We provide real SSCP exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass ISC2 SSCP Exam quickly & easily. The SSCP PDF type is available for reading and printing. You can print more and practice many times. With the help of our ISC2 SSCP dumps pdf and vce product and material, you can easily pass the SSCP exam.
Free SSCP Demo Online For ISC2 Certifitcation:
NEW QUESTION 1
Which of the following is an example of a connectionless communication protocol?
- A. UDP
- B. X.25
- C. Packet switching
- D. TCP
Answer: A
Explanation:
UDP is an example of connectionless communication protocol, wherein no connection needs to be established before data can be exchanged.
In telecommunications, connectionless describes communication between two network end points in which a message can be sent from one end point to another without prior arrangement. The device at one end of the communication transmits data addressed to the other, without first ensuring that the recipient is available and ready to receive the data. Some protocols allow for error correction by requested retransmission. Internet Protocol (IP) and User Datagram Protocol (UDP) are connectionless protocols.
Connectionless protocols are also described as stateless because the endpoints have no protocol-defined way to remember where they are in a "conversation" of message exchanges.
List of connectionless protocols
Hypertext Transfer Protocol IP
UDP ICMP IPX TIPC NetBEUI
References:
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 86).
and https://secure.wikimedia.org/wikipedia/en/wiki/Connectionless_protocol
NEW QUESTION 2
A 'Pseudo flaw' is which of the following?
- A. An apparent loophole deliberately implanted in an operating system program as a trap for intruders.
- B. An omission when generating Psuedo-code.
- C. Used for testing for bounds violations in application programming.
- D. A normally generated page fault causing the system to halt.
Answer: A
Explanation:
A Pseudo flaw is something that looks like it is vulnerable to attack, but really acts as an alarm or triggers automatic actions when an intruder attempts to exploit the flaw.
The following answers are incorrect:
An omission when generating Psuedo-code. Is incorrect because it is a distractor. Used for testing for bounds violations in application programming. Is incorrect, this is a testing methodology.
A normally generated page fault causing the system to halt. This is incorrect because it is distractor.
NEW QUESTION 3
Which OSI/ISO layer is the Media Access Control (MAC) sublayer part of?
- A. Transport layer
- B. Network layer
- C. Data link layer
- D. Physical layer
Answer: C
Explanation:
The data link layer contains the Logical Link Control sublayer and the Media Access Control (MAC) sublayer.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 83).
NEW QUESTION 4
The RSA Algorithm uses which mathematical concept as the basis of its encryption?
- A. Geometry
- B. 16-round ciphers
- C. PI (3.14159...)
- D. Two large prime numbers
Answer: D
Explanation:
Source: TIPTON, et. al, Official (ISC)2 Guide to the CISSP CBK, 2007 edition, page 254.
And from the RSA web site, http://www.rsa.com/rsalabs/node.asp?id=2214 :
The RSA cryptosystem is a public-key cryptosystem that offers both encryption and digital signatures (authentication). Ronald Rivest, Adi Shamir, and Leonard Adleman developed the RSA system in 1977 [RSA78]; RSA stands for the first letter in each of its inventors' last names.
The RSA algorithm works as follows: take two large primes, p and q, and compute their product n = pq; n is called the modulus. Choose a number, e, less than n and relatively prime to (p-1)(q-1), which means e and (p-1)(q-1) have no common factors except 1. Find another number d such that (ed - 1) is divisible by (p-1)(q-1). The values e and d are called the public and private exponents, respectively. The public key is the pair (n, e); the private key is (n, d). The factors p and q may be destroyed or kept with the private key.
It is currently difficult to obtain the private key d from the public key (n, e). However if one could factor n into p and q, then one could obtain the private key d. Thus the security of the RSA system is based on the assumption that factoring is difficult. The discovery of an easy method of factoring would "break" RSA (see Question 3.1.3 and Question 2.3.3).
Here is how the RSA system can be used for encryption and digital signatures (in practice, the actual use is slightly different; see Questions 3.1.7 and 3.1.8):
Encryption
Suppose Alice wants to send a message m to Bob. Alice creates the ciphertext c by exponentiating: c = me mod n, where e and n are Bob's public key. She sends c to Bob. To decrypt, Bob also exponentiates: m = cd mod n; the relationship between e and d ensures
that Bob correctly recovers m. Since only Bob knows d, only Bob can decrypt this message.
