Virtual of 300-815 free exam materials and exam dumps for Cisco certification for IT examinee, Real Success Guaranteed with Updated 300-815 pdf dumps vce Materials. 100% PASS Implementing Cisco Advanced Call Control and Mobility Services (CLACCM) exam Today!
Also have 300-815 free dumps questions for you:
NEW QUESTION 1
Cisco SIP IP telephony is implemented on two floors of your company. Afterward, users report intermittent voice issues in calls established between floors. All calls are established, and sometimes they work well, but sometimes there is oneway audio or no audio. You determine that there is a firewall between the floors, and the administrator reports that it is allowing SIP signaling and UDP ports from 20000 to 22000 bidirectionally. What are two possible solutions? (Choose two.)
- A. Go to the SIP profile assigned to these IP phones in Cisco Unified CM and change the range of media ports to 16384-32767
- B. Ask the firewall administrator to change the ports to TCP.
- C. Ask the firewall administrator to change the range of UDP ports to 16384-32767.
- D. Go to the SIP profile assigned to these IP phones in Cisco Unified CM and change the range of media ports to 20000-22000.
- E. Go to System Parameters in Cisco Unified Communications Manager and change the range of media ports to 20000-22000.
Answer: AC
NEW QUESTION 2
Which section under the Real-Time Monitoring Tool allows for reviewing the call flow and signaling for a SIP call in real time?
- A. Analysis Manager > Inventory > Trace File Repositories
- B. System > Tools > Trace and Log Central
- C. Voice/Video > Session Trace Log View > Real Time Data
- D. Voice/Video > Session Trace Log View > Open From Local Disk
Answer: C
NEW QUESTION 3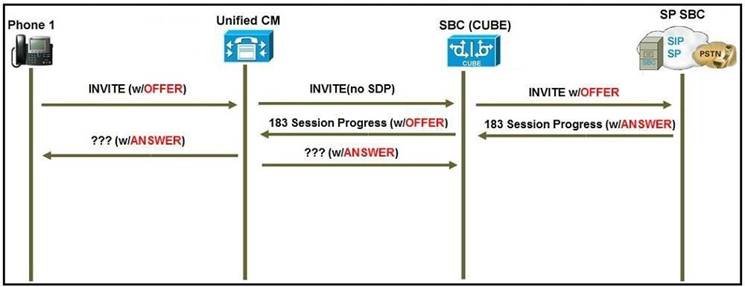
Refer to the exhibit. A user reports that when they call a specific phone number, no one answers the call, but when they call from a mobile phone, the call is answered. The engineer troubleshooting the issue is expecting the far-end gateway to cut through audio on the 183 Session Progress SIP message. Which SIP Profile configuration element is necessary for the Cisco Unified Communications Manager to send acknowledgement of provisional responses?
- A. Allow Passthrough of Configured Line Device Caller Information must be enabled.
- B. Accept Audio Codec Preferences in Received Offer must be set to On.
- C. On the SIP Profile, the configuration parameter SIP Rel1XX Options must be set to Send PRACK for all 1xx Messages.
- D. Early Offer for G Clear Calls must be enabled.
Answer: C
NEW QUESTION 4
An engineer must configure a secure SIP trunk with a remote provider, with a specific requirement to use port 5065 for inbound and otubound traffic. Which two items must be configured to complete this configuration? (Choose two.)
- A. Incoming Port in SIP Information section of the SIP Trunk configuration.
- B. Incoming Port in Security Information of the SIP Profile configuration.
- C. Destination Port in SIP Information section of the SIP Trunk configuration
- D. Incoming Port in SIP Trunk Security Profile configuration
- E. Destination Port in SIP Trunk Security Profile configuration
Answer: CD
NEW QUESTION 5
For s SIP to SIP call flow, when does Cisco Unified Border Element require transcoding resources for DTMF?
- A. interworking between an OOB method and RFC2833 for flow-around calls
- B. interworking between h245-signal and rtp-nte
- C. interworking between an OOB method and RFC2833 for flow-through calls
- D. interworking between h245-alpha numeric and sip-kpml
Answer: A
NEW QUESTION 6
A user reports that when they attempt to log out from the Cisco Extension Mobility service by pressing the Services button, they cannot log out. What is the most likely cause of this issue?
- A. The Cisco Extension Mobility service has not been configured on the phone.
- B. There might be a significant delay between the button being pressed and the Cisco Extension Mobility service recognizing i
- C. It would be best to check network latency.
