we provide Realistic EC-Council 412-79v9 exams which are the best for clearing 412-79v9 test, and to get certified by EC-Council EC-Council Certified Security Analyst (ECSA) v9. The 412-79v9 Questions & Answers covers all the knowledge points of the real 412-79v9 exam. Crack your EC-Council 412-79v9 Exam with latest dumps, guaranteed!
Online EC-Council 412-79v9 free dumps demo Below:
NEW QUESTION 1
Why is a legal agreement important to have before launching a penetration test?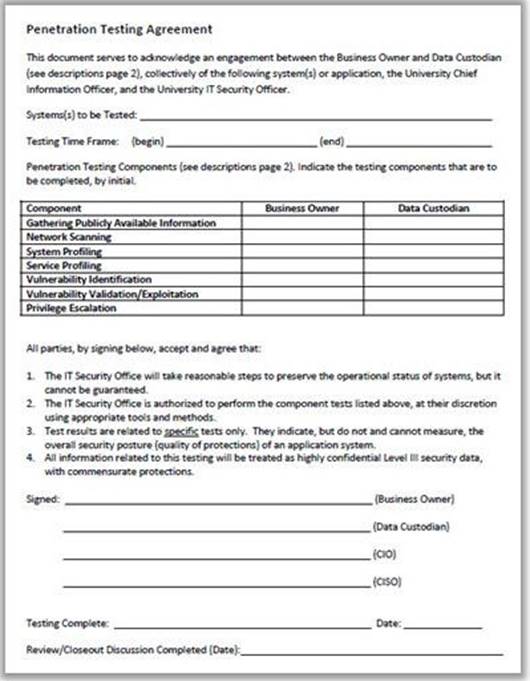
- A. Guarantees your consultant fees
- B. Allows you to perform a penetration test without the knowledge and consent of the organization's upper management
- C. It establishes the legality of the penetration test by documenting the scope of the project and the consent of the company.
- D. It is important to ensure that the target organization has implemented mandatory security policies
Answer: C
NEW QUESTION 2
What are placeholders (or markers) in an HTML document that the web server will dynamically replace with data just before sending the requested documents to a browser?
- A. Server Side Includes
- B. Sort Server Includes
- C. Server Sort Includes
- D. Slide Server Includes
Answer: A
NEW QUESTION 3
What are the scanning techniques that are used to bypass firewall rules and logging mechanisms and disguise themselves as usual network traffic?
- A. Connect Scanning Techniques
- B. SYN Scanning Techniques
- C. Stealth Scanning Techniques
- D. Port Scanning Techniques
Answer: C
Explanation:
Reference: http://wwww.pc-freak.net/tutorials/hacking_info/arkin%20network%20scanning%20techniques.pdf (page 7
NEW QUESTION 4
Rule of Engagement (ROE) is the formal permission to conduct a pen-test. It provides top- level guidance for conducting the penetration testing.
Various factors are considered while preparing the scope of ROE which clearly explain the limits associated with the security test.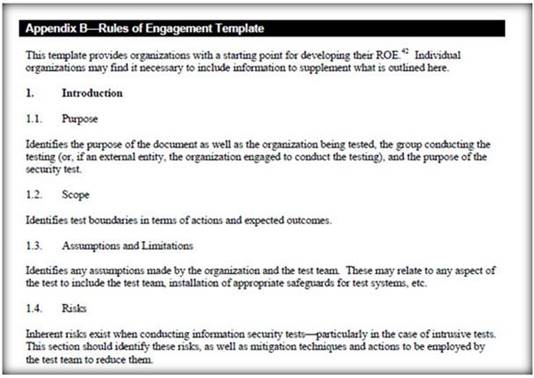
Which of the following factors is NOT considered while preparing the scope of the Rules of Engagment (ROE)?
