Your success in Cisco 350-901 is our sole target and we develop all our 350-901 braindumps in a way that facilitates the attainment of this target. Not only is our 350-901 study material the best you can find, it is also the most detailed and the most updated. 350-901 Practice Exams for Cisco Cisco Other Exam 350-901 are written to the highest standards of technical accuracy.
Online Cisco 350-901 free dumps demo Below:
NEW QUESTION 1
Which two types of storage are supported for app hosting on a Cisco Catalyst 9000 Series Switch? (Choose two.)
- A. external USB storage
- B. internal SSD
- C. CD-ROM
- D. SD-card
- E. bootflash
Answer: AB
NEW QUESTION 2
A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority. Which approach must be taken to secure API keys and passwords?
- A. Embed them directly in the code.
- B. Store them in a hidden file.
- C. Store them inside the source tree of the application.
- D. Change them periodically.
Answer: D
NEW QUESTION 3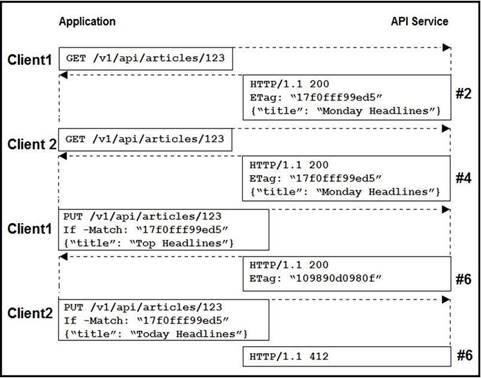
Refer to the exhibit. Two editors are concurrently updating an article’s headline from their mobile devices. What results from this scenario based on this REST API sequence?
- A. The article is marked as “Conflicted”
- B. The article headline is “Monday Headlines”
- C. The article headline is “Today Headlines”
- D. The article headline is “Top Headlines”
Answer: B
NEW QUESTION 4
AppGigabitEthernet interface is used as data port for a container on a Cisco Catalyst 9000 Series Switch. Which two interface configuration options should be used? (Choose two.)
- A. trunk interface
- B. bridged virtual interface
- C. SPAN port
- D. management interface
- E. subinterface
Answer: AC
NEW QUESTION 5
A user is receiving a 429 Too Many Requests error. Which scheme is the server employing that causes this error?
- A. rate limiting
- B. time outs
- C. caching
- D. redirection
Answer: A
NEW QUESTION 6
A developer has completed the implementation of a REST API, but when it is executed, it returns a 401 error message. What must be done on the API to resolve the issue?
- A. Access permission to the resource must be granted, before the request.
- B. Configure new valid credentials.
- C. The requested API endpoint does not exist, and the request URL must be changed.
- D. Additional permission must be granted before the request can submitted.
Answer: D
NEW QUESTION 7
Which snippet presents the correct API call to configure, secure, and enable an SSID using the Meraki API?
- A.
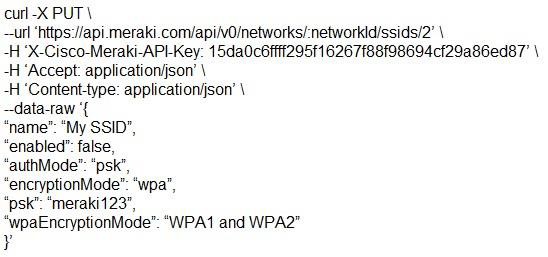
- B.
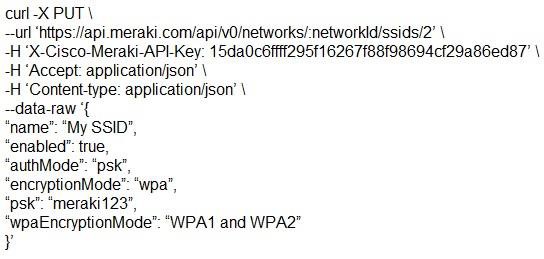
- C.
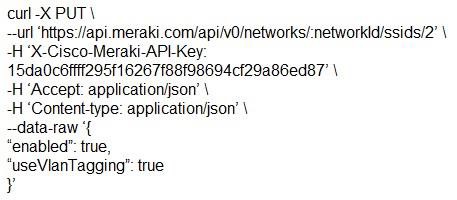
- D.
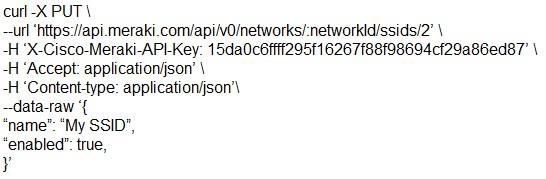
Answer: B
NEW QUESTION 8
The UCS Python SDK includes modules for Service Profile template creation. Which two UCS Service Profile template types are supported? (Choose two.)
