Our pass rate is high to 98.9% and the similarity percentage between our GSNA study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the GIAC GSNA exam in just one try? I am currently studying for the GIAC GSNA exam. Latest GIAC GSNA Test exam practice questions and answers, Try GIAC GSNA Brain Dumps First.
Check GSNA free dumps before getting the full version:
NEW QUESTION 1
TCP/IP stack fingerprinting is the passive collection of configuration attributes from a remote device during standard layer 4 network communications. The combination of parameters may then be used to infer the remote operating system (OS fingerprinting), or incorporated into a device fingerprint. Which of the following Nmap switches can be used to perform TCP/IP stack fingerprinting?
- A. nmap -sS
- B. nmap -sU -p
- C. nmap -O -p
- D. nmap -sT
Answer: C
Explanation:
The nmap -O -p switch can be used to perform TCP/IP stack fingerprinting. Nmap is a free open-source utility for network exploration and security auditing. It is used to discover computers and services on a computer network, thus creating a "map" of the network. Just like many simple port scanners, Nmap is capable of discovering passive services. In addition, Nmap may be able to determine various details about the remote computers. These include operating system, device type, uptime, software product used to run a service, exact version number of that product, presence of some firewall techniques and, on a local area network, even vendor of the remote network card. Nmap runs on Linux, Microsoft Windows etc. Answer B is incorrect. The nmap -sU -p switch can be used to perform UDP port scanning. Answer A is incorrect. The nmap -sS switch is used to perform a TCP half scan. TCP SYN scanning is also known as half-open scanning because in this a full TCP connection is never opened. Answer D is incorrect. The nmap -sT switch is used to perform a TCP full scan.
NEW QUESTION 2
Data mining is a process of sorting through data to identify patterns and establish relationships. Which of the following data mining parameters looks for patterns where one event is connected to another event?
- A. Sequence or path analysis
- B. Forecasting
- C. Clustering
- D. Association
Answer: D
Explanation:
Data mining is a process of sorting through data to identify patterns and establish relationships. Following are the data mining parameters: Association: Looking for patterns where one event is connected to another event. Sequence or path analysis: Looking for patterns where one event leads to another later event. Classification: Looking for new patterns (may result in a change in the way the data is organized but is acceptable). Clustering: Finding and visually documenting groups of facts not previously known. Forecasting: Discovering patterns in data that can lead to reasonable predictions about the future (This area of data mining is known as predictive analytics).
NEW QUESTION 3
You have recently joined as a Network Auditor in XYZ CORP. The company has a Windows-based network. You have been assigned the task to determine whether or not the company's goal is being achieved. As an auditor, which of the following tasks should you perform before conducting the data center review? Each correct answer represents a complete solution. Choose three.
- A. Review the future IT organization chart.
- B. Meet with IT management to determine possible areas of concern.
- C. Review the company's IT policies and procedures.
- D. Research all operating systems, software applications, and data center equipment operating within the data center.
Answer: BCD
Explanation:
The auditor should be adequately educated about the company and its critical business activities before conducting a data center review. The objective of the data center is to align data center activities with the goals of the business while maintaining the security and integrity of critical information and processes. To adequately determine if whether or not the client's goal is being achieved, the auditor should perform the following before conducting the review: Meet with IT management to determine possible areas of concern. Review the current IT organization chart. Review job descriptions of data center
employees. Research all operating systems, software applications, and data center equipment operating within the data center. Review the company's IT policies and procedures. Evaluate the company's IT budget and systems planning documentation. Review the data center's disaster recovery plan. Answer A is incorrect. An auditor should review the current organization chart. Reviewing the future organization chart would not help in finding the current threats to the organization.
NEW QUESTION 4
You work as a Network Architect for Tech Perfect Inc. The company has a TCP/IP based Enterprise network. The company uses Cisco IOS technologies in the Enterprise network. You have enabled system message logging (syslog) service on all the routers that are currently working in the network. The syslog service provides all the reports, and important error and notification messages. You want to store all the reports and messages. Choose the locations where you can store all of these.
