Our pass rate is high to 98.9% and the similarity percentage between our DOP-C01 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the Amazon-Web-Services DOP-C01 exam in just one try? I am currently studying for the Amazon-Web-Services DOP-C01 exam. Latest Amazon-Web-Services DOP-C01 Test exam practice questions and answers, Try Amazon-Web-Services DOP-C01 Brain Dumps First.
Check DOP-C01 free dumps before getting the full version:
NEW QUESTION 1
You have implemented a system to automate deployments of your configuration and application dynamically after an Amazon EC2 instance in an Auto Scaling group is launched. Your system uses a configuration management tool that works in a standalone configuration, where there is no master node. Due to the volatility of application load, new instances must be brought into service within three minutes of the launch of the instance operating system. The deployment stages take the following times to complete:
1) Installing configuration management agent: 2mins
2) Configuring instance using artifacts: 4mins
3) Installing application framework: 15mins
4) Deploying application code: 1min
What process should you use to automate the deployment using this type of standalone agent configuration?
- A. Configureyour Auto Scaling launch configuration with an Amazon EC2 UserData script toinstall the agent, pull configuration artifacts and application code from anAmazon S3 bucket, and then execute the agent to configure the infrastructureand application.
- B. Builda custom Amazon Machine Image that includes all components pre-installed,including an agent, configuration artifacts, application frameworks, and code.Create a startup script that executes the agent to configure the system onstartu
- C. *t
- D. Builda custom Amazon Machine Image that includes the configuration management agentand application framework pre-installed.Configure your Auto Scaling launchconfiguration with an Amazon EC2 UserData script to pull configurationartifacts and application code from an Amazon S3 bucket, and then execute theagent toconfigure the system.
- E. Createa web service that polls the Amazon EC2 API to check for new instances that arelaunched in an Auto Scaling grou
- F. When it recognizes a new instance, execute aremote script via SSH to install the agent, SCP the configuration artifacts andapplication code, and finally execute the agent to configure the system
Answer: B
Explanation:
Since the new instances need to be brought up in 3 minutes, hence the best option is to pre-bake all the components into an AMI. If you try to user the User Data option, it will just take time, based on the time mentioned in the question to install and configure the various components.
For more information on AMI design please see the below link:
• https://aws.amazon.com/answers/configuration-management/aws-ami-design/
NEW QUESTION 2
What is the amount of time that Opswork stacks services waits for a response from an underlying instance before deeming it as a failed instance?
- A. Iminute.
- B. 5minutes.
- C. 20minutes.
- D. 60minutes
Answer: B
Explanation:
The AWS Documentation mentions
Every instance has an AWS OpsWorks Stacks agent that communicates regularly with the service. AWS OpsWorks Stacks uses that communication to monitor instance health. If an agent does not communicate with the service for more than approximately five minutes, AWS OpsWorks Stacks considers the instance to have failed.
For more information on the Auto healing feature, please visit the below URL: http://docs.aws.amazon.com/opsworks/latest/userguide/workinginstances-auto healing.htmI
NEW QUESTION 3
You are using a configuration management system to manage your Amazon EC2 instances. On your Amazon EC2 Instances, you want to store credentials for connecting to an Amazon RDS MYSQL DB instance. How should you securely store these credentials?
- A. Give the Amazon EC2 instances an 1AM role that allows read access to a private Amazon S3 bucke
- B. Store a file with database credentials in the Amazon S3 bucke
- C. Have your configuration management system pull the file from the bucket when it is needed.
- D. Launch an Amazon EC2 instance and use the configuration management system to bootstrap the instance with the Amazon RDS DB credential
- E. Create an AMI from this instance.
- F. Store the Amazon RDS DB credentials in Amazon EC2 user dat
- G. Import the credentials into the Instance on boot.
- H. Assign an 1AM role to your Amazon EC2 instance, and use this 1AM role to access the Amazon RDS DB from your Amazon EC2 instances.
Answer: D
Explanation:
Creating and Using an 1AM Policy for 1AM Database Access
To allow an 1AM user or role to connect to your DB instance or DB cluster, you must create an 1AM policy. After that you attach the policy to an 1AM user or role.
Note
To learn more about 1AM policies, see Authentication and Access Control for Amazon RDS.
