We provide real AZ-203 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass Microsoft AZ-203 Exam quickly & easily. The AZ-203 PDF type is available for reading and printing. You can print more and practice many times. With the help of our Microsoft AZ-203 dumps pdf and vce product and material, you can easily pass the AZ-203 exam.
Free demo questions for Microsoft AZ-203 Exam Dumps Below:
NEW QUESTION 1
You need to ensure the security policies are met. What code do you add at line CS07?
- A. -PermissionsToKeys wrapkey, unwrapkey, get
- B. -PermissionsToKeys create, encrypt, decrypt
- C. -PermissionsToCertificates wrapkey, unwrapkey, get
- D. -PermissionsToCertificates create, encrypt, decrypt
Answer: D
Explanation:
Case Study: 3
Proseware, Inc
Background
You are a developer for Proseware, Inc. You are developing an application that applies a set of governance policies for Proseware's internal services, external services, and applications. The application will also provide a shared library for common functionality.
Requirements Policy service
You develop and deploy a stateful ASP.NET Core 2.1 web application named Policy service to an Azure App Service Web App. The application reacts to events from Azure Event Grid and performs policy actions based on those events.
The application must include the Event Grid Event ID field in all Application Insights telemetry.
Policy service must use Application Insights to automatically scale with the number of policy actions that it is performing.
Policies Log policy
All Azure App Service Web Apps must write logs to Azure Blob storage. All log files should be saved to a container named logdrop. Logs must remain in the container for 15 days.
Authentication events
Authentication events are used to monitor users signing in and signing out. All authentication events must be processed by Policy service. Sign outs must be processed as quickly as possible.
Policylib
You have a shared library named PolicyLib that contains functionality common to all ASP.NET Core web services and applications. The Policy Lib library must
• Exclude non-user actions from Application Insights telemetry.
• Provide methods that allow a web service to scale itself.
• Ensure that scaling actions do not disrupt application usage.
Other
Anomaly detection service
You have an anomaly detection service that analyzes log information for anomalies. It is implemented as an Azure as a web service.
If an anomaly is detected, an Azure Function that emails administrators is called by using an HTTP WebHook.
