Actualtests offers free demo for SY0-601 exam. "CompTIA Security+ Exam", also known as SY0-601 exam, is a CompTIA Certification. This set of posts, Passing the CompTIA SY0-601 exam, will help you answer those questions. The SY0-601 Questions & Answers covers all the knowledge points of the real exam. 100% real CompTIA SY0-601 exams and revised by experts!
Free demo questions for CompTIA SY0-601 Exam Dumps Below:
NEW QUESTION 1
A company recently moved sensitive videos between on-premises. Company-owned websites. The company then learned the videos had been uploaded and shared to the internet. Which of the following would MOST likely allow the company to find the cause?
- A. Checksums
- B. Watermarks
- C. Oder of volatility
- D. A log analysis
- E. A right-to-audit clause
Answer: D
NEW QUESTION 2
A security analyst is reviewing a new website that will soon be made publicly available. The analyst sees the following in the URL:
http://dev-site.comptia.org/home/show.php?sessionID=77276554&loc=us
The analyst then sends an internal user a link to the new website for testing purposes, and when the user clicks the link, the analyst is able to browse the website with the following URL:
http://dev-site.comptia.org/home/show.php?sessionID=98988475&loc=us Which of the following application attacks is being tested?
- A. Pass-the-hash
- B. Session replay
- C. Object deference
- D. Cross-site request forgery
Answer: B
NEW QUESTION 3
A company wants to deploy PKI on its Internet-facing website. The applications that are currently deployed are: www.company.com (main website)
www.company.com (main website) contactus.company.com (for locating a nearby location)
contactus.company.com (for locating a nearby location)  quotes.company.com (for requesting a price quote)
quotes.company.com (for requesting a price quote)
The company wants to purchase one SSL certificate that will work for all the existing applications and any future applications that follow the same naming conventions, such as store.company.com. Which of the following certificate types would BEST meet the requirements?
- A. SAN
- B. Wildcard
- C. Extended validation
- D. Self-signed
Answer: B
NEW QUESTION 4
A company is implementing MFA for all applications that store sensitive data. The IT manager wants MFA to be non-disruptive and user friendly. Which of the following technologies should the IT manager use when implementing MFA?
- A. One-time passwords
- B. Email tokens
- C. Push notifications
- D. Hardware authentication
Answer: C
NEW QUESTION 5
A security analyst needs to be proactive in understand the types of attacks that could potentially target the company's execute. Which of the following intelligence sources should to security analyst review?
- A. Vulnerability feeds
- B. Trusted automated exchange of indicator information
- C. Structured threat information expression
- D. Industry information-sharing and collaboration groups
Answer: D
NEW QUESTION 6
An end user reports a computer has been acting slower than normal for a few weeks. During an investigation, an analyst determines the system is sending the user's email address and a ten-digit number to an IP address once a day. The only recent log entry regarding the user's computer is the following: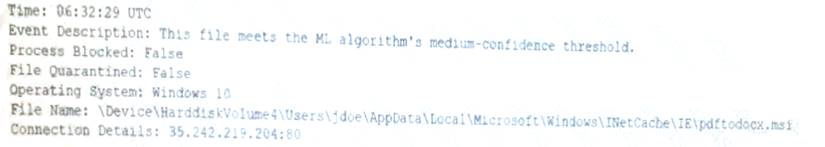
Which of the following is the MOST likely cause of the issue?
- A. The end user purchased and installed a PUP from a web browser
- B. A bot on the computer is brute forcing passwords against a website
- C. A hacker is attempting to exfiltrate sensitive data
- D. Ransomware is communicating with a command-and-control server.
Answer: A
NEW QUESTION 7
A security administrator checks the table of a network switch, which shows the following output: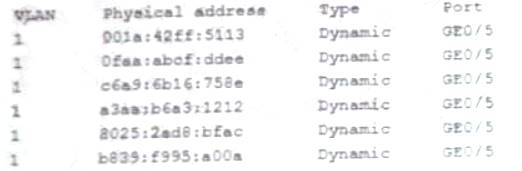
Which of the following is happening to this switch?