- A. A list of employees in the client organization
- B. A list of acceptable testing techniques
- C. Specific IP addresses/ranges to be tested
- D. Points of contact for the penetration testing team
Answer: A
NEW QUESTION 5
Which of the following shields Internet users from artificial DNS data, such as a deceptive or mischievous address instead of the genuine address that was requested?
- A. DNSSEC
- B. Firewall
- C. Packet filtering
- D. IPSec
Answer: A
Explanation:
Reference: http://tools.ietf.org/html/draft-osterweil-dane-ipsec-01 (abstract, first para)
NEW QUESTION 6
Which Wireshark filter displays all the packets where the IP address of the source host is 10.0.0.7?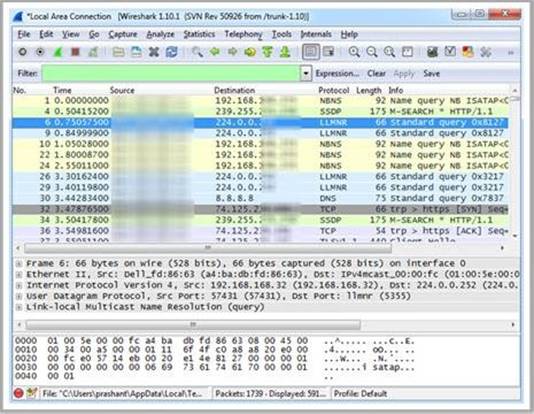
- A. ip.dst==10.0.0.7
- B. ip.port==10.0.0.7
- C. ip.src==10.0.0.7
- D. ip.dstport==10.0.0.7
Answer: C
NEW QUESTION 7
Identify the correct formula for Return on Investment (ROI).
- A. ROI = ((Expected Returns – Cost of Investment) / Cost of Investment) * 100
- B. ROI = (Expected Returns + Cost of Investment) / Cost of Investment
- C. ROI = (Expected Returns Cost of Investment) / Cost of Investment
- D. ROI = ((Expected Returns + Cost of Investment) / Cost of Investment) * 100
Answer: C
Explanation:
Reference: http://www.investopedia.com/terms/r/returnoninvestment.asp
NEW QUESTION 8
Passwords protect computer resources and files from unauthorized access by malicious users. Using passwords is the most capable and effective way to protect information and to increase the security level of a company.
Password cracking is the process of recovering passwords from data that have been stored in or transmitted by a computer system to gain unauthorized access to a system.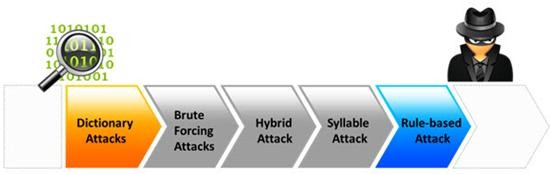
Which of the following password cracking attacks tries every combination of characters until the password is broken?
- A. Brute-force attack
- B. Rule-based attack
- C. Hybrid attack
- D. Dictionary attack
Answer: A
Explanation:
Reference: http://books.google.com.pk/books?id=m2qZNW4dcyIC&pg=PA237&lpg=PA237&dq=passw ord+cracking+attacks+tries+every+combination+of+characters+until+the+password+is+bro ken&source=bl&ots=RKEUUo6LYj&sig=MPEfFBEpoO0yvOwMxYCoPQuqM5g&hl=en&sa= X&ei=ZdwdVJm3CoXSaPXsgPgM&ved=0CCEQ6AEwAQ#v=onepage&q=password%20cr acking%20attacks%20tries%20every%20combination%20of%20characters%20until%20th e%20password%20is%20broken&f=false
NEW QUESTION 9
Before performing the penetration testing, there will be a pre-contract discussion with different pen-testers (the team of penetration testers) to gather a quotation to perform pen testing.
Which of the following factors is NOT considered while preparing a price quote to perform pen testing?
