It is impossible to pass ISC2 SSCP exam without any help in the short term. Come to Passleader soon and find the most advanced, correct and guaranteed ISC2 SSCP practice questions. You will get a surprising result by our Most up-to-date System Security Certified Practitioner (SSCP) practice guides.
Online ISC2 SSCP free dumps demo Below:
NEW QUESTION 1
Access control is the collection of mechanisms that permits managers of a system to exercise a directing or restraining influence over the behavior, use, and content of a system. It does not permit management to:
- A. specify what users can do
- B. specify which resources they can access
- C. specify how to restrain hackers
- D. specify what operations they can perform on a system.
Answer: C
Explanation:
Access control is the collection of mechanisms that permits managers of a system to exercise a directing or restraining influence over the behavior, use, and content of a system. It permits management to specify what users can do, which resources they can access, and what operations they can perform on a system. Specifying HOW to restrain hackers is not directly linked to access control.
Source: DUPUIS, Clement, Access Control Systems and Methodology, Version 1, May 2002, CISSP Open Study Group Study Guide for Domain 1, Page 12.
NEW QUESTION 2
Which of the following BEST describes a function relying on a shared secret key that is used along with a hashing algorithm to verify the integrity of the communication content as well as the sender?
- A. Message Authentication Code - MAC
- B. PAM - Pluggable Authentication Module
- C. NAM - Negative Acknowledgement Message
- D. Digital Signature Certificate
Answer: A
Explanation:
The purpose of a message authentication code - MAC is to verify both the source and message integrity without the need for additional processes.
A MAC algorithm, sometimes called a keyed (cryptographic) hash function (however, cryptographic hash function is only one of the possible ways to generate MACs), accepts as input a secret key and an arbitrary-length message to be authenticated, and outputs a MAC (sometimes known as a tag). The MAC value protects both a message's data integrity as well as its authenticity, by allowing verifiers (who also possess the secret key) to detect any changes to the message content.
MACs differ from digital signatures as MAC values are both generated and verified using the same secret key. This implies that the sender and receiver of a message must agree on the same key before initiating communications, as is the case with symmetric encryption. For the same reason, MACs do not provide the property of non-repudiation offered by signatures specifically in the case of a network-wide shared secret key: any user who can verify a MAC is also capable of generating MACs for other messages.
In contrast, a digital signature is generated using the private key of a key pair, which is asymmetric encryption. Since this private key is only accessible to its holder, a digital signature proves that a document was signed by none other than that holder. Thus, digital signatures do offer non-repudiation.
The following answers are incorrect:
PAM - Pluggable Authentication Module: This isn't the right answer. There is no known message authentication function called a PAM. However, a pluggable authentication module (PAM) is a mechanism to integrate multiple low-level authentication schemes and commonly used within the Linux Operating System.
NAM - Negative Acknowledgement Message: This isn't the right answer. There is no known message authentication function called a NAM. The proper term for a negative acknowledgement is NAK, it is a signal used in digital communications to ensure that data is received with a minimum of errors.
Digital Signature Certificate: This isn't right. As it is explained and contrasted in the explanations provided above.
The following reference(s) was used to create this question:
The CCCure Computer Based Tutorial for Security+, you can subscribe at http://www.cccure.tv
and http://en.wikipedia.org/wiki/Message_authentication_code
NEW QUESTION 3
Which of the following can prevent hijacking of a web session?
- A. RSA
- B. SET
- C. SSL
- D. PPP
Answer: C
Explanation:
The Secure Socket Layer (SSL) protocol is used between a web server and client and provides entire session encryption, thus preventing from session hijacking. RSA is asymmetric encryption algorithm that can be used in setting up a SSL session. SET is the Secure Electronic Transaction protocol that was introduced by Visa and Mastercard to allow for more credit card transaction possibilities. PPP is a point-to-point protocol. Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 89).
NEW QUESTION 4
A business continuity plan should list and prioritize the services that need to be brought back after a disaster strikes. Which of the following services is more likely to be of primary concern in the context of what your Disaster Recovery Plan would include?
