Your success in CompTIA 220-1002 is our sole target and we develop all our 220-1002 braindumps in a way that facilitates the attainment of this target. Not only is our 220-1002 study material the best you can find, it is also the most detailed and the most updated. 220-1002 Practice Exams for CompTIA CompTIA Other Exam 220-1002 are written to the highest standards of technical accuracy.
Free 220-1002 Demo Online For CompTIA Certifitcation:
NEW QUESTION 1
Joe, a user, reports that several of his colleagues have received a suspicious email from his account that he did not send. A technician asks one of the colleagues to forward the email for inspection. After ruling out spoofing, the technician verifies the email originated from the corporate email server.
Which of the following is the FIRST step the technician should take to correct this issue?
- A. See if Joe’s email address has been blacklisted
- B. Change the password on Joe’s email account
- C. Update the antivirus and perform a full scan on the PC
- D. Isolate Joe’s computer from the network
Answer: D
NEW QUESTION 2
Joe. a customer, requests to have a technician rename his laptop to the name of his favorite sports team. Which of the following documents MUST the technician consider before performing this action?
- A. Acceptable use policy
- B. Inventory management
- C. EULA
- D. MDM policy
Answer: B
NEW QUESTION 3
A technician responds to a call from a user who claims to have a virus on a workstation. The technician observes the following notification from the system tray:
There are 1033 infected files on this computer. Click here to disinfect.
The link is blocked by the corporate content filter and displays a message stating the site contains known malware. Which of the following should the technician complete to secure the computer with MINIMAL impact to the user?
- A. Compare the startup items and services to a known clean image, and remove any startup items not found in the other imag
- B. Run an anti-malware scan.
- C. Validate that the alerts are false positives, and disable security software on the workstation to prevent further false notifications.
- D. Back up the user’s file
- E. Restore the system to the original system image designated by corporate IT policie
- F. Restore the user’s files.
- G. Request a content filter exception to allow access to the link from the notificatio
- H. Once available, follow the instructions on the linked site.
Answer: A
NEW QUESTION 4
Which of the following features has undergone the most significant changes from Windows 7 to Windows 10 and greatly simplified the operating system installation process?
- A. Driver detection
- B. Metro interface
- C. Account control
- D. PXE installation
Answer: A
NEW QUESTION 5
A junior Linux system administrator needs to update system software. Which of the following shell commands would allow the administrator to gain the necessary permissions to update the software?
- A. sudo
- B. chmod
- C. grep
- D. pwd
Answer: A
NEW QUESTION 6
A technician has set up a new computer for a customer and needs to add a login with administrative privileges. Which of the following tools should the technician use?
- A. Component Services
- B. System Configuration
- C. Security Policy
- D. Local Users and Groups
Answer: D
NEW QUESTION 7
A small office calls a technician to investigate some “invalid certificate” errors from a concerned user. The technician observes that whenever the user to access a secure website from the Windows desktop, this error is encountered. No other users in the office are experiencing this error. Which of the following should the technician do NEXT? (Choose two.)
- A. Remove any proxy servers configured on the user’s browsers.
- B. Assist the user with purchasing an SSL certificate and save the certificate to the desktop.
- C. Disable the SPI firewall on the office’s gateway and any other routers.
- D. Instruct the user to ignore the certificate error since the user is connecting to a secure website.
- E. Create an outbound rule in Windows Firewall named after the user’s homepage.
- F. Run anti-malware scans and download the latest Windows updates.
Answer: AF
NEW QUESTION 8
A MAC user’s operating system became corrupted, and files were deleted after malware was downloaded. The user needs to access the data that was previously stored on the MAC. Which of the following built-in utilities should be used?
- A. Time Machine
- B. Snapshot
- C. System Restore
- D. Boot Camp
Answer: A
NEW QUESTION 9
A SOHO user reports desktop applications are performing slowly, and no emails have been received all morning. A technician remotes in and determines Internet pages’ load slowly or not at all, CPU performance is normal, and the local router can successfully ping.
The remote connection drops periodically. Which of the following steps should the technician take NEXT to resolve the problem?
- A. Reboot into safe mode, uninstall the latest OS update, and run a repair on the OS
- B. Update the antivirus software, run an antivirus scan, verify the browser settings, and check all email settings
- C. Reboot to BIOS setup, verify the TPM is enabled, and start a System Restore from safe mode
- D. Send a test email, open a command prompt to check the file system, and empty the browser cache
Answer: B
NEW QUESTION 10
A user’s mobile device appears to be losing battery life rapidly and often feels warm to the touch, even when it is put away.