- A. Auxiliary
- B. Buffer
- C. Syslog server
- D. tty lines
- E. Console
Answer: BCDE
Explanation:
According to the scenario, you have enabled system message logging (syslog) service on all the routers that are currently working in the network. If you want to store all the repots, important error and notification messages sent by the routers, you can store all of these in the buffer, console, syslog server, and tty lines. You can use buffer, if you want to store syslog messages for later analysis of the network. Buffer is the memory of the router. The syslog messages that you have stored in the buffer are later available for the network analysis until the router is rebooted. You can use console port of the routers to send syslog messages to the attached terminal. You can also use vty and tty lines to send syslog messages to the remote terminal. However, the messages send through the console, vty, and tty lines are not later available for network analysis. You can use syslog server to store all the reports, and important error and notification messages. It is the best option to store all these because it is easy to configure a syslog server and you can store a large volume of logs. Note: If you have configured to run an SNMP agent, the routers send all the reports, and important error and messages in the form of SNMP traps to an SNMP server. Using this you can store the reports and messages for a long period of time. Answer A is incorrect. You cannot store syslog messages in the auxiliary line.
NEW QUESTION 5
You work as a Network Administrator for Tech Perfect Inc. You have a laptop running Windows Vista Ultimate. You want to configure Windows Defender on your laptop so that it does not take any action automatically whenever it scans malicious software. Rather, it should recommend the action and wait for your approval for taking any action. Which of the following actions will you take to accomplish the task?
- A. Clear the Use real-time protection check box in Defender Options
- B. Clear the Automatically scan my computer check box in Defender Options
- C. Select the Create a restore point before applying action to detected items check box in Defender Options
- D. Clear the Apply default actions to items detected during a scan check box in Defender Options.
Answer: D
Explanation:
According to the question, you want to prevent Windows Defender from taking any action automatically during the scanning of your laptop. In order to accomplish this, you will have to clear the Apply default actions to items detected during a scan check box in Defender Options.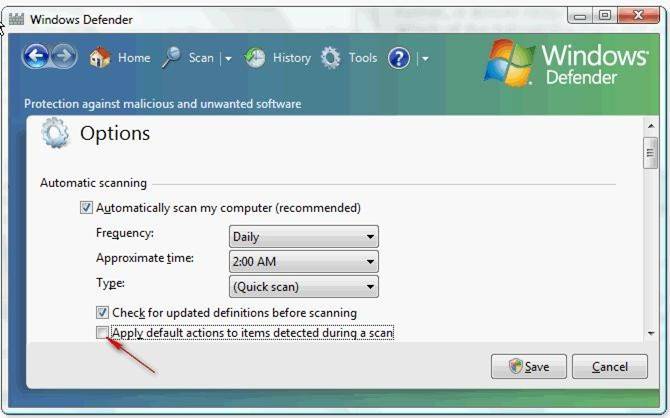
If you clear the Apply default actions to items detected during a scan check box, it will result in Windows Defender only recommending an action to take for detected malicious software.
NEW QUESTION 6
You want to repeat the last command you entered in the bash shell. Which of the following commands will you use?
- A. history ##
- B. history !#
- C. history !!
- D. history !1
Answer: C
Explanation:
The history !! command shows the previously entered command in the bash shell. In the bash shell, the history command is used to view the recently executed commands. History is on by default. A user can turn off history using the command set +o history and turn it on using set -o history. An environment variable HISTSIZE is used to inform bash about how many history lines should be kept. The following commands are frequently used to view
and manipulate history: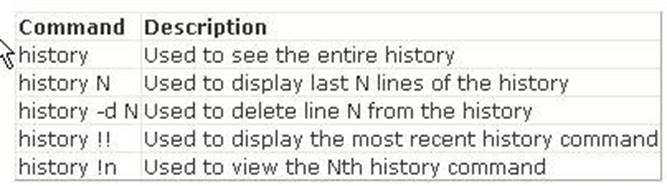
Answer B is incorrect. The history !# command shows the entire command line typed. Answer D is incorrect. The history !n command shows the nth command typed. Since n is equal to 1 in this command, the first command will be shown. Answer A is incorrect. It is not a valid command.
NEW QUESTION 7
Which of the following features of a switch helps to protect network from MAC flood and MAC spoofing?
