery key.
NEW QUESTION 8
You have a Windows 10 Enterprise computer named Computer1. Computer1 has File History enabled. You create a folder named Folder1 in the root of the C: drive.
You need to ensure that Folder1 is protected by File History.
What are two possible ways to achieve the goal? Each correct answer presents a complete solution.
- A. From File Explorer, include Folder1 in an existing library.
- B. Modify the Advanced settings from the FileHistory Control Panel item.
- C. From the Settings app, modify the Backup options.
- D. From File Explorer, modify the system attribute of Folder1.
Answer: AC
Explanation: By default, File History backs up all libraries. We can therefore ensure that Folder1 is protected by File History by adding the folder to a library.
The second method of ensuring that Folder1 is protected by File History is to add the folder location to File History. You do this by modifying the Backup options, not the File History Control Panel item as you might expect. In the Settings app, select Update & Security then Backup. Under the Back up using File History heading, select the Add a drive option.
NEW QUESTION 9
Note: This question is part of a series of questions that use the same or similar answer choices. An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in this series. Information and details in a question apply only to that question.
You have a mobile device that connects to a 4G network and a laptop. You work from a remote location that does not have Internet access.
You plan to use the mobile device as a mobile hotspot for the laptop, so that you can access files from the corporate office.
Which Control Panel application should you use on the laptop to connect to the mobile hotspot?
- A. Phone and Modem
- B. RemoteApp and Desktop Connections
- C. System
- D. Credential Manager
- E. Work Folders
- F. Power Options
- G. Sync Center
- H. Network and Sharing Center
Answer: H
NEW QUESTION 10
You have a standalone Windows 10 Enterprise computer that has a single hard drive installed and configured.
You need to identify which storage devices can have content backed up by using File History.
What should you identify?
- A. A writable Blu-ray disc
- B. A writable DVD disc
- C. An internal drive that is formatted NTFS
- D. An SD card that is formatted FAT32
Answer: D
Explanation: References: http://www.laptopmag.com/articles/back-files-file-history-windows-10
NEW QUESTION 11
A company has Windows 10 Enterprise client computers.
You install a new printer on a client computer. The printer software installation includes an application that runs when the computer starts. You experience problems with the application.
You need to prevent the application from running when the computer starts, without affecting any other application.
What should you do?
- A. Run the bcdedit -p command.
- B. Run the msconfig -p command.
- C. Configure the printer by using Device Manager.
- D. Configure the printer application by using Task Manager.
Answer: D
NEW QUESTION 12
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You administer devices in your corporate environment. The company allows employees to bring their own devices (BYOD). All BYOD devices must run Windows
10. For employees who elect to not use BYOD, the company provides a corporate laptop.
The company has a Microsoft Intune subscription and all BYOD devices have the Intune client installed. None of the BYOD devices are joined to the domain. All the corporate standard devices are managed by System Center Configuration Manager (SCCM).
You have an application that was developed in house that must be installed on all the BYOD devices.
The application must be installed automatically on the BYOD devices without any user intervention.
Solution: You upload the app to the Intune storage and make the app available. Does the solution meet the goal?
- A. Yes
- B. No
Answer: A
Explanation: References: https://docs.microsoft.com/en-us/intune/lob-apps-windows
NEW QUESTION 13
You are the network administrator for Contoso, Ltd. Many users have Windows 10 Enterprise laptops, and your IT department configures all of them to use BitLocker on all fixed drives.
Many users carry sensitive corporate data on their USB drives. You need to enable BitLocker for these USB drives.
Which key protector option should you use?
- A. a smartcard
- B. a startup key
- C. TPM+PIN
- D. TPM+Password
Answer: D
Explanation: References: http://www.howtogeek.com/192894/how-to-set-up-bitlocker-encryption- on-windows/
NEW QUESTION 14
DRAG DROP
A Windows 10 Enterprise computer has an external hard drive that contains selected folders that are encrypted by using EFS. The computer's internal hard drive fails.
You have a backup of the certificate and key.
