Examcollection offers free demo for PCNSA exam. "Palo Alto Networks Certified Network Security Administrator", also known as PCNSA exam, is a Paloalto-Networks Certification. This set of posts, Passing the Paloalto-Networks PCNSA exam, will help you answer those questions. The PCNSA Questions & Answers covers all the knowledge points of the real exam. 100% real Paloalto-Networks PCNSA exams and revised by experts!
Online Paloalto-Networks PCNSA free dumps demo Below:
NEW QUESTION 1
Which two Palo Alto Networks security management tools provide a consolidated creation of policies, centralized management and centralized threat intelligence. (Choose two.)
- A. GlobalProtect
- B. Panorama
- C. Aperture
- D. AutoFocus
Answer: BD
NEW QUESTION 2
What are two differences between an implicit dependency and an explicit dependency in App- ID? (Choose two.)
- A. An implicit dependency does not require the dependent application to be added in the security policy
- B. An implicit dependency requires the dependent application to be added in the security policy
- C. An explicit dependency does not require the dependent application to be added in the security policy
- D. An explicit dependency requires the dependent application to be added in the security policy
Answer: AD
NEW QUESTION 3
Given the topology, which zone type should zone A and zone B to be configured with?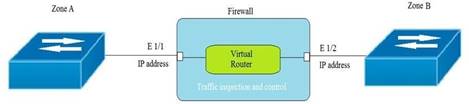
- A. Layer3
- B. Tap
- C. Layer2
- D. Virtual Wire
Answer: A
NEW QUESTION 4
Your company requires positive username attribution of every IP address used by wireless devices to support a new compliance requirement. You must collect IP –to-user mappings as soon as possible with minimal downtime and minimal configuration changes to the wireless devices themselves. The wireless devices are from various manufactures.
Given the scenario, choose the option for sending IP-to-user mappings to the NGFW.
- A. syslog
- B. RADIUS
- C. UID redistribution
- D. XFF headers
Answer: A
NEW QUESTION 5
A security administrator has configured App-ID updates to be automatically downloaded and installed. The company is currently using an application identified by App-ID as SuperApp_base. On a content update notice, Palo Alto Networks is adding new app signatures labeled SuperApp_chat and SuperApp_download, which will be deployed in 30 days. Based on the information, how is the SuperApp traffic affected after the 30 days have passed?
- A. All traffic matching the SuperApp_chat, and SuperApp_download is denied because it no longer matches the SuperApp-base application
- B. No impact because the apps were automatically downloaded and installed
- C. No impact because the firewall automatically adds the rules to the App-ID interface
- D. All traffic matching the SuperApp_base, SuperApp_chat, and SuperApp_download is denied until the security administrator approves the applications
Answer: C
NEW QUESTION 6
Which option shows the attributes that are selectable when setting up application filters?
- A. Category, Subcategory, Technology, and Characteristic
- B. Category, Subcategory, Technology, Risk, and Characteristic
- C. Name, Category, Technology, Risk, and Characteristic
- D. Category, Subcategory, Risk, Standard Ports, and Technology
Answer: B
NEW QUESTION 7
In which stage of the Cyber-Attack Lifecycle would the attacker inject a PDF file within an email?
- A. Weaponization
- B. Reconnaissance
- C. Installation
- D. Command and Control
- E. Exploitation
Answer: A
NEW QUESTION 8
Which five Zero Trust concepts does a Palo Alto Networks firewall apply to achieve an integrated approach to prevent threats? (Choose five.)
- A. User identification
- B. Filtration protection
- C. Vulnerability protection
- D. Antivirus
- E. Application identification
- F. Anti-spyware
Answer: ACDEF
NEW QUESTION 9
An administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact a command-and-control (C2) server. Which two security profile components will detect and prevent this threat after the firewall’s signature database has been updated? (Choose two.)
- A. vulnerability protection profile applied to outbound security policies
- B. anti-spyware profile applied to outbound security policies
- C. antivirus profile applied to outbound security policies
- D. URL filtering profile applied to outbound security policies
Answer: BD
NEW QUESTION 10
When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None?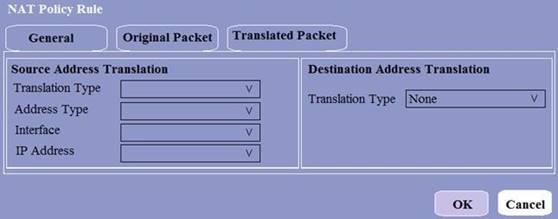
- A. Translation Type
- B. Interface
- C. Address Type
- D. IP Address
Answer: A
NEW QUESTION 11
Which file is used to save the running configuration with a Palo Alto Networks firewall?
- A. running-config.xml
- B. run-config.xml
- C. running-configuration.xml
- D. run-configuratin.xml
Answer: A
NEW QUESTION 12
Which firewall plane provides configuration, logging, and reporting functions on a separate processor?
- A. control
- B. network processing
- C. data
- D. security processing
Answer: A
NEW QUESTION 13
Identify the correct order to configure the PAN-OS integrated USER-ID agent.
3. add the service account to monitor the server(s)
2. define the address of the servers to be monitored on the firewall
4. commit the configuration, and verify agent connection status
1. create a service account on the Domain Controller with sufficient permissions to execute the User- ID agent
- A. 2-3-4-1
- B. 1-4-3-2
- C. 3-1-2-4
- D. 1-3-2-4
Answer: D
NEW QUESTION 14
......
P.S. Easily pass PCNSA Exam with 115 Q&As Certshared Dumps & pdf Version, Welcome to Download the Newest Certshared PCNSA Dumps: https://www.certshared.com/exam/PCNSA/ (115 New Questions)
