Your success in Cisco 400-007 is our sole target and we develop all our 400-007 braindumps in a way that facilitates the attainment of this target. Not only is our 400-007 study material the best you can find, it is also the most detailed and the most updated. 400-007 Practice Exams for Cisco 400-007 are written to the highest standards of technical accuracy.
Cisco 400-007 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Refer to the exhibit. There are multiple trees in the Cisco FabricPath. All switches in the Layer 2 fabric share the same view of each tree.
Which two concepts describe how the multicast traffic is load-balanced across this topology? (Choose two )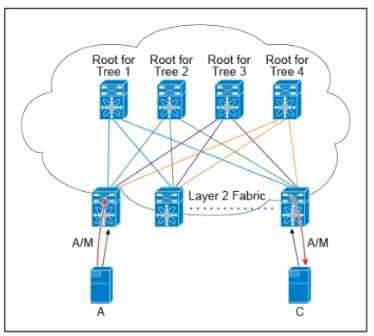
- A. A specific (S.G) traffic is not load-balanced
- B. All trees are utilized at the same level of the traffic rate
- C. Every leaf node assigns the specific (S.G) to the same tree.
- D. A specific (S.G) multicast traffic is load-balanced across all trees due to better link utilization efficiency.
- E. The multicast traffic is generally load-balanced across all trees
Answer: BD
NEW QUESTION 2
Which two possible drawbacks should you consider when introducing Network Functions Virtualization in a network design? (Choose two)
- A. Bandwidth utilization increases
- B. Traffic flows are suboptimal
- C. High-end routers are required to support NFV
- D. OpenFlow must be supported in the network
- E. An SDN orchestration layer is required to support NFV
Answer: CE
NEW QUESTION 3
An enterprise that runs numerous proprietary applications has major issues with its on-premises server estate hardware, to the point where business-critical functions are compromised. The enterprise accelerates plans to migrate services to the cloud.
Which cloud service should be used if the enterprise wants to avoid hardware issues yet have control of its applications and operating system?
- A. SaaS
- B. PaaS
- C. laaS
- D. hybrid cloud
Answer: C
NEW QUESTION 4
You are a network designer and you must ensure that the network you design is secure.
How do you plan to prevent infected devices on your network from sourcing random DDoS attacks using forged source address?
- A. ACL based forwarding
- B. unicast RPF loose mode
- C. unicast RPF strict mode
- D. ACL filtering by destination
Answer: C
NEW QUESTION 5
A network architect must redesign a service provider edge, where multiservice and multitenant PEs are currently present.
Which design feature should be minimized in the new design to achieve reliability?
- A. bridging
- B. fate sharing
- C. redundancy
- D. unicast overlay routing
Answer: B
NEW QUESTION 6
Which two foundational aspects of loT are still evolving and being worked on by the industry at large? (Choose two)
- A. WiFi protocols
- B. Regulatory domains
- C. Low energy Bluetooth sensors
- D. loT consortia
- E. Standards
Answer: AC
NEW QUESTION 7
Which two features control multicast traffic in a VLAN environment? (Choose two)
- A. IGMP snooping
- B. MLD snooping
- C. RGMP
- D. PIM snooping
- E. pruning
Answer: AB
NEW QUESTION 8
Which statement about hot-potato routing architecture design is true?
- A. Hot-potato routing is the preferred architecture when connecting to content providers
- B. Hop-potato keeps traffic under the control of the network administrator for longer
- C. OSPF uses hot-potato routing if all ASBRs use the same value for the external metric
- D. Hot-potato routing is prone to misconfiguration as well as poor coordination between twonetworks
Answer: A
NEW QUESTION 9
Organizations that embrace Zero Trust initiatives ranging from business policies to technology infrastructure can reap business and security benefits.
Which two domains should be covered under Zero Trust initiatives? (Choose two)
- A. workload
- B. work domain
- C. workplace
- D. workgroup
- E. workspace
Answer: AC
NEW QUESTION 10
You are designing a new Ethernet-based metro-area network for an enterprise customer to connect 50 sites within the same city OSPF will be the routing protocol used. The customer is primarily concerned with IPv4 address conservation and convergence time.
Which two combined actions do you recommend? (Choose two)
- A. Use a multipoint Metro-E service for router connections
- B. Use a single address per router for all P2P links
- C. Use P2P links between routers in a hub-and-spoke design
- D. Configure address aggregation at each site router
- E. Determine which OSPF routers will be DR/BDR
Answer: AC
NEW QUESTION 11
An enterprise requires MPLS connected branches to access cloud-based Microsoft 365 services over an SD-WAN solution. Internet access Is available only at dual regional hub sites that are connected to the MPLS network.