- A. initial-template
- B. updating-template
- C. abstract-template
- D. attached-template
- E. base-template
Answer: AB
NEW QUESTION 9
Into which two areas are AppDynamics APIs categorized? (Choose two.)
- A. application-centric
- B. analytics-events
- C. database-visibility
- D. platform-side
- E. agent-side
Answer: DE
NEW QUESTION 10
Refer to the exhibit. An application uses an API to periodically sync a large data set. Based on the HTTP message sequence provided, which statements are true about the caching behavior seen in the scenario? (Choose two.)
- A. The full dataset was transmitted to the client twice.
- B. The dataset changed sometime between message #4 and #5.
- C. A partial dataset was transmitted to the client in message #4.
- D. The dataset did not change during the scenario.
- E. Messages #3 and #5 are equivalent.
Answer: AD
NEW QUESTION 11
A developer needs to configure an environment to orchestrate and configure. Which two tools should be used for each task? (Choose two.)
- A. Puppet for orchestration
- B. Terraform for orchestration
- C. Terraform for configuration
- D. Ansible for orchestration
- E. Ansible for configuration
Answer: BE
NEW QUESTION 12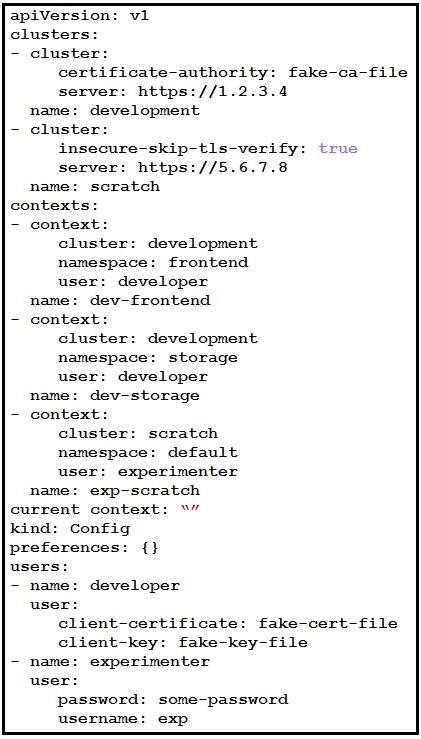
Refer to the exhibit. A kubeconfig file to manage access to clusters is provided. How many clusters are defined and which of them are accessed using username/password authentication versus certificate?
- A. two clusters; scratch
- B. three clusters; scratch
- C. three clusters; development
- D. two clusters; development
Answer: C
NEW QUESTION 13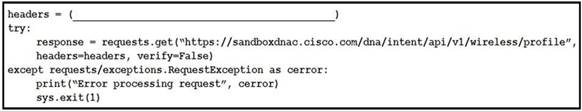
Refer to the exhibit. Which code snippet is required in the headers to successfully authorize wireless information from Cisco DNA Center?
- A. headers = {‘X-auth-token’:’fa8426a0-8eaf-4d22-8e13-7c1b16a9370c’} B.headers = {‘Authorization’:’Basic YWRtaW46R3JhcGV2aW5IMQ==’}
- B. headers = {‘Authorization’:’Bearer ASDNFALKJER23412RKDALSNKF”}
- C. headers = {‘Content-type’:’application/json}
Answer: A
NEW QUESTION 14
A cloud native project is being worked on in which all source code and dependencies are written in Python, Ruby, and/or JavaScnpt. A change in code triggers a notification to the CI/CD tool to run the CI/CD pipeline.
Which step should be omitted from the pipeline?
- A. Deploy the code to one or more environments, such as staging and/or production.
- B. Build one of more containers that package up code and all its dependencies.
- C. Compile code.
- D. Run automated tests to validate the correctness.
Answer: A
NEW QUESTION 15
Which statement about microservices architecture is true?
- A. Applications are written in a single unit.
- B. It is a complex application composed of multiple independent parts.
- C. It is often a challenge to scale individual parts.
- D. A single faulty service can bring the whole application down.
Answer: B
NEW QUESTION 16
Which two situations are flagged by software tools designed for dependency checking in continuous integration environments, such as OWASP? (Choose two.)
- A. publicly disclosed vulnerabilities related to the included dependencies
- B. mismatches in coding styles and conventions in the included dependencies
- C. incompatible licenses in the included dependencies
- D. test case failures introduced by bugs in the included dependencies
- E. buffer overflows to occur as the result of a combination of the included dependencies
Answer: AE
NEW QUESTION 17
DRAG DROP
Drag and drop the characteristics from the left onto the correct data processing techniques on the right, in the context of GDPR.