- A. MAC Flooding
- B. DNS poisoning
- C. MAC cloning
- D. ARP poisoning
Answer: A
NEW QUESTION 8
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.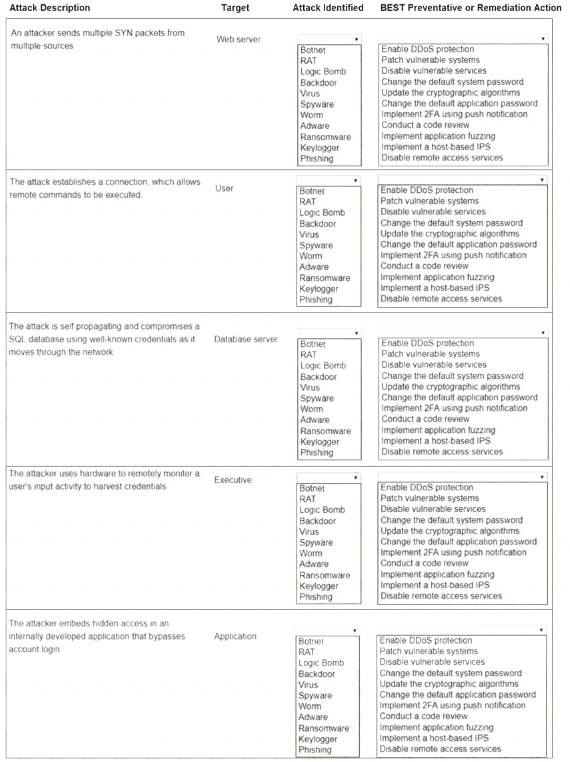
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 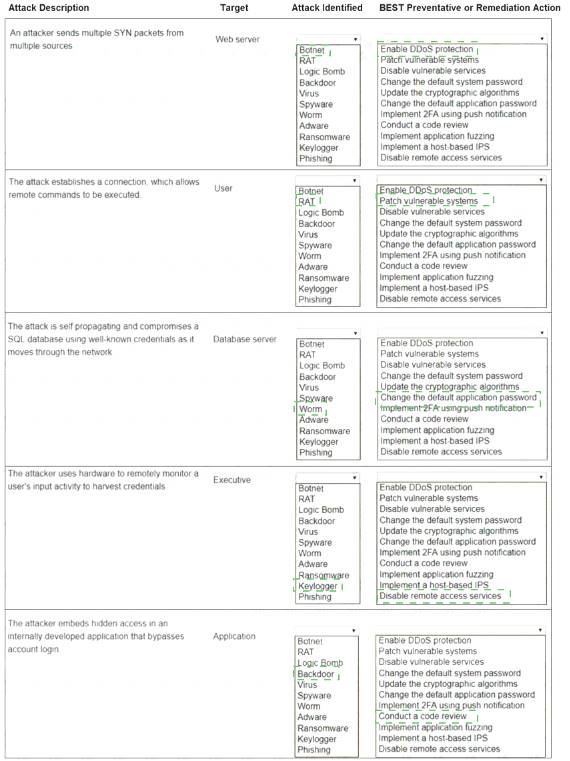
NEW QUESTION 9
An organization’s help desk is flooded with phone calls from users stating they can no longer access certain websites. The help desk escalates the issue to the security team, as these websites were accessible the previous day. The security analysts run the following command: ipconfig /flushdns, but the issue persists. Finally, an analyst changes the DNS server for an impacted machine, and the issue goes away. Which of the following attacks MOST likely occurred on the original DNS server?
- A. DNS cache poisoning
- B. Domain hijacking
- C. Distributed denial-of-service
- D. DNS tunneling
Answer: B
NEW QUESTION 10
Which of the following control sets should a well-written BCP include? (Select THREE)
- A. Preventive
- B. Detective
- C. Deterrent
- D. Corrective
- E. Compensating
- F. Physical
- G. Recovery
Answer: ADG
NEW QUESTION 11
An analyst visits an internet forum looking for information about a tool. The analyst finds a threat that appears to contain relevant information. One of the posts says the following:
Which of the following BEST describes the attack that was attempted against the forum readers?
- A. SOU attack
- B. DLL attack
- C. XSS attack
- D. API attack
Answer: C
NEW QUESTION 12
A host was infected with malware. During the incident response, Joe, a user, reported that he did not receive any emails with links, but he had been browsing the Internet all day. Which of the following would MOST likely show where the malware originated?
- A. The DNS logs
- B. The web server logs
- C. The SIP traffic logs
- D. The SNMP logs
Answer: A
NEW QUESTION 13
Which of the following relets to applications and systems that are used within an organization without consent or approval?
