It is impossible to pass EC-Council 312-50v10 exam without any help in the short term. Come to Passleader soon and find the most advanced, correct and guaranteed EC-Council 312-50v10 practice questions. You will get a surprising result by our Renewal Certified Ethical Hacker v10 practice guides.
Free demo questions for EC-Council 312-50v10 Exam Dumps Below:
NEW QUESTION 1
You have compromised a server and successfully gained a root access. You want to pivot and pass traffic undetected over the network and evade any possible Intrusion Detection System.
What is the best approach?
- A. Install Cryptcat and encrypt outgoing packets from this server.
- B. Install and use Telnet to encrypt all outgoing traffic from this server.
- C. Use Alternate Data Streams to hide the outgoing packets from this server.
- D. Use HTTP so that all traffic can be routed via a browser, thus evading the internal Intrusion Detection Systems.
Answer: A
Explanation:
Cryptcat enables us to communicate between two systems and encrypts the communication between them with twofish.
References:
http://null-byte.wonderhowto.com/how-to/hack-like-pro-create-nearly-undetectable-backdoor-with-cryptcat-014
NEW QUESTION 2
Which of the following is the BEST way to protect Personally Identifiable Information (PII) from being exploited due to vulnerabilities of varying web applications?
- A. Use cryptographic storage to store all PII
- B. Use full disk encryption on all hard drives to protect PII
- C. Use encrypted communications protocols to transmit PII
- D. Use a security token to log into all Web applications that use PII
Answer: C
NEW QUESTION 3
It is a regulation that has a set of guidelines, which should be adhered to by anyone who handles any electronic medical data. These guidelines stipulate that all medical practices must ensure that all necessary measures are in place while saving, accessing, and sharing any electronic medical data to keep patient data secure.
Which of the following regulations best matches the description?
- A. HIPAA
- B. ISO/IEC 27002
- C. COBIT
- D. FISMA
Answer: A
Explanation:
The HIPAA Privacy Rule regulates the use and disclosure of Protected Health Information (PHI) held by "covered entities" (generally, health care clearinghouses, employer sponsored health plans, health insurers, and medical service providers that engage in certain transactions.)[15] By regulation, the Department of Health and Human Services extended the HIPAA privacy rule to independent contractors of covered entities who fit within the definition of "business associates".
References: https://en.wikipedia.org/wiki/Health_Insurance_Portability_and_Accountability_Act#Privacy_Rule
NEW QUESTION 4
The Open Web Application Security Project (OWASP) testing methodology addresses the need to secure web applications by providing which one of the following services?
- A. An extensible security framework named COBIT
- B. A list of flaws and how to fix them
- C. Web application patches
- D. A security certification for hardened web applications
Answer: B
NEW QUESTION 5
An organization hires a tester to do a wireless penetration test. Previous reports indicate that the last test did not contain management or control packets in the submitted traces. Which of the following is the most likely reason for lack of management or control packets?
- A. The wireless card was not turned on.
- B. The wrong network card drivers were in use by Wireshark.
- C. On Linux and Mac OS X, only 802.11 headers are received in promiscuous mode.
- D. Certain operating systems and adapters do not collect the management or control packets.
Answer: D
NEW QUESTION 6
What kind of detection techniques is being used in antivirus softwares that identifies malware by collecting data from multiple protected systems and instead of analyzing files locally it's made on the premiers
environment-
- A. VCloud based
- B. Honypot based
- C. Behaviour based
- D. Heuristics based
Answer: A
NEW QUESTION 7
You are performing a penetration test. You achieved access via a buffer overflow exploit and you proceed to find interesting data, such as files with usernames and passwords. You find a hidden folder that has the administrator's bank account password and login information for the administrator's bitcoin account.
What should you do?
- A. Report immediately to the administrator
- B. Do not report it and continue the penetration test.
- C. Transfer money from the administrator's account to another account.
- D. Do not transfer the money but steal the bitcoins.
Answer: A
NEW QUESTION 8
Which of the following open source tools would be the best choice to scan a network for potential targets?
- A. NMAP
- B. NIKTO
- C. CAIN
- D. John the Ripper
Answer: A
NEW QUESTION 9
Which of the following statements is TRUE?
- A. Sniffers operate on Layer 2 of the OSI model
- B. Sniffers operate on Layer 3 of the OSI model
- C. Sniffers operate on both Layer 2 & Layer 3 of the OSI model.
- D. Sniffers operate on the Layer 1 of the OSI model.