The following example policy allows an 1AM user to connect to a DB instance using 1AM database authentication.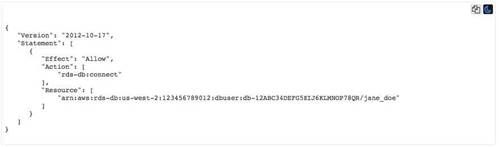
Important
Don't confuse the rds-db: prefix with other Amazon RDS action prefixes that begin with rds:. You use the rds-db: prefix and the rds-db:connect action only for 1AM database authentication. They aren't valid in any other context.
1AM Database Authentication for MySQL and Amazon Aurora
With Amazon RDS for MySQL or Aurora with MySQL compatibility, you can authenticate to your DB instance or DB cluster using AWS Identity and Access Management (IAMJ database authentication. With this authentication method, you don't need to use a password when you connect to a DB instance. Instead, you use an authentication token.
An authentication token is a unique string of characters that Amazon RDS generates on request. Authentication tokens are generated using AWS Signature Version 4. Each token has a lifetime of 15 minutes. You don't need to store user credentials in the database, because authentication is managed externally using 1AM. You can also still use standard database authentication.
IAM database authentication provides the following benefits:
• Network traffic to and from the database is encrypted using Secure Sockets Layer (SSL).
• You can use IAM to centrally manage access to your database resources, instead of managing access individually on each DB instance or DB cluster.
• For applications running on Amazon EC2, you can use EC2 instance profile credentials to access the database instead of a password, for greater security.
For more information please refer to the below document link from AWS https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/UsingWithRDS.IAMDBAuth.html https://docs^ws.amazon.com/AmazonRDS/latest/UserGuide/UsingWithRDS.IAMDBAuth.lAMPolicy. html
You can use roles to delegate access to users, applications, or services that don't normally have access to your AWS resources. For example, you might want to grant users in your AWS account access to resources they don't usually have, or grant users in one AWS account access to resources in another account. Or you might want to allow a mobile app to use AWS resources, but not want to embed AWS keys within the app (where they can be difficult to rotate and where users can potentially extract them). Sometimes you want to give AWS access to users who already have identities defined outside of AWS, such as in your corporate directory. Or, you might want to grant access to your account to third parties so that they can perform an audit on your resources. For more information on 1AM Roles, please refer to the below document link: from AWS
http://docs.aws.a mazon.com/IAM/latest/UserGuide/id_roles. html
NEW QUESTION 4
You are a Devops Engineer and are designing an Opswork stack in AWS. The company has some custom recipes that are part of their on-premise Chef configuration. These same recipes need to be run whenever an instance is launched in Opsworks. Which of the following steps need to be carried out to to ensure this requirement gets fulfilled. Choose 2 answers from the options given below
- A. Ensurethe custom cookbooks option is set in Opswork stack.
- B. Ensurethe custom cookbooks option is set in Opswork layer.
- C. Ensurethe recipe is placed as part of the Setup Lifecycle event as part of the Layersetting.
- D. Ensurethe recipe is placed as part of the Setup Lifecycle event as part of the Stacksetting.
Answer: AC
Explanation:
The AWS Documentation mentions the below
Each layer has a set of built-in recipes assigned to each lifecycle event, although some layers lack Undeploy recipes. When a lifecycle event occurs on an instance,
AWS OpsWorks Stacks runs the appropriate set of recipes for the associated layer.
The below diagram shows a snapshot in the stack settings where you can enable custom cookbooks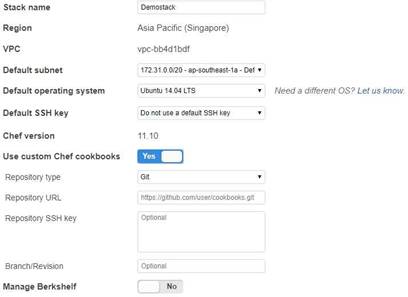
For more information on automating recipe's, please visit the below URL: http://docs.aws.amazon.com/opsworks/latest/userguide/workingcookbook-assigningcustom.html
NEW QUESTION 5
You are incharge of creating a Cloudformation template that will be used to spin our resources on demand for your Devops team. The requirement is that this cloudformation template should be able to spin up resources in different regions. Which of the following aspects of Cloudformation templates can help you design the template to spin up resources based on the region.
- A. Use mappings section in the Cloudformation template, so that based on the relevant region, the relevant resource can be spinned up.
