Act now and download your GIAC GISF test today! Do not waste time for the worthless GIAC GISF tutorials. Download Renewal GIAC GIAC Information Security Fundamentals exam with real questions and answers and begin to learn GIAC GISF with a classic professional.
Online GIAC GISF free dumps demo Below:
NEW QUESTION 1
You are concerned about possible hackers doing penetration testing on your network as a prelude to an attack. What would be most helpful to you in finding out if this is occurring?
- A. Examining your firewall logs
- B. Examining your DNS Server logs
- C. Examining your domain controller server logs
- D. Examining your antivirus logs
Answer: A
NEW QUESTION 2
Mark work as a Network Administrator for Roadways Travel Inc. The conmpany wants to implement a strategy for its external employees so that they can connect to Web based applications. What will Mark do to achieve this?
(Click the Exhibit button on the toolbar to see the case study.)
- A. He will install a VPN server in the VLAN, Roadways, and an IIS server in the corporate LAN at the headquarters.
- B. He will install a VPN server in the corporate LAN at the headquarters and an IIS server in the DMZ.
- C. He will install a VPN server in the DMZ and an IIS server in the corporate LAN at the headquarters.
- D. He will install a VPN server in the VLAN, Roadways, and an IIS server in the DMZ.
Answer: C
NEW QUESTION 3
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases.
The email header of the suspicious email is given below: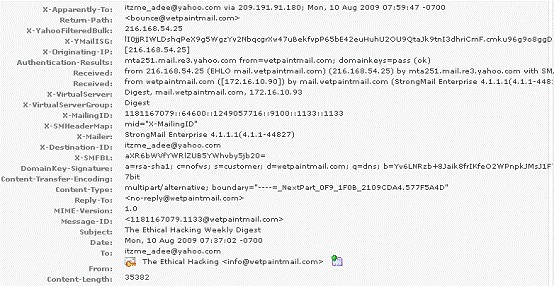
What is the IP address of the sender of this email?
- A. 209.191.91.180
- B. 141.1.1.1
- C. 172.16.10.90
- D. 216.168.54.25
Answer: D
NEW QUESTION 4
According to the case study, what protocol should be used to protect a customer's privacy and credit card information?
(Click the Exhibit button on the toolbar to see the case study.)
- A. L2TP
- B. FTP
- C. HTTP
- D. MS-CHAP
- E. HTTPS
- F. PPTP
Answer: E
NEW QUESTION 5
A company would like your consulting firm to review its current network and suggest changes that will increase its efficiency and optimize the business processes.
To design such a network, you prepare a case study.
Which of the following policies should be implemented through a group policy that is associated with the netperfect.com domain?
(Click the Exhibit button on the toolbar to see the case study.)
Each correct answer represents a complete solution. Choose all that apply.
- A. Account lockout policy.
- B. Password policy.
- C. Limit computers that can access production schedule software.
- D. Assign MS Office suite to appropriate users.
Answer: ABD
NEW QUESTION 6
The new security policy requires you to encrypt all data transmitted from the laptop computers of sales personnel to the distribution centers. How will you implement the security requirements?
(Click the Exhibit button on the toolbar to see the case study.)
- A. Use 40-bit encryption for Routing and Remote Access Service(RRAS) Serve
- B. Use PPTP without packet filtering for VPN.
- C. Use 128-bit encryption for Routing and Remote Access Service(RRAS) Serve
- D. Use PPTP without packet filtering for VPN.
- E. Use 128-bit encryption for Routing and Remote Access Service(RRAS) Serve
- F. Use PPTP with packet filtering for VPN.
- G. Use 40-bit encryption for the Routing and Remote Access Service(RRAS) Serve
- H. Use PPTP with packet filtering for VPN.
Answer: C
NEW QUESTION 7
Peter, a malicious hacker, wants to perform an attack. He first compromises computers distributed across the internet and then installs specialized software on these computers. He then instructs the compromised hosts to execute the attack. Every host can then be used to launch its own attack on the target computers. Which of the following attacks is Peter performing?
