We provide real NSE4_FGT-6.4 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass Fortinet NSE4_FGT-6.4 Exam quickly & easily. The NSE4_FGT-6.4 PDF type is available for reading and printing. You can print more and practice many times. With the help of our Fortinet NSE4_FGT-6.4 dumps pdf and vce product and material, you can easily pass the NSE4_FGT-6.4 exam.
Online NSE4_FGT-6.4 free questions and answers of New Version:
NEW QUESTION 1
Refer to the exhibits.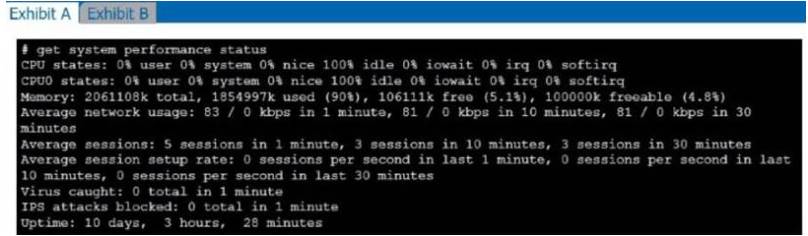
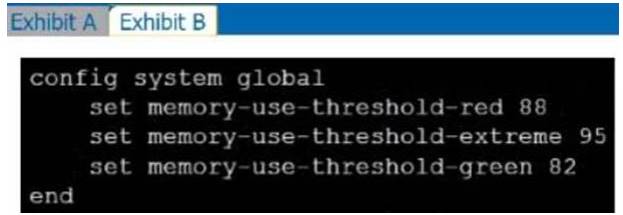
Exhibit A shows system performance output. Exhibit B shows a FortiGate configured with the default configuration of high memory usage thresholds. Based on the system performance output, which two statements are correct? (Choose two.)
- A. Administrators can access FortiGate only through the console port.
- B. FortiGate has entered conserve mode.
- C. FortiGate will start sending all files to FortiSandbox for inspection.
- D. Administrators cannot change the configuration.
Answer: CD
NEW QUESTION 2
Examine this FortiGate configuration: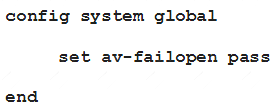
Examine the output of the following debug command: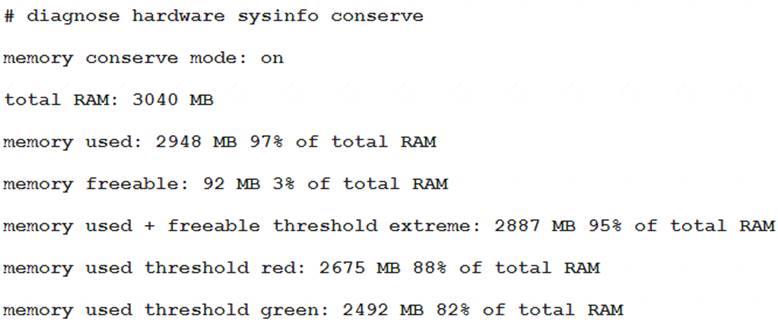
Based on the diagnostic outputs above, how is the FortiGate handling the traffic for new sessions that require inspection?
- A. It is allowed, but with no inspection
- B. It is allowed and inspected as long as the inspection is flow based
- C. It is dropped.
- D. It is allowed and inspected, as long as the only inspection required is antivirus.
Answer: C
NEW QUESTION 3
Which type of logs on FortiGate record information about traffic directly to and from the FortiGate management IP addresses?
- A. System event logs
- B. Forward traffic logs
- C. Local traffic logs
- D. Security logs
Answer: A
NEW QUESTION 4
Examine this PAC file configuration.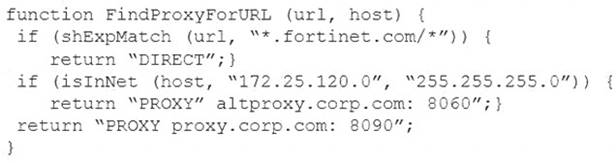
Which of the following statements are true? (Choose two.)
- A. Browsers can be configured to retrieve this PAC file from the FortiGate.
- B. Any web request to the 172.25.120.0/24 subnet is allowed to bypass the proxy.
- C. All requests not made to Fortinet.com or the 172.25.120.0/24 subnet, have to go through altproxy.corp.com: 8060.
- D. Any web request fortinet.com is allowed to bypass the proxy.
Answer: AD
NEW QUESTION 5
Examine this FortiGate configuration: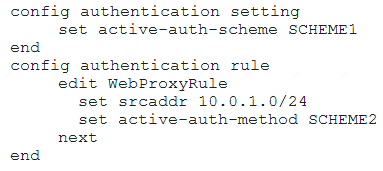
How does the FortiGate handle web proxy traffic coming from the IP address 10.2.1.200 that requires authorization?