Digital Signature
Suppose Alice wants to send a message m to Bob in such a way that Bob is assured the message is both authentic, has not been tampered with, and from Alice. Alice creates a digital signature s by exponentiating: s = md mod n, where d and n are Alice's private key. She sends m and s to Bob. To verify the signature, Bob exponentiates and checks that the message m is recovered: m = se mod n, where e and n are Alice's public key.
Thus encryption and authentication take place without any sharing of private keys: each person uses only another's public key or their own private key. Anyone can send an encrypted message or verify a signed message, but only someone in possession of the correct private key can decrypt or sign a message.
NEW QUESTION 5
Which of the following is more suitable for a hardware implementation?
- A. Stream ciphers
- B. Block ciphers
- C. Cipher block chaining
- D. Electronic code book
Answer: A
Explanation:
A stream cipher treats the message as a stream of bits or bytes and performs mathematical functions on them individually. The key is a random value input into the stream cipher, which it uses to ensure the randomness of the keystream data. They are more suitable for hardware implementations, because they encrypt and decrypt one bit at a
time. They are intensive because each bit must be manipulated, which works better at the silicon level. Block ciphers operate a the block level, dividing the message into blocks of bits. Cipher Block chaining (CBC) and Electronic Code Book (ECB) are operation modes of DES, a block encryption algorithm.
Source: WALLHOFF, John, CBK#5 Cryptography (CISSP Study Guide), April 2002 (page 2).
NEW QUESTION 6
Network cabling comes in three flavors, they are:
- A. twisted pair, coaxial, and fiber optic.
- B. tagged pair, coaxial, and fiber optic.
- C. trusted pair, coaxial, and fiber optic.
- D. twisted pair, control, and fiber optic.
Answer: A
Explanation:
Network cabling comes in three flavors: twisted pair, coaxial, and fiber optic. Twisted pair
Twisted pair cabling is a form of wiring in which two wires (the forward and return conductors of a single circuit) are twisted together for the purposes of canceling out electromagnetic interference (EMI) from external sources. This type of cable is used for home and corporate Ethernet networks. Twisted pair cables consist of two insulated copper wires. There are three types of twisted pair cables: Shielded, Unshielded and Foil
Fiber Optic cable
An optical fiber cable consists of a center glass core surrounded by several layers of protective material. The outer insulating jacket is made of Teflon or PVC to prevent interference. It is expensive but has higher bandwidth and can transmit data over longer distances.
Coaxial cable
Coaxial lines confine the electromagnetic wave to area inside the cable, between the center conductor and the shield. The transmission of energy in the line occurs totally through the dielectric inside the cable between the conductors. Coaxial lines can therefore be bent and twisted (subject to limits) without negative effects, and they can be strapped to conductive supports without inducing unwanted currents in them and though.
The most common use for coaxial cables is for television and other signals with bandwidth of multiple megahertz. Although in most homes coaxial cables have been installed for transmission of TV signals, new technologies (such as the ITU-T G.hn standard) open the possibility of using home coaxial cable for high-speed home networking applications (Ethernet over coax).
See the following page for more details: http://fcit.usf.edu/network/chap4/chap4.htm Reference used for this question:
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 101.
and
Wikipedia at http://en.wikipedia.org/wiki/Networking_cables
NEW QUESTION 7
What IDS approach relies on a database of known attacks?
- A. Signature-based intrusion detection
- B. Statistical anomaly-based intrusion detection
- C. Behavior-based intrusion detection
- D. Network-based intrusion detection
Answer: A
Explanation:
A weakness of the signature-based (or knowledge-based) intrusion detection approach is that only attack signatures that are stored in a database are detected.
Network-based intrusion detection can either be signature-based or statistical anomaly- based (also called behavior-based).
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 2: Access control systems (page 49).
NEW QUESTION 8
What is the main objective of proper separation of duties?
- A. To prevent employees from disclosing sensitive information.
- B. To ensure access controls are in place.
- C. To ensure that no single individual can compromise a system.
- D. To ensure that audit trails are not tampered with.