- A. Marketing/Public relations
- B. Data/Telecomm/IS facilities
- C. IS Operations
- D. Facilities security
Answer: B
Explanation:
The main concern when recovering after a disaster is data, telecomm and IS facilities. Other services, in descending priority order are: IS operations, IS support services, market structure, marketing/public relations, customer service & systems support, market regulation/surveillance, listing, application development, accounting services, facilities, human resources, facilities security, legal and Office of the Secretary, national sales.
Source: BARNES, James C. & ROTHSTEIN, Philip J., A Guide to Business Continuity Planning, John Wiley & Sons, 2001 (page 129).
NEW QUESTION 5
Which of the following cannot be undertaken in conjunction or while computer incident handling is ongoing?
- A. System development activity
- B. Help-desk function
- C. System Imaging
- D. Risk management process
Answer: A
Explanation:
If Incident Handling is underway an incident has potentially been identified. At that point all use of the system should stop because the system can no longer be trusted and any changes could contaminate the evidence. This would include all System Development Activity.
Every organization should have plans and procedures in place that deals with Incident Handling.
Employees should be instructed what steps are to be taken as soon as an incident occurs and how to report it. It is important that all parties involved are aware of these steps to protect not only any possible evidence but also to prevent any additional harm.
It is quite possible that the fraudster has planted malicous code that could cause destruction or even a Trojan Horse with a back door into the system. As soon as an incident has been identified the system can no longer be trusted and all use of the system should cease.
Shon Harris in her latest book mentions:
Although we commonly use the terms ??event?? and ??incident?? interchangeably, there are subtle differences between the two. An event is a negative occurrence that can be observed, verified, and documented, whereas an incident is a series of events that negatively affects the company and/ or impacts its security posture. This is why we call
reacting to these issues ??incident response?? (or ??incident handling??), because something is negatively affecting the company and causing a security breach.
Many types of incidents (virus, insider attack, terrorist attacks, and so on) exist, and sometimes it is just human error. Indeed, many incident response individuals have received a frantic call in the middle of the night because a system is acting ??weird.?? The reasons could be that a deployed patch broke something, someone misconfigured a device, or the administrator just learned a new scripting language and rolled out some code that caused mayhem and confusion.
When a company endures a computer crime, it should leave the environment and evidence unaltered and contact whomever has been delegated to investigate these types of situations. Someone who is unfamiliar with the proper process of collecting data and evidence from a crime scene could instead destroy that evidence, and thus all hope of prosecuting individuals, and achieving a conviction would be lost.
Companies should have procedures for many issues in computer security such as enforcement procedures, disaster recovery and continuity procedures, and backup procedures. It is also necessary to have a procedure for dealing with computer incidents because they have become an increasingly important issue of today??s information security departments. This is a direct result of attacks against networks and information systems increasing annually. Even though we don??t have specific numbers due to a lack of universal reporting and reporting in general, it is clear that the volume of attacks is increasing.
Just think about all the spam, phishing scams, malware, distributed denial-of-service, and other attacks you see on your own network and hear about in the news. Unfortunately, many companies are at a loss as to who to call or what to do right after they have been the victim of a cybercrime. Therefore, all companies should have an incident response policy that indicates who has the authority to initiate an incident response, with supporting procedures set up before an incident takes place.
This policy should be managed by the legal department and security department. They need to work together to make sure the technical security issues are covered and the legal issues that surround criminal activities are properly dealt with. The incident response policy should be clear and concise. For example, it should indicate if systems can be taken offline to try to save evidence or if systems have to continue functioning at the risk of destroying evidence. Each system and functionality should have a priority assigned to it. For instance, if the file server is infected, it should be removed from the network, but not shut down. However, if the mail server is infected, it should not be removed from the network or shut down because of the priority the company attributes to the mail server over the file server.
Tradeoffs and decisions will have to be made, but it is better to think through these issues before the situation occurs, because better logic is usually possible before a crisis, when there??s less emotion and chaos.
The Australian Computer Emergency Response Team??s General Guidelines for Computer Forensics:
Keep the handling and corruption of original data to a minimum. Document all actions and explain changes.
Follow the Five Rules for Evidence (Admissible, Authentic, Complete, Accurate, Convincing).