Health monitoring
All web applications and services have health monitoring at the /health service endpoint.
Issues Policy loss
When you deploy Policy service, policies may not be applied if they were in the process of being applied during the deployment.
Performance issue
When under heavy load, the anomaly detection service undergoes slowdowns and rejects connections.
Notification latency
Users report that anomaly detection emails can sometimes arrive several minutes after an anomaly is detected.
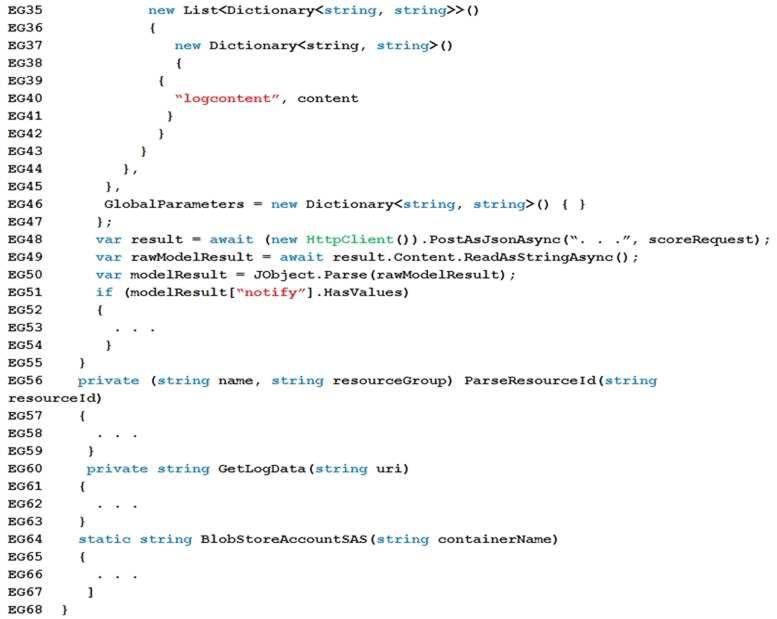
App code EnventGridController.cs
Relevant portions of the app files are shown below. Line numbers are included for reference only and include a two-character prefix that denotes the specific file to which they belong.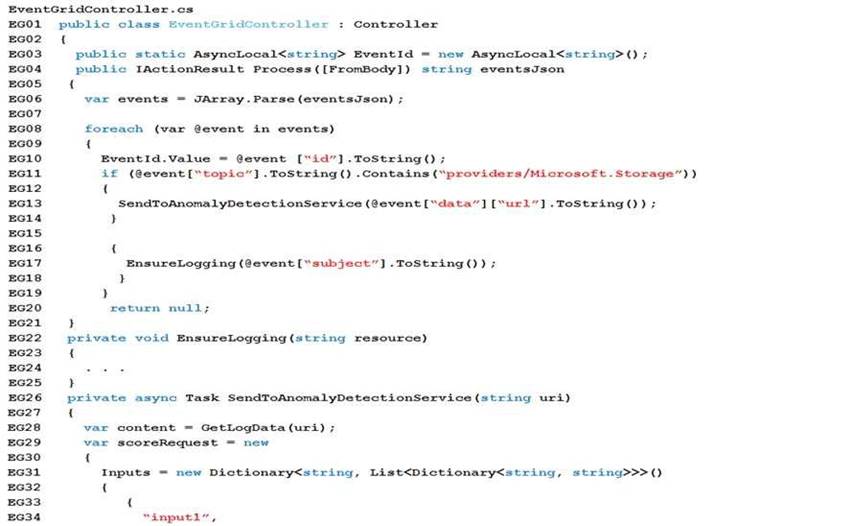
LoginEvents.cs
Relevant portions of the app files are shown below. Line numbers are included for reference only and include a two-character prefix that denotes the specific file to which they belong.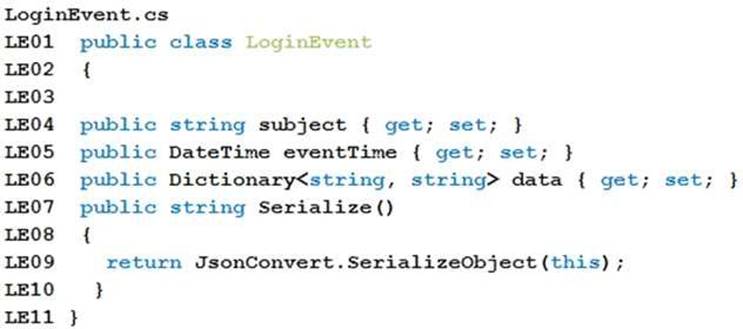
NEW QUESTION 2
HOTSPOT
You need to ensure that security requirements are met.
What value should be used for the ConnectionString field on line DB03 in the Database class? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.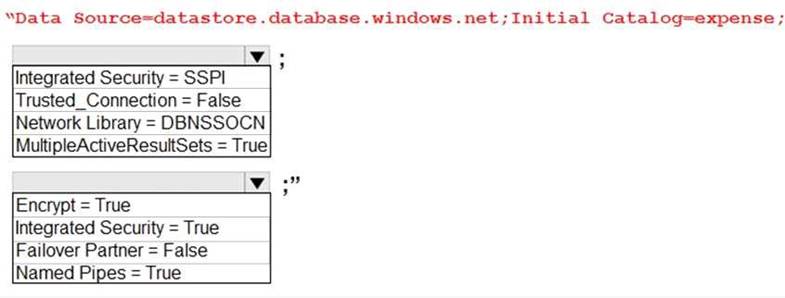
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Box 1: Integrated Security=SSPI
Integrated security: For all data source types, connect using the current user account.
For SqlClient you can use Integrated Security=true; or Integrated Security=SSPI; Scenario: All access to Azure Storage and Azure SQL database must use the application’s Managed Service Identity (MSI)
Box 2: Encrypt = True
Scenario: All data must be protected in transit. References:
https://docs.microsoft.com/en-us/dotnet/framework/data/adonet/connection-string- syntax
NEW QUESTION 3
You develop a serverless application using several Azure Functions. These functions connect to data from within the code.
You want to configure tracing for an Azure Function App project. You need to change configuration settings in the hostjson file. Which tool should you use?
- A. Azure portal
- B. Azure PowerShell
- C. Azure Functions Core Tools (Azure CLI)
- D. Visual Studio
Answer: C
NEW QUESTION 4
You are developing an internal website for employees to view sensitive data. The website uses Azure Active Directory (AAD) for authentication. You need to implement multifactor authentication for the website.