- B. Use the outputs section in the Cloudformation template, so that based on the relevant region, the relevant resource can be spinned up.
- C. Use the parameters section in the Cloudformation template, so that based on the relevant region, the relevant resource can be spinned up.
- D. Use the metadata section in the Cloudformation template, so that based on the relevant region, the relevant resource can be spinned up.
Answer: A
Explanation:
The AWS Documentation mentions
The optional Mappings section matches a key to a corresponding set of named values. For example, if you want to set values based on a region, you can create a
mapping that uses the region name as a key and contains the values you want to specify for each specific region. You use the Fn::FindlnMap intrinsic function to
retrieve values in a map.
For more information on mappings please refer to the below link:
◆ http://docs.aws.amazon.com/AWSCIoudFormation/latest/UserGuide/mappings-section-structure.html
NEW QUESTION 6
Which of the following services can be used in conjunction with Cloudwatch Logs. Choose the 3 most viable services from the options given below
- A. Amazon Kinesis
- B. Amazon S3
- C. Amazon SQS
- D. Amazon Lambda
Answer: ABD
Explanation:
The AWS Documentation the following products which can be integrated with Cloudwatch logs
1) Amazon Kinesis - Here data can be fed for real time analysis
2) Amazon S3 - You can use CloudWatch Logs to store your log data in highly durable storage such as S3.
3) Amazon Lambda - Lambda functions can be designed to work with Cloudwatch log For more information on Cloudwatch Logs, please refer to the below link: link:http://docs^ws.amazon.com/AmazonCloudWatch/latest/logs/WhatlsCloudWatchLogs.html
NEW QUESTION 7
Which of the following is not a component of Elastic Beanstalk?
- A. Application
- B. Environment
- C. Docker
- D. ApplicationVersion
Answer: C
Explanation:
Answer - C
The following are the components of Clastic Beanstalk
1) Application - An Clastic Beanstalk application is a logical collection of Clastic Beanstalk components, including environments, versions, and environment configurations. In Clastic Beanstalk an application is conceptually similar to a folder
2) Application version - In Clastic Beanstalk, an application version refers to a specific, labeled iteration of deployable code for a web application
3) environment - An environment is a version that is deployed onto AWS resources. Cach environment runs only a single application version at a time, however you can run the same version or different versions in many environments at the same time.
4) environment Configuration - An environment configuration identifies a collection of parameters and settings that define how an environment and its associated resources behave.
5) Configuration Template - A configuration template is a starting point for creating unique environment configurations. For more information on the components of Clastic beanstalk please refer to the below link
http://docs.aws.amazon.com/elasticbeanstalk/latest/dg/concepts.components.html
NEW QUESTION 8
You are using lifecycle hooks in your AutoScaling Group. Because there is a lifecycle hook, the instance is put in the Pending:Wait state, which means that it is not available to handle traffic yet. When the instance enters the wait state, other scaling actions are suspended. After some time, the instance state is changed to Pending:Proceed, and finally InService where the instances that are part of the Autoscaling Group can start serving up traffic. But you notice that the bootstrapping process on the instances finish much earlier, long before the state is changed to PendingiProceed.
What can you do to ensure the instances are placed in the right state after the bootstrapping process is complete?
- A. Use the complete-lifecycle-action call to complete the lifecycle actio
- B. Run this command from another EC2 Instance.
- C. Use the complete-lifecycle-action call to complete the lifecycle actio
- D. Run this command from the Command line interfac
- E. -^C Use the complete-lifecycle-action call to complete the lifecycle actio
- F. Run this command from the Simple Notification service.