Which connectivity method provides an optimum access method to the cloud- based services If one ISP suffers loss or latency?
- A. Cloud onRamp gateway site
- B. Cloud onRamp SWG
- C. Cloud onRamp
- D. Cloud onRamp SaaS
Answer: D
NEW QUESTION 12
Company XYZ wants to secure the data plane of their network.
Which two technologies can be included in the security design? (Choose two)
- A. DAI
- B. IP Source Guard
- C. BEEP
- D. CPPr
- E. MPP
Answer: AB
NEW QUESTION 13
Which two aspects are considered when designing a dual hub dual DMVPN cloud topology? (Choose two )
- A. will only work with single-tier headend architecture
- B. hub sites must connect to both DMVPN clouds
- C. recommended for high availability
- D. spoke-to-spoke traffic will transit the hub unless spokes exchange dynamic routing directly
- E. requires all sites to have dual Internet connections
Answer: AC
NEW QUESTION 14
According to the CIA triad principles for network security design, which principle should be priority for a Zero Trust network?
- A. requirement for data-in-motion encryption and 2FA authentication
- B. requirement for data-at-rest encryption foe user identification within the VPN terminationhardware
- C. categorization of systems, data, and enterprise BYOD assets that are connected to networkzones based on individual privacy needs
- D. ensuring that authorized users have high-availability system access from defined zones todefined systems or zones
Answer: A
NEW QUESTION 15
A small organization of 20 employees is looking to deliver a network design service for
modernizing customer networks to support advanced solutions:
- Project scope and weekly progress should be visualized by the management.
- Always consider feedback and make changes accordingly during the project.
- Should consider flexibility to change scope at the point of time.
Which project methodology meets the requirements and have the least impact on the outcome?
- A. Scrum
- B. LEAN
- C. Kanban
- D. Six-Sigma
Answer: C
NEW QUESTION 16
Drag and Drop Question
Drag and drop the multicast protocols from the left onto the current design situation on the right.
Solution:

Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 17
Which two conditions must be met for EIGRP to maintain an alternate loop-free path to a remote network? (Choose two.)
- A. The Reported Distance from a successor is lower than the local Feasible Distance.
- B. The Reported Distance from a successor is higher than the local Feasible Distance.
- C. The feasibility condition does not need to be met.
- D. The Feasible Distance from a successor is lower than the local Reported Distance.
- E. A feasible successor must be present.
Answer: AE
NEW QUESTION 18
Refer to the exhibit.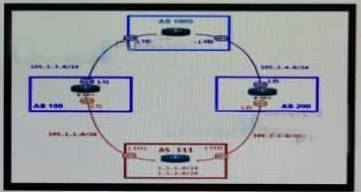
An engineer is designing the network for a multihomed customer running in AS 111 does not have any other Ass connected to it.
Which technology is more comprehensive to use in the design to make sure that the AS is not being used as a transit AS?
- A. Configure the AS-set attribute to allow only routes from AS 111 to be propagated to the neighborASs.
- B. Use the local preference attribute to configure your AS as a non-transit'' AS.
- C. include an AS path access list to send routes to the neighboring ASs that only have AS 111 in theAS path field.
- D. Include a prefix list to only receive routes from neighboring ASs.
Answer: C
NEW QUESTION 19
Which two statements describe the usage of the IS-IS overload bit technique? (Choose two )
- A. lf overload-bit is set on a Level 2 intermediate system, the other Level 2 intermediate systems inthe topology will stop using the overloaded IS to forward Level 2 traffic However, the intermediatesystem can still forward Level 1 traffic
- B. It can be set in intermediate systems (IS-IS routers) to prioritize control plane CSNP packets.
- C. It can be used to automatically synchronize the link-state database between Level 1 intermediatesystems
- D. It can be set in intermediate systems (IS-IS routers) to avoid traffic black holes until routingprotocols are fully converged after a reload operation.
- E. It can be set in intermediate systems (IS-IS routers) to attract transit traffic from otherintermediate systems
Answer: AD
NEW QUESTION 20
Which design principal improves network resiliency?
- A. Added load-balancing
- B. Added redundancy
- C. Added confidentiality
- D. Added reliability
Answer: B
NEW QUESTION 21
......
Recommend!! Get the Full 400-007 dumps in VCE and PDF From Thedumpscentre.com, Welcome to Download: https://www.thedumpscentre.com/400-007-dumps/ (New 0 Q&As Version)
