It is more faster and easier to pass the by using . Immediate access to the and find the same core area with professionally verified answers, then PASS your exam with a high score now.
Free NSE4 Demo Online For Microsoft Certifitcation:
NEW QUESTION 1
Which of the following statements is true regarding the TCP SYN packets that go from a client, through an implicit web proxy (transparent proxy), to a web server listening at TCP port 80? (Choose three.)
- A. The source IP address matches the client IP address.
- B. The source IP address matches the proxy IP address.
- C. The destination IP address matches the proxy IP address.
- D. The destination IP address matches the server IP addresses.
- E. The destination TCP port number is 80.
Answer: ADE
NEW QUESTION 2
A firewall policy has been configured for the internal email server to receive email from external parties through SMTP. Exhibits A and B show the antivirus and email filter profiles applied to this policy.
Exhibit A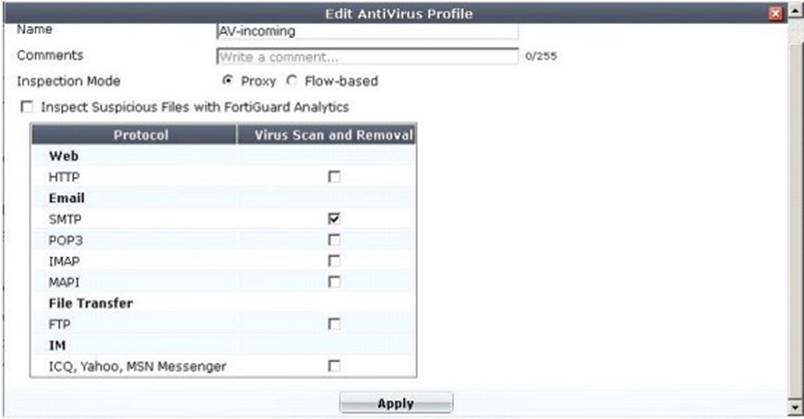
Exhibit B: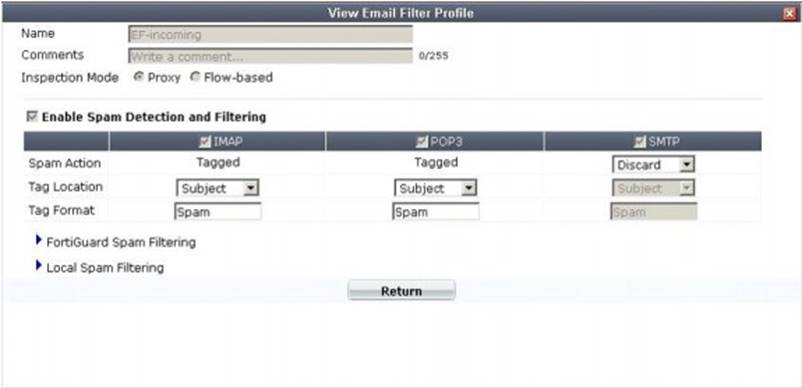
What is the correct behavior when the email attachment is detected as a virus by the FortiGate antivirus engine?
- A. The FortiGate unit will remove the infected file and deliver the email with a replacement message to alert the recipient that the original attachment was infected.
- B. The FortiGate unit will reject the infected email and the sender will receive a failed delivery message.
- C. The FortiGate unit will remove the infected file and add a replacement messag
- D. Both sender and recipient are notified that the infected file has been removed.
- E. The FortiGate unit will reject the infected email and notify the sender.
Answer: B
NEW QUESTION 3
Which protocol can an Internet browser use to download the PAC file with the web proxy configuration?