- A. It always authorizes the traffic without requiring authentication.
- B. It drops the traffic.
- C. It authenticates the traffic using the authentication scheme SCHEME2.
- D. It authenticates the traffic using the authentication scheme SCHEME1.
Answer: D
Explanation:
“What happens to traffic that requires authorization, but does not match any authentication rule? The active and passive SSO schemes to use for those cases is defined under config authentication setting”
NEW QUESTION 6
Refer to the exhibit.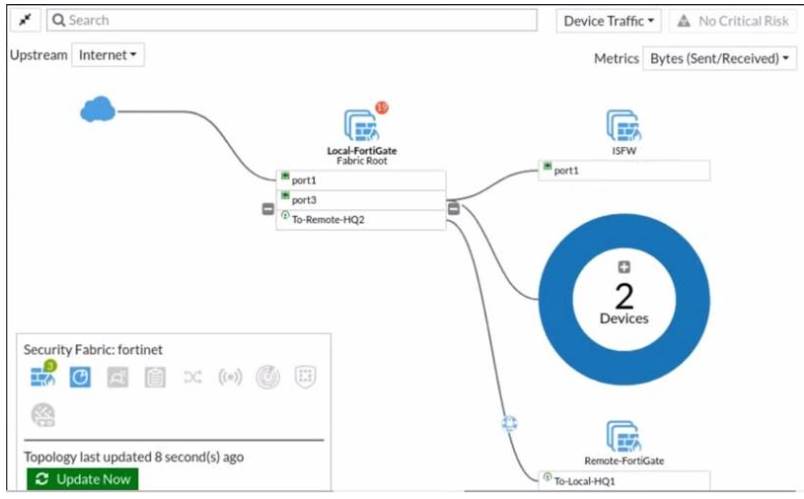
Given the security fabric topology shown in the exhibit, which two statements are true? (Choose two.)
- A. This security fabric topology is a logical topology view.
- B. There are 19 security recommendations for the security fabric.
- C. There are five devices that are part of the security fabric.
- D. Device detection is disabled on all FortiGate devices.
Answer: AD
NEW QUESTION 7
NGFW mode allows policy-based configuration for most inspection rules. Which security profile’s configuration does not change when you enable policy-based inspection?
- A. Web filtering
- B. Antivirus
- C. Web proxy
- D. Application control
Answer: B
NEW QUESTION 8
An administrator has configured two-factor authentication to strengthen SSL VPN access. Which additional best practice can an administrator implement?
- A. Configure Source IP Pools.
- B. Configure split tunneling in tunnel mode.
- C. Configure different SSL VPN realms.
- D. Configure host check.
Answer: D
NEW QUESTION 9
How do you format the FortiGate flash disk?
- A. Load a debug FortiOS image.
- B. Load the hardware test (HQIP) image.
- C. Execute the CLI command execute formatlogdisk.
- D. Select the format boot device option from the BIOS menu.
Answer: D
NEW QUESTION 10
Refer to the exhibit.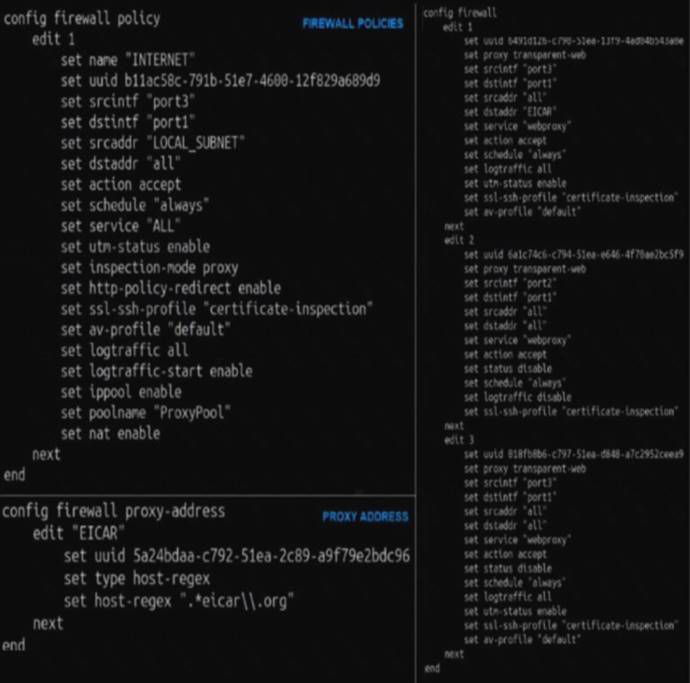
The exhibit shows a CLI output of firewall policies, proxy policies, and proxy addresses.
