It is more faster and easier to pass the Paloalto-Networks PCCSA exam by using Approved Paloalto-Networks Palo Alto Networks Certified Cybersecurity Associate questuins and answers. Immediate access to the Avant-garde PCCSA Exam and find the same core area PCCSA questions with professionally verified answers, then PASS your exam with a high score now.
Also have PCCSA free dumps questions for you:
NEW QUESTION 1
What are two methods to securely transmit personally identifiable information? (Choose two.)
- A. data checksumming
- B. data fragmentation
- C. data encryption
- D. encrypted tunnels
Answer: CD
NEW QUESTION 2
Which device would an Evil Twin attack use to lure the victim to connect to the attack surface network?
- A. switch
- B. firewall
- C. router
- D. access point
Answer: D
NEW QUESTION 3
What is a component of a public key infrastructure?
- A. Key Distribution Center
- B. KDC ticket
- C. SSH key
- D. certificate authority
Answer: D
NEW QUESTION 4
Which type of attack floods a target with ICMP requests?
- A. route table poisoning
- B. reconnaissance
- C. IP spoofing
- D. denial-of-service
Answer: D
NEW QUESTION 5
Match each type of breach to its consequence.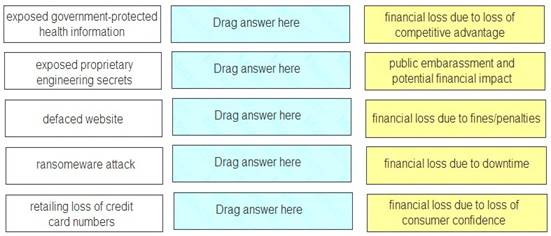
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Exposed government-protected health information – financial loss due to fines/penalties Exposed proprietary engineering secrets – financial loss due to loss of competitive advantage Defaced website – public embarrassment and potential financial impact
Ransomware attack – financial loss due to downtime
Retailing loss of credit card numbers – financial loss due to consumer confidence
NEW QUESTION 6
Which network method securely connects two sites across a public network?
- A. VPN
- B. VLAN
- C. switch
- D. router
Answer: A
NEW QUESTION 7
Assume that it is your responsibility to secure the software functioning at all layers in the exhibit. Which cloud service model type is represented?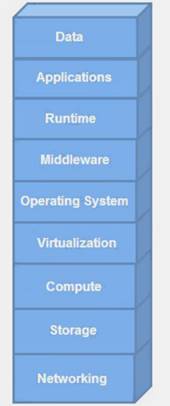
- A. software as a service
- B. platform as a service
- C. infrastructure as a service
- D. on-premises
Answer: D
NEW QUESTION 8
Match the Palo Alto Networks Wild Fire analysis verdict with its definition.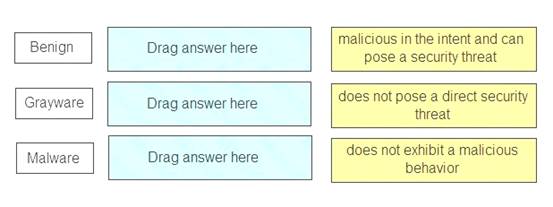
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Benign – does not exhibit a malicious behavior Grayware – does not pose a direct security threat
Malware – malicious in the intent and can pose a security threat References:
NEW QUESTION 9
Which two items operate at the network layer in the OSI network model? (Choose two.)
- A. IP address
- B. router
- C. switch
- D. MAC address
Answer: AB
NEW QUESTION 10
Which security principle describes the practice of giving users the minimum rights to access the resources necessary to do their jobs?
- A. known privilege
- B. least privilege
- C. user privilege
- D. lowest privilege
Answer: B
NEW QUESTION 11
To which type of organization does the PCI DSS apply?
- A. any organization that accepts, transmits, or stores any cardholder data
- B. organizations that only accept cardholder data regardless of size or number of transactions
- C. only organization larger than 100 employees that accept, transmit, or store any cardholder data
- D. organization that only transmit data regardless of size or number of transactions
Answer: A
NEW QUESTION 12
What method can be used to guarantee that a document originates from you and no one else?
- A. public key encryption, encrypting the document with the private key and making the public key available to others
- B. symmetric encryption, ecnrypting the document with the secret key and making a different secret key available to others
- C. symmetric encryption, ecnrypting the document with the secret key and making the same secret kay available to others
- D. public key encryption, encrypting the document with the private key and making the private key available to others
Answer: A
NEW QUESTION 13
Which security component should be used to prevent a malware attack delivered by USB drive?
- A. endpoint security
- B. password security
- C. physical security
- D. firewall security
Answer: C
NEW QUESTION 14
What does a hypervisor enable?
- A. high-speed searching of already aggregated security log files
- B. high-speed aggregation and viewing of security log files
- C. multiple physical machines to be configured into a high-performance cluster
- D. multiple guest operating systems to run on a single physical machine
Answer: D
NEW QUESTION 15
Match the common TCP/IP protocol with its corresponding port(s).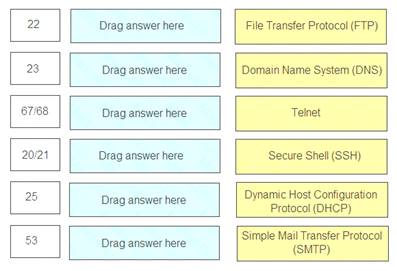
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
22 – Secure Shell (SSH) 23 – Telnet
67/68 – Dynamic Host Configuration Protocol (DHCP) 25 – Simple Mail Transfer Protocol (SMTP)
53 – Domain Name System (DNS)
NEW QUESTION 16
Company policy allows employees to access the internet. While searching for office supplies on the internet, a corporate user mistypes a URL, connects to a malicious website, and unknowingly downloads malware.
Which action should have been taken to prevent the malware download but still allow user access to the internet?
- A. deploy a firewall with content filtering capabilities on the corporate perimeter
- B. allow only encrypted HTTPS access to the internet
- C. configure digital certificates for all users to authenticate internet downloads
- D. permit web connections only to TCP port 443
Answer: A
NEW QUESTION 17
You discover malware has corrupted the BIOS on your laptop. Which type of malware is this?
- A. bootkit
- B. exploit
- C. rootkit
- D. vulnerability
Answer: A
NEW QUESTION 18
Which data security compliance standard is used to protect card holder data wherever it is processed, stored, or transmitted?
- A. Property Card Industry
- B. Payment Card Industry
- C. Personal Card Industry
- D. Payment Club Industry
Answer: B
NEW QUESTION 19
Which type of security device uses a single-pass, parallel processor hardware architecture to accelerate content inspection?
- A. unified threat management
- B. stateless firewalls
- C. next-generation firewall
- D. PoS-based firewall
Answer: C
NEW QUESTION 20
......
P.S. Easily pass PCCSA Exam with 50 Q&As Thedumpscentre.com Dumps & pdf Version, Welcome to Download the Newest Thedumpscentre.com PCCSA Dumps: https://www.thedumpscentre.com/PCCSA-dumps/ (50 New Questions)