- G. Use the complete-lifecycle-action call to complete the lifecycle actio
- H. Run this command from a SQS queue
Answer: B
Explanation:
The AWS Documentation mentions the following
3. If you finish the custom action before the timeout period ends, use the complete-1ifecycle-action command so that the Auto Scalinggroup can continue launching
or terminating the instance. You can specify the lifecycle action token, as shown in the following command:
3. If you finish the custom action before the timeout period ends, use the complete-lifecycle-action command so that Auto Scaling can continue launching or terminating the instance. You can specify the lifecycle action token, as shown in the following command: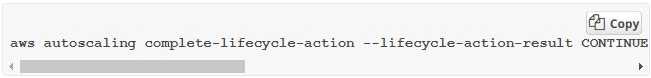
For more information on lifecycle hooks, please refer to the below URL:
• http://docs.aws.amazon.com/autoscaling/latest/userguide/lifecycle-hooks.htm I
NEW QUESTION 9
Your IT company is currently hosting a production environment in Elastic beanstalk. You understand that the Elastic beanstalk service provides a facility known as Managed updates which are minor and patch version updates which are periodically required for your system. Your IT supervisor is worried about the impact that these updates would have on the system. What can you tell about the Elastic beanstalk service with regards to managed updates
- A. Package updates can be configurable weekly maintenance window
- B. Elastic Beanstalk applies managed updates with no downtime
- C. Elastic Beanstalk applies managed updates with no reduction in capacity
- D. All of the above
Answer: D
Explanation:
The AWS Documentation mentions the following on package updates for the Clastic beanstalk environment
You can configure your environment to apply minor and patch version updates automatically during a configurable weekly maintenance window with Managed Platform Updates. Elastic Beanstalk applies managed updates with no downtime or reduction in capacity, and cancels the update immediately if instances running your application on the new version fail health checks.
For more information on Elastic beanstalk managed updates please refer to the URL: https://docs.aws.a mazon.com/elasticbeanstalk/latest/dg/environment- platform -update-managed, html
http://docs.aws.amazon.com/elasticbeanstalk/latest/dg/using-features.platform.upgrade.html
NEW QUESTION 10
You are in charge of designing a number of Cloudformation templates for your organization. You are required to make changes to stack resources every now and then based on the requirement. How can you check the impact of the change to resources in a cloudformation stack before deploying changes to the stack?
- A. Thereis no way to control thi
- B. You need to check for the impact beforehand.
- C. UseCloudformation change sets to check for the impact to the changes.
- D. UseCloudformation Stack Policies to check for the impact to the changes.
- E. UseCloudformation Rolling Updates to check for the impact to the changes.
Answer: B
Explanation:
The AWS Documentation mentions
When you need to update a stack, understanding how your changes will affect running resources before you implement them can help you update stacks with confidence. Change sets allow you to preview how proposed changes to a stack might impact your running resources, for example, whether your changes will delete or replace any critical resources, AWS CloudFormation makes the changes to your stack only when you decide to execute the change set, allowing you to decide whether to proceed with your proposed changes or explore other changes by creating another change set. You can create and manage change sets using the AWS
CloudFormation console, AWS CLI, or AWS CloudFormation API.
For more information on Cloudformation change sets, please visit the below url http://docs.aws.amazon.com/AWSCIoudFormation/latest/UserGuide/using-cfn-updating-stacks-changesets.html
NEW QUESTION 11
You are planning on using the Amazon RDS facility for Fault tolerance for your application. How does Amazon RDSmuIti Availability Zone model work
- A. A second, standby database is deployed and maintained in a different availability zone from master, using synchronous replication.
- B. A second, standby database is deployed and maintained in a different availability zone from master using asynchronous replication.
- C. A second, standby database is deployed and maintained in a different region from master using asynchronous replication.
- D. A second, standby database is deployed and maintained in a different region from master using synchronous replication.
Answer: A
Explanation:
Amazon RDS Multi-AZ deployments provide enhanced availability and durability for Database (DB)
Instances, making them a natural fit for production database
workloads. When you provision a Multi-AZ DB Instance, Amazon RDS automatically creates a primary DB Instance and synchronously replicates the data to a
standby instance in a different Availability Zone (AZ). Cach AZ runs on its own physically distinct, independent infrastructure, and is engineered to be highly reliable.
In case of an infrastructure failure, Amazon RDS performs an automatic failover to the standby (or to a read replica in the case of Amazon Aurora), so that you can
resume database operations as soon as the failover is complete.
The below diagram from the AWS documentation shows how this is configured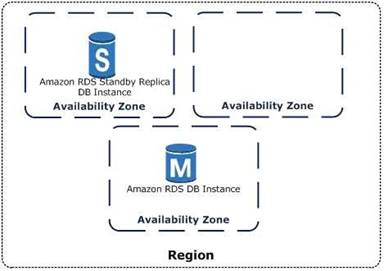
Option B is invalid because the replication is synchronous.