- A. HTTPS
- B. FTP
- C. TFTP
- D. HTTP
Answer: D
NEW QUESTION 4
Which of the following statements are correct concerning the IPsec phase 1 and phase 2, shown in the exhibit? (choose two)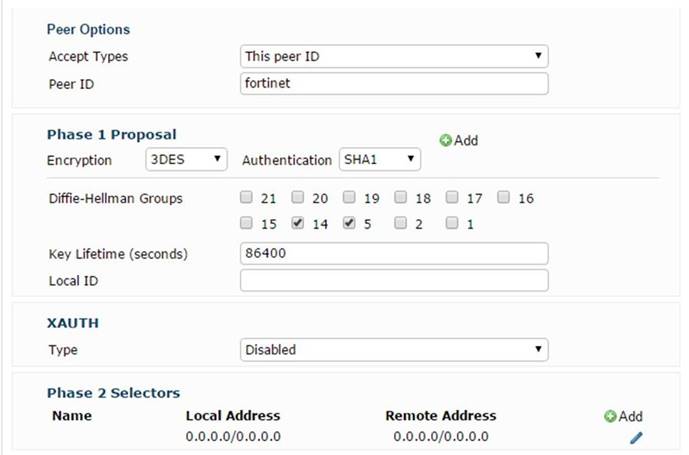
- A. The quick mode selector in the remote site must also be 0.0.0.0/0 for the source and destination addresses.
- B. Only remote peers with the peer ID 'fortinet' will be able to establish a VPN.
- C. The FortiGate device will automatically add a static route to the source quick mode selector address received from each remote VPN peer.
- D. The configuration will work only to establish FortiClient-to-FortiGate tunnel
- E. A FortiGate tunnel requires a different configuration.
Answer: CD
NEW QUESTION 5
There are eight (8) log severity levels that indicate the importance of an event. Not including Debug, which is only needed to log diagnostic data, what are both the lowest AND highest severity levels?
- A. Notification, Emergency
- B. Information, Critical
- C. Error, Critical
- D. Information, Emergency
- E. Information, Alert
Answer: D
NEW QUESTION 6
Which TCP states does the global setting ‘tcp-half-open-timer’ applies to? (Choose two.)
- A. SYN SENT
- B. SYN & SYN/ACK
- C. FIN WAIT
- D. TIME WAIT
Answer: AD
NEW QUESTION 7
Your Linux email server runs on a non-standard port number, port 2525. Which statement is true?
- A. IPS cannot scan that traffic for SMTP anomalies because of the non-standard port numbe
- B. You must reconfigured the server to run on port 2.
- C. To apply IPS to traffic to that server, you must configured FortiGate SMTP proxy to listen on port 2525
- D. IPS will apply all SMTP signatures, regardless of whether they apply to clients or servers.
- E. Protocol decoders automatically detect SMTP and scan for matches with appropriate IPS signature.
Answer: B
NEW QUESTION 8
A FortiGate device is configure to perform an AV & IPS scheduled update every hour.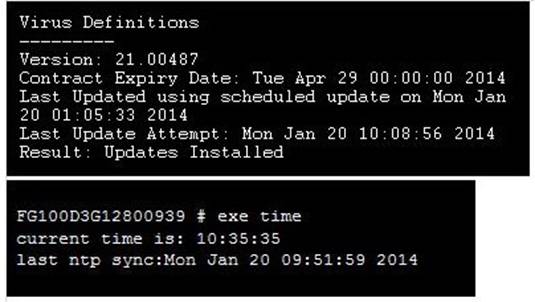
Given the information in the exhibit, when will the next update happen?