Answer: A
NEW QUESTION 10
A security analyst is performing an audit on the network to determine if there are any deviations from the security policies in place. The analyst discovers that a user from the IT department had a dial-out modem installed. Which security policy must the security analyst check to see if dial-out modems are allowed?
- A. Firewall-management policy
- B. Acceptable-use policy
- C. Remote-access policy
- D. Permissive policy
Answer: C
NEW QUESTION 11
In the context of password security, a simple dictionary attack involves loading a dictionary file (a text file full of dictionary words) into a cracking application such as L0phtCrack or John the Ripper, and running it against user accounts located by the application. The larger the word and word fragment selection, the more effective the dictionary attack is. The brute force method is the most inclusive, although slow. It usually tries every possible letter and number combination in its automated exploration. If you would use both brute force and dictionary methods combined together to have variation of words, what would you call such an attack?
- A. Full Blown
- B. Thorough
- C. Hybrid
- D. BruteDics
Answer: C
NEW QUESTION 12
On performing a risk assessment, you need to determine the potential impacts when some of the critical business process of the company interrupt its service. What is the name of the process by which you can determine those critical business?
- A. Risk Mitigation
- B. Emergency Plan Response (EPR)
- C. Disaster Recovery Planning (DRP)
- D. Business Impact Analysis (BIA)
Answer: D
NEW QUESTION 13
What is the term coined for logging, recording and resolving events in a company?
- A. Internal Procedure
- B. Security Policy
- C. Incident Management Process
- D. Metrics
Answer: C
NEW QUESTION 14
An LDAP directory can be used to store information similar to a SQL database. LDAP uses a database structure instead of SQL’s structure. Because of this, LDAP has difficulty representing many-to-one relationships.
- A. Relational, Hierarchical
- B. Strict, Abstract
- C. Hierarchical, Relational
- D. Simple, Complex
Answer: C
NEW QUESTION 15
Employees in a company are no longer able to access Internet web sites on their computers. The network administrator is able to successfully ping IP address of web servers on the Internet and is able to open web sites by using an IP address in place of the URL. The administrator runs the nslookup command for www.eccouncil.org and receives an error message stating there is no response from the server. What should the administrator do next?
- A. Configure the firewall to allow traffic on TCP ports 53 and UDP port 53.
- B. Configure the firewall to allow traffic on TCP ports 80 and UDP port 443.
- C. Configure the firewall to allow traffic on TCP port 53.
- D. Configure the firewall to allow traffic on TCP port 8080.
Answer: A
NEW QUESTION 16
A certified ethical hacker (CEH) completed a penetration test of the main headquarters of a company almost two months ago, but has yet to get paid. The customer is suffering from financial problems, and the CEH is worried that the company will go out of business and end up not paying. What actions should the CEH take?
- A. Threaten to publish the penetration test results if not paid.
- B. Follow proper legal procedures against the company to request payment.
- C. Tell other customers of the financial problems with payments from this company.
- D. Exploit some of the vulnerabilities found on the company webserver to deface it.
Answer: B
NEW QUESTION 17
What do Trinoo, TFN2k, WinTrinoo, T-Sight, and Stracheldraht have in common?
- A. All are hacking tools developed by the legion of doom
- B. All are tools that can be used not only by hackers, but also security personnel
- C. All are DDOS tools
- D. All are tools that are only effective against Windows
- E. All are tools that are only effective against Linux
Answer: C
NEW QUESTION 18
The following is an entry captured by a network IDS. You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel processor. You figure that the attacker is attempting a buffer overflow attack.
You also notice "/bin/sh" in the ASCII part of the output. As an analyst what would you conclude about the attack?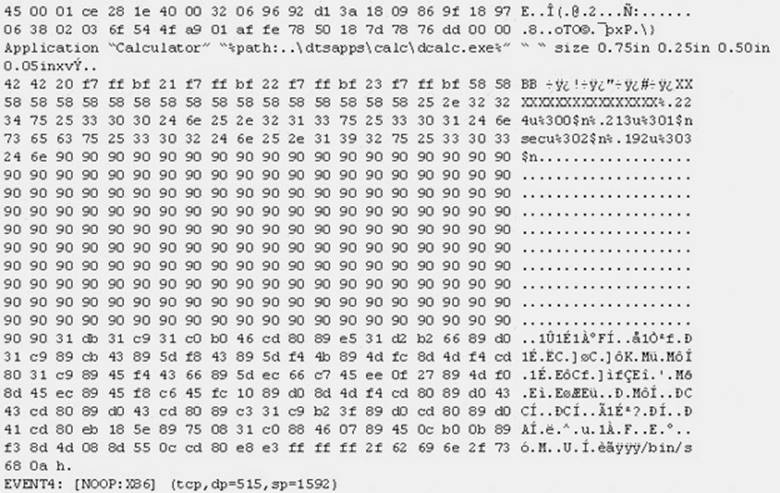
- A. The buffer overflow attack has been neutralized by the IDS
- B. The attacker is creating a directory on the compromised machine
- C. The attacker is attempting a buffer overflow attack and has succeeded
- D. The attacker is attempting an exploit that launches a command-line shell
Answer: D
NEW QUESTION 19
Which of the following is an advantage of utilizing security testing methodologies to conduct a security audit?