What should you do? Each correct answer presents part of the solution. NOTE; Each correct selection is worth one point.
- A. In Azure AD, create a new conditional access policy.
- B. In Azure AD, enable application proxy.
- C. Configure the website to use Azure AD B2C.
- D. In Azure AD conditional access, enable the baseline policy.
- E. Upgrade to Azure AD Premium.
Answer: CE
NEW QUESTION 5
You are developing an ASP.NET Core Web API web service. The web service uses Azure Application Insights for all telemetry and dependency tracking. The web service reads and writes data to a database other than Microsoft SQL Server.
You need to ensure that dependency tracking works for calls to the third-party database.
Which two Dependency Telemetry properties should you store in the database? Each correct answer
presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. Telemetry.Context.Operation.Id
- B. Tetemetry.Context.Cloud.Rolelnstance
- C. Telemetry.Id
- D. Telemetry.ContextSession.Id
- E. Telemetry.Name
Answer: BC
NEW QUESTION 6
HOTSPOT
You need to retrieve all order line items sorted alphabetically by the city.
How should you complete the code? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.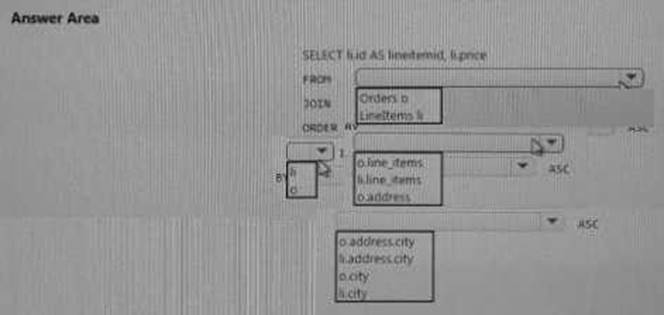
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 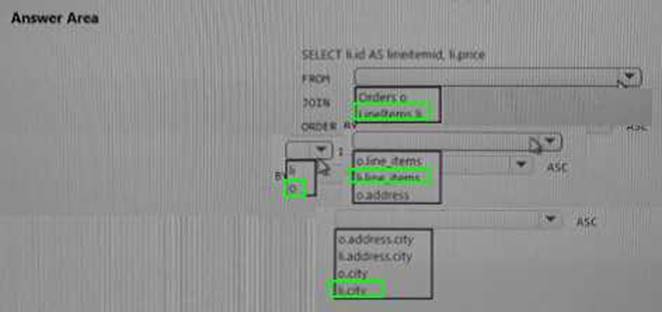
NEW QUESTION 7
Note: This question is part of a series of questions that present the same scenario.
Each question in the series contains a unique solution. Determine whether the solution meets the stated goals. You need to meet the LabelMaket application
Solution; Create a conditional access policy and assign it to the Azure Kubernetes service cluster.
Does the solution meet the goal?
- A. Yes
- B. No
Answer: B
Explanation:
Scenario: The LabelMaker applications must be secured by using an AAD account that has full access to all namespaces of the Azure Kubernetes Service (AKS) cluster.
Before an Azure Active Directory account can be used with the AKS cluster, a role binding or cluster role binding needs to be created.
References:
https://docs.microsoft.com/en-us/azure/aks/aad-integration
NEW QUESTION 8
You need to update the chatbot to greet the user when they sign in.
Which two rich card formats can you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point
- A. Thumbnail
- B. Adaptive
- C. Sign-in
- D. Hero
- E. Animation
Answer: AC
Explanation:
Scenario: The chatbot greeting interface must match the formatting of the following example: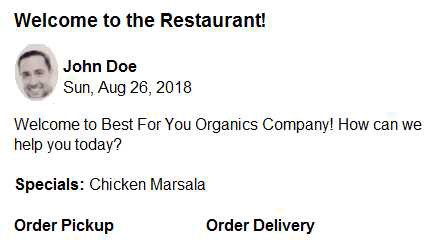
A message exchange between user and bot can contain one or more rich cards rendered as a list or carousel. The Attachments property of the Activity object contains an array of Attachment objects that represent the rich cards and media attachments within the message.