- A. 01:00
- B. 02:05
- C. 11:00
- D. 11:08
Answer: D
NEW QUESTION 9
What capabilities can a FortiGate provide? (Choose three)
- A. Mail relay
- B. Email filtering
- C. Firewall
- D. VPN gateway
- E. Mail server
Answer: BCD
NEW QUESTION 10
Examine the following output from the diagnose sys session list command: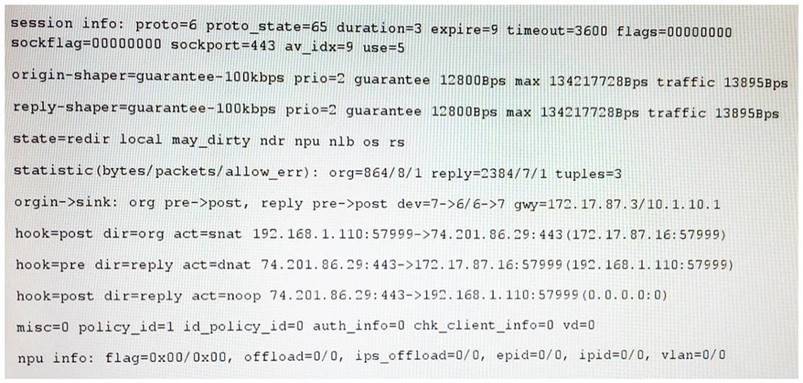
Which statements are true regarding the session above? (Choose two.)
- A. Session Time-To-Live (TTL) was configured to 9 seconds.
- B. FortiGate is doing NAT of both the source and destination IP address on all packets coming from the 192.168.1.110 address.
- C. The IP address 192.168.1.110 is being translated to 172.17.87.16.
- D. The FortiGate is not translating the TCP port numbers of the packets in this session.
Answer: CD
NEW QUESTION 11
An administrator configures a FortiGate unit in Transparent mode on the 192.168.11.0 subnet. Automatic Discovery is enabled to detect any available FortiAnalyzers on the
network.
Which of the following FortiAnalyzers will be detected?
- A. 192.168.11.100
- B. 192.168.11.251
- C. 192.168.10.100
- D. 192.168.10.251
Answer: AB
NEW QUESTION 12
Which are outputs for the command ‘diagnose hardware deviceinfo nic’? (Choose two.)
- A. ARP cache
- B. Physical MAC address
- C. Errors and collisions
- D. Listening TCP ports
Answer: BC
NEW QUESTION 13
A FortiGate is configured to receive push updates from the FortiGuard Distribution Network, however, they are not being received.
Which of the following statements are possible reasons for this?
A FortiGate unit is configured to receive push updates from the FortiGuard Distribution Network, however, updates are not being received. Which of the following statements are possible reasons for this? (Select all that apply.)
- A. The external facing interface of the FortiGate unit is configured to use DHCP.
- B. The FortiGate unit has not been registered.
- C. There is a NAT device between the FortiGate unit and the FortiGuard Distribution Network and no override push IP is configured.
- D. The FortiGate unit is in Transparent mode which does not support push updates.
Answer: ABC
NEW QUESTION 14
Which of the following statements are true about IPsec VPNs? (Choose three.)
- A. IPsec increases overhead and bandwidth.
- B. IPsec operates at the layer 2 of the OSI model.
- C. End-user's network applications must be properly pre-configured to send traffic across the IPsec VPN.
- D. IPsec protects upper layer protocols.
- E. IPsec operates at the layer 3 of the OSI model.
Answer: ADE
NEW QUESTION 15
Which of the following statements is true regarding a FortiGate device operating in transparent mode? (Choose three.)
- A. It acts as a layer 2 bridge
- B. It acts as a layer 3 router
- C. It forwards frames using the destination MAC address.
- D. It forwards packets using the destination IP address.
- E. It can perform content inspection (antivirus, web filtering, etc)
Answer: ACE
NEW QUESTION 16
Which of the following are benefits of using web caching? (Choose three.)
- A. Decrease bandwidth utilization
- B. Reduce server load
- C. Reduce FortiGate CPU usage
- D. Reduce FortiGate memory usage
- E. Decrease traffic delay
Answer: ABE
P.S. Easily pass NSE4 Exam with 301 Q&As Certleader Dumps & pdf Version, Welcome to Download the Newest Certleader NSE4 Dumps: https://www.certleader.com/NSE4-dumps.html (301 New Questions)