How does FortiGate process the traffic sent to http://www.fortinet.com?
- A. Traffic will be redirected to the transparent proxy and it will be allowed by proxy policy ID 3.
- B. Traffic will not be redirected to the transparent proxy and it will be allowed by firewall policy ID 1.
- C. Traffic will be redirected to the transparent proxy and It will be allowed by proxy policy ID 1.
- D. Traffic will be redirected to the transparent proxy and it will be denied by the proxy implicit deny policy.
Answer: D
NEW QUESTION 11
What types of traffic and attacks can be blocked by a web application firewall (WAF) profile? (Choose three.)
- A. Traffic to botnetservers
- B. Traffic to inappropriate web sites
- C. Server information disclosure attacks
- D. Credit card data leaks
- E. SQL injection attacks
Answer: ACE
NEW QUESTION 12
An administrator has configured a strict RPF check on FortiGate. Which statement is true about the strict RPF check?
- A. The strict RPF check is run on the first sent and reply packet of any new session.
- B. Strict RPF checks the best route back to the sourceusingtheincoming interface.
- C. Strict RPF checks only for the existence of at cast one active route back to the source using the incoming interface.
- D. Strict RPF allows packets back to sources with all active routes.
Answer: A
NEW QUESTION 13
Which of statement is true about SSL VPN web mode?
- A. The tunnel is up while the client is connected.
- B. It supports a limited number of protocols.
- C. The external network application sends data through the VPN.
- D. It assigns a virtual IP address to the client.
Answer: C
NEW QUESTION 14
Refer to the exhibit.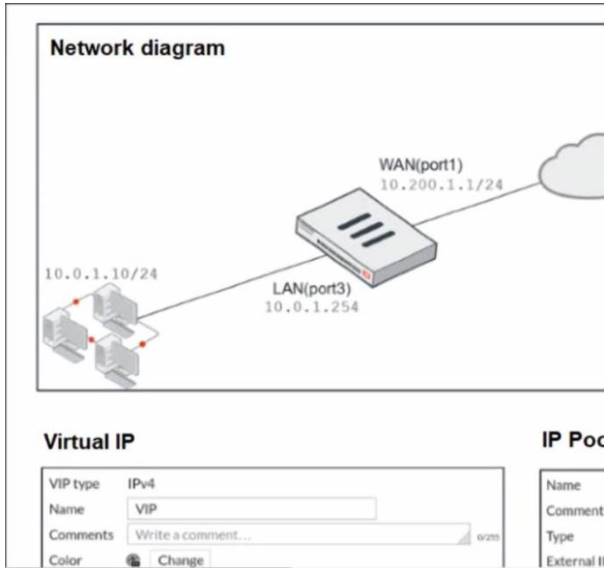
The exhibit contains a network diagram, virtual IP, IP pool, and firewall policies configuration. The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10 .0.1.254. /24. The first firewall policy has NAT enabled using IP Pool.
The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the internet traffic coming from a workstation with the IP address 10.0.1.10?
- A. 10.200.1.1
- B. 10.200.3.1
- C. 10.200.1.100
- D. 10.200.1.10
Answer: A
NEW QUESTION 15
In consolidated firewall policies, IPv4 and IPv6 policies are combined in a single consolidated policy. Instead of separate policies. Which three statements are true about consolidated IPv4 and IPv6 policy configuration? (Choose three.)
- A. The IP version of the sources and destinations in a firewall policy must be different.
- B. The Incoming Interfac
- C. Outgoing Interfac
- D. Schedule, and Service fields can be shared with both IPv4and IPv6.
- E. The policy table in the GUI can be filtered to display policies with IPv4, IPv6 or IPv4 and IPv6 sources and destinations.
- F. The IP version of the sources and destinations in a policy must match.
- G. The policy table in the GUI will be consolidated to display policies with IPv4 and IPv6 sources and destinations.
Answer: ACE
NEW QUESTION 16
Which two settings can be separately configured per VDOM on a FortiGate device? (Choose two.)
- A. System time
- B. FortiGuaid update servers
- C. Operating mode
- D. NGFW mode
Answer: AD
NEW QUESTION 17
Examine the following web filtering log.
Which statement about the log message is true?
- A. The action for the category Games is set to block.
- B. The usage quota for the IP address 10.0.1.10 has expired
- C. The name of the applied web filter profile is default.
- D. The web site miniclip.com matches a static URL filter whose action is set to Warning.
Answer: C
NEW QUESTION 18
Why does FortiGate Keep TCP sessions in the session table for several seconds, even after both sides (client and server) have terminated the session?
- A. To allow for out-of-order packets that could arrive after the FIN/ACK packets
- B. To finish any inspection operations
- C. To remove the NAT operation
- D. To generate logs
Answer: B
NEW QUESTION 19
Which CLI command will display sessions both from client to the proxy and from the proxy to the servers?