The Bot Framework currently supports eight types of rich cards:
Thumbnail Card. A card that typically contains a single thumbnail image, one or more buttons, and text.
SignIn Card. A card that enables a bot to request that a user sign-in. It typically contains text and one or more buttons that the user can click to initiate the sign-in process.
Incorrect Answers:
B: Animation Card. A card that can play animated GIFs or short videos.
C Hero Card. A card that typically contains a single large image, one or more buttons, and text.
E: Adaptive Card. A customizable card that can contain any combination of text, speech, images, buttons, and input fields.
Note:
Receipt Card. A card that enables a bot to provide a receipt to the user. It typically contains the list of items to include on the receipt, tax and total information, and other text.
Video Card. A card that can play videos. References:
https://docs.microsoft.com/en-us/azure/bot-service/dotnet/bot-builder-dotnet-add- rich-card-attachments?view=azure-bot-service-3.0
NEW QUESTION 9
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Margie's Travel is an international travel and bookings management service. The company is expanding into restaurant bookings. You are tasked with implementing Azure Search tor the restaurants listed in their solution.
You create the index in Azure Search.
You need to import the restaurant data into the Azure Search service by using the Azure Search NET SDK.
Solution:
1. Create a SearchServiceClient object to connect to the search index.
- A. Mastered
- B. Not Mastered
Answer: A
NEW QUESTION 10
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution Determine whether the solution meets the stated goals.
You need to meet the vendor notification requirement.
Solution: Configure notifications in the Azure API Management instance. Does the solution meet the goal?
- A. Yes
- B. No
Answer: B
Explanation:
Use a custom outbound Azure API Management policy. Scenario:
If a vendor is nearing the number of calls or bandwidth limit, the API must trigger email notifications to the vendor.
(API usage must not exceed 5,000 calls and 50,000 kilobytes of bandwidth per hour per vendor.)
References:
https://docs.microsoft.com/en-us/azure/api-management/api-management-howto- policies
NEW QUESTION 11
HOTSPOT
You need to ensure that you can deploy the LabelMaker application.
How should you complete the CLI commands? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.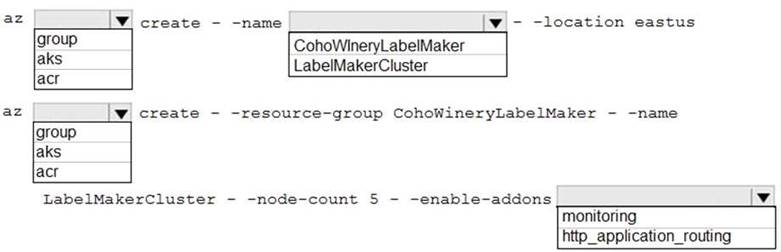
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Box 1: group
Create a resource group with the az group create command. An Azure resource group is a logical group in which Azure resources are deployed and managed.
The following example creates a resource group named myResourceGroup in the westeurope location.
az group create --name myResourceGroup --location westeurope Box 2: CohoWinterLabelMaker
Use the resource group named, which is used in the second command. Box 3: aks
The command az aks create, is used to create a new managed Kubernetes cluster. Box 4: monitoring
Scenario: LabelMaker app
Azure Monitor Container Health must be used to monitor the performance of workloads that are deployed to Kubernetes environments and hosted on Azure Kubernetes Service (AKS).
You must use Azure Container Registry to publish images that support the AKS deployment.
NEW QUESTION 12
DRAG DROP
You are developing Azure WebJobs.
You need to recommend a WebJob type for each scenario.
Which WebJob type should you recommend? To answer, drag the appropriate WebJob types to the correct scenarios. Each WebJob type may be used once more than once, or not at all. You may need to drag the split bar between panes or scroll to view content
NOTE: Each correct selection s worth one point.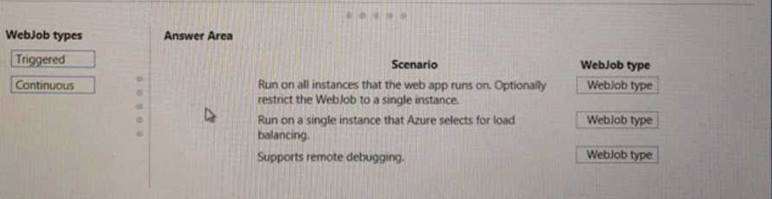
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 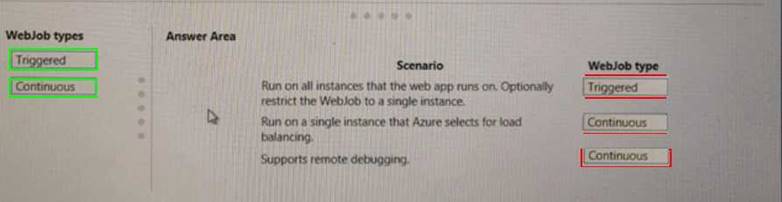
NEW QUESTION 13
HOTSPOT
You need to ensure that security policies are met. What code should you add at Line PC26?