The device is relatively new, so the user is concerned it is defective. A technician inspects the device and see the following:
Which of the following should be changed to resolve this issue?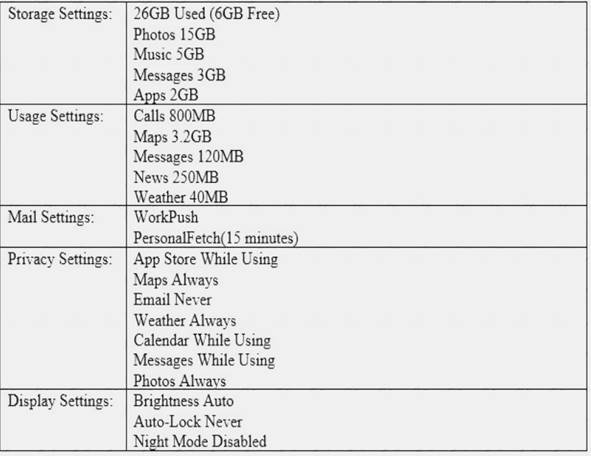
- A. Privacy – Maps
- B. Display – Brightness
- C. Storage – Photos
- D. Mail – Work
Answer: B
NEW QUESTION 11
When a user browses to a favorite website on a Windows laptop, a different website opens. A technician installs an additional web browser, but it also opens to the same unfamiliar site. The technician resets the web browser settings back to default, but the issue persists. Which of the following troubleshooting steps should the technician complete NEXT?
- A. Change the browser’s home page
- B. Check the Windows host file
- C. Update the default web browser
- D. Restore Windows to a previous date
Answer: B
NEW QUESTION 12
A user reports that when opening a web browser the initial page loads to a search engine the user does not recognize When the user performs searches on the site, the results are often irrelevant, and there are many pop-ups Which of the following should a technician do to resolve these issues? (Select TWO)
- A. Reset the user’s browser to default settings
- B. Delete the user’s cached images, temporary files, and cookies
- C. Reboot the user’s computer and install a secondary antivirus
- D. Convince the user to use a different web browser that is currently unaffected
- E. Download the update to the user’s web browser of choice
- F. Remove any unapproved applications from the user’s startup items
Answer: AF
NEW QUESTION 13
A technician performs a virus cleaning on a computer that has been redirecting all browsers to a phishing website. System Restore was turned off before the cleaning. The technician runs the machine through several scanners, and then tests for redirection. A smaller number of sites are still redirecting to the phishing website. The antivirus software correctly blocks the website. Which of the following should the technician do NEXT?
- A. Check the contents of the hosts file
- B. Do a System Restore to a date before the infection
- C. Rerun the antivirus scan with higher sensitivity
- D. Rebuild the OS on the machine
Answer: A
NEW QUESTION 14
Which of the following is the amount of memory a user is limited to with a 32-bit version of Windows?
- A. 2GB
- B. 4GB
- C. 8GB
- D. 16GB
Answer: B
NEW QUESTION 15
Which of the following encryption methods is used by WPA2 to improve data security as compared to previous wireless encryption protocols?
- A. AES
- B. TKIP
- C. S/MIME
- D. 3DES
Answer: A
NEW QUESTION 16
A user is working on a shared computer and attempts to open the email application, which freezes when opened. A technician logs into the computer, and the email application works without issue. The technician has the user log back in, but the application still freezes when opened. Which of the following is the NEXT step the technician should take to resolve the issue?
- A. Check for and apply software updates
- B. Perform repair installation on the application
- C. Add the user to the local administrators group
- D. Rebuild the user’s mail profile
Answer: D
NEW QUESTION 17
A technician is installing the latest OS on a user’s system. The user wants all of the settings and file to remain intact during the installation.
Which of the following upgrade methods should the technician use?
- A. network installation
- B. clean install
- C. in-place upgrade
- D. image deployment
Answer: C
NEW QUESTION 18
A manager requests remote access to a server after hours and on weekends to check data. The manager insists on using the server. Before granting the access, which of the following is the MOST important step a technician can take to protect against possible infection?