- D. The user device profile has not been assigned to the user.
- E. The user device profile is not subscribed to the Cisco Extension Mobility service.
Answer: D
NEW QUESTION 7
Which top-level IOS command is needed to begin the configuration of a Cisco Unified Communications Manager Express gateway to enable phones to be registered via SIP?
- A. allow-connections sip to sip
- B. voice service voip
- C. voice register global
- D. voice register dn
Answer: C
NEW QUESTION 8
Which two extended capabilities must be configured on dial peers for fast start-to-early media scenarios (H.323 to SIP interworking)? (Choose two.)
- A. DTMF
- B. BFCP
- C. VIDEO
- D. FAX
- E. AUDIO
Answer: AB
NEW QUESTION 9
Which two statements are correct with respect to the Client Matter Code setting in the route pattern configuration? (Choose two.)
- A. The Client Matter Code feature does not support overlap sending because the Cisco Unified CM cannot determine when to prompt the user for the code.
- B. If you check the Allow Overlap Sending check box, the Require Client Matter Code check box becomes disabled.
- C. If you check the Allow Overlap Sending check box, you can also check the Require Client Matter Code check box.
- D. The Client Matter Code feature does support overlap sending because the Cisco Unified Communications Manager can determine when to prompt the user for the code.
- E. The Client Matter Code has the option to configure Authorization Level such as in the Forced Authorization Code.
Answer: AB
NEW QUESTION 10
An administrator is configuring a cluster for ILS and wants to limit the amount of entities that Cisco Unified Communications Manager can write to the database for data that is learned through ILS. Which service parameter is used to adjust this limit?
- A. ILS Max Number of Learned Objects in Database
- B. ILS Active Learned Object Upper Limit
- C. Global Data Service Parameter Limit
- D. Imported Dial Plan Replication Database Object Lower Limit
Answer: A
NEW QUESTION 11
An engineer must route all SIP calls in the form of <user>@example.com to the SIP trunk gateway corporate local. Which two SIP route patterns can be used to accomplish this task? (Choose two.)
- A. example.com@gateway.corporate.local
- B. *@example.com
- C. gateway.corporate.local
- D. example.com
- E. *.*
Answer: BE
NEW QUESTION 12
Which two descriptions of the Standard Local Route Group deployment are true? (Choose two.)
- A. can be associated under the route group
- B. can be associated only under the route list
- C. chooses the route group that is configured under the device pool of the calling-party device
- D. chooses the route group that is configured under the device pool of the called-party device
- E. can be assigned directly to the route pattern
Answer: BD
NEW QUESTION 13
Which description of RTP timestamps or sequence numbers is true?
- A. The sequence number is used to detect losses.
- B. Timestamps increase by the time “carrying” by a packet.
- C. Sequence numbers increase by four for each RTP packet transmitted.
- D. The timestamp is used to place the incoming audio and video packets in the correct timing order (playout delay compensation).
Answer: D
NEW QUESTION 14
A network engineer designs a new dial plan and wants to block a certain range of numbers (8135100 through 8135105). What is the most specific route pattern that can be configured to block only the numbers in this range?
- A. 813510[012345]
- B. 813510[12345]
- C. 813510[^0-5]
- D. 81XXXXX
Answer: A
NEW QUESTION 15
Which action is correct with respect to toll fraud prevention configuration in the Cisco Unified Communications Manager Express?
- A. Configure Direct Inward Dial for Incoming ISDN Calls with overlap dialing.
- B. Configure IP Address Trusted Authentication for Incoming VoIP Calls.
- C. Configure the command no ip address trusted authenticate under “voice service voip”.
- D. Enable Secondary Dial tone on Analog and Digital FXO Ports.
Answer: B
NEW QUESTION 16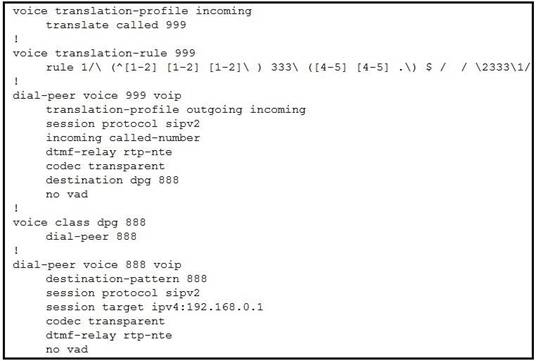
Refer to the exhibit. Calls incoming from the provider are not working through newly set up Cisco Unified Border Element. Provider engineers get the 404 Not Found SIP message. Incoming calls are coming from the provider with called number “222333444” and Cisco Unified Communications Manager is expecting the called number to be delivered as “444333222”. The administrator already verified that the IP address of the Cisco Unified CM is set up correctly and there are no dial peers configured other than those shown in the exhibit. Which action must the administrator take to fix the issue?