To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.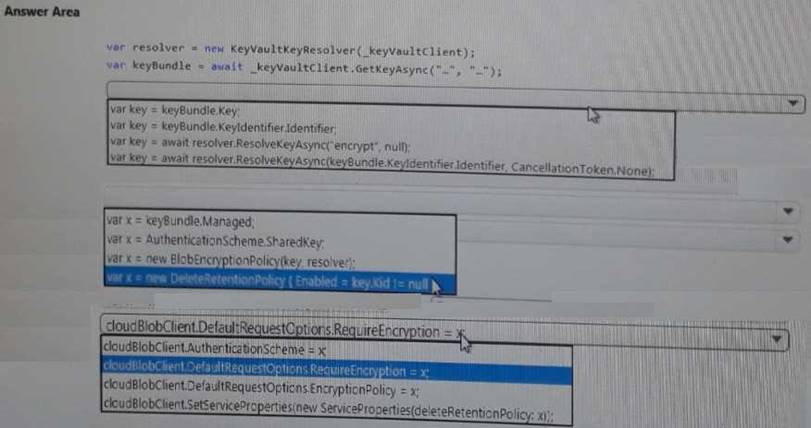
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 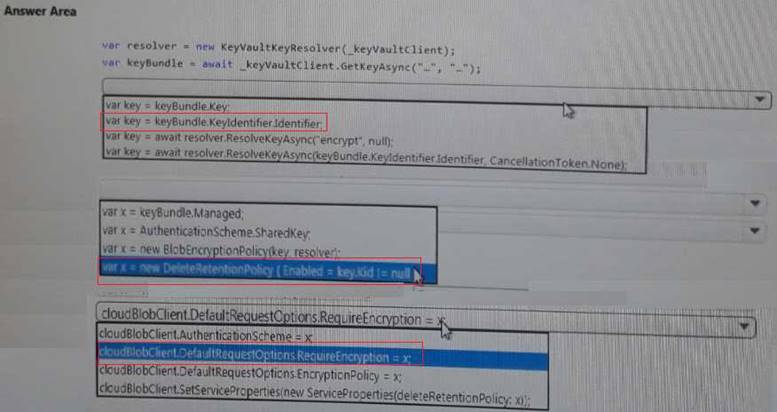
NEW QUESTION 14
DRAG DROP
Fourth Coffee has an ASP.NET Core web app that runs in Docker. The app is mapped to the www.fourthcoffee.com domain.
Fourth Coffee is migrating this application to Azure.
You need to provision an App Service Web App to host this docker image and map the custom domain to the App Service web app.
A resource group named FourthCoffeePublicWebResourceGroup has been created in the WestUS region that contains an App Service Plan named AppServiceLinuxDockerPlan.
Which order should the CLI commands be used to develop the solution? To answer, move all of the Azure CLI commands from the list of commands to the answer area and arrange them in the correct order.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 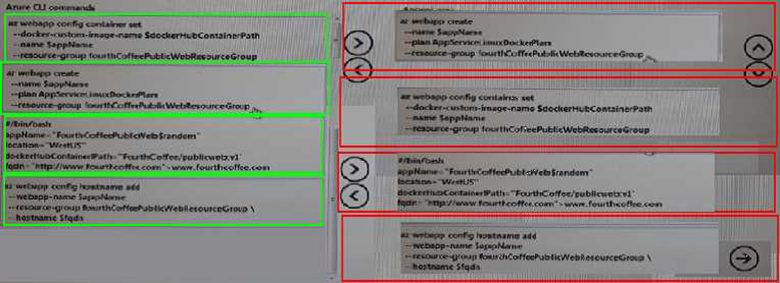
NEW QUESTION 15
DRAG DROP
Your company has several websites that use a company logo image. You use Azure Content Delivery Network (CDN) to store the static image.