- A. Multi-Authentication
- B. Port security
- C. MAC Authentication Bypass
- D. Quality of Service (QoS)
Answer: B
Explanation:
If a switch has the ability to enable port security, this will help to protect network from both the MAC Flood and MAC Spoofing attacks. Answer D is incorrect. Quality of Service (QoS) feature is useful for prioritizing VOIP traffic. Switches are offering the ability to assign a device a Quality of Service (QoS) value or a rate limiting value based on the RADIUS response. Answer A is incorrect. Multi-Authentication feature is used to allow multiple devices to use a single port. Answer C is incorrect. MAC Authentication Bypass feature is used to allow the RADIUS server to specify the default VLAN/ACL for every device that doesn't authenticate by 802.1X.
NEW QUESTION 8
From an auditing perspective, database security can be broken down into four key categories: Server Security Database Connections Table Access Control Restricting Database Access Which of the following categories leads to the process of limiting access to the database server?
- A. Table access control
- B. Database connections
- C. Restricting database access
- D. Server security
Answer: D
Explanation:
Server security is the process of limiting access to the database server. This is one of the most basic and most important components of database security. It is imperative that an organization not let their database server be visible to the world. If an organization's database server is supplying information to a web server, then it should be configured to allow connections only from that web server. Also, every server should be configured to allow only trusted IP addresses. Answer B is incorrect. With regard to database connections, system administrators should not allow immediate unauthenticated updates to a database. If users are allowed to make updates to a database via a web page, the system administrator should validate all updates to make sure that they are warranted and safe. Also, the system administrator should not allow users to use their designation of "sa" when accessing the database. This gives employees complete access to all of the data stored on the database regardless of whether or not they are authenticated to have such access. Answer A is incorrect. Table access control is related to an access control list, which is a table that tells a computer operating system which access rights each user has to a particular system object. Table access control has been referred to as one of the most overlooked forms of database security. This is primarily because it is so difficult to apply. In order to properly use table access control, the system administrator and the database developer need to collaborate with each other. Answer C is incorrect. Restricting database access is important especially for the companies that have their databases uploaded on the Internet. Internet-based databases have been the most recent targets of attacks, due to their open access or open ports. It is very easy for criminals to conduct a "port scan" to look for ports that are open that popular database systems are using by default. The ports that are used by default can be changed, thus throwing off a criminal looking for open ports set by default. Following are the security measures that can be implemented to prevent open access from the Internet: Trusted IP addresses: Servers can be configured to answer pings from a list of trusted hosts only. Server account disabling: The server ID can be suspended after three password attempts. Special tools: Products can be used to send an alert when an external server is attempting to breach the system's security. One such example is RealSecure by ISS.
NEW QUESTION 9
The employees of CCN Inc. require remote access to the company's proxy servers. In order to provide solid wireless security, the company uses LEAP as the authentication protocol. Which of the following is supported by the LEAP protocol?
- A. Dynamic key encryption
- B. Public key certificate for server authentication
- C. Strongest security level
- D. Password hash for client authentication
Answer: AD
Explanation:
LEAP can use only password hash as the authentication technique. Not only LEAP, but EAP-TLS, EAP-TTLS, and PEAP also support dynamic key encryption and mutual authentication. Answer C is incorrect. LEAP provides only a moderate level of security. Answer B is incorrect. LEAP uses password hash for server authentication.
NEW QUESTION 10
Which of the following are the goals of risk management? (Choose three)
- A. Identifying the risk
- B. Assessing the impact of potential threats
- C. Finding an economic balance between the impact of the risk and the cost of the countermeasure
- D. Identifying the accused
Answer: ABC
Explanation:
There are three goals of risk management as follows: Identifying the risk Assessing the impact of potential threats Finding an economic balance between the impact of the risk and the cost of the countermeasure Answer D is incorrect. Identifying the accused does not come under the scope of risk management.
NEW QUESTION 11
You want to record auditing information in the SYS.AUD$ table, and also want to record SQL bind variables as well as the SQL text in the audit trail. Which of the following statements will accomplish this task?
