Exam Code: CEH-001 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Certified Ethical Hacker (CEH)
Certification Provider: GAQM
Free Today! Guaranteed Training- Pass CEH-001 Exam.
GAQM CEH-001 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Which of the following can the administrator do to verify that a tape backup can be recovered in its entirety?
- A. Restore a random file.
- B. Perform a full restore.
- C. Read the first 512 bytes of the tape.
- D. Read the last 512 bytes of the tape.
Answer: B
NEW QUESTION 2
Exhibit: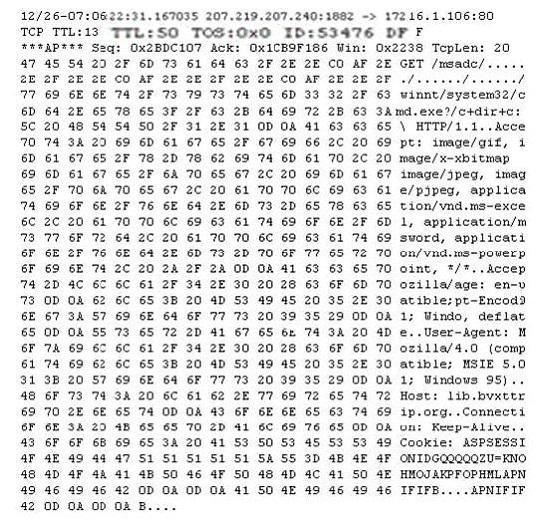
Study the following log extract and identify the attack.
- A. Hexcode Attack
- B. Cross Site Scripting
- C. Multiple Domain Traversal Attack
- D. Unicode Directory Traversal Attack
Answer: D
Explanation:
The “Get /msadc/……/……/……/winnt/system32/cmd.exe?” shows that a Unicode Directory Traversal Attack has been performed.
NEW QUESTION 3
You receive an email with the following message: Hello Steve,
We are having technical difficulty in restoring user database record after the recent blackout. Your account data is corrupted. Please logon to the SuperEmailServices.com and change your password.
http://www.supermailservices.com@0xde.0xad.0xbe.0xef/support/logon.htm
If you do not reset your password within 7 days, your account will be permanently disabled locking you out from our e-mail services.
Sincerely, Technical Support
SuperEmailServices
From this e-mail you suspect that this message was sent by some hacker since you have been using their e-mail services for the last 2 years and they have never sent out an e-mail such as this. You also observe the URL in the message and confirm your suspicion about 0xde.0xad.0xbde.0xef which looks like hexadecimal numbers. You immediately enter the following at Windows 2000 command prompt:
Ping 0xde.0xad.0xbe.0xef
You get a response with a valid IP address.
What is the obstructed IP address in the e-mail URL?
- A. 222.173.190.239
- B. 233.34.45.64
- C. 54.23.56.55
- D. 199.223.23.45
Answer: A
Explanation:
0x stands for hexadecimal and DE=222, AD=173, BE=190 and EF=239
NEW QUESTION 4
Which of the following is a symmetric cryptographic standard?
- A. DSA
- B. PKI
- C. RSA
- D. 3DES
Answer: D
NEW QUESTION 5
Maintaining a secure Web server requires constant effort, resources, and vigilance from an organization. Securely administering a Web server on a daily basis is an essential aspect of Web server security.
Maintaining the security of a Web server will usually involve the following steps:
1. Configuring, protecting, and analyzing log files
2. Backing up critical information frequently
3. Maintaining a protected authoritative copy of the organization's Web content
4. Establishing and following procedures for recovering from compromise
5. Testing and applying patches in a timely manner
6. Testing security periodically.
In which step would you engage a forensic investigator?
- A. 1
- B. 2
- C. 3
- D. 4
- E. 5
- F. 6
Answer: D
NEW QUESTION 6
Joel and her team have been going through tons of garbage, recycled paper, and other rubbish in order to find some information about the target they are attempting to penetrate. How would you call this type of activity?