- A. Total number of employees in the client organization
- B. Type of testers involved
- C. The budget required
- D. Expected time required to finish the project
Answer: A
NEW QUESTION 10
Rules of Engagement (ROE) document provides certain rights and restriction to the test team for performing the test and helps testers to overcome legal, federal, and policy-related restrictions to use different penetration testing tools and techniques.
What is the last step in preparing a Rules of Engagement (ROE) document?
- A. Conduct a brainstorming session with top management and technical teams
- B. Decide the desired depth for penetration testing
- C. Conduct a brainstorming session with top management and technical teams
- D. Have pre-contract discussions with different pen-testers
Answer: C
NEW QUESTION 11
Which of the following methods is used to perform server discovery?
- A. Banner Grabbing
- B. Whois Lookup
- C. SQL Injection
- D. Session Hijacking
Answer: B
Explanation:
Reference: http://luizfirmino.blogspot.com/2011/09/server-discovery.html
NEW QUESTION 12
Which of the following equipment could a pen tester use to perform shoulder surfing?
- A. Binoculars
- B. Painted ultraviolet material
- C. Microphone
- D. All the above
Answer: A
Explanation:
Reference: http://en.wikipedia.org/wiki/Shoulder_surfing_(computer_security)
NEW QUESTION 13
A firewall protects networked computers from intentional hostile intrusion that could compromise confidentiality or result in data corruption or denial of service. It examines all traffic routed between the two networks to see if it meets certain criteria. If it does, it is routed between the networks, otherwise it is stopped.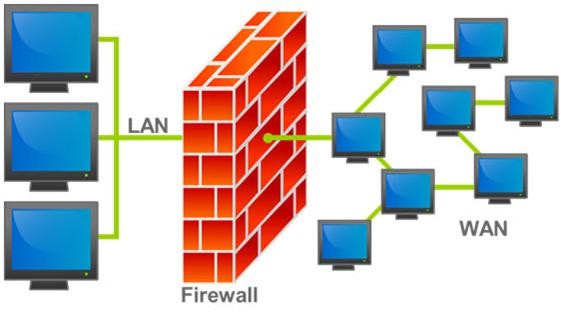
Why is an appliance-based firewall is more secure than those implemented on top of the commercial operating system (Software based)?
- A. Appliance based firewalls cannot be upgraded
- B. Firewalls implemented on a hardware firewall are highly scalable
- C. Hardware appliances does not suffer from security vulnerabilities associated with the underlying operating system
- D. Operating system firewalls are highly configured
Answer: C
NEW QUESTION 14
Which of the following protocol’s traffic is captured by using the filter tcp.port==3389 in the Wireshark tool?
- A. Reverse Gossip Transport Protocol (RGTP)
- B. Real-time Transport Protocol (RTP)
- C. Remote Desktop Protocol (RDP)
- D. Session Initiation Protocol (SIP)
Answer: C
Explanation:
Reference: http://wiki.wireshark.org/RDP
NEW QUESTION 15
Firewall is an IP packet filter that enforces the filtering and security policies to the flowing network traffic. Using firewalls in IPv6 is still the best way of protection from low level attacks at the network and transport layers. Which one of the following cannot handle routing protocols properly?
- A. “Internet-router-firewall-net architecture”
- B. “Internet-firewall-router-net architecture”
- C. “Internet-firewall/router(edge device)-net architecture”
- D. “Internet-firewall -net architecture”
Answer: B
NEW QUESTION 16
Which one of the following tools of trade is a commercial shellcode and payload generator written in Python by Dave Aitel?
- A. Microsoft Baseline Security Analyzer (MBSA)
- B. CORE Impact
- C. Canvas
- D. Network Security Analysis Tool (NSAT)
Answer: C
NEW QUESTION 17
ARP spoofing is a technique whereby an attacker sends fake ("spoofed") Address
Resolution Protocol (ARP) messages onto a Local Area Network. Generally, the aim is to associate the attacker's MAC address with the IP address of another host (such as the default gateway), causing any traffic meant for that IP address to be sent to the attacker instead.