- A. Change the destination-pattern on the outgoing dial peer to match “444333222”.
- B. Set up translation-profile on the incoming dial peer to match incoming traffic.
- C. Create specific matching for “222333444” on the incoming dial peer.
- D. Fix the voice translation-rule to match specifically number “222333444” and change it to “444333222”.
Answer: B
NEW QUESTION 17
Why would RTP traffic that is sent from the originating endpoint fail to be received on the far endpoint?
- A. The far end connection data (c=) in the SDP was overwritten by deep packet inspection in the call signaling path.
- B. Cisco Unified Communications Manager invoked media termination point resources.
- C. The RTP traffic is arriving beyond the jitter buffer on the receiving end.
- D. A firewall in the media path is blocking TCP ports 16384-32768.
Answer: D
NEW QUESTION 18
Which configuration must an administrator perform to display Translation Pattern operations in Cisco Unified Communications Manager SDL traces?
- A. Enable the Detailed Call Analysis option under Enterprise Parameters for Unified CM.
- B. Set up the Digit Analysis Complexity in Service Parameters for Cisco Unified CM to TranslationAndAlternatePatternAnalysis.
- C. Check the Translation Patterns Analysis check box in Micro Traces on the Cisco Unified CM Serviceability page.
- D. By default, the Translation Patterns operations are printed in SDL traces, so no additional configuration is necessary.
Answer: A
NEW QUESTION 19
Refer to the exhibit. Users report that outbound PSTN calls from phones registered to Cisco Unified Communications Manager are not completing. The local service provider in North America has a requirement to receive calls in 10-digit format. The Cisco Unified CM sends the calls to the Cisco Unified Border Element router in a globalized E.164 format. There is an outbound dial peer on Cisco Unified Border Element configured to send the calls to the provider. The dial peer has a voice translation profile applied in the correct direction but an incorrect voice translation rule applied, which is shown in the exhibit. Which rule modified DNIS in the format that the provider is expecting?
- A. rule 1 /^/+([^1].*)/ /0111/
- B. rule 1/^+1([2-9]..[2-9]……$)/ /1/
- C. rule 1 /^([2-9]..[2-9]……$)/ /1/
- D. rule 1 /^+1([2-9]..[2-9]……$)/ /�/
Answer: B
NEW QUESTION 20
Which services are needed to successfully implement Cisco Extension Mobility in a standalone Cisco Unified Communications Manager server?
- A. Cisco Extended Functions, Cisco Extension Mobility, and Cisco AXL Web Service
- B. Cisco CallManager, Cisco TFTP, and Cisco CallManager SNMP Service
- C. Cisco CallManager, Cisco TFTP, and Cisco Extension Mobility
- D. Cisco TAPS Service, Cisco TFTP, and Cisco Extension Mobility
Answer: C
NEW QUESTION 21
When the services key is pressed Cisco Extension Mobility does not show up. What is the cause of the issue?
- A. The URL configured for Cisco Extension Mobility is not correct.
- B. Cisco Extension Mobility Service is not running.
- C. The phone is not subscribed to Cisco Extension Mobility Service.
- D. Cisco Extension Mobility is not enabled in the Phone Configuration Window (Device > Phone)
Answer: C
NEW QUESTION 22
After configuring a Cisco CallManager Express with Cisco Unity Express, inbound calls from the PSTN SIP trunk receive a ring tone for 20 seconds and then a busy signal instead of voicemail. Which configuration fixes this problem?
- A. Router(config)# voice service voipRouter(conf-voi-serv)#allow-connections h323 to h323
- B. Router(config)#dial-peer voice 2 voipRouter(config-dial-peer)#no vad
- C. Router(config)# voice service voipRouter(conf-voi-serv)#allow-connections voice-mail mod
- D. Router(config)# voice service voipRouter(conf-voi-serv)#no supplementary-service sip moved-temporarily
Answer: A
NEW QUESTION 23
......
Thanks for reading the newest 300-815 exam dumps! We recommend you to try the PREMIUM Dumps-files.com 300-815 dumps in VCE and PDF here: https://www.dumps-files.com/files/300-815/ (0 Q&As Dumps)