Answer: C
Explanation:
The primary objective of proper separation of duties is to ensure that one person acting alone cannot compromise the company's security in any way. A proper separation of duties does not prevent employees from disclosing information, nor does it ensure that access controls are in place or that audit trails are not tampered with. Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw- Hill/Osborne, 2002, Chapter 12: Operations Security (Page 808).
NEW QUESTION 9
The Information Technology Security Evaluation Criteria (ITSEC) was written to address which of the following that the Orange Book did not address?
- A. integrity and confidentiality.
- B. confidentiality and availability.
- C. integrity and availability.
- D. none of the above.
Answer: C
Explanation:
TCSEC focused on confidentiality while ITSEC added integrity and availability as security goals.
The following answers are incorrect:
integrity and confidentiality. Is incorrect because TCSEC addressed confidentiality. confidentiality and availability. Is incorrect because TCSEC addressed confidentiality. none of the above. Is incorrect because ITSEC added integrity and availability as security goals.
NEW QUESTION 10
Which of the following is less likely to be used today in creating a Virtual Private Network?
- A. L2TP
- B. PPTP
- C. IPSec
- D. L2F
Answer: D
Explanation:
L2F (Layer 2 Forwarding) provides no authentication or encryption. It is a
Protocol that supports the creation of secure virtual private dial-up networks over the Internet.
At one point L2F was merged with PPTP to produce L2TP to be used on networks and not only on dial up links.
IPSec is now considered the best VPN solution for IP environments.
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw- Hill/Osborne, 2002, Chapter 8: Cryptography (page 507).
NEW QUESTION 11
Because all the secret keys are held and authentication is performed on the Kerberos TGS and the authentication servers, these servers are vulnerable to:
- A. neither physical attacks nor attacks from malicious code.
- B. physical attacks only
- C. both physical attacks and attacks from malicious code.
- D. physical attacks but not attacks from malicious code.
Answer: C
Explanation:
Since all the secret keys are held and authentication is performed on the Kerberos TGS and the authentication servers, these servers are vulnerable to both physical attacks and attacks from malicious code.
Because a client's password is used in the initiation of the Kerberos request for the service protocol, password guessing can be used to impersonate a client.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 42.
NEW QUESTION 12
Which of the following is true related to network sniffing?
- A. Sniffers allow an attacker to monitor data passing across a network.
- B. Sniffers alter the source address of a computer to disguise and exploit weak authentication methods.
- C. Sniffers take over network connections.
- D. Sniffers send IP fragments to a system that overlap with each other.
Answer: A
Explanation:
The following answers are incorrect: Sniffers alter the source address of a computer to disguise and exploit weak authentication methods. IP Spoofing is a network-
based attack, which involves altering the source address of a computer to disguise the attacker and exploit weak authentication methods.
Sniffers take over network connections. Session Hijacking tools allow an attacker to take over network connections, kicking off the legitimate user or sharing a login.
Sniffers send IP fragments to a system that overlap with each other. Malformed Packet attacks are a type of DoS attack that involves one or two packets that are formatted in an unexpected way. Many vendor product implementations do not take into account all variations of user entries or packet types. If software handles such errors poorly, the system may crash when it receives such packets. A classic example of this type of attack involves sending IP fragments to a system that overlap with each other (the fragment offset values are incorrectly set. Some unpatched Windows and Linux systems will crash when the encounter such packets.
The following reference(s) were/was used to create this question:
Source: TIPTON, Harold F. & KRAUSE, MICKI, Information Security Management Handbook, 4th Edition, Volume 2, Auerbach, NY, NY 2001, Chapter 22, Hacker Tools and Techniques by Ed Skoudis.
ISC2 OIG, 2007 p. 137-138, 419
NEW QUESTION 13
In the Open Systems Interconnect (OSI) Reference Model, at what level are TCP and UDP provided?
- A. Transport
- B. Network
- C. Presentation
- D. Application
Answer: A
Explanation:
The Answer Transport. The Layer 4 Transport layer supports the TCP and UDP protocols in the OSI Reference Model. This layer creates an end-to-end transportation between peer hosts. The transmission can be connectionless and unreliable such as UDP, or connection-oriented and ensure error-free delivery such as TCP.