ARP spoofing attack is used as an opening for other attacks.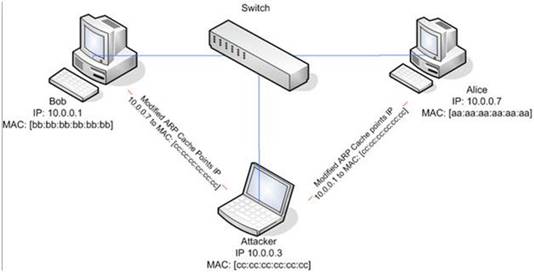
What type of attack would you launch after successfully deploying ARP spoofing?
- A. Parameter Filtering
- B. Social Engineering
- C. Input Validation
- D. Session Hijacking
Answer: D
Explanation:
http://en.wikipedia.org/wiki/ARP_spoofing
NEW QUESTION 18
A pen tester has extracted a database name by using a blind SQL injection. Now he begins to test the table inside the database using the below query and finds the table:
http://juggyboy.com/page.aspx?id=1; IF (LEN(SELECT TOP 1 NAME from sysobjects where xtype='U')=3) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),1,1)))=101) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),2,1)))=109) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),3,1)))=112) WAITFOR DELAY '00:00:10'—
What is the table name?
- A. CTS
- B. QRT
- C. EMP
- D. ABC
Answer: C
NEW QUESTION 19
Application security assessment is one of the activity that a pen tester performs in the attack phase. It is designed to identify and assess threats to the organization through bespoke, proprietary applications or systems. It checks the application so that a malicious user cannot access, modify, or destroy data or services within the system.
Identify the type of application security assessment which analyzes the application-based code to confirm that it does not contain any sensitive information that an attacker might use to exploit an application.
- A. Web Penetration Testing
- B. Functionality Testing
- C. Authorization Testing
- D. Source Code Review
Answer: D
NEW QUESTION 20
SQL injection attack consists of insertion or "injection" of either a partial or complete SQL query via the data input or transmitted from the client (browser) to the web application.
A successful SQL injection attack can: i)Read sensitive data from the database
iii) Modify database data (insert/update/delete)
iii)Execute administration operations on the database (such as shutdown the DBMS) iV)Recover the content of a given file existing on the DBMS file system or write files into the file system
v)Issue commands to the operating system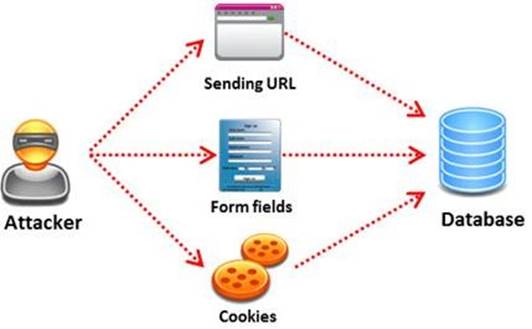
Pen tester needs to perform various tests to detect SQL injection vulnerability. He has to make a list of all input fields whose values could be used in crafting a SQL query, including the hidden fields of POST requests and then test them separately, trying to interfere with the query and to generate an error.
In which of the following tests is the source code of the application tested in a non-runtime environment to detect the SQL injection vulnerabilities?
- A. Automated Testing
- B. Function Testing
- C. Dynamic Testing
- D. Static Testing
Answer: D
Explanation:
Reference: http://ijritcc.org/IJRITCC%20Vol_2%20Issue_5/Removal%20of%20Data%20Vulnerabilities
%20Using%20SQL.pdf
NEW QUESTION 21
Timing is an element of port-scanning that can catch one unaware. If scans are taking too long to complete or obvious ports are missing from the scan, various time parameters may need to be adjusted. Which one of the following scanned timing options in NMAP’s scan is useful across slow WAN links or to hide the scan?