- A. ALTER SYSTEM SET AUDIT_TRAIL = DB, XML SCOPE=SPFILE;
- B. ALTER SYSTEM SET AUDIT_TRAIL = 'DB, EXTENDED' SCOPE=SPFILE;
- C. ALTER SYSTEM SET AUDIT_TRAIL = 'DB','EXTENDED' SCOPE=SPFILE;
- D. ALTER SYSTEM SET AUDIT_TRAIL = DB, EXTENDED SCOPE=SPFILE;
- E. ALTER SYSTEM SET AUDIT_FILE_DEST = 'DB, EXTENDED' SCOPE=SPFILE;
- F. ALTER SYSTEM SET AUDIT_TRAIL = DB, EXTENDED SCOPE=BOTH;
Answer: CD
Explanation:
The initialization parameter AUDIT_TRAIL is used to specify the kind of auditing that needs to be performed, as well as the destination where it will be performed. There are three basic values for auditing that are DB, OS, and XML. Specifying DB sends all audit rows to the table SYS.AUD$, OS sends the audit rows to an operating system file, and XML sends the audit rows to an operating system file in the XML format. The location for external audit rows is specified by the AUDIT_FILE_DEST parameter. By adding the EXTENDED parameter for either DB or XML auditing, all SQL bind variables and the text of all SQL commands are included in the audit row. EXTENDED cannot be specified for OS auditing. In addition, NONE can be specified as the value for AUDIT_TRAIL, which will disable all auditing. Answer B is incorrect. DB, EXTENDED in single quotes cannot be specified when setting the AUDIT_TRAIL parameter. Answer E is incorrect. AUDIT_TRAIL must be set to specify the type of auditing. AUDIT_FILE_DEST is used to specify the operating system location for either OS or XML auditing. Answer A is incorrect. DB and XML auditing cannot be specified at the same time and the database must be restarted for the auditing change to go into effect.
NEW QUESTION 12
You work as a Network Administrator for NTY Inc. The company has a secure wireless network. While auditing the network for maintaining security, you find an unknown node. You want to locate that node. Which tool will you use to pinpoint the actual physical location of the node?
- A. Kismet
- B. Ekahau
- C. WEPCrack
- D. AirSnort
Answer: B
Explanation:
Ekahau is an easy-to-use powerful and comprehensive tool for network site surveys and optimization. It is an auditing tool that can be used to pinpoint the actual physical location of wireless devices in the network. This tool can be used to make a map of the office and then perform the survey of the office. In the process, if one finds an unknown node, ekahau can be used to locate that node. Answer D is incorrect. AirSnort is a Linux-based WLAN WEP cracking tool that recovers encryption keys. AirSnort operates by passively monitoring transmissions. It uses Ciphertext Only Attack and captures approximately 5 to 10 million packets to decrypt the WEP keys.
Answer A is incorrect. Kismet is a Linux-based 802.11 wireless network sniffer and intrusion detection system. It can work with any wireless card that supports raw monitoring (rfmon) mode. Kismet can sniff 802.11b, 802.11a, 802.11g, and 802.11n traffic. Kismet can be used for the following tasks: To identify networks by passively collecting packets To detect standard named networks To detect masked networks To collect the presence of non-beaconing networks via data traffic Answer C is incorrect. WEPcrack is a wireless network cracking tool that exploits the vulnerabilities in the RC4 Algorithm, which comprises the WEP security parameters. It mainly consists of three tools, which are as follows: WeakIVGen: It allows a user to emulate the encryption output of 802.11 networks to weaken the secret key used to encrypt the network traffic. Prism-getIV: It analyzes packets of information until ultimately matching patterns to the one known to decrypt the secret key. WEPcrack: It pulls the all beneficial data of WeakIVGen and Prism-getIV to decipher the network encryption.
NEW QUESTION 13
You have to ensure that your Cisco Router is only accessible via telnet and ssh from the following hosts and subnets: 10.10.2.103 10.10.0.0/24 Which of the following sets of commands will you use to accomplish the task?