• Bring in more experienced help when handling and/ or analyzing the evidence is beyond your knowledge, skills, or abilities.
Adhere to your organization??s security policy and obtain written permission to conduct a forensics investigation.
Capture as accurate an image of the system( s) as possible while working quickly. Be ready to testify in a court of law.
Make certain your actions are repeatable.
Prioritize your actions, beginning with volatile and proceeding to persistent evidence. Do not run any programs on the system( s) that are potential evidence.
Act ethically and in good faith while conducting a forensics investigation, and do not attempt to do any harm.
The following answers are incorrect:
help-desk function. Is incorrect because during an incident, employees need to be able to communicate with a central source. It is most likely that would be the help-desk. Also the help-desk would need to be able to communicate with the employees to keep them informed.
system imaging. Is incorrect because once an incident has occured you should perform a capture of evidence starting with the most volatile data and imaging would be doen using bit for bit copy of storage medias to protect the evidence.
risk management process. Is incorrect because incident handling is part of risk management, and should continue.
Reference(s) used for this question:
Harris, Shon (2012-10-25). CISSP All-in-One Exam Guide, 6th Edition (Kindle Locations
21468-21476). McGraw-Hill. Kindle Edition. and
Harris, Shon (2012-10-25). CISSP All-in-One Exam Guide, 6th Edition (Kindle Locations 21096-21121). McGraw-Hill. Kindle Edition.
and
NIST Computer Security incident handling http://csrc.nist.gov/publications/nistpubs/800- 12/800-12-html/chapter12.html
NEW QUESTION 6
Which of the following keys has the SHORTEST lifespan?
- A. Secret key
- B. Public key
- C. Session key
- D. Private key
Answer: C
Explanation:
As session key is a symmetric key that is used to encrypt messages between two users. A session key is only good for one communication session between users.
For example , If Tanya has a symmetric key that she uses to encrypt messages between Lance and herself all the time , then this symmetric key would not be regenerated or changed. They would use the same key every time they communicated using encryption. However , using the same key repeatedly increases the chances of the key being captured and the secure communication being compromised. If , on the other hand , a new symmetric key were generated each time Lance and Tanya wanted to communicate , it would be used only during their dialog and then destroyed. if they wanted to communicate
and hour later , a new session key would be created and shared. The other answers are not correct because :
Public Key can be known to anyone.
Private Key must be known and used only by the owner.
Secret Keys are also called as Symmetric Keys, because this type of encryption relies on each user to keep the key a secret and properly protected.
REFERENCES:
SHON HARRIS , ALL IN ONE THIRD EDITION : Chapter 8 : Cryptography , Page : 619- 620
NEW QUESTION 7
The Computer Security Policy Model the Orange Book is based on is which of the following?
- A. Bell-LaPadula
- B. Data Encryption Standard
- C. Kerberos
- D. Tempest
Answer: A
Explanation:
The Computer Security Policy Model Orange Book is based is the Bell- LaPadula Model. Orange Book Glossary.
The Data Encryption Standard (DES) is a cryptographic algorithm. National Information Security Glossary.
TEMPEST is related to limiting the electromagnetic emanations from electronic equipment. Reference: U.S. Department of Defense, Trusted Computer System Evaluation Criteria (Orange Book), DOD 5200.28-STD. December 1985 (also available here).
NEW QUESTION 8
What does the directive of the European Union on Electronic Signatures deal with?
- A. Encryption of classified data
- B. Encryption of secret data
- C. Non repudiation
- D. Authentication of web servers
Answer: C
Explanation:
Reference: FORD, Warwick & BAUM, Michael S., Secure Electronic Commerce: Building the Infrastructure for Digital Signatures and Encryption (2nd Edition), 2000, Prentice Hall PTR, Page 589; Directive 1999/93/EC of 13 December 1999 on a Community framework for electronic signatures.
NEW QUESTION 9
Which of the following offers security to wireless communications?
- A. S-WAP
- B. WTLS
- C. WSP
- D. WDP
Answer: B
Explanation:
Wireless Transport Layer Security (WTLS) is a communication protocol that allows wireless devices to send and receive encrypted information over the Internet. S- WAP is not defined. WSP (Wireless Session Protocol) and WDP (Wireless Datagram Protocol) are part of Wireless Access Protocol (WAP).