- A. Create a policy to remove Internet access from the server during off hours
- B. Set the local antivirus software on the server to update and scan daily
- C. Ensure the server is patched with the latest security updates
- D. Educate the manager on safe Internet browsing practices
Answer: C
NEW QUESTION 19
A user is trying to install a very large .dmg file on a Windows computer but is receiving an error message. Which of the following is causing the error?
- A. Small hard drive
- B. Insufficient RAM
- C. OS compatibility
- D. Folder permissions
Answer: C
NEW QUESTION 20
A technician repaired a laptop for a customer. The customer then complained the repair took too long and questioned the steps the technician took to fix the problem. Which of the following should the technician do NEXT?
- A. Provide documentation of the repair to the customer
- B. Allow the customer to voice concerns and post the story to social media later
- C. Inform the customer the job is done and return to the office
- D. Defend each step and why it was necessary
Answer: A
NEW QUESTION 21
A network administrator has given a technician documentation detailing the switchports the technician will need to patch in for a network upgrade. Which of the following documents did the network administrator MOST likely give to the technician?
- A. Process diagram
- B. Physical network diagram
- C. Fiber backbone diagram
- D. Logical topology diagram
Answer: B
NEW QUESTION 22
A technician is troubleshooting a print issue on a Windows computer and want to disable the printer to test a theory, Which of the following should the technician use to accomplish this?
- A. Devices and Printer
- B. Sync Center
- C. Device Manager
- D. Power Option
Answer: D
NEW QUESTION 23
After a security audit, a technician is tasked with implementing new measures to help secure company workstations. The new policy states that all workstations must be signed off at night, a password is necessary to boot the computer, and encryption must be enabled. Which of the following features should the technician implement to BEST meet these requirements? (Choose three.)
- A. Screen locks
- B. Screensaver passwords
- C. UEFI passwords
- D. Login time restrictions
- E. Strong passwords
- F. Multifactor authentication
- G. BitLocker
- H. Credential Manager
- I. Smart card
- J. Biometric authentication
Answer: ABG
NEW QUESTION 24
Joe, a customer, calls a technician to report a remote computer is demonstrating erratic behavior while he is working on it. The technician verifies the files and directories. Joe is working on locally cannot be opened in any application, and the computer is running extremely slow. Which of the following is the MOST likely cause of this issue?
- A. Files disappearing
- B. File permission changes
- C. Application crash
- D. Too many startup items
Answer: D
NEW QUESTION 25
A user’s Windows laptop has become consistently slower over time. The technician checks the CPU utilization and sees that it varies between 95% and 100%. After the technician closes some running applications, the CPU utilization drops to approximately 20%, and the laptop runs much faster. The next day the same user calls again with the same problem. Which of the following is a tool the technician can use to resolve the issue?
- A. Task Manager
- B. MSTSC
- C. MSConfig
- D. PerfMon
Answer: A
NEW QUESTION 26
A customer's computer is powered on and working, but the customer is unable to get to any wired network resources, shared drives, printers, or the Internet. Which of the following command-line tools should be used to troubleshoot this scenario?
- A. Ping
- B. Iwconfig
- C. Nbtstat
- D. Nslookup
Answer: A
NEW QUESTION 27
A technician has identified malware on a user’s system. Which of the following should the technician do NEXT according to malware removal best practices?
- A. Enable System Restore and create a restore point so no data is lost
- B. Educate the user about how to avoid malware in the future
- C. Update the antivirus software and run a full system scan
- D. Move the infected system to a lab with no network connectivity
Answer: D
NEW QUESTION 28
Which of the following is a reason to use WEP over WPA?
- A. Device compatibility
- B. Increased security
- C. TACACS
- D. Multifactor authentication
Answer: B
NEW QUESTION 29
A user’s smartphone is making the camera shutter noise even when the user is not taking pictures. When the user opens the photo album, there are no new pictures. Which of the following steps should be taken FIRST to determine the cause of the issue?
- A. Uninstall the camera application
- B. Check the application permissions
- C. Reset the phone to factory settings
- D. Update all of the applications on the phone
- E. Run any pending OS updates
Answer: B
NEW QUESTION 30
......
Thanks for reading the newest 220-1002 exam dumps! We recommend you to try the PREMIUM Thedumpscentre.com 220-1002 dumps in VCE and PDF here: https://www.thedumpscentre.com/220-1002-dumps/ (188 Q&As Dumps)