The following answers are incorrect:
Network. The Network layer moves information between hosts that are not physically connected. It deals with routing of information. IP is a protocol that is used in Network Layer. TCP and UDP do not reside at the Layer 3 Network Layer in the OSI Reference Model.
Presentation. The Presentation Layer is concerned with the formatting of data into a standard presentation such as
ASCII. TCP and UDP do not reside at the Layer 6 Presentation Layer in the OSI Reference Model.
Application. The Application Layer is a service for applications and Operating Systems data transmission, for example HTTP, FTP and SMTP. TCP and UDP do not reside at the Layer 7 Application Layer in the OSI Reference Model.
The following reference(s) were/was used to create this question: ISC2 OIG, 2007 p. 411
Shon Harris AIO v.3 p. 424
NEW QUESTION 14
Smart cards are an example of which type of control?
- A. Detective control
- B. Administrative control
- C. Technical control
- D. Physical control
Answer: C
Explanation:
Logical or technical controls involve the restriction of access to systems and the protection of information. Smart cards and encryption are examples of these types of control.
Controls are put into place to reduce the risk an organization faces, and they come in three main flavors: administrative, technical, and physical. Administrative controls are commonly referred to as ??soft controls?? because they are more management-oriented. Examples of administrative controls are security documentation, risk management, personnel security, and training. Technical controls (also called logical controls) are software or hardware components, as in firewalls, IDS, encryption, identification and authentication mechanisms. And physical controls are items put into place to protect facility, personnel, and resources. Examples of physical controls are security guards, locks, fencing, and lighting.
Many types of technical controls enable a user to access a system and the resources within that system. A technical control may be a username and password combination, a Kerberos implementation, biometrics, public key infrastructure (PKI), RADIUS, TACACS +, or authentication using a smart card through a reader connected to a system. These technologies verify the user is who he says he is by using different types of authentication methods. Once a user is properly authenticated, he can be authorized and allowed access to network resources.
Reference(s) used for this question:
Harris, Shon (2012-10-25). CISSP All-in-One Exam Guide, 6th Edition (p. 245). McGraw- Hill. Kindle Edition.
and
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 2: Access control systems (page 32).
NEW QUESTION 15
When a biometric system is used, which error type deals with the possibility of GRANTING access to impostors who should be REJECTED?
- A. Type I error
- B. Type II error
- C. Type III error
- D. Crossover error
Answer: B
Explanation:
When the biometric system accepts impostors who should have been rejected , it is called a Type II error or False Acceptance Rate or False Accept Rate.
Biometrics verifies an individual??s identity by analyzing a unique personal attribute or behavior, which is one of the most effective and accurate methods of verifying identification.
Biometrics is a very sophisticated technology; thus, it is much more expensive and complex than the other types of identity verification processes. A biometric system can make authentication decisions based on an individual??s behavior, as in signature dynamics, but these can change over time and possibly be forged.
Biometric systems that base authentication decisions on physical attributes (iris, retina, fingerprint) provide more accuracy, because physical attributes typically don??t change much, absent some disfiguring injury, and are harder to impersonate.
When a biometric system rejects an authorized individual, it is called a Type I error (False Rejection Rate (FRR) or False Reject Rate (FRR)).
When the system accepts impostors who should be rejected, it is called a Type II error (False Acceptance Rate (FAR) or False Accept Rate (FAR)). Type II errors are the most dangerous and thus the most important to avoid.
The goal is to obtain low numbers for each type of error, but When comparing different biometric systems, many different variables are used, but one of the most important metrics is the crossover error rate (CER).
The accuracy of any biometric method is measured in terms of Failed Acceptance Rate (FAR) and Failed Rejection Rate (FRR). Both are expressed as percentages. The FAR is the rate at which attempts by unauthorized users are incorrectly accepted as valid. The FRR is just the opposite. It measures the rate at which authorized users are denied access.
The relationship between FRR (Type I) and FAR (Type II) is depicted in the graphic below . As one rate increases, the other decreases. The Cross-over Error Rate (CER) is sometimes considered a good indicator of the overall accuracy of a biometric system. This
is the point at which the FRR and the FAR have the same value. Solutions with a lower CER are typically more accurate.