- A. Dumpster Diving
- B. Scanning
- C. CI Gathering
- D. Garbage Scooping
Answer: A
NEW QUESTION 7
Exhibit: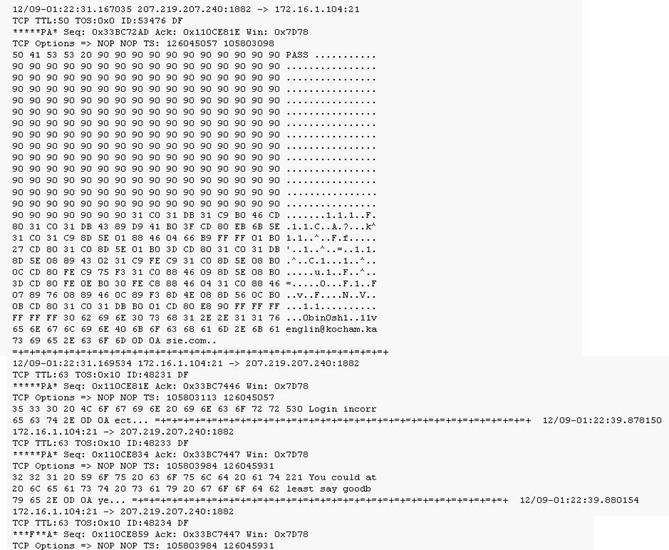
Given the following extract from the snort log on a honeypot, what do you infer from the attack?
- A. A new port was opened
- B. A new user id was created
- C. The exploit was successful
- D. The exploit was not successful
Answer: D
Explanation:
The attacker submits a PASS to the honeypot and receives a login incorrect before disconnecting.
NEW QUESTION 8
What is the key advantage of Session Hijacking?
- A. It can be easily done and does not require sophisticated skills.
- B. You can take advantage of an authenticated connection.
- C. You can successfully predict the sequence number generation.
- D. You cannot be traced in case the hijack is detected.
Answer: B
Explanation:
As an attacker you don’t have to steal an account and password in order to take advantage of an authenticated connection.
NEW QUESTION 9
Jimmy, an attacker, knows that he can take advantage of poorly designed input validation routines to create or alter SQL commands to gain access to private data or execute commands in the database. What technique does Jimmy use to compromise a database?
- A. Jimmy can submit user input that executes an operating system command to compromise a target system
- B. Jimmy can gain control of system to flood the target system with requests, preventing legitimate users from gaining access
- C. Jimmy can utilize an incorrect configuration that leads to access with higher-than expected privilege of the database
- D. Jimmy can utilize this particular database threat that is an SQL injection technique to penetrate a target system
Answer: D
NEW QUESTION 10
This method is used to determine the Operating system and version running on a remote target system. What is it called?
- A. Service Degradation
- B. OS Fingerprinting
- C. Manual Target System
- D. Identification Scanning
Answer: B
NEW QUESTION 11
A newly discovered flaw in a software application would be considered which kind of security vulnerability?
- A. Input validation flaw
- B. HTTP header injection vulnerability
- C. 0-day vulnerability
- D. Time-to-check to time-to-use flaw
Answer: C
NEW QUESTION 12
Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal?
05/20-17:0645.061034 192.160.13.4:31337 --> 172.16.1.101:1
TCP TTL:44 TOS:0x10 ID:242
***FRP** Seq:0xA1D95 Ack:0x53 Win: 0x400
What is odd about this attack? (Choose the most appropriate statement)
- A. This is not a spoofed packet as the IP stack has increasing numbers for the three flags.
- B. This is back orifice activity as the scan comes from port 31337.
- C. The attacker wants to avoid creating a sub-carrier connection that is not normally valid.
- D. There packets were created by a tool; they were not created by a standard IP stack.
Answer: B
Explanation:
Port 31337 is normally used by Back Orifice. Note that 31337 is hackers spelling of ‘elite’, meaning ‘elite hackers’.
NEW QUESTION 13
What type of session hijacking attack is shown in the exhibit?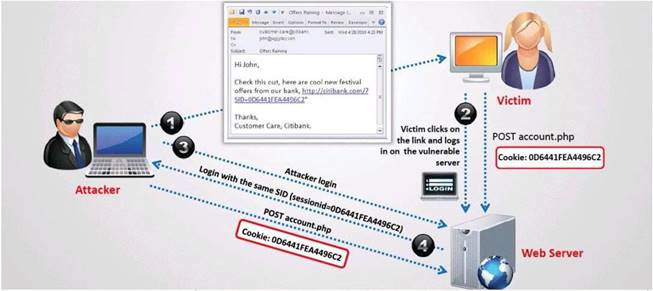
- A. Cross-site scripting Attack
- B. SQL Injection Attack
- C. Token sniffing Attack
- D. Session Fixation Attack
Answer: D
NEW QUESTION 14
Which Steganography technique uses Whitespace to hide secret messages?