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 4: Cryptography (page 173).
NEW QUESTION 10
What would be considered the biggest drawback of Host-based Intrusion Detection systems (HIDS)?
- A. It can be very invasive to the host operating system
- B. Monitors all processes and activities on the host system only
- C. Virtually eliminates limits associated with encryption
- D. They have an increased level of visibility and control compared to NIDS
Answer: A
Explanation:
The biggest drawback of HIDS, and the reason many organizations resist its use, is that it can be very invasive to the host operating system. HIDS must have the capability to monitor all processes and activities on the host system and this can sometimes interfere with normal system processing.
HIDS versus NIDS
A host-based IDS (HIDS) can be installed on individual workstations and/ or servers to watch for inappropriate or anomalous activity. HIDSs are usually used to make sure users do not delete system files, reconfigure important settings, or put the system at risk in any other way.
So, whereas the NIDS understands and monitors the network traffic, a HIDS??s universe is
limited to the computer itself. A HIDS does not understand or review network traffic, and a NIDS does not ??look in?? and monitor a system??s activity. Each has its own job and stays out of the other??s way.
The ISC2 official study book defines an IDS as:
An intrusion detection system (IDS) is a technology that alerts organizations to adverse or unwanted activity. An IDS can be implemented as part of a network device, such as a router, switch, or firewall, or it can be a dedicated IDS device monitoring traffic as it traverses the network. When used in this way, it is referred to as a network IDS, or NIDS. IDS can also be used on individual host systems to monitor and report on file, disk, and process activity on that host. When used in this way it is referred to as a host-based IDS, or HIDS.
An IDS is informative by nature and provides real-time information when suspicious activities are identified. It is primarily a detective device and, acting in this traditional role, is not used to directly prevent the suspected attack.
What about IPS?
In contrast, an intrusion prevention system (IPS), is a technology that monitors activity like an IDS but will automatically take proactive preventative action if it detects unacceptable activity. An IPS permits a predetermined set of functions and actions to occur on a network or system; anything that is not permitted is considered unwanted activity and blocked. IPS is engineered specifically to respond in real time to an event at the system or network layer. By proactively enforcing policy, IPS can thwart not only attackers, but also authorized users attempting to perform an action that is not within policy. Fundamentally, IPS is considered an access control and policy enforcement technology, whereas IDS is considered network monitoring and audit technology.
The following answers were incorrect:
All of the other answer were advantages and not drawback of using HIDS
TIP FOR THE EXAM:
Be familiar with the differences that exists between an HIDS, NIDS, and IPS. Know that IDS's are mostly detective but IPS are preventive. IPS's are considered an access control and policy enforcement technology, whereas IDS's are considered network monitoring and audit technology.
Reference(s) used for this question:
Harris, Shon (2012-10-25). CISSP All-in-One Exam Guide, 6th Edition (Kindle Locations
5817-5822). McGraw-Hill. Kindle Edition. and
Schneiter, Andrew (2013-04-15). Official (ISC)2 Guide to the CISSP CBK, Third Edition : Access Control ((ISC)2 Press), Domain1, Page 180-188 or on the kindle version look for Kindle Locations 3199-3203. Auerbach Publications.
NEW QUESTION 11
Which of the following is NOT a common backup method?
- A. Full backup method
- B. Daily backup method
- C. Incremental backup method
- D. Differential backup method
Answer: B
Explanation:
A daily backup is not a backup method, but defines periodicity at which backups are made. There can be daily full, incremental or differential backups.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 69).
NEW QUESTION 12
Which of the following are required for Life-Cycle Assurance?
- A. System Architecture and Design specification.
- B. Security Testing and Covert Channel Analysis.
- C. Security Testing and Trusted distribution.
- D. Configuration Management and Trusted Facility Management.
Answer: C
Explanation:
Security testing and trusted distribution are required for Life-Cycle Assurance.
The following answers are incorrect:
System Architecture and Design specification. Is incorrect because System Architecture is not requried for Life-Cycle Assurance.