You need to determine the correct process of how the CDN and the Point of Presence (POP) server will distribute the image and list the items in the correct
order.
In which order do the actions occur? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.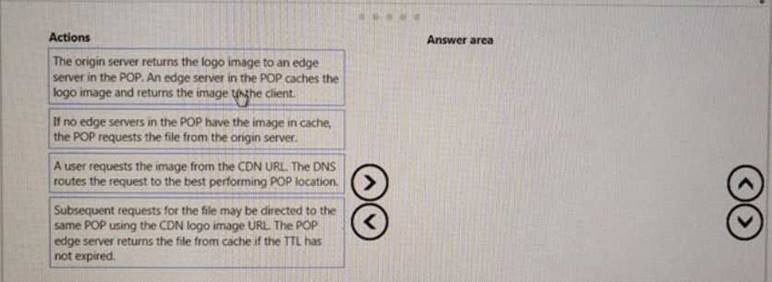
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 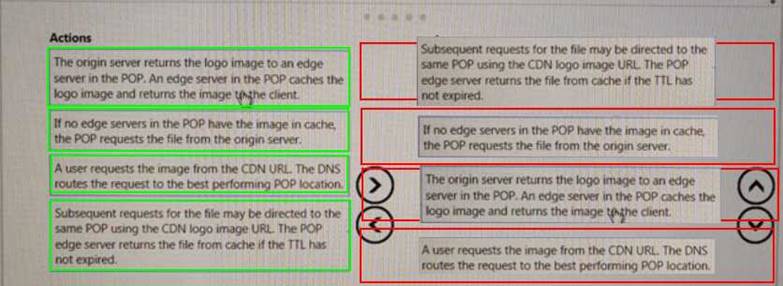
NEW QUESTION 16
DRAG DROP
You develop a gateway solution for a public facing news API.
The news API back end is implemented as a RESTful sen/ice and hosted in an Azure App Service instance.
You need to configure back-end authentication for the API Management service instance.
Which target and gateway credential type should you use? To answer, drag the appropriate values to the correct parameters. Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 17
You are creating a hazard notification system that has a single signaling server which triggers audio and visual alarms to start and stop.
You implement Azure Service Bus to publish alarms. Each alarm controller uses Azure Service Bus to receive alarm signals as part of a transaction. Alarm events must be recorded for audit purposes. Each transaction record must include information about the alarm type that was activated.
You need to implement a reply trail auditing solution.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. Assign the value of the hazard message SessionID property to the SequenceNumber property.
- B. Assign the value of the hazard message SequenceNumber property to the DeliveryCount propert
- C. Assign the value of the hazard message MessageId property to the DeliveryCount property.
- D. Assign the value of the hazard message SessionID property to the ReplyToSessionld property.
- E. Assign the value of the hazard message MessageId property to the SequenceNumber property.
- F. Assign the value of the hazard message Messageld property to the CorrelationId property.
Answer: AB
NEW QUESTION 18
HOTSPOT
You need to meet the security requirements for external partners. Which Azure Active Directory features should you use?
To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.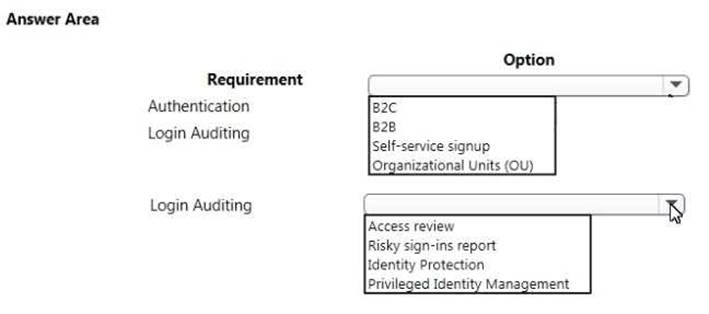
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 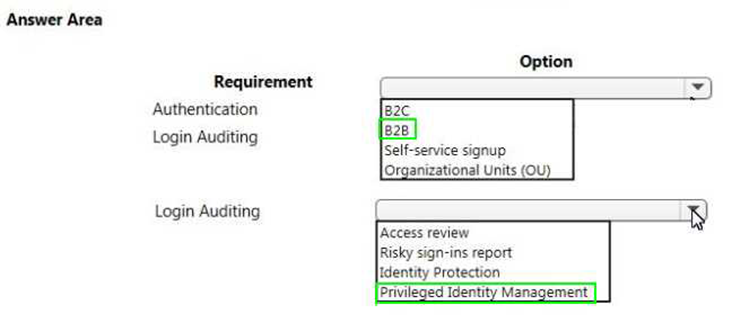
NEW QUESTION 19
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You need to ensure that the SecurityPin security requirements are met.