- A. snow
- B. beetle
- C. magnet
- D. cat
Answer: A
NEW QUESTION 15
E-mail scams and mail fraud are regulated by which of the following?
- A. 18 U.S.
- B. pa
- C. 1030 Fraud and Related activity in connection with Computers
- D. 18 U.S.
- E. pa
- F. 1029 Fraud and Related activity in connection with Access Devices
- G. 18 U.S.
- H. pa
- I. 1362 Communication Lines, Stations, or Systems
- J. 18 U.S.
- K. pa
- L. 2510 Wire and Electronic Communications Interception and Interception of Oral Communication
Answer: A
Explanation:
http://www.law.cornell.edu/uscode/html/uscode18/usc_sec_18_00001030---- 000-.html
NEW QUESTION 16
Password cracking programs reverse the hashing process to recover passwords.(True/False.
- A. True
- B. False
Answer: B
Explanation:
Password cracking programs do not reverse the hashing process. Hashing is a one-way process. What these programs can do is to encrypt words, phrases, and characters using the same encryption process and compare them to the original password.
A hashed match reveals the true password.
NEW QUESTION 17
LAN Manager Passwords are concatenated to 14 bytes, and split in half. The two halves are hashed individually. If the password is 7 characters or less, than the second half of the hash is always:
- A. 0xAAD3B435B51404EE
- B. 0xAAD3B435B51404AA
- C. 0xAAD3B435B51404BB
- D. 0xAAD3B435B51404CC
Answer: A
NEW QUESTION 18
Which set of access control solutions implements two-factor authentication?
- A. USB token and PIN
- B. Fingerprint scanner and retina scanner
- C. Password and PIN
- D. Account and password
Answer: A
NEW QUESTION 19
A company firewall engineer has configured a new DMZ to allow public systems to be located away from the internal network. The engineer has three security zones set:
Untrust (Internet) – (Remote network = 217.77.88.0/24) DMZ (DMZ) – (11.12.13.0/24)
Trust (Intranet) – (192.168.0.0/24)
The engineer wants to configure remote desktop access from a fixed IP on the remote network to a remote desktop server in the DMZ. Which rule would best fit this requirement?
- A. Permit 217.77.88.0/24 11.12.13.0/24 RDP 3389
- B. Permit 217.77.88.12 11.12.13.50 RDP 3389
- C. Permit 217.77.88.12 11.12.13.0/24 RDP 3389
- D. Permit 217.77.88.0/24 11.12.13.50 RDP 3389
Answer: B
NEW QUESTION 20
Which of the following snort rules look for FTP root login attempts?
- A. alert tcp -> any port 21 (msg:"user root";)
- B. alert tcp -> any port 21 (message:"user root";)
- C. alert ftp -> ftp (content:"user password root";)
- D. alert tcp any any -> any any 21 (content:"user root";)
Answer: D
Explanation:
The snort rule header is built by defining action (alert), protocol (tcp), from IP subnet port (any any), to IP subnet port (any any 21), Payload Detection Rule Options (content:”user root”;)
NEW QUESTION 21
Snort is an open source Intrusion Detection system. However, it can also be used for a few other purposes as well.
Which of the choices below indicate the other features offered by Snort?
- A. IDS, Packet Logger, Sniffer
- B. IDS, Firewall, Sniffer
- C. IDS, Sniffer, Proxy
- D. IDS, Sniffer, content inspector
Answer: A
Explanation:
Snort is a free software network intrusion detection and prevention system capable of performing packet logging & real-time traffic analysis, on IP networks. Snort was written by Martin Roesch but is now owned and developed by Sourcefire
NEW QUESTION 22
Sandra is conducting a penetration test for XYZ.com. She knows that XYZ.com is using wireless networking for some of the offices in the building right down the street. Through social engineering she discovers that they are using 802.11g. Sandra knows that 802.11g uses the same 2.4GHz frequency range as 802.11b. Using NetStumbler and her 802.11b wireless NIC, Sandra drives over to the building to map the wireless networks. However, even though she repositions herself around the building several times, Sandra is not able to detect a single AP.
