we provide Downloadable Microsoft 98-367 exam engine which are the best for clearing 98-367 test, and to get certified by Microsoft MTA Security Fundamentals Practice Test. The 98-367 Questions & Answers covers all the knowledge points of the real 98-367 exam. Crack your Microsoft 98-367 Exam with latest dumps, guaranteed!
Check 98-367 free dumps before getting the full version:
NEW QUESTION 1
An attorney hires you to increase the wireless network security for the law firm's office. The office has a very basic network, with just a modem and a router.
Which of these security modes offers the highest security?
- A. WPA-Personal
- B. WEP
- C. WPA2-Personal
- D. WPA-Enterprise
Answer: C
NEW QUESTION 2
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 3
To protect systems from buffer overflow errors, you can use:
- A. Antivirus software
- B. Data Execution Prevention
- C. A proxy server
- D. An Intruder Prevention System
Answer: B
NEW QUESTION 4
You want to make your computer resistant to online hackers and malicious software. What should you do?
- A. Configure a forward proxy.
- B. Install anti-virus software.
- C. Enable spam filtering.
- D. Turn on Windows Firewall.
Answer: B
NEW QUESTION 5
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.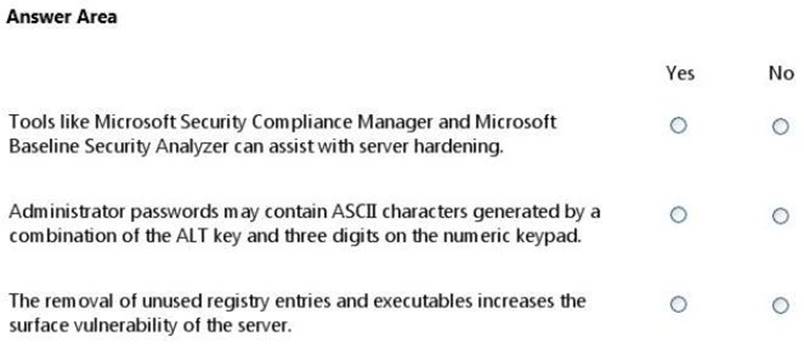
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 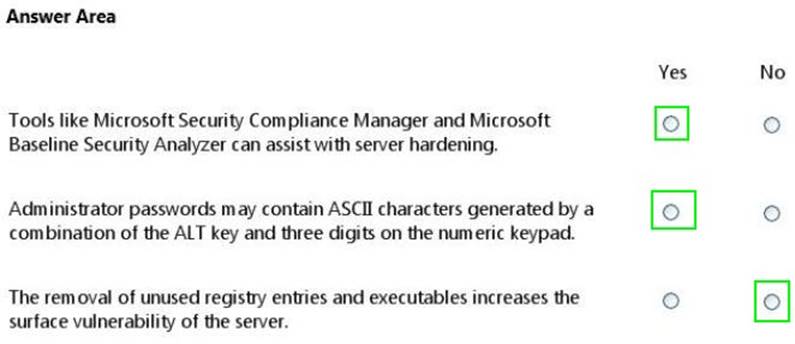
NEW QUESTION 6
A user who receives a large number of emails selling prescription medicine is probably receiving pharming mail.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the underlined text makes the statement correct.
- A. Malware
- B. Spoofed mail
- C. Spam
- D. No change is needed.
Answer: C
NEW QUESTION 7
You are setting up Remote Desktop on your computer. Your computer is a member of a domain.