Option C and D are invalid because this is built around AZ and not regions. For more information on Multi-AZ RDS, please visit the below URL: https://aws.amazon.com/rds/details/multi-az/
NEW QUESTION 12
You have an ELB on AWS which has a set of web servers behind them. There is a requirement that the SSL key used to encrypt data is always kept secure. Secondly the logs of ELB should only be decrypted by a subset of users. Which of these architectures meets all of the requirements?
- A. UseElastic Load Balancing to distribute traffic to a set of web server
- B. Toprotect the SSL private key.upload the key to the load balancer and configure the load balancer to offloadthe SSL traffi
- C. Write yourweb server logs to an ephemeral volume that has been encrypted using a randomlygenerated AES key.
- D. UseElastic Load Balancing to distribute traffic to a set of web server
- E. Use TCPIoad balancing on theload balancer and configure your web servers to retrieve the private key from aprivate Amazon S3bucket on boo
- F. Write your web server logs to a private Amazon S3 bucket usingAmazon S3 server- sideencryption.
- G. UseElastic Load Balancing to distribute traffic to a set of web servers, configurethe load balancer toperform TCP load balancing, use an AWS CloudHSM to perform the SSLtransactions, and write yourweb server logs to a private Amazon S3 bucket using Amazon S3 server-sideencryption.
- H. UseElastic Load Balancing to distribute traffic to a set of web server
- I. Configurethe load balancer toperform TCP load balancing, use an AWS CloudHSM to perform the SSLtransactions, and write yourweb server logs to an ephemeral volume that has been encrypted using a randomlygenerated AES key.
Answer: C
Explanation:
The AWS CIoudHSM service helps you meet corporate, contractual and regulatory compliance requirements for data security by using dedicated Hardware Security
Module (HSM) appliances within the AWS cloud. With CIoudHSM, you control the encryption keys and cryptographic operations performed by the HSM.
Option D is wrong with the CIoudHSM option because of the ephemeral volume which this is temporary storage
For more information on cloudhsm, please refer to the link:
• https://aws.amazon.com/cloudhsm/
NEW QUESTION 13
You have a requirement to host a cluster of NoSQL databases. There is an expectation that there will be a lot of I/O on these databases. Which EBS volume type is best for high performance NoSQL cluster deployments?
- A. io1
- B. gp1
- C. standard
- D. gp2
Answer: A
Explanation:
Provisioned IOPS SSD should be used for critical business applications that require sustained IOPS performance, or more than 10,000 IOPS or 160 MiB/s of throughput per volume
This is ideal for Large database workloads, such as:
• MongoDB
• Cassandra
• MicrosoftSQL Server
• MySQL
• PostgreSQL
• Oracle
For more information on the various CBS Volume Types, please refer to the below link:
• http://docs.aws.amazon.com/AWSCC2/latest/UserGuide/ CBSVolumeTvpes.html
NEW QUESTION 14
A vendor needs access to your AWS account. They need to be able to read protected messages in a private S3 bucket. They have a separate AWS account. Which of the solutions below is the best way to do this?
- A. Allowthe vendor to ssh into your EC2 instance and grant them an 1AM role with fullaccess to the bucket.
- B. Createa cross-account 1AM role with permission to access the bucket, and grantpermission to use the role to the vendor AWS account.
- C. Createan 1AM User with API Access Key
- D. Give the vendor the AWS Access Key ID and AWSSecret Access Key for the user.
- E. Createan S3 bucket policy that allows the vendor to read from the bucket from theirAWS account.
Answer: B
Explanation:
The AWS Documentation mentions the following on cross account roles
You can use AWS Identity and Access Management (I AM) roles and AWS Security Token Service (STS) to set up cross-account access between AWS accounts. When you assume an 1AM role in another AWS account to obtain cross-account access to services and resources in that account, AWS CloudTrail logs the cross-account activity. For more information on Cross account roles, please visit the below URL
http://docs.aws.amazon.com/IAM/latest/UserGuide/tuto rial_cross-account-with-roles.htm I https://docs.aws.amazon.com/AmazonS3/latest/dev/example-walkthroughs-managing-access- example2.html
NEW QUESTION 15
Your company has a set of development teams that work in a variety of programming languages. They develop applications which have a lot of different application dependencies. There is a move from the company to move these development environments onto AWS. Which of the below is the best option to make this happen.