- A. access-list 10 permit host 10.10.2.103access-list 10 permit 10.10.0.0 0.0.0.255access-list 10 deny any line vty 0 4 access-class 10 out
- B. access-list 10 permit 10.10.2.103access-list 10 permit 10.10.0.0 0.0.0.255access-list 10 deny any line vty 0 4 access-group 10 in
- C. access-list 10 permit host 10.10.2.103access-list 10 permit 10.10.0.0 0.0.0.255access-list 10 deny any line vty 0 4access-class 10 in
- D. access-list 10 permit host 10.10.2.103access-list 11 permit host 10.10.0.0 255.255.255.0access-list 12 deny any line vty 0 4access-group 10, 11, 12 in
Answer: C
Explanation:
In order to accomplish the task, you will have to run the following sets of commands: access-list 10 permit host 10.10.2.103 access-list 10 permit 10.10.0.0 0.0.0.255 access-list 10 deny any line vty 0 4 access-class 10 in This configuration set meets all the requirements. The ACL is correctly configured and is applied to the VTY lines using the access-class command for inbound connections. Answer D is incorrect. This
configuration actually creates 3 separate ACL's (10, 11, and 12) and also incorrectly attempts to apply the ACL's to the VTY lines. Answer A is incorrect. This configuration is correct except for the access-class command being applied in the outbound direction. When using "access-class out", the router will not match connections coming into the router for Telnet and/or SSH. Instead, it will match connections being generated from the router. Answer B is incorrect. This configuration is correct except for the access-group command. Access-group is used to apply ACLs to an interface. Access-class is used to apply ACLs to VTY lines.
NEW QUESTION 14
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Active Directory-based single domain single forest network. The functional level of the
forest is Windows Server 2003. The company has recently provided laptops to its sales team members. You have configured access points in the network to enable a wireless network. The company's security policy states that all users using laptops must use smart cards for authentication. Which of the following authentication techniques will you use to implement the security policy of the company?
- A. IEEE 802.1X using EAP-TLS
- B. IEEE 802.1X using PEAP-MS-CHAP
- C. Pre-shared key
- D. Open system
Answer: A
Explanation:
In order to ensure that the laptop users use smart cards for authentication, you will have to configure IEEE 802.1X authentication using the EAP-TLS protocol on the network.
NEW QUESTION 15
You have just installed a Windows 2003 server. What action should you take regarding the default shares?
- A. Disable them only if this is a domain server.
- B. Disable them.
- C. Make them hidden shares.
- D. Leave them, as they are needed for Windows Server operations.
Answer: B
Explanation:
Default shares should be disabled, unless they are absolutely needed. They pose a significant security risk by providing a way for an intruder to enter your machine. Answer A is incorrect. Whether this is a domain server, a DHCP server, a file server, or database server does not change the issue with shared drives/folders. Answer C is incorrect. They cannot be hidden. Shared folders are, by definition, not hidden but rather available to users on the network. Answer D is incorrect. These are not necessary for Windows Server operations.
NEW QUESTION 16
Mark works as a Web Developer for XYZ CORP. He is developing a Web site for the company. The Manager of the company requires Mark to use tables instead of frames in the Web site. What is the major advantage that a table-structured Web site has over a frame-structured Web site?
- A. Easy maintenance
- B. Speed
- C. Better navigation
- D. Capability of being bookmarked or added to the Favorites folder
Answer: D
Explanation:
The major advantage that a table-structured Web site has over a frame- structured Web site is that users can bookmark the pages of a table- structured Web site, whereas pages of a frame-structured Web site cannot be bookmarked or added to the Favorites folder. Non-frame Web sites also give better results with search engines. Better navigation: Web pages can be divided into multiple frames and each frame can display a separate Web page. It helps in providing better and consistent navigation. Easy maintenance: Fixed elements, such as a navigation link and company logo page, can be created once and used with all the other pages. Therefore, any change in these pages is required to be made only once.
NEW QUESTION 17
You work as a Network Administrator for Blue Well Inc. The company has a TCP/IP-based routed network. Two segments have been configured on the network as shown below: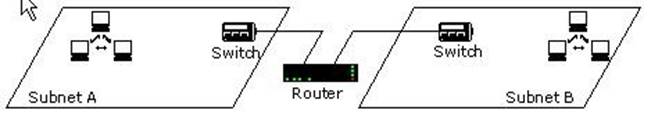
One day, the switch in Subnet B fails. What will happen?
- A. Communication between the two subnets will be affected.
- B. The whole network will collapse.
- C. Workstations on Subnet A will become offline
- D. Workstations on Subnet B will become offline.
