Passleader 210-260 Questions are updated and all 210-260 answers are verified by experts. Once you have completely prepared with our 210-260 exam prep kits you will be ready for the real 210-260 exam without a problem. We have Renewal Cisco 210-260 dumps study guide. PASSED 210-260 First attempt! Here What I Did.
NEW QUESTION 1
What is a possible reason for the error message?Router(config)#aaa server?% Unrecognized command
- A. The command syntax requires a space after the word “server”
- B. The command is invalid on the target device
- C. The router is already running the latest operating system
- D. The router is a new device on which the aaa new-model command must be applied before continuing
Answer: D
Explanation:
Before you can use any of the services AAA network security services provide, you must enable AAA. Source: http://www.cisco.com/c/en/us/td/docs/ios/12_2/security/configuration/guide/fsecur_c/scfaaa.html
NEW QUESTION 2
What feature defines a campus area network?
- A. It has a single geographic location.
- B. It has limited or restricted Internet access.
- C. It has a limited number of segments.
- D. it lacks external connectivity.
Answer: A
NEW QUESTION 3
A user on your network inadvertently activates a botnet program that was received as an email attachment Which type of mechanism does Cisco Firepower use to detect and block only the botnet attack?
- A. network-based access control rule
- B. botnet traffic filter
- C. reputation-based
- D. user-based access control rule
Answer: B
NEW QUESTION 4
Which option is the most effective placement of an IPS device within the infrastructure?
- A. Inline, behind the internet router and firewall
- B. Inline, before the internet router and firewall
- C. Promiscuously, after the Internet router and before the firewall
- D. Promiscuously, before the Internet router and the firewall
Answer: A
Explanation:
Firewalls are generally designed to be on the network perimeter and can handle dropping a lot of the non- legitimate traffic (attacks, scans etc.) very quickly at the ingress interface, often in hardware.
An IDS/IPS is, generally speaking, doing more deep packet inspections and that is a much more computationally expensive undertaking. For that reason, we prefer to filter what gets to it with the firewall line of defense before engaging the IDS/IPS to analyze the traffic flow.
Source: https://supportforums.cisco.com/discussion/12428821/correct-placement-idsips-network-architecture
NEW QUESTION 5
Which feature can help a router or switch maintain packet forwarding and protocol states despite an attack or heavy traffic load on the router or switch?
- A. Control Plane Policing
- B. Service Policy
- C. Cisco Express Forwarding
- D. Policy Map
Answer: A
NEW QUESTION 6
Which command help user1 to use enable,disable,exit&etc commands?
- A. catalyst1(config)#username user1 privilege 0 secret us1pass
- B. catalyst1(config)#username user1 privilege 1 secret us1pass
- C. catalyst1(config)#username user1 privilege 2 secret us1pass
- D. catalyst1(config)#username user1 privilege 5 secret us1pass
Answer: A
Explanation:
To understand this example, it is necessary to understand privilege levels. By default, there are three command levels on the router:
+ privilege level 0 -- Includes the disable, enable, exit, help, and logout commands.
+ privilege level 1 -- Normal level on Telnet; includes all user-level commands at the router> prompt.
+ privilege level 15 -- Includes all enable-level commands at the router# prompt.
Source:
http://www.cisco.com/c/en/us/support/docs/security-vpn/terminal-access-controller-access-control- system-tacacs-/23383-showrun.html
NEW QUESTION 7
What technology can you use to provide data confidentiality, data integrity and data origin authentication on your network?
- A. Certificate Authority
- B. IKE
- C. IPSec
- D. Data Encryption Standards
Answer: C
NEW QUESTION 8
Which two ESA services are available for incoming and outgoing mails? (Choose two.)
- A. DLP
- B. reputation filter
- C. content filter
- D. anti-Dos
- E. antispam
Answer: CE
NEW QUESTION 9
You are configuring a NAT rule on a Cisco ASA. Which description of a mapped interface is true?
- A. It is mandatory for all fire wall modes.
- B. It is mandatory for identity NAT only.
- C. It is optional in transparent mode.
- D. It is optional in routed mode.
Answer: D
NEW QUESTION 10
What are two reasons to recommend SNMPv3 over SNMPv2? (Choose two.)