Security Testing and Covert Channel Analysis. Is incorrect because Covert Channel Analysis is not requried for Life-Cycle Assurance.
Configuration Management and Trusted Facility Management. Is incorrect because Trusted Facility Management. is not requried for Life-Cycle Assurance.
NEW QUESTION 13
This baseline sets certain thresholds for specific errors or mistakes allowed and the amount of these occurrences that can take place before it is considered suspicious?
- A. Checkpoint level
- B. Ceiling level
- C. Clipping level
- D. Threshold level
Answer: C
Explanation:
Organizations usually forgive a particular type, number, or pattern of violations, thus permitting a predetermined number of user errors before gathering this data for analysis. An organization attempting to track all violations, without sophisticated statistical computing ability, would be unable to manage the sheer quantity of such data. To make a violation listing effective, a clipping level must be established.
The clipping level establishes a baseline for violation activities that may be normal user errors. Only after this baseline is exceeded is a violation record produced. This solution is particularly effective for small- to medium-sized installations. Organizations with large-scale computing facilities often track all violations and use statistical routines to cull out the minor infractions (e.g., forgetting a password or mistyping it several times).
If the number of violations being tracked becomes unmanageable, the first step in correcting the problems should be to analyze why the condition has occurred. Do users understand how they are to interact with the computer resource? Are the rules too difficult to follow? Violation tracking and analysis can be valuable tools in assisting an organization to develop thorough but useable controls. Once these are in place and records are produced that accurately reflect serious violations, tracking and analysis become the first line of defense. With this procedure, intrusions are discovered before major damage occurs and sometimes early enough to catch the perpetrator. In addition, business protection and preservation are strengthened.
The following answers are incorrect:
All of the other choices presented were simply detractors. The following reference(s) were used for this question:
Handbook of Information Security Management
NEW QUESTION 14
Which of the following is an IP address that is private (i.e. reserved for internal networks, and not a valid address to use on the Internet)?
- A. 172.12.42.5
- B. 172.140.42.5
- C. 172.31.42.5
- D. 172.15.42.5
Answer: C
Explanation:
This is a valid Class B reserved address. For Class B networks, the reserved addresses are 172.16.0.0 - 172.31.255.255.
The private IP address ranges are defined within RFC 1918: RFC 1918 private ip address range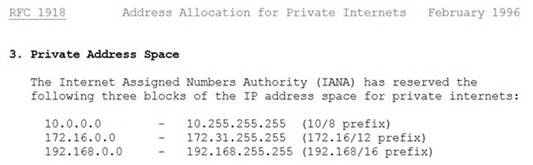
C:\Users\MCS\Desktop\1.jpg
The following answers are incorrect:
172.12.42.5 Is incorrect because it is not a Class B reserved address. 172.140.42.5 Is incorrect because it is not a Class B reserved address. 172.15.42.5 Is incorrect because it is not a Class B reserved address.
NEW QUESTION 15
Kerberos depends upon what encryption method?
- A. Public Key cryptography.
- B. Secret Key cryptography.
- C. El Gamal cryptography.
- D. Blowfish cryptography.
Answer: B
Explanation:
Kerberos depends on Secret Keys or Symmetric Key cryptography.
Kerberos a third party authentication protocol. It was designed and developed in the mid 1980's by MIT. It is considered open source but is copyrighted and owned by MIT. It relies on the user's secret keys. The password is used to encrypt and decrypt the keys.
This question asked specifically about encryption methods. Encryption methods can be SYMMETRIC (or secret key) in which encryption and decryption keys are the same, or ASYMMETRIC (aka 'Public Key') in which encryption and decryption keys differ.
'Public Key' methods must be asymmetric, to the extent that the decryption key CANNOT be easily derived from the encryption key. Symmetric keys, however, usually encrypt more efficiently, so they lend themselves to encrypting large amounts of data. Asymmetric encryption is often limited to ONLY encrypting a symmetric key and other information that is needed in order to decrypt a data stream, and the remainder of the encrypted data uses the symmetric key method for performance reasons. This does not in any way diminish the security nor the ability to use a public key to encrypt the data, since the symmetric key method is likely to be even MORE secure than the asymmetric method.