See graphic below from Biometria showing this relationship. The Cross-over Error Rate (CER) is also called the Equal Error Rate (EER), the two are synonymous.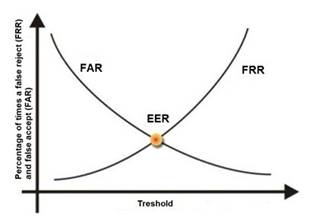
C:\Users\MCS\Desktop\1.jpg Cross Over Error Rate
The other answers are incorrect:
Type I error is also called as False Rejection Rate where a valid user is rejected by the system.
Type III error : there is no such error type in biometric system.
Crossover error rate stated in percentage , represents the point at which false rejection equals the false acceptance rate.
Reference(s) used for this question: http://www.biometria.sk/en/principles-of-biometrics.html
and
Shon Harris, CISSP All In One (AIO), 6th Edition , Chapter 3, Access Control, Page 188- 189
and
Tech Republic, Reduce Multi_Factor Authentication Cost
NEW QUESTION 16
A DMZ is located:
- A. right behind your first Internet facing firewall
- B. right in front of your first Internet facing firewall
- C. right behind your first network active firewall
- D. right behind your first network passive Internet http firewall
Answer: A
Explanation:
While the purpose of systems in the DMZ is to allow public access to certain internal network resources (EMAIL, DNS, Web), it is a good practice to restrict that access to the minimum necessary to provide those services through use of a firewall.
In computer security, a DMZ or Demilitarized Zone (sometimes referred to as a perimeter network) is a physical or logical subnetwork that contains and exposes an organization's external-facing services to a larger and untrusted network, usually the Internet. The purpose of a DMZ is to add an additional layer of security to an organization's local area network (LAN); an external attacker only has direct access to equipment in the DMZ, rather than any other part of the network. The name is derived from the term "demilitarized zone", an area between nation states in which military operation is not permitted.
The following are incorrect answers:
"Right in front of your first Internet facing firewall" While the purpose of systems in the DMZ is to allow public access to certain internal network resources (EMAIL, DNS, Web), it is a good practice to restrict that access to the minimum necessary to provide those services through use of a firewall.
"Right behind your first network active firewall" This is an almost-right-sounding answer meant to distract the unwary.
"Right behind your first network passive Internet http firewall" This is an almost-right- sounding answer meant to distract the unwary.
References: CBK, p. 434
and
AIO3, p. 483
and http://en.wikipedia.org/wiki/DMZ_%28computing%29
NEW QUESTION 17
In this type of attack, the intruder re-routes data traffic from a network device to a personal machine. This diversion allows an attacker to gain access to critical resources and user credentials, such as passwords, and to gain unauthorized access to critical systems of an organization. Pick the best choice below.
- A. Network Address Translation
- B. Network Address Hijacking
- C. Network Address Supernetting
- D. Network Address Sniffing
Answer: B
Explanation:
Network address hijacking allows an attacker to reroute data traffic from a network device to a personal computer.
Also referred to as session hijacking, network address hijacking enables an attacker to capture and analyze the data addressed to a target system. This allows an attacker to gain access to critical resources and user credentials, such as passwords, and to gain
unauthorized access to critical systems of an organization.
Session hijacking involves assuming control of an existing connection after the user has successfully created an authenticated session. Session hijacking is the act of unauthorized insertion of packets into a data stream. It is normally based on sequence number attacks, where sequence numbers are either guessed or intercepted.
The following are incorrect answers:
Network address translation (NAT) is a methodology of modifying network address information in Internet Protocol (IP) datagram packet headers while they are in transit across a traffic routing device for the purpose of remapping one IP address space into another. See RFC 1918 for more details.
Network Address Supernetting There is no such thing as Network Address Supernetting. However, a supernetwork, or supernet, is an Internet Protocol (IP) network that is formed from the combination of two or more networks (or subnets) with a common Classless Inter- Domain Routing (CIDR) prefix. The new routing prefix for the combined network aggregates the prefixes of the constituent networks.