- A. SNMPv3 is secure because you can configure authentication and privacy
- B. SNMPv3 is a Cisco proprietary protocol
- C. SNMPv2 is secure because you can configure authentication and privacy
- D. SNMPv2 is insecure because it sends information in clear text
- E. SNMPv3 is insecure because it sends information in clear text
Answer: AB
NEW QUESTION 11
Refer to the exhibit.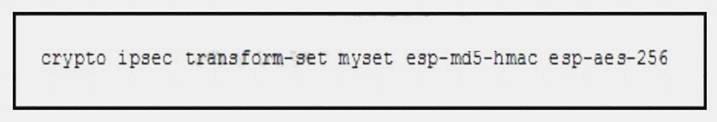
What are two effects of the given command? (Choose two.)
- A. It configures authentication to use AES 256.
- B. It configures authentication to use MD5 HMAC.
- C. It configures authorization use AES 256.
- D. It configures encryption to use MD5 HMAC.
- E. It configures encryption to use AES 256.
Answer: BE
Explanation:
To define a transform set -- an acceptable combination of security protocols and algorithms -- use the crypto ipsec transform-set global configuration command.
ESP Encryption Transform
+ esp-aes 256: ESP with the 256-bit AES encryption algorithm. ESP Authentication Transform
+esp-md5-hmac: ESP with the MD5 (HMAC variant) authentication algorithm. (No longer recommended) Source: http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/security/a1/sec-a1-cr-book/sec-cr- c3.html#wp2590984165
NEW QUESTION 12
On an ASA, the policy that indicates that traffic should not be translated is often referred to as which of the following?
- A. NAT zero
- B. NAT allow
- C. NAT null
- D. NAT forward
Answer: A
NEW QUESTION 13
Which statement about NAT table evaluation in the ASA in true?
- A. Auto-NAT executed first
- B. After Auto-NAT executed first
- C. Auto-NAT executed after the Manual NAT
Answer: A
NEW QUESTION 14
What is the maximum number of methods that a single method list can contain?
- A. 4
- B. 3
- C. 2
- D. 5
Answer: D
NEW QUESTION 15
When is "Deny all" policy an exception in Zone Based Firewall
- A. traffic traverses 2 interfaces in same zone
- B. traffic sources from router via self zone
- C. traffic terminates on router via self zone
- D. traffic traverses 2 interfaces in different zones
- E. traffic terminates on router via self zone
Answer: A
Explanation:
+ There is a default zone, called the self zone, which is a logical zone. For any packets directed to the router directly (the destination IP represents the packet is for the router), the router automatically considers that traffic to be entering the self zone. In addition, any traffic initiated by the router is considered as leaving the self zone.
By default, any traffic to or from the self zone is allowed, but you can change this policy.
+ For the rest of the administrator-created zones, no traffic is allowed between interfaces in different zones.
+ For interfaces that are members of the same zone, all traffic is permitted by default. Source: Cisco Official Certification Guide, Zones and Why We Need Pairs of Them, p.380
NEW QUESTION 16
Which two types of VLANs using PVLANs are valid? (Choose two.)
- A. secondary
- B. community
- C. isolated
- D. promiscuous
- E. backup
Answer: CD
Explanation:  Promiscuous (P) :- Usually connects to a router – a type of a port which is allowed to send and receive frames from any other port on the VLAN.
Promiscuous (P) :- Usually connects to a router – a type of a port which is allowed to send and receive frames from any other port on the VLAN. Isolated (I) : This type of port is only allowed to communicate with P ports – they are “stub”. This typ of ports usually connects to hosts.
Isolated (I) : This type of port is only allowed to communicate with P ports – they are “stub”. This typ of ports usually connects to hosts.
https://learningnetwork.cisco.com/docs/DOC-16110
NEW QUESTION 17
A data breach has occurred and your company database has been copied. Which security principle has been violated?
- A. confidentiality
- B. availability
- C. access
- D. control
Answer: A
Explanation:
Confidentiality: There are two types of data: data in motion as it moves across the network; and data at rest, when data is sitting on storage media (server, local workstation, in the cloud, and so forth). Confidentiality means that only the authorized individuals/ systems can view sensitive or classified information.
Source: Cisco Official Certification Guide, Confidentiality, Integrity, and Availability, p.6
NEW QUESTION 18
Which three ESP fields can be encrypted during transmission? (Choose three.)
- A. Security Parameter Index
- B. Sequence Number
- C. MAC Address
- D. Padding
- E. Pad Length
- F. Next Header
Answer: DEF
NEW QUESTION 19
What port option in a PVLAN that can communicate with every other port?
- A. Promiscuous ports
- B. Community ports
- C. Ethernet ports
- D. Isolate ports
Answer: A
Explanation:
+ Promiscuous -- A promiscuous port belongs to the primary VLAN. The promiscuous port can communicate with all interfaces, including the community and isolated host ports, that belong to those secondary VLANs associated to the promiscuous port and associated with the primary VLAN.