Your firewall configuration is shown in the following image: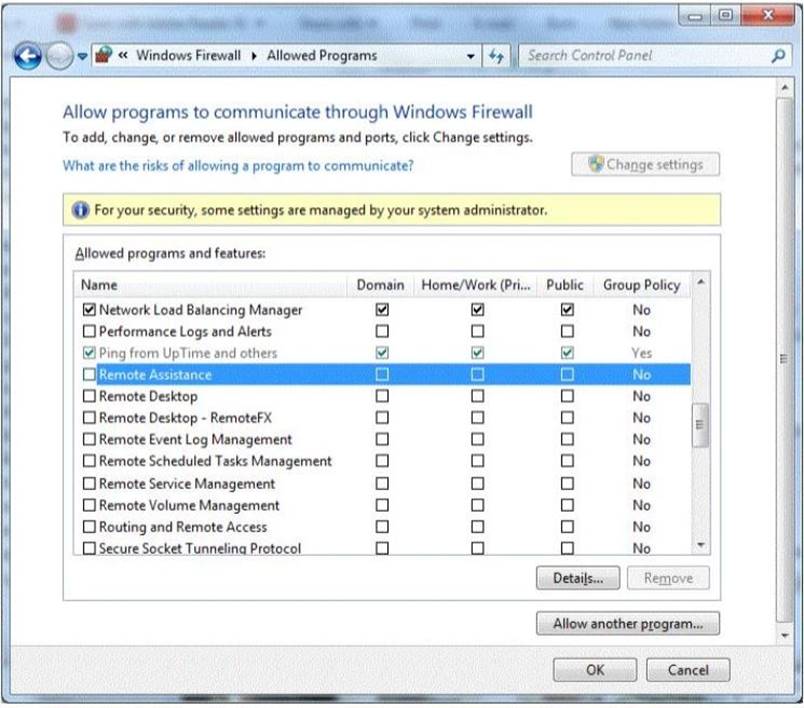
You need to allow Remote Desktop to be able to get through your firewall for users on your company's network.
Which settings should you enable?
- A. Remote Assistance: Home/Work (Private)
- B. Remote Desktop: Public
- C. Remote Desktop: Home/Work (Private)
- D. Remote Assistance: Domain
Answer: A
NEW QUESTION 8
E-mail bombing attacks a specific entity by:
- A. Redirecting all e-mail to another entity
- B. Sending high volumes of e-mail
- C. Tracing e-mail to the destination address
- D. Triggering high levels of security alerts
Answer: B
Explanation:
In Internet usage, an email bomb is a form of net abuse consisting of sending huge volumes of email to an address in an attempt to overflow the mailbox or overwhelm the server where the email address is hosted in a denial-of-service attack.
NEW QUESTION 9
Humongous Insurance is an online healthcare insurance company. During an annual security audit a security firm tests the strength of the company's password policy and suggests that Humongous Insurance implement password history policy.
What is the likely reason that the security firm suggests this?
- A. Past passwords were easily cracked by the brute force method.
- B. Past passwords of users contained dictionary words.
- C. Previous password breaches involved use of past passwords.
- D. Past passwords lacked complexity and special characters.
Answer: B
NEW QUESTION 10
Which three elements does HTTPS encrypt? (Choose three.)
- A. Browser cookies
- B. Server IP address
- C. Port numbers
- D. Website URL
- E. Login information
Answer: ADE
Explanation:
Reference: http://stackoverflow.com/questions/499591/are-https-urls-encrypted
NEW QUESTION 11
Which enables you to change the permissions on a folder?
- A. Take ownership
- B. Extended attributes
- C. Auditing
- D. Modify
Answer: D
NEW QUESTION 12
To prevent users from copying data to removable media, you should:
- A. Lock the computer cases
- B. Apply a group policy
- C. Disable copy and paste
- D. Store media in a locked room
Answer: B
Explanation:
Reference: http://blogs.technet.com/b/askds/archive/2008/08/25/removable-storage-group- policy-and-windows-server-2008-and-windows-vista.aspx
NEW QUESTION 13
Which is a special folder permission?
- A. Read
- B. Modify
- C. Write
- D. Delete
Answer: D
Explanation:
Reference: http://support.microsoft.com/kb/308419
NEW QUESTION 14
How does the sender policy framework (SPF) aim to reduce spoofed email?
- A. It provides a list of IP address ranges for particular domains so senders can be verified.
- B. It includes an XML policy file with each email that confirms the validity of the message.
- C. It lists servers that may legitimately forward mail for a particular domain.