What do you think is the reason behind this?
- A. Netstumbler does not work against 802.11g.
- B. You can only pick up 802.11g signals with 802.11a wireless cards.
- C. The access points probably have WEP enabled so they cannot be detected.
- D. The access points probably have disabled broadcasting of the SSID so they cannot be detected.
- E. 802.11g uses OFDM while 802.11b uses DSSS so despite the same frequency and 802.11b card cannot see an 802.11g signal.
- F. Sandra must be doing something wrong, as there is no reason for her to not see the signals.
Answer: E
NEW QUESTION 23
Bart is looking for a Windows NT/2000/XP command-line tool that can be used to assign, display, or modify ACL’s (access control lists) to files or folders and also one that can be used within batch files.
Which of the following tools can be used for that purpose? (Choose the best answer)
- A. PERM.exe
- B. CACLS.exe
- C. CLACS.exe
- D. NTPERM.exe
Answer: B
Explanation:
Cacls.exe is a Windows NT/2000/XP command-line tool you can use to assign, display, or modify ACLs (access control lists) to files or folders. Cacls is an interactive tool, and since it's a command-line utility, you can also use it in batch files.
NEW QUESTION 24
Which type of hacker represents the highest risk to your network?
- A. black hat hackers
- B. grey hat hackers
- C. disgruntled employees
- D. script kiddies
Answer: C
NEW QUESTION 25
A hacker was able to sniff packets on a company's wireless network. The following information was discovereD.
The Key 10110010 01001011
The Cyphertext 01100101 01011010
Using the Exlcusive OR, what was the original message?
- A. 00101000 11101110
- B. 11010111 00010001
- C. 00001101 10100100
- D. 11110010 01011011
Answer: B
NEW QUESTION 26
Leesa is the senior security analyst for a publicly traded company. The IT department recently rolled out an intranet for company use only with information ranging from training, to holiday schedules, to human resources data. Leesa wants to make sure the site is not accessible from outside and she also wants to ensure the site is Sarbanes-Oxley (SOX) compliant. Leesa goes to a public library as she wants to do some Google searching to verify whether the company's intranet is accessible from outside and has been indexed by Google. Leesa wants to search for a website title of "intranet" with part of the URL containing the word "intranet" and the words "human resources" somewhere in the webpage.
What Google search will accomplish this?
- A. related:intranet allinurl:intranet:"human resources"
- B. cache:"human resources" inurl:intranet(SharePoint)
- C. intitle:intranet inurl:intranet+intext:"human resources"
- D. site:"human resources"+intext:intranet intitle:intranet
Answer: C
NEW QUESTION 27
The following script shows a simple SQL injection. The script builds an SQL query by concatenating hard-coded strings together with a string entered by the user: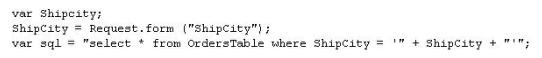
The user is prompted to enter the name of a city on a Web form. If she enters Chicago, the query assembled by the script looks similar to the following:
SELECT * FROM OrdersTable WHERE ShipCity = 'Chicago'
How will you delete the OrdersTable from the database using SQL Injection?
- A. Chicago'; drop table OrdersTable --
- B. Delete table'blah'; OrdersTable --
- C. EXEC; SELECT * OrdersTable > DROP --
- D. cmdshell'; 'del c:sqlmydbOrdersTable' //
Answer: A
NEW QUESTION 28
Which type of scan is used on the eye to measure the layer of blood vessels?
- A. Facial recognition scan
- B. Retinal scan
- C. Iris scan
- D. Signature kinetics scan
Answer: B
NEW QUESTION 29
......
Recommend!! Get the Full CEH-001 dumps in VCE and PDF From Dumps-files.com, Welcome to Download: https://www.dumps-files.com/files/CEH-001/ (New 878 Q&As Version)