- A. Usethe Cloudformation service to create docker containers for each type ofapplication
- B. Usethe Elastic beanstalk service and use Docker containers to host eachapplication environment for the developer community
- C. Usethe Opswork service, create a stack and create separate layers for eachappl ication environment for the developer community
- D. Launch separate EC2 Instances to host each application type for the developercommunity
Answer: B
Explanation:
The AWS Documentation mentions the following
Clastic Beanstalk supports the deployment of web applications from Docker containers. With Docker containers, you can define your own runtime environment. You can choose your own platform, programming language, and any application dependencies (such as package managers or tools), that aren't supported by other platforms. Docker containers are self-contained and include all the configuration information and software your web application requires to run.
For more information on Elastic Beanstalk and docker, please refer to the below U RL: http://docs.aws.amazon.com/elasticbeanstalk/latest/dg/create_deploy_docker.html
NEW QUESTION 16
You've been tasked with building out a duplicate environment in another region for disaster recovery purposes. Part of your environment relies on EC2 instances with preconfigured software. What steps would you take to configure the instances in another region? Choose the correct answer from the options below
- A. Createan AMI oftheEC2 instance
- B. CreateanAMIoftheEC2instanceandcopytheAMItothedesiredregion
- C. Makethe EC2 instance shareable among other regions through 1AM permissions
- D. Noneof the above
Answer: B
Explanation:
You can copy an Amazon Machine Image (AMI) within or across an AWS region using the AWS Management Console, the AWS command line tools or SDKs, or the Amazon CC2 API, all of which support the Copylmage action. You can copy both Amazon CBS-backed AM Is and instance store-backed AM Is. You can copy AMIs with encrypted snapshots and encrypted AMIs.
For more information on copying AMI's, please refer to the below link:
• http://docs.aws.amazon.com/AWSCC2/latest/UserGuide/CopyingAMIs.htTTil
NEW QUESTION 17
Your company has an application hosted on an Elastic beanstalk environment. You have been instructed that whenever application changes occur and new versions need to be deployed that the fastest deployment approach is employed. Which of the following deployment mechanisms will fulfil this requirement?
- A. Allatonce
- B. Rolling
- C. Immutable
- D. Rollingwith batch
Answer: A
Explanation:
The following table from the AWS documentation shows the deployment time for each deployment methods.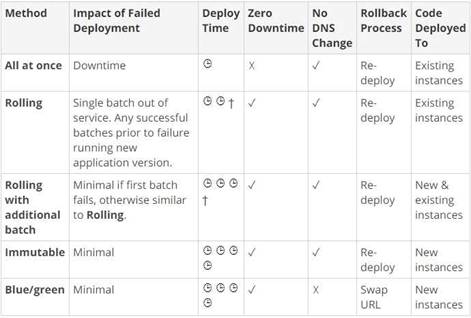
For more information on Elastic beanstalk deployments, please refer to the below link: http://docs.aws.amazon.com/elasticbeanstalk/latest/dg/using-features.deploy-existing- version, htm I
NEW QUESTION 18
You have a current Clouformation template defines in AWS. You need to change the current alarm threshold defined in the Cloudwatch alarm. How can you achieve this?
- A. Currently, there is no option to change what is already defined in Cloudformation templates.
- B. Update the template and then update the stack with the new templat
- C. Automatically all resources will be changed in the stack.
- D. Update the template and then update the stack with the new templat
- E. Only those resources that need to be changed will be change
- F. All other resources which do not need to be changed will remain as they are.
- G. Delete the current cloudformation templat
- H. Create a new one which will update the current resources.
Answer: C
Explanation:
Option A is incorrect because Cloudformation templates have the option to update resources.
Option B is incorrect because only those resources that need to be changed as part of the stack update are actually updated.
Option D is incorrect because deleting the stack is not the ideal option when you already have a change option available.
When you need to make changes to a stack's settings or change its resources, you update the stack instead of deleting it and creating a new stack. For example, if you
have a stack with an EC2 instance, you can update the stack to change the instance's AMI ID.
When you update a stack, you submit changes, such as new input parameter values or an updated template. AWS CloudFormation compares the changes you submit with the current state of your stack and updates only the changed resources
For more information on stack updates please refer to the below link:
• http://docs.aws.a mazon.com/AWSCIoudFormation/latest/UserGuide/using-cfn-updating- stacks.htmI
NEW QUESTION 19
Your development team wants account-level access to production instances in order to do live debugging of a highly secure environment. Which of the following should you do?