- D. It provides an encryption key so that authenticity of an email message can be validated
Answer: A
NEW QUESTION 15
Password history policies are used to prevent:
- A. Brute force attacks
- B. Users from sharing passwords
- C. Social engineering
- D. Passwords from being reused immediately
Answer: D
Explanation:
This security setting determines the number of unique new passwords that have to be associated with a user account before an old password can be reused. The value must be between 0 and 24 passwords.
This policy enables administrators to enhance security by ensuring that old passwords are not reused continually.
Reference: http://technet.microsoft.com/en-us/library/cc758950(v=ws.10).aspx
NEW QUESTION 16
Bridging is a process of sending packets from source to destination on OSI layer 3.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the underlined text makes the statement correct.
- A. Routing
- B. Switching
- C. Repeating
- D. No change is needed.
Answer: A
NEW QUESTION 17
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 18
HOTSPOT
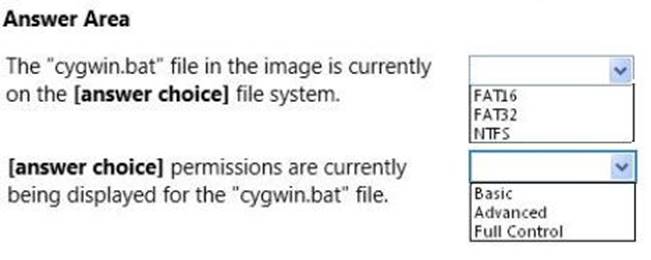
Your supervisor asks you to review file permission settings on the application.bat file. You need to report which file system the file is on and the type of permission the file has. You review the application Properties dialog box shown in the following image: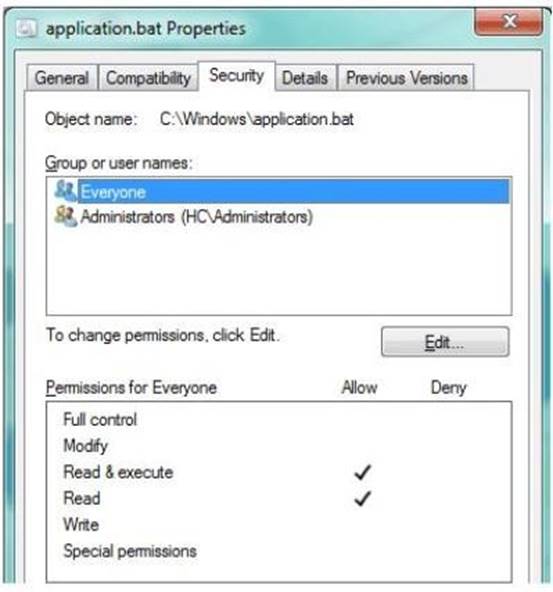
Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 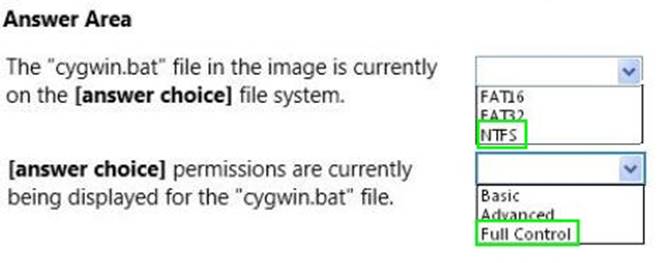
NEW QUESTION 19
A group of users has access to Folder A and all of its contents. You need to prevent some of the users from accessing a subfolder inside Folder A.
What should you do first?
- A. Disable folder sharing
- B. Hide the folder
- C. Change the owner
- D. Block inheritance
Answer: A
NEW QUESTION 20
Which is the minimum requirement to create BitLocker-To-Go media on a client computer?
- A. Windows XP Professional Service Pack 3
- B. Windows Vista Enterprise Edition
- C. Windows 7 Enterprise Edition
- D. Windows 2000 Professional Service Pack 4
Answer: A
NEW QUESTION 21
......
P.S. Easily pass 98-367 Exam with 163 Q&As Dumps-files.com Dumps & pdf Version, Welcome to Download the Newest Dumps-files.com 98-367 Dumps: https://www.dumps-files.com/files/98-367/ (163 New Questions)