Select and Place: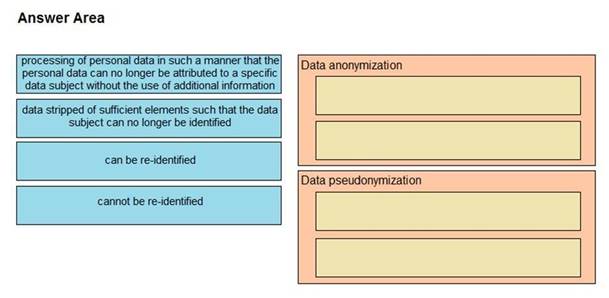
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 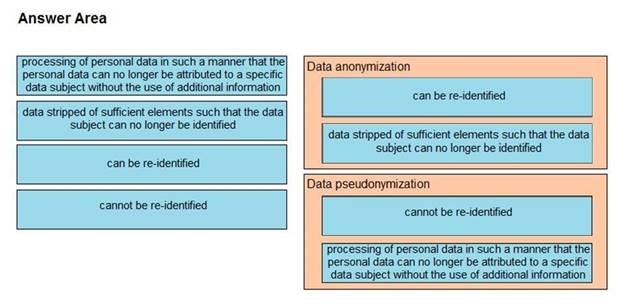
NEW QUESTION 18
Which two statements describe advantages of static code analysis over unit tests? (Choose two.)
- A. It checks for potential tainted data where input is not checked.
- B. It enforces proper coding standards and style.
- C. It performs a quick analysis of whether tests will pass or fail when run.
- D. It checks for race conditions in threaded applications.
- E. It estimates the performance of the code when run.
Answer: BC
NEW QUESTION 19
Refer to the exhibit. Which set of API requests must be executed by a Webex Teams bot after receiving a webhook callback to process messages in a room and reply with a new message back to the same room?
- A.

- B.
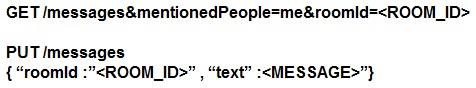
- C.
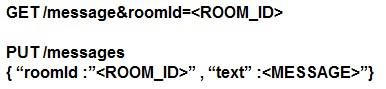
- D.
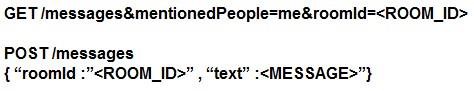
Answer: B
NEW QUESTION 20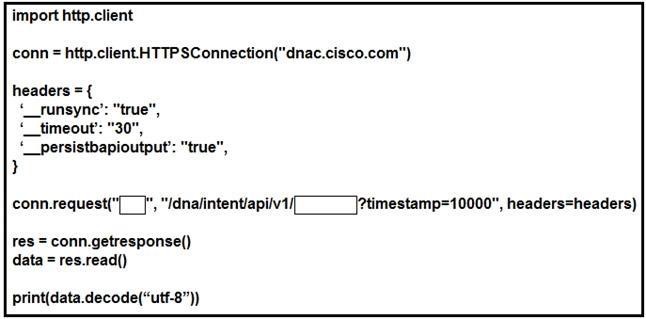
Refer to the exhibit. Which configuration of method and parameter retrieves the health of a laptop connected to the network from Cisco DNA Center?
- A. PUT; network-health;
- B. GET; client-health;
- C. GET; network-device;
- D. POST; network-device;
Answer: C
NEW QUESTION 21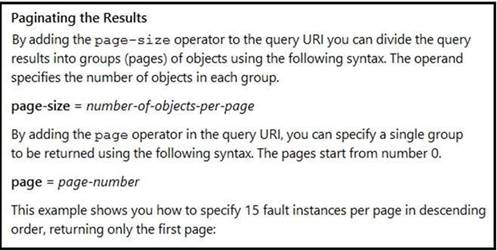
Refer to the exhibit. Many faults have occurred in the ACI environment and a sample of them needs to be examined. Which API call retrieves faults 30 through 45?
- A. GET https://apic-ip-address/api/class/faultInfo.json?order-by=faultinst.severity|desc&page=1&page-size=15
- B. GET https://apic-ip-address/api/class/faultInfo.json?order-by=faultinst.severity|desc&page=2&page-size=15
- C. GET https://apic-ip-address/api/class/faultInfo.json?order-by=faultinst.severity|desc&page=30
- D. GET https://apic-ip-address/api/class/faultInfo.json?order-by=faultinst.severity|desc&page=2&page-size=30
Answer: D
NEW QUESTION 22
While developing an application following the 12-factor app methodology, which approach should be used in the application for logging?
- A. Write a log to a file in the application directory.
- B. Write a log to a file in /var/log.
- C. Write the logs buffered to stdout.
- D. Write the logs unbuffered to stdout.
Answer: D
NEW QUESTION 23
......
P.S. Dumps-hub.com now are offering 100% pass ensure 350-901 dumps! All 350-901 exam questions have been updated with correct answers: https://www.dumps-hub.com/350-901-dumps.html (0 New Questions)