Solution: Using the Azure Portal, add Data Masking to the SecurityPin column, and exclude the dbo user. Add a SQL security policy with a filter predicate based on the user identity.
Does the solution meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 20
Create a DataContainer that contains the documents which must be added.
- A. Mastered
- B. Not Mastered
Answer: A
NEW QUESTION 21
You need to resolve a notification latency issue.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point
- A. Ensure that the Azure Function is using an App Service plan.
- B. Set Always On to false
- C. Ensure that the Azure Function is set to use a consumption plan.
- D. Set Always On to true.
Answer: AD
Explanation:
Azure Functions can run on either a Consumption Plan or a dedicated App Service Plan. If you run in a dedicated mode, you need to turn on the Always On setting for your Function App to run properly. The Function runtime will go idle after a few minutes of inactivity, so only HTTP triggers will actually "wake up" your functions. This is similar to how WebJobs must have Always On enabled.
Scenario: Notification latency: Users report that anomaly detection emails can sometimes arrive several minutes after an anomaly is detected.
Anomaly detection service: You have an anomaly detection service that analyzes log information for anomalies. It is implemented as an Azure Machine Learning model. The model is deployed as a web service.
If an anomaly is detected, an Azure Function that emails administrators is called by using an HTTP WebHook.
References:
https://github.com/Azure/Azure-Functions/wiki/Enable-Always-On-when-running-on-dedicated-App-Service-Plan
NEW QUESTION 22
HOTSPOT
A company is developing a gaming platform. Users can join teams to play online and see leaderboards that include player statistics. The solution includes an entity named Team.
You plan to implement an Azure Redis Cache instance to improve the efficiency of data operations for entities that rarely change.
You need to invalidate the cache when team data is changed.
How should you complete the code? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.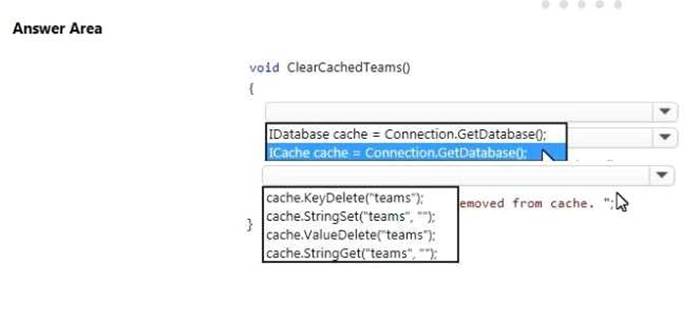
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 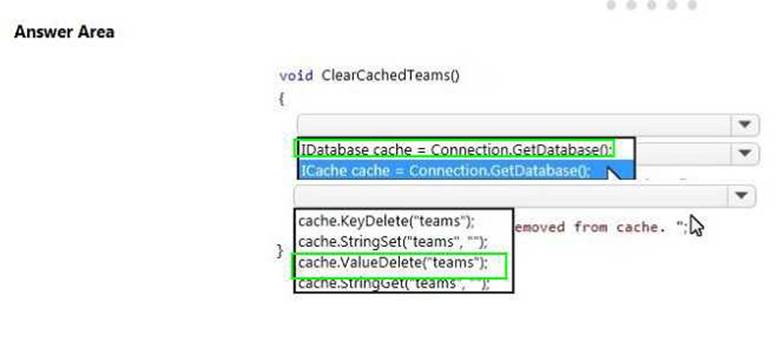
NEW QUESTION 23
HOTSPOT
A company runs an international travel and bookings management service. The company plans to begin offering restaurant bookings. You must develop a solution that uses Azure Search and meets the following requirements:
• Users must be able to search for restaurants by name, description, location, and cuisine.