- A. They provide a repeatable framework.
- B. Anyone can run the command line scripts.
- C. They are available at low cost.
- D. They are subject to government regulation.
Answer: A
NEW QUESTION 20
The following are types of Bluetooth attack EXCEPT ?
- A. Bluejacking
- B. Bluesmaking
- C. Bluesnarfing
- D. Bluedriving
Answer: D
NEW QUESTION 21
You have the SOA presented below in your Zone.
Your secondary servers have not been able to contact your primary server to synchronize information. How long will the secondary servers attempt to contact the primary server before it considers that zone is dead and stops responding to queries?
collegae.edu.SOA, cikkye.edu ipad.college.edu. (200302028 3600 3600 604800 3600)
- A. One day
- B. One hour
- C. One week
- D. One month
Answer: C
NEW QUESTION 22
International Organization for Standardization (ISO) standard 27002 provides guidance for compliance by outlining
- A. guidelines and practices for security controls.
- B. financial soundness and business viability metrics.
- C. standard best practice for configuration management.
- D. contract agreement writing standards.
Answer: A
NEW QUESTION 23
Which protocol and port number might be needed in order to send log messages to a log analysis tool that resides behind a firewall?
- A. UDP 123
- B. UDP 541
- C. UDP 514
- D. UDP 415
Answer: C
NEW QUESTION 24
Study the snort rule given below: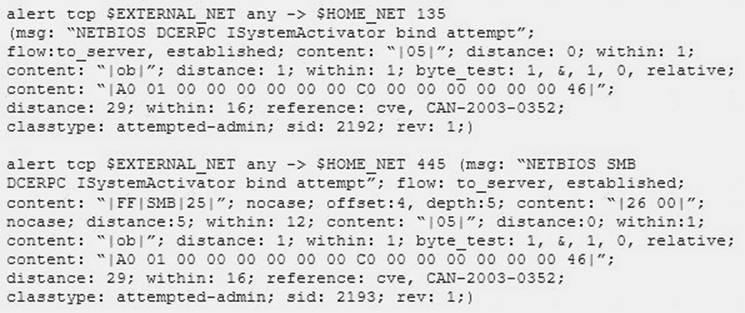
From the options below, choose the exploit against which this rule applies.
- A. WebDav
- B. SQL Slammer
- C. MS Blaster
- D. MyDoom
Answer: C
NEW QUESTION 25
Some passwords are stored using specialized encryption algorithms known as hashes. Why is this an appropriate method?
- A. It is impossible to crack hashed user passwords unless the key used to encrypt them is obtained.
- B. If a user forgets the password, it can be easily retrieved using the hash key stored by administrators.
- C. Hashing is faster compared to more traditional encryption algorithms.
- D. Passwords stored using hashes are non-reversible, making finding the password much more difficult.
Answer: D
NEW QUESTION 26
Every company needs a formal written document which spells out to employees precisely what they are allowed to use the company's systems for, what is prohibited, and what will happen to them if they break the rules. Two printed copies of the policy should be given to every employee as soon as possible after they join the organization. The employee should be asked to sign one copy, which should be safely filed by the company. No one should be allowed to use the company's computer systems until they have signed the policy in acceptance of its terms.
What is this document called?
- A. Information Audit Policy (IAP)
- B. Information Security Policy (ISP)
- C. Penetration Testing Policy (PTP)
- D. Company Compliance Policy (CCP)
Answer: B
NEW QUESTION 27
Name two software tools used for OS guessing? (Choose two.)
- A. Nmap
- B. Snadboy
- C. Queso
- D. UserInfo
- E. NetBus
Answer: AC
NEW QUESTION 28
......
100% Valid and Newest Version 312-50v10 Questions & Answers shared by Certshared, Get Full Dumps HERE: https://www.certshared.com/exam/312-50v10/ (New 736 Q&As)