- A. Place the credentials provided by Amazon Elastic Compute Cloud (EC2) into a secure Amazon Sample Storage Service (S3) bucket with encryption enable
- B. Assign AWS Identity and Access Management (1AM) users to each developer so they can download the credentials file.
- C. Place an internally created private key into a secure S3 bucket with server-side encryption using customer keys andconfiguration management, create a service account on al I the instances using this private key, and assign I AM users to each developer so they can download the fi le.
- D. Place each developer's own public key into a private S3 bucket, use instance profiles and configuration management to create a user account for each developer on all instances, and place the user's public keys into the appropriate accoun
- E. ^/
- F. Place the credentials provided by Amazon EC2 onto an MFA encrypted USB drive, and physically share it with each developer so that the private key never leaves the office.
Answer: C
Explanation:
An instance profile is a container for an 1AM role that you can use to pass role information to an CC2 instance when the instance starts.
A private S3 bucket can be created for each developer, the keys can be stored in the bucket and then assigned to the instance profile.
Option A and D are invalid, because the credentials should not be provided by a AWS EC2 Instance. Option B is invalid because you would not create a service account, instead you should create an instance profile.
For more information on Instance profiles, please refer to the below document link: from AWS
• http://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use_switch-ro le-ec2_instance- profiles.htm I
NEW QUESTION 20
You are creating a cloudformation templates which takes in a database password as a parameter. How can you ensure that the password is not visible when anybody tries to describes the stack
- A. Usethe password attribute for the resource
- B. Usethe NoEcho property for the parameter value
- C. Usethe hidden property for the parameter value
- D. Setthe hidden attribute for the Cloudformation resource.
Answer: B
Explanation:
The AWS Documentation mentions
For sensitive parameter values (such as passwords), set the NoEcho property to true. That way, whenever anyone describes your stack, the parameter value is shown as asterisks (*•*").
For more information on Cloudformation parameters, please visit the below URL:
• http://docs.aws.amazon.com/AWSCIoudFormation/latest/UserGuide/parameters-section- structure.html
NEW QUESTION 21
A company has EC2 instances running in AWS. The EC2 instances are running via an Autoscaling solution. There is a lot of requests being lost because of the load on the servers. The Autoscaling solution is launching new instances to take the load but there are still some requests which are being lost. Which of the following is likely to provide the most cost-effective solution to avoid losing recently submitted requests? Choose the correct answer from the options given below
- A. UseanSQS queue to decouple the application components
- B. Keepone extra EC2 instance always powered on in case a spike occurs
- C. Uselarger instances for your application
- D. Pre -warmyour Elastic Load Balancer
Answer: A
Explanation:
Amazon Simple Queue Service (SQS) is a fully-managed message queuing service for reliably communicating among distributed software components and microservices - at any scale. Building applications from individual components that each perform a discrete function improves scalability and reliability, and is best practice design for modern applications
For more information on SQS, please refer to the below link:
• https://aws.amazon.com/sqs/
NEW QUESTION 22
Your development team is using an Elastic beanstalk environment. After a week, the environment was torn down and a new one was created. When the development team tried to access the data on the older environment, it was not available. Why is this the case?
- A. Thisis because the underlying EC2 Instances are created with encrypted storage andcannot be accessed once the environment has been terminated.
- B. Thisis because the underlying EC2 Instances are created with IOPS volumes andcannot be accessed once the environment has been terminated.
- C. Thisis because before the environment termination, Elastic beanstalk copies thedata to DynamoDB, and hence the data is not present in the EBS volumes
- D. Thisis because the underlying EC2 Instances are created with no persistent localstorage
Answer: D
Explanation:
The AWS documentation mentions the following
Clastic Beanstalk applications run on Amazon CC2 instances that have no persistent local storage.
When the Amazon CC2 instances terminate, the local file system is not saved, and new Amazon CC2 instances start with a default file system. You should design your application to store data in a persistent data source.
For more information on Elastic beanstalk design concepts, please refer to the below link: http://docs.aws.amazon.com/elasticbeanstalk/latest/dg/concepts.concepts.design.htmI
NEW QUESTION 23
......
Thanks for reading the newest DOP-C01 exam dumps! We recommend you to try the PREMIUM Surepassexam DOP-C01 dumps in VCE and PDF here: https://www.surepassexam.com/DOP-C01-exam-dumps.html (116 Q&As Dumps)