Answer: AD
Explanation:
According to the question, the network is a routed network where two segments have been divided and each segment has a switch. These switches are connected to a common router. All workstations in a segment are connected to their respective subnet's switches. Failure of the switch in Subnet B will make all workstations connected to it offline. Moreover, communication between the two subnets will be affected, as there will be no link to connect to Subnet B.
NEW QUESTION 18
Which of the following are the limitations for the cross site request forgery (CSRF) attack?
- A. The attacker must determine the right values for all the form inputs.
- B. The attacker must target a site that doesn't check the referrer header.
- C. The target site should have limited lifetime authentication cookies.
- D. The target site should authenticate in GET and POST parameters, not only cookies.
Answer: AB
Explanation:
Following are the limitations of cross site request forgeries to be successful:
* 1. The attacker must target either a site that doesn't check the Referer header (which is common) or a victim with a browser or plugin bug that allows Referer spoofing (which is rare).
* 2. The attacker must find a form submission at the target site that does something useful to the attacker (e.g., transfers money, or changes the victim's e-mail address or password).
* 3. The attacker must determine the right values for all the form inputs: if any of them are required to be secret authentication values or IDs that the attacker can't guess, the attack will fail.
* 4. The attacker must lure the victim to a Web page with malicious code while the victim is logged in to the target site. Since, the attacker can't see what the target Web site sends back to the victim in response to the forged requests, unless he exploits a cross- site scripting or other bug at the target Web site.
Similarly, the attacker can only "click" any links or submit any forms that come up after the initial forged request, if the subsequent links or forms are similarly predictable. (Multiple "clicks" can be simulated by including multiple images on a page, or by using JavaScript to introduce a delay between clicks). from cross site request forgeries (CSRF) by applying the following countermeasures available: Requiring authentication in GET and POST parameters, not only cookies. Checking the HTTP Referer header. Ensuring there's no crossdomain.xml file granting unintended access to Flash movies. Limiting the lifetime of authentication cookies. Requiring a secret, user-specific token in all form submissions prevents CSRF; the attacker's site can't put the right token in its submissions. Individual Web users can do relatively little to prevent cross-site request forgery. Logging out of sites and avoiding their "remember me" features can mitigate CSRF risk; not displaying external images or not clicking links in "spam" or unreliable e-mails may also help.
NEW QUESTION 19
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He wants to use Kismet as a wireless sniffer to sniff the We-are-secure network. Which of the following IEEE-based traffic can be sniffed with Kismet?
- A. 802.11g
- B. 802.11n
- C. 802.11b
- D. 802.11a
Answer: ABCD
Explanation:
Kismet can sniff IEEE 802.11a, 802.11b, 802.11g, and 802.11n-based wireless network traffic.
NEW QUESTION 20
Which of the following statements is true about the Digest Authentication scheme?
- A. A valid response from the client contains a checksum of the username, the password, the given random value, the HTTP method, and the requested URL.
- B. In this authentication scheme, the username and password are passed with everyrequest, not just when the user first types them.
- C. The password is sent over the network in clear text format.
- D. It uses the base64 encoding encryption scheme.
Answer: A
Explanation:
The Digest Authentication scheme is a replacement of the Basic Authentication scheme. This authentication scheme is based on the challenge response model. In Digest authentication, the password is never sent across the network in clear text format but is always transmitted as an MD5 digest of the user's password. In this way, the password cannot be determined with the help of a sniffer.
How does it work? In this authentication scheme, an optional header allows the server to specify the algorithm used to create the checksum or digest (by default, the MD5 algorithm). The Digest Authentication scheme provides the challenge using a randomly chosen value. This randomly chosen value is a server-specified data string which may be uniquely generated each time a 401 response is made. A valid response contains a checksum (by default, the MD5 checksum) of the username, the password, the given random value, the HTTP method, and the requested URL. In this way, the password is never sent in clear text format. Drawback: Although the password is not sent in clear text format, an attacker can gain access with the help of the digested password, since the digested password is really all the information needed to access the web site. Answer B, C, D are incorrect. These statements are true about the Basic Authentication scheme.
NEW QUESTION 21
......
Recommend!! Get the Full GSNA dumps in VCE and PDF From Dumps-files.com, Welcome to Download: https://www.dumps-files.com/files/GSNA/ (New 368 Q&As Version)