- A. Shadow IT
- B. OSINT
- C. Dark web
- D. Insider threats
Answer: A
NEW QUESTION 14
A security engineer is reviewing log files after a third discovered usernames and passwords for the organization’s accounts. The engineer sees there was a change in the IP address for a vendor website one earlier. This change lasted eight hours. Which of the following attacks was MOST likely used?
- A. Man-in- the middle
- B. Spear-phishing
- C. Evil twin
- D. DNS poising
Answer: D
NEW QUESTION 15
A security analyst discovers several .jpg photos from a cellular phone during a forensics investigation involving a compromised system. The analyst runs a forensics tool to gather file metadata. Which of the following would be part of the images if all the metadata is still intact?
- A. The GPS location
- B. When the file was deleted
- C. The total number of print jobs
- D. The number of copies made
Answer: A
NEW QUESTION 16
An organization has decided to host its web application and database in the cloud Which of the following BEST describes the security concerns for this decision?
- A. Access to the organization's servers could be exposed to other cloud-provider clients
- B. The cloud vendor is a new attack vector within the supply chain
- C. Outsourcing the code development adds risk to the cloud provider
- D. Vendor support will cease when the hosting platforms reach EOL.
Answer: B
NEW QUESTION 17
The CSIRT is reviewing the lessons learned from a recent incident. A worm was able to spread unhindered throughout the network and infect a large number of computers and servers. Which of the following recommendations would be BEST to mitigate the impacts of a similar incident in the future?
- A. Install a NIDS device at the boundary.
- B. Segment the network with firewalls.
- C. Update all antivirus signatures daily.
- D. Implement application blacklisting.
Answer: B
NEW QUESTION 18
A company uses wireless tor all laptops and keeps a very detailed record of its assets, along with a comprehensive list of devices that are authorized to be on the wireless network. The Chief Information Officer (CIO) is concerned about a script kiddie potentially using an unauthorized device to brute force the wireless PSK and obtain access to the internal network. Which of the following should the company implement to BEST prevent this from occurring?
- A. A BPDU guard
- B. WPA-EAP
- C. IP filtering
- D. A WIDS
Answer: B
NEW QUESTION 19
Which of the following would be the BEST method for creating a detailed diagram of wireless access points and hot-spots?
- A. Footprinting
- B. White-box testing
- C. A drone/UAV
- D. Pivoting
Answer: A
NEW QUESTION 20
Which of the following would MOST likely support the integrity of a voting machine?
- A. Asymmetric encryption
- B. Blockchain
- C. Transport Layer Security
- D. Perfect forward secrecy
Answer: D
NEW QUESTION 21
An analyst needs to identify the applications a user was running and the files that were open before the user’s computer was shut off by holding down the power button. Which of the following would MOST likely contain that information?
- A. NGFW
- B. Pagefile
- C. NetFlow
- D. RAM
Answer: C
NEW QUESTION 22
Joe, a user at a company, clicked an email link led to a website that infected his workstation. Joe, was connected to the network, and the virus spread to the network shares. The protective measures failed to stop this virus, and It has continues to evade detection. Which of the following should administrator implement to protect the environment from this malware?
- A. Install a definition-based antivirus.
- B. Implement an IDS/IPS
- C. Implement a heuristic behavior-detection solution.
- D. Implement CASB to protect the network shares.
Answer: C
NEW QUESTION 23
A network administrator has been asked to install an IDS to improve the security posture of an organization. Which of the following control types is an IDS?
- A. Corrective
- B. Physical
- C. Detective
- D. Administrative
Answer: C
NEW QUESTION 24
A financial organization has adopted a new secure, encrypted document-sharing application to help with its customer loan process. Some important PII needs to be shared across this new platform, but it is getting blocked by the DLP systems. Which of the following actions will BEST allow the PII to be shared with the secure application without compromising the organization’s security posture?
- A. Configure the DLP policies to allow all PII
- B. Configure the firewall to allow all ports that are used by this application
- C. Configure the antivirus software to allow the application
- D. Configure the DLP policies to whitelist this application with the specific PII
- E. Configure the application to encrypt the PII
Answer: D
NEW QUESTION 25
......
P.S. DumpSolutions.com now are offering 100% pass ensure SY0-601 dumps! All SY0-601 exam questions have been updated with correct answers: https://www.dumpsolutions.com/SY0-601-dumps/ (218 New Questions)
