Certleader offers free demo for JN0-1332 exam. "Security Design. Specialist (JNCDS-SEC)", also known as JN0-1332 exam, is a Juniper Certification. This set of posts, Passing the Juniper JN0-1332 exam, will help you answer those questions. The JN0-1332 Questions & Answers covers all the knowledge points of the real exam. 100% real Juniper JN0-1332 exams and revised by experts!
Online JN0-1332 free questions and answers of New Version:
NEW QUESTION 1
You are designing a service provider network. As part of your design you must ensure that the OSPF, BGP, and RSVP protocol communications are secured using the same authentication method. Which authentication protocol will accomplish this task?
- A. HMAC-MD5
- B. simple authentication
- C. SHA-RSA
- D. SHA-256
Answer: B
NEW QUESTION 2
You are asked to provide a security solution to secure corporate traffic across the Internet between sites. This solution must provide data integrity, confidentiality and encryption Which security feature will accomplish this task?
- A. IPsecVPN
- B. IP-IP tunnel
- C. Layer 3 VPN
- D. IGRE tunnel
Answer: A
NEW QUESTION 3
You are asked to design security into the configuration of routing protocols on your Junos network to stop rogue neighbors from forming adjacencies for an enterprise WAN What win accomplish this task?
- A. PAP
- B. SAML
- C. MOS
- D. TTLS
Answer: D
NEW QUESTION 4
Refer to the Exhibit.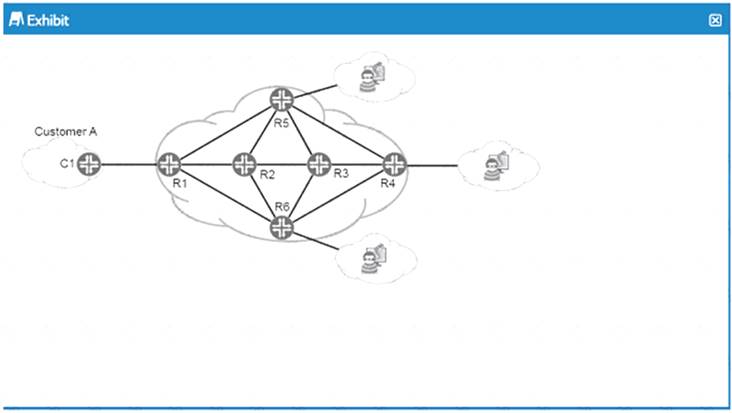
You are asked to provide a proposal for security elements in the service provider network shown in the exhibit. You must provide DOoS protection for Customer A from potential upstream attackers.
Which statements correct in this scenario?
- A. You should implement DDoS protection to drop offending traffic on the edge devices closest to the destination of the attack.
- B. You should implement DDoS protection to drop offending traffic on the edge devices closest to the source of the attack.
- C. You should implement DDoS protection to drop offending traffic on the core devices.
- D. You should implement DDoS protection to drop offending traffic on the customer edge device.
Answer: C
NEW QUESTION 5
When two security services process a packet whether it is being processed in the first-packet path or the fast path? (Choose two.)
- A. screen options
- B. ALG
- C. route lookup
- D. policy lookup
Answer: CD
NEW QUESTION 6
Which three statements about Group VPNs #e true? (Choose three.)
- A. The IP pay load is encrypted
- B. Data can flow directly between sites without transiting a central hub
- C. Group VPNs use a client/server architecture
- D. All data transits through a central hub
- E. The IP headers are encrypted
Answer: ACD
NEW QUESTION 7
When considering the data center, which two security aspects must be considered? (Choose two)
- A. theoretical
- B. conceptual
- C. physical
- D. logical
Answer: A
NEW QUESTION 8
What are two considerations when performing a risk assessment for assets in a data center? (Choose two.)
- A. Insurance is a viable mitigation strategy when performing risk assessment calculations
- B. Exposure of assets could have larger economic impact man loss of assets
- C. Migration of a data center to a cloud prouder increases economic impact of asset loss
- D. Migration of a data center to a cloud provider reduces the economic impact of asset exposure
Answer: C
NEW QUESTION 9
You are asked to segment the networks connected to an SRX Series device into distinct logical groups with different security requirements.