For symmetric key ciphers, there are basically two types: BLOCK CIPHERS, in which a fixed length block is encrypted, and STREAM CIPHERS, in which the data is encrypted one 'data unit' (typically 1 byte) at a time, in the same order it was received in.
The following answers are incorrect:
Public Key cryptography. Is incorrect because Kerberos depends on Secret Keys or Symmetric Key cryptography and not Public Key or Asymmetric Key cryptography.
El Gamal cryptography. Is incorrect because El Gamal is an Asymmetric Key encryption algorithm.
Blowfish cryptography. Is incorrect because Blowfish is a Symmetric Key encryption
algorithm. References:
OIG CBK Access Control (pages 181 - 184) AIOv3 Access Control (pages 151 - 155)
Wikipedia http://en.wikipedia.org/wiki/Blowfish_%28cipher%29 ; http://en.wikipedia.org/wiki/El_Gamal http://www.mrp3.com/encrypt.html
NEW QUESTION 16
Which of the following is addressed by Kerberos?
- A. Confidentiality and Integrity
- B. Authentication and Availability
- C. Validation and Integrity
- D. Auditability and Integrity
Answer: A
Explanation:
Kerberos addresses the confidentiality and integrity of information. It also addresses primarily authentication but does not directly address availability.
Reference(s) used for this question:
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 42.
and https://www.ietf.org/rfc/rfc4120.txt and
http://learn-networking.com/network-security/how-kerberos-authentication-works
NEW QUESTION 17
Which of the following OSI layers provides routing and related services?
- A. Network Layer
- B. Presentation Layer
- C. Session Layer
- D. Physical Layer
Answer: A
Explanation:
The Network Layer performs network routing functions. The following answers are incorrect:
Presentation Layer. Is incorrect because the Presentation Layer transforms the data to provide a standard interface for the Application layer.
Session Layer. Is incorrect because the Session Layer controls the dialogues/connections
(sessions) between computers.
Physical Layer. is incorrect because the Physical Layer defines all the electrical and physical specifications for devices.
NEW QUESTION 18
What can be defined as an event that could cause harm to the information systems?
- A. A risk
- B. A threat
- C. A vulnerability
- D. A weakness
Answer: B
Explanation:
A threat is an event or activity that has the potential to cause harm to the information systems. A risk is the probability that a threat will materialize. A vulnerability, or weakness, is a lack of a safeguard, which may be exploited by a threat, causing harm to the information systems.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 1: Access Control Systems (page 32).
NEW QUESTION 19
Which of the following is NOT a common integrity goal?
- A. Prevent unauthorized users from making modifications.
- B. Maintain internal and external consistency.
- C. Prevent authorized users from making improper modifications.
- D. Prevent paths that could lead to inappropriate disclosure.
Answer: D
Explanation:
Inappropriate disclosure is a confidentiality, not an integrity goal.
All of the other choices above are integrity goals addressed by the Clark-Wilson integrity model.
The Clark-Wilson model is an integrity model that addresses all three integrity goals:
1. prevent unauthorized users from making modifications,
2. prevent authorized users from making improper modifications, and
3. maintain internal and external consistency through auditing. NOTE: Biba address only the first goal of integrity above
Reference(s) used for this question:
Harris, Shon (2012-10-18). CISSP All-in-One Exam Guide, 6th Edition (p. 1384). McGraw- Hill. Kindle Edition.
NEW QUESTION 20
What does the (star) property mean in the Bell-LaPadula model?
- A. No write up
- B. No read up
- C. No write down
- D. No read down
Answer: C
Explanation:
The (star) property of the Bell-LaPadula access control model states that writing of information by a subject at a higher level of sensitivity to an object at a lower level of sensitivity is not permitted (no write down).
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 5: Security Architectures and Models (page 202).
Also check out: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw- Hill/Osborne, 2002, Chapter 5: Security Models and Architecture (page 242, 243).
NEW QUESTION 21
......
Thanks for reading the newest SSCP exam dumps! We recommend you to try the PREMIUM Certshared SSCP dumps in VCE and PDF here: https://www.certshared.com/exam/SSCP/ (1074 Q&As Dumps)