+ Isolated -- An isolated port is a host port that belongs to an isolated secondary VLAN. This port has complete isolation from other ports within the same private VLAN domain, except that it can communicate with associated promiscuous ports
+Community -- A community port is a host port that belongs to a community secondary VLAN. Community ports communicate with other ports in the same community VLAN and with associated promiscuous ports Source: http://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus5000/sw/configuration/guide/cli/ CLIConfigurationGuide/PrivateVLANs.html
NEW QUESTION 20
Which two attack types can be prevented with the implementation of a Cisco IPS solution? (Choose two)
- A. ARP spoofing
- B. DDoS
- C. VLAN hopping
- D. man-in-the-middle
- E. worms
Answer: BE
NEW QUESTION 21
By which kind of threat is the victim tricked into entering username and password information at a disguised website?
- A. Spoofing
- B. Malware
- C. Spam
- D. Phishing
Answer: D
Explanation:
Phishing presents a link that looks like a valid trusted resource to a user. When the user clicks it, the user is prompted to disclose confidential information such as usernames/passwords.
Source: Cisco Official Certification Guide, Table 1-5 Attack Methods, p.13
NEW QUESTION 22
Drag the hash or algorithm from the left column to its appropriate category on the right.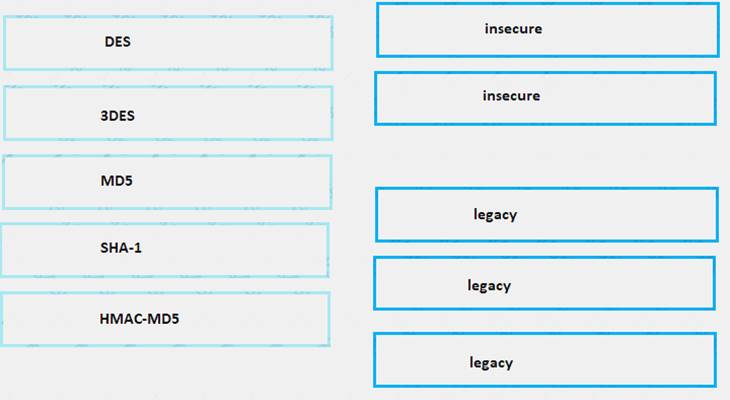
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
https://www.cisco.com/c/en/us/about/security-center/next-generation-cryptography.html
NEW QUESTION 23
What command can you use to verify the binding table status?
- A. show ip dhcp snooping database
- B. show ip dhcp snooping binding
- C. show ip dhcp snooping statistics
- D. show ip dhcp pool
- E. show ip dhcp source binding
- F. show ip dhcp snooping
Answer: A
Explanation:
A device's burned-in address is its MAC address. So by changing it to something else may trick hosts on the network into sending packets to it.
NEW QUESTION 24
Which of the following commands result in a secure bootset? (Choose all that apply.)
- A. secure boot-set
- B. secure boot-config
- C. secure boot-files
- D. secure boot-image
Answer: BD
NEW QUESTION 25
Which type of attack can exploit design flaws in the implementation of an application without going noticed?
- A. Volume-based DDoS attacks.
- B. application DDoS flood attacks.
- C. DHCP starvation attacks
- D. low-rate DoS attacks
Answer: D
NEW QUESTION 26
How can FirePOWER block malicious email attachments?
- A. It forwards email requests to an external signature engine.
- B. It scans inbound email messages for known bad URLs.
- C. It sends the traffic through a file policy.
- D. It sends an alert to the administrator to verify suspicious email messages.
Answer: C
Explanation:
A file policy is a set of configurations that the system uses to perform advanced malware protection and file control, as part of your overall access control configuration.
A file policy, like its parent access control policy, contains rules that determine how the system handles files that match the conditions of each rule. You can configure separate file rules to take different actions for different file types, application protocols, or directions of transfer.
You can associate a single file policy with an access control rule whose action is Allow, Interactive Block, or Interactive Block with reset. The system then uses that file policy to inspect network traffic that meets the conditions of the access control rule.
Source:
http://www.cisco.com/c/en/us/td/docs/security/firesight/541/firepower-module-user-guide/asa-firepower- module-user-guide-v541/AMP-Config.html
NEW QUESTION 27
......
P.S. Certshared now are offering 100% pass ensure 210-260 dumps! All 210-260 exam questions have been updated with correct answers: https://www.certshared.com/exam/210-260/ (481 New Questions)