How would you accomplish this task?
- A. Define different NAT policies for each network segment.
- B. Define different security policies for each network segment.
- C. Define different intrusion prevention policies for each network segment.
- D. Define different security zones for each network segment
Answer: B
NEW QUESTION 10
A new virus is sheading across the Internet, with the potential to affect your customer's network
Which two statements describe how Policy Enforcer interacts with other devices to ensure that the network is protected in this scenario? (Choose two.)
- A. Policy Enforcer pulls security intelligence feeds from Juniper ATP Cloud to apply to SRX Series devices
- B. Policy Enforcer pulls security policies from Juniper ATP cloud and apples them to SRX Series devices
- C. Policy Enforcer automates the enrollment of SRX Series devices with Jumper ATP Cloud
- D. Security Director pulls security intelligence feeds from Juniper ATP Cloud and applies them to Policy Enforcer
Answer: B
NEW QUESTION 11
A customer wants to understand why Poky Enforcer is included as a part of your network design proposal.
In this situation, which statement is correct
- A. Policy Enforcer submits files to Juniper ATP Cloud for malware scanning
- B. Policy Enforcer can provide client security based on software installed on the client machine
- C. Policy Enforcer provides 2ero trust security to ail devices connecting to the network
- D. Policy Enforcer can collect events and news from a wide range of network devices
Answer: A
NEW QUESTION 12
You must implement a solution to deploy end-to-end security services on network elements. Which solution will accomplish this task?
- A. Security Director
- B. Network Director
- C. JSA
- D. SRX Series devices
Answer: C
NEW QUESTION 13
When designing the security for a service provider core router, you are asked to add a firewall fitter on the to0 interface in this scenario, which two protocols would you want to allow through the filter? (Choose two.)
- A. LLDP
- B. SSH
- C. BGP
- D. STP
Answer: AC
NEW QUESTION 14
Multiple customers use the shared infrastructure of your data center. These customers require isolation for compliance and security reasons.
What would you do to satisfy this requirement?
- A. Isolate each customer by using different physical hard//are
- B. Deploy multiple physical security control points
- C. Deploy a single logical security control point.
- D. Place each customers VLANs separate virtual router
Answer: C
NEW QUESTION 15
Your network design requires that you ensure privacy between WAN endpoints. Which transport technology requires an IPsec overlay to satisfy this requirement?
- A. L3VPN
- B. leased line
- C. internet
- D. L2VPN
Answer: A
NEW QUESTION 16
You want to reduce the possibility of your data center's server becoming an unwilling participant in a DDoS attack When tvA3 features should you use on your SRX Series devices to satisfy this requirement? (Choose two.)
- A. dynamic IPsec tunnels
- B. Juniper ATP Cloud GeolP
- C. UTMWebtaering
- D. Juniper ATP Cloud CC feeds
Answer: AD
NEW QUESTION 17
You are asked to deploy multiple kiosk locations around the country. Their locations will change frequently and will need to access services in the corporate data center as well as other kiosk locations You need a central key location In this scenario, which solution would you deploy?
- A. Mesh VPN
- B. Group VPN
- C. Juniper Secure Connect
- D. Auto VPN
Answer: D
NEW QUESTION 18
You are designing a central management solution Your customer wants a togging solution that will support the collection of up to 10.000 events per second from many SRX Series devices that will be deployed m their network. In this scenario. which solution should you include in your design proposal?
- A. Log Oi rector
- B. Network Director
- C. Contrail Insights
- D. Contrail Server Orchestration
Answer: A
NEW QUESTION 19
Which two features would provide protection from known malware? (Choose two.)
- A. ALGs
- B. screens
- C. Junker ATP Cloud
- D. IPS
Answer: BC
NEW QUESTION 20
......
100% Valid and Newest Version JN0-1332 Questions & Answers shared by Certshared, Get Full Dumps HERE: https://www.certshared.com/exam/JN0-1332/ (New 65 Q&As)