You need to provide access to the encrypted folders on the external hard drive. Which four actions should you perform in sequence? To answer, move the appropriate four actions from the list of actions to the answer area and arrange them in the correct order.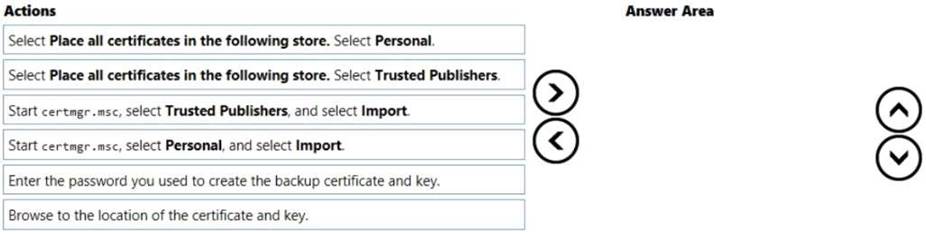
Answer:
Explanation: 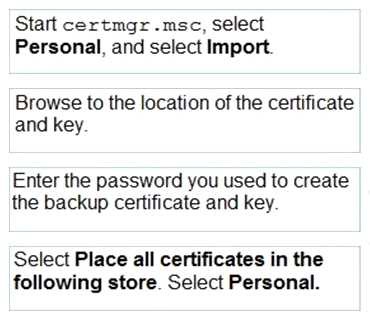
NEW QUESTION 15
You administer Windows 10 Enterprise client computers in your company network.
You change settings on a reference computer by using the Windows Firewall with Advanced Security tool. You want to apply the same settings to other computers.
You need to save the Windows Firewall with Advanced Security configuration settings from the reference computer. You also need to be able to import the configuration settings into a Group Policy object later.
What should you do?
- A. Open Local Group Policy Editor, select the Windows Firewall with Advanced Security node, and then select the Export Policy action.
- B. Run the netsh advfirewall export c:settings.wfw command.
- C. Run the netsh firewall export c:settings.xml command.
- D. Run the netsh advfirewall export c:settings.xml command
Answer: B
NEW QUESTION 16
You administer Windows 10 Enterprise client computers that are members of an Active Directory domain that includes Active Directory Certificate Services (AD CS). You restored a computer from a backup that was taken 45 days ago. Users are no longer able to log on to that computer by using their domain accounts. An error message states that the trust relationship between the computer and the primary domain has failed.
What should you do?
- A. Renew the certificates issued to the client computer.
- B. Reset the passwords of all affected domain users.
- C. Logon as a local administrator and issue the netdom resetpwd comman
- D. Log off and restart the computer.
- E. Restore the client computer from a known good backup that was taken two weeks earlier than the backup you previously restored.
Answer: C
Explanation: References: http://theitbros.com/fix-trust-relationship-failed-without-domain- rejoining/
NEW QUESTION 17
DRAG DROP
You support Windows 10 Enterprise computers. AppLocker policies are deployed. Company policy states that AppLocker must be disabled.
You need to disable AppLocker.
Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)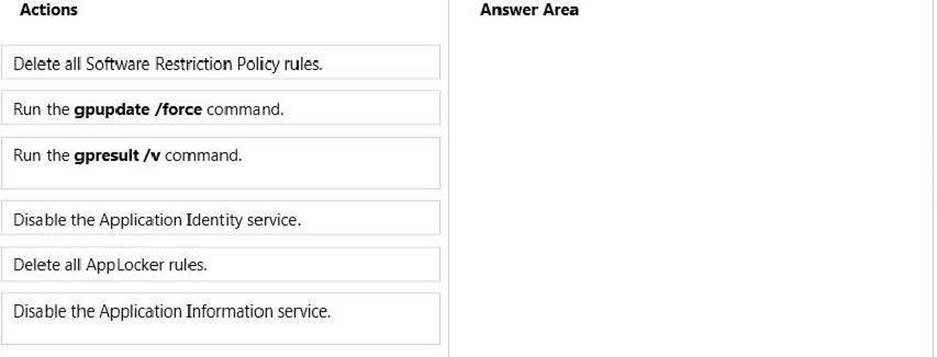
Answer:
Explanation: Box 1: Delete all AppLocker rules.
Box 2: Disable the Application Identity service.
Box 3: Run the gpupdate /force command. Note:
* Before you can enforce AppLocker policies, you must start the Application Identity service by using the Services snap-in console.
* The Application Identity service determines and verifies the identity of an application. Stopping this service will prevent AppLocker policies from being enforced.
The gpresult command is used to display the Resultant Set of Policy (RSoP) information for a remote user and computer. And used in conjunction with the /v parameter – it displays verbose policy information. This includes detailed settings that were applied with a precedence of 1.
References:
http://technet.microsoft.com/en-us/library/hh852337.aspx http://technet.microsoft.com/en-us/library/cc733160.aspx
Recommend!! Get the Full 70-697 dumps in VCE and PDF From Certshared, Welcome to Download: https://www.certshared.com/exam/70-697/ (New 338 Q&As Version)