- A. diagnose wad session list
- B. diagnose wad session list | grep hook-pre&&hook-out
- C. diagnose wad session list | grep hook=pre&&hook=out
- D. diagnose wad session list | grep "hook=pre"&"hook=out"
Answer: D
NEW QUESTION 20
Which certificate value can FortiGate use to determine the relationship between the issuer and the certificate?
- A. Subject Key Identifiervalue
- B. SMMIE Capabilitiesvalue
- C. Subjectvalue
- D. Subject Alternative Namevalue
Answer: C
NEW QUESTION 21
Which statement about the IP authentication header (AH) used by IPsec is true?
- A. AH does not provide any data integrity or encryption.
- B. AH does not support perfect forward secrecy.
- C. AH provides data integrity bur no encryption.
- D. AH provides strong data integrity but weak encryption.
Answer: C
NEW QUESTION 22
Which three statements about security associations (SA) in IPsec are correct? (Choose three.)
- A. Phase 2 SAs are used for encrypting and decrypting the data exchanged through the tunnel.
- B. An SA never expires.
- C. A phase 1 SA is bidirectional, while a phase 2 SA is directional.
- D. Phase 2 SA expiration can be time-based, volume-based, or both.
- E. Both the phase 1 SA and phase 2 SA are bidirectional.
Answer: BCD
NEW QUESTION 23
Refer to the exhibits.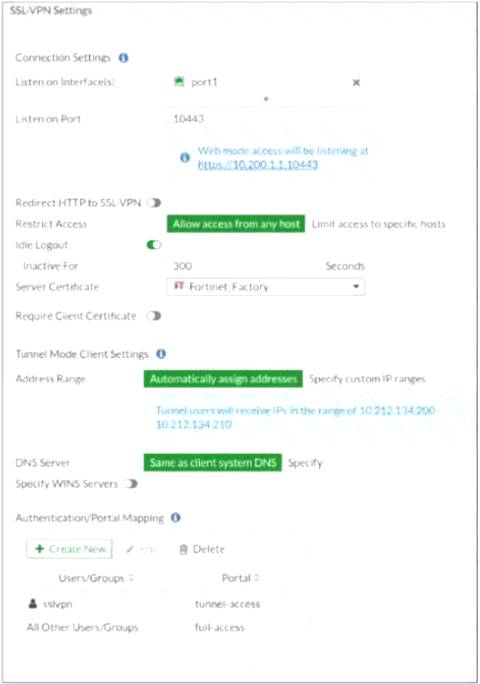
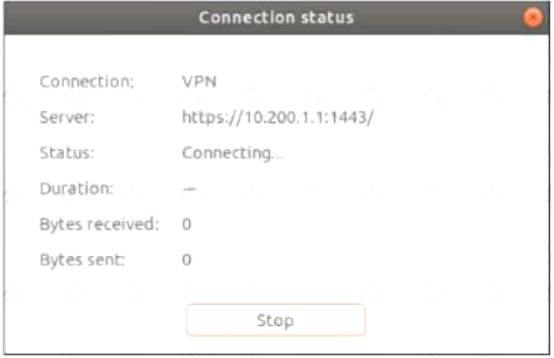
The SSL VPN connection fails when a user attempts to connect to it. What should the user do to successfully connect to SSL VPN?
- A. Change the SSL VPN port on the client.
- B. Change the Server IP address.
- C. Change the idle-timeout.
- D. Change the SSL VPN portal to the tunnel.
Answer: D
NEW QUESTION 24
Which two statements are correct regarding FortiGate HA cluster virtual IP addresses? (Choose two.)
- A. Heartbeat interfaces have virtual IP addresses that are manually assigned.
- B. A change in the virtual IP address happens when a FortiGate device joins or leaves the cluster.
- C. Virtual IP addresses are used to distinguish between cluster members.
- D. The primary device in the clusteris always assigned IP address 169.254.0.1.
Answer: AB
NEW QUESTION 25
A network administrator is configuring a new IPsec VPN tunnel on FortiGate. The remote peer IP address is dynamic, in addition, the remote peer does not support a dynamic DNS update service. What type of remote gateway should tie administrator configure on FortiGate for the new IPsec VPN tunnel to work?
- A. Static IP Address
- B. Dialup User
- C. Dynamic DNS
- D. Pre-shared Key
Answer: C
NEW QUESTION 26
......
100% Valid and Newest Version NSE4_FGT-6.4 Questions & Answers shared by Downloadfreepdf.net, Get Full Dumps HERE: https://www.downloadfreepdf.net/NSE4_FGT-6.4-pdf-download.html (New 94 Q&As)