- A. Teardrop attack
- B. SYN flood attack
- C. Ping of Death attack
- D. DDoS attack
Answer: D
NEW QUESTION 8
Which of the following technologies is used to detect unauthorized attempts to access and manipulate computer systems locally or through the Internet or an intranet?
- A. Packet filtering
- B. Firewall
- C. Intrusion detection system (IDS)
- D. Demilitarized zone (DMZ)
Answer: C
NEW QUESTION 9
Which of the following are the goals of the cryptographic systems? Each correct answer represents a complete solution. Choose three.
- A. Availability
- B. Authentication
- C. Confidentiality
- D. Integrity
Answer: BCD
NEW QUESTION 10
You work as an executive manager for Mariotx.Inc. You entered into a business contract with a firm called Helfixnet.Inc. You passed on the contract details to Helfixnet.Inc and also got an acceptance approval. You later find that Helfixnet.Inc is violating the rules of the contract and they claim that they had never entered into any contract with Mariotx.Inc when asked. Which of the following directives of Information Assurance can you apply to ensure prevention from such issues?
- A. Confidentiality
- B. Non-repudiation
- C. Data integrity
- D. Data availability
Answer: B
NEW QUESTION 11
You are concerned about outside attackers penetrating your network via your company Web server.
You wish to place your Web server between two firewalls One firewall between the Web server and the outside world The other between the Web server and your network
What is this called?
- A. IDS
- B. SPI firewall
- C. DMZ
- D. Application Gateway firewall
Answer: C
NEW QUESTION 12
You are a Consumer Support Technician. You are helping a user troubleshoot computer- related issues. While troubleshooting the user's computer, you find a malicious program similar to a virus or worm. The program negatively affects the privacy and security of the computer and is capable of damaging the computer. Which of the following alert levels of Windows Defender is set for this program?
- A. Low
- B. High
- C. Severe
- D. Medium
Answer: C
NEW QUESTION 13
Your network utilizes a coax cable for connections between various network segments. Your predecessor made sure none of the coax cables were in an exposed area that could easily be accessed. This caused the use of significant extra cabling. Why do you think this was done?
- A. This was an error you should correc
- B. It wastes the cable and may make maintenance more difficult.
- C. He was concerned about wireless interception of data.
- D. He was concerned about electromagnetic emanation being used to gather data.
- E. He was concerned about vampire taps.
Answer: D
NEW QUESTION 14
You are hired by Techmart Inc. to upgrade its existing network. You have prepared a case study for planning the network.
According to your study, how many domains are required to setup the network of Techmart Inc.?
(Click the Exhibit button on the toolbar to see the case study.)
- A. Two
- B. Four
- C. Three
- D. One
Answer: D
NEW QUESTION 15
You have been assigned the task of selecting a hash algorithm. The algorithm will be specifically used to ensure the integrity of certain sensitive files. It must use a 128 bit hash value. Which of the following should you use?
- A. SHA
- B. AES
- C. MD5
- D. DES
Answer: C
NEW QUESTION 16
Which of the following refers to the process of verifying the identity of a person, network host, or system process?
- A. Hacking
- B. Authentication
- C. Packet filtering
- D. Auditing
Answer: B
NEW QUESTION 17
You work in a company that accesses the Internet frequently. This makes the company's files susceptible to attacks from unauthorized access. You want to protect your company's network from external attacks. Which of the following options will help you in achieving your aim?
- A. FTP
- B. Gopher
- C. Firewall
- D. HTTP
Answer: C
NEW QUESTION 18
Which of the following two cryptography methods are used by NTFS Encrypting File System (EFS) to encrypt the data stored on a disk on a file-by-file basis?
- A. Public key
- B. Digital certificates
- C. Twofish
- D. RSA
Answer: AB
NEW QUESTION 19
......
P.S. Easily pass GISF Exam with 333 Q&As Surepassexam Dumps & pdf Version, Welcome to Download the Newest Surepassexam GISF Dumps: https://www.surepassexam.com/GISF-exam-dumps.html (333 New Questions)