• Users must be able to narrow the results further by location, cuisine, rating, and family-friendliness.
• All words in descriptions must be included in searches. You need to add annotations to the restaurant class.
How should you complete the code segment? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.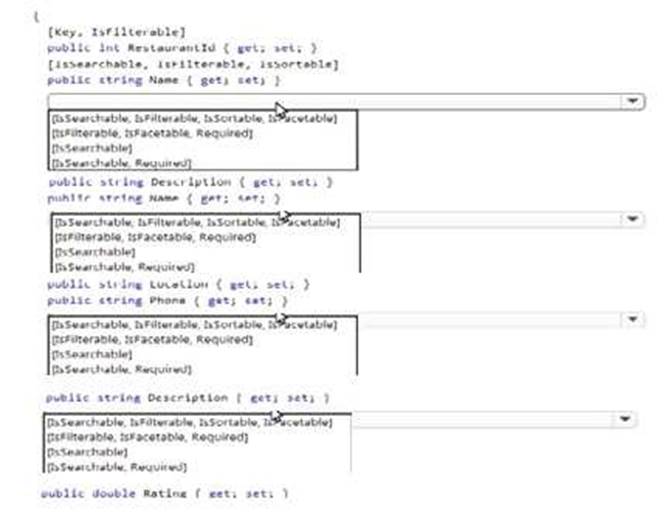
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 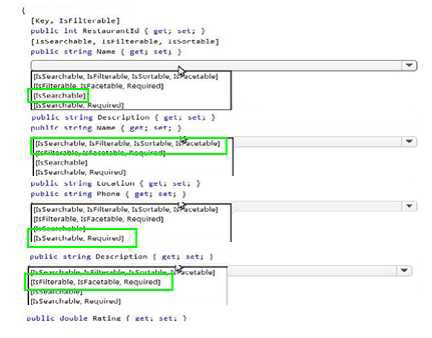
NEW QUESTION 24
DRAG DROP
You are developing a .NET Core model-view controller (MVC) application hosted on Azure for a health care system that allows providers access to their information.
You develop the following code: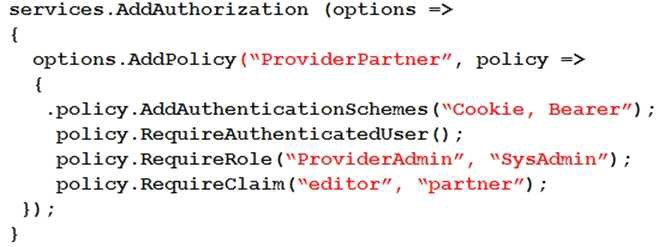
You define a role named SysAdmin.
You need to ensure that the application meets the following authorization requirements:
Allow the ProviderAdmin and SysAdmin roles access to the Partner controller regardless of whether the user holds an editor claim of partner.
Limit access to the Manage action of the controller to users with an editor claim of partner who are also members of the SysAdmin role.
How should you complete the code? To answer, drag the appropriate code segments to the correct locations. Each code segment may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.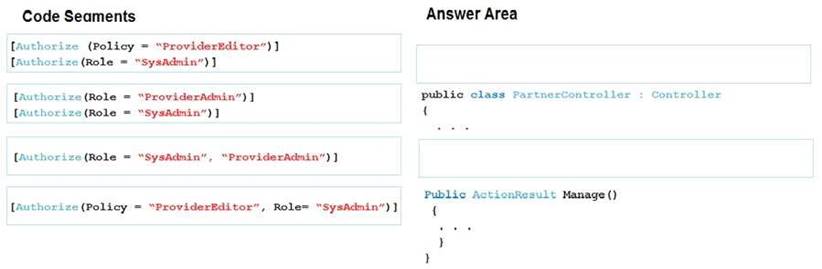
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Box 1:
Allow the ProviderAdmin and SysAdmin roles access to the Partner controller regardless of whether the user holds an editor claim of partner.
Box 2:
Limit access to the Manage action of the controller to users with an editor claim of partner who are also members of the SysAdmin role.
NEW QUESTION 25
......
Thanks for reading the newest AZ-203 exam dumps! We recommend you to try the PREMIUM Surepassexam AZ-203 dumps in VCE and PDF here: https://www.surepassexam.com/AZ-203-exam-dumps.html (132 Q&As Dumps)