Network Address Sniffing This is another bogus choice that sound good but does not even exist. However, sniffing is a common attack to capture cleartext password and information unencrypted over the network. Sniffier is accomplished using a sniffer also called a Protocol Analyzer. A network sniffers monitors data flowing over computer network links. It can be a self-contained software program or a hardware device with the appropriate software or firmware programming. Also sometimes called "network probes" or "snoops," sniffers examine network traffic, making a copy of the data but without redirecting or altering it.
The following reference(s) were used for this question:
Hernandez CISSP, Steven (2012-12-21). Official (ISC)2 Guide to the CISSP CBK, Third Edition ((ISC)2 Press ) (Kindle Locations 8641-8642). Auerbach Publications. Kindle Edition.
http://compnetworking.about.com/od/networksecurityprivacy/g/bldef_sniffer.htm http://wiki.answers.com/Q/What_is_network_address_hijacking
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 239.
NEW QUESTION 18
What is RAD?
- A. A development methodology
- B. A project management technique
- C. A measure of system complexity
- D. Risk-assessment diagramming
Answer: A
Explanation:
RAD stands for Rapid Application Development.
RAD is a methodology that enables organizations to develop strategically important systems faster while reducing development costs and maintaining quality.
RAD is a programming system that enables programmers to quickly build working programs.
In general, RAD systems provide a number of tools to help build graphical user interfaces that would normally take a large development effort.
Two of the most popular RAD systems for Windows are Visual Basic and Delphi. Historically, RAD systems have tended to emphasize reducing development time, sometimes at the expense of generating in-efficient executable code. Nowadays, though, many RAD systems produce extremely faster code that is optimized.
Conversely, many traditional programming environments now come with a number of visual tools to aid development. Therefore, the line between RAD systems and other development environments has become blurred.
Reference:
Information Systems Audit and Control Association, Certified Information Systems Auditor 2002 review manual, chapter 6: Business Application System Development, Acquisition, Implementation and Maintenance (page 307)
http://www.webopedia.com
NEW QUESTION 19
Brute force attacks against encryption keys have increased in potency because of increased computing power. Which of the following is often considered a good protection
against the brute force cryptography attack?
- A. The use of good key generators.
- B. The use of session keys.
- C. Nothing can defend you against a brute force crypto key attack.
- D. Algorithms that are immune to brute force key attacks.
Answer: B
Explanation:
If we assume a crytpo-system with a large key (and therefore a large key space) a brute force attack will likely take a good deal of time - anywhere from several hours to several years depending on a number of variables. If you use a session key for each message you encrypt, then the brute force attack provides the attacker with only the key for that one message. So, if you are encrypting 10 messages a day, each with a different session key, but it takes me a month to break each session key then I am fighting a loosing battle.
The other answers are not correct because:
"The use of good key generators" is not correct because a brute force key attack will eventually run through all possible combinations of key. Therefore, any key will eventually be broken in this manner given enough time.
"Nothing can defend you against a brute force crypto key attack" is incorrect, and not the best answer listed. While it is technically true that any key will eventually be broken by a brute force attack, the question remains "how long will it take?". In other words, if you encrypt something today but I can't read it for 10,000 years, will you still care? If the key is changed every session does it matter if it can be broken after the session has ended? Of the answers listed here, session keys are "often considered a good protection against the brute force cryptography attack" as the question asks.
"Algorithms that are immune to brute force key attacks" is incorrect because there currently are no such algorithms.
References:
Official ISC2 Guide page: 259
All in One Third Edition page: 623
NEW QUESTION 20
Which of the following protocols operates at the session layer (layer 5)?
- A. RPC
- B. IGMP
- C. LPD
- D. SPX
Answer: A
Explanation:
Remotre Procedure Call (RPC) is the only of the above choices to operate at the session layer (layer 5).
All of the other answers were wrong. LPD operates at layer 7
SPX operates at layer 4
IGMP operates at layer 3.
Reference:
WALLHOFF, John, CBK#2 Telecommunications and Network Security (CISSP Study Guide), April 2002 (page 1).
NEW QUESTION 21
......
P.S. Easily pass SSCP Exam with 1074 Q&As DumpSolutions.com Dumps & pdf Version, Welcome to Download the Newest DumpSolutions.com SSCP Dumps: https://www.dumpsolutions.com/SSCP-dumps/ (1074 New Questions)