- A. Paranoid
- B. Sneaky
- C. Polite
- D. Normal
Answer: C
NEW QUESTION 22
Which of the following reports provides a summary of the complete pen testing process, its outcomes, and recommendations?
- A. Vulnerability Report
- B. Executive Report
- C. Client-side test Report
- D. Host Report
Answer: B
NEW QUESTION 23
A firewall’s decision to forward or reject traffic in network filtering is dependent upon which of the following?
- A. Destination address
- B. Port numbers
- C. Source address
- D. Protocol used
Answer: D
Explanation:
Reference: http://www.vicomsoft.com/learning-center/firewalls/ (what does a firewall do)
NEW QUESTION 24
Which one of the following is a useful formatting token that takes an int * as an argument, and writes the number of bytes already written, to that location?
- A. “%n”
- B. “%s”
- C. “%p”
- D. “%w”
Answer: A
NEW QUESTION 25
Which of the following policies helps secure data and protects the privacy of organizational information?
- A. Special-Access Policy
- B. Document retention Policy
- C. Cryptography Policy
- D. Personal Security Policy
Answer: C
NEW QUESTION 26
An attacker injects malicious query strings in user input fields to bypass web service authentication mechanisms and to access back-end databases. Which of the following attacks is this?
- A. Frame Injection Attack
- B. LDAP Injection Attack
- C. XPath Injection Attack
- D. SOAP Injection Attack
Answer: D
Explanation:
http://luizfirmino.blogspot.com/2011_09_01_archive.html
NEW QUESTION 27
In a TCP packet filtering firewall, traffic is filtered based on specified session rules, such as when a session is initiated by a recognized computer.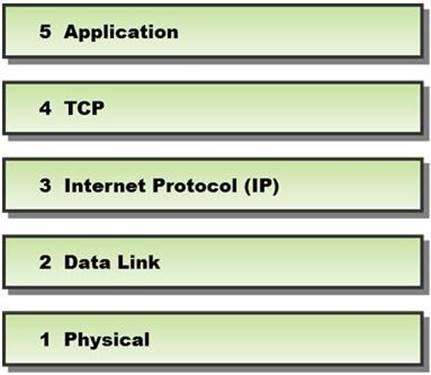
Identify the level up to which the unknown traffic is allowed into the network stack.
- A. Level 5 – Application
- B. Level 2 – Data Link
- C. Level 4 – TCP
- D. Level 3 – Internet Protocol (IP)
Answer: D
Explanation:
Reference: http://books.google.com.pk/books?id=KPjLAyA7HgoC&pg=PA208&lpg=PA208&dq=TCP+packet+filtering+firewall+level+up+to+which+the+unknown+traffic+is+allowed+into+the+network+stack&source=bl&ots=zRrbchVYng&sig=q5G3T8lggTfAMNRkL7Kp0SRslHU&hl=en&sa=X&ei=5PUeVLSbC8TmaMzrgZgC&ved=0CBsQ6AEwAA#v=onepage&q=TCP%20packet%20filtering%20firewall%20level%20up%20to%20which%20the%20unknown%20traffic%20is%20allowed%20into%20the%20network%20stack&f=false
NEW QUESTION 28
Which of the following acts is a proprietary information security standard for organizations that handle cardholder information for the major debit, credit, prepaid, e-purse, ATM, and POS cards and applies to all entities involved in payment card processing?
- A. PIPEDA
- B. PCI DSS
- C. Human Rights Act 1998
- D. Data Protection Act 1998
Answer: B
Explanation:
Reference: http://en.wikipedia.org/wiki/Payment_Card_Industry_Data_Security_Standard
NEW QUESTION 29
......
P.S. Easily pass 412-79v9 Exam with 203 Q&As Certleader Dumps & pdf Version, Welcome to Download the Newest Certleader 412-79v9 Dumps: https://www.certleader.com/412-79v9-dumps.html (203 New Questions)
