Cause all that matters here is passing the CompTIA PT0-002 exam. Cause all that you need is a high score of PT0-002 CompTIA PenTest+ Certification Exam exam. The only one thing you need to do is downloading Certleader PT0-002 exam study guides now. We will not let you down with our money-back guarantee.
Online CompTIA PT0-002 free dumps demo Below:
NEW QUESTION 1
A penetration tester has been given an assignment to attack a series of targets in the 192.168.1.0/24 range, triggering as few alarms and countermeasures as possible.
Which of the following Nmap scan syntaxes would BEST accomplish this objective?
- A. nmap -sT -vvv -O 192.168.1.2/24 -PO
- B. nmap -sV 192.168.1.2/24 -PO
- C. nmap -sA -v -O 192.168.1.2/24
- D. nmap -sS -O 192.168.1.2/24 -T1
Answer: D
NEW QUESTION 2
A company’s Chief Executive Officer has created a secondary home office and is concerned that the WiFi service being used is vulnerable to an attack. A penetration tester is hired to test the security of the WiFi’s router.
Which of the following is MOST vulnerable to a brute-force attack?
- A. WPS
- B. WPA2-EAP
- C. WPA-TKIP
- D. WPA2-PSK
Answer: A
NEW QUESTION 3
A penetration tester conducted an assessment on a web server. The logs from this session show the following:
http://www.thecompanydomain.com/servicestatus.php?serviceID=892&serviceID=892 ‘ ; DROP TABLE SERVICES; -
Which of the following attacks is being attempted?
- A. Clickjacking
- B. Session hijacking
- C. Parameter pollution
- D. Cookie hijacking
- E. Cross-site scripting
Answer: C
NEW QUESTION 4
A red-team tester has been contracted to emulate the threat posed by a malicious insider on a company’s network, with the constrained objective of gaining access to sensitive personnel files. During the assessment, the red-team tester identifies an artifact indicating possible prior compromise within the target environment.
Which of the following actions should the tester take?
- A. Perform forensic analysis to isolate the means of compromise and determine attribution.
- B. Incorporate the newly identified method of compromise into the red team’s approach.
- C. Create a detailed document of findings before continuing with the assessment.
- D. Halt the assessment and follow the reporting procedures as outlined in the contract.
Answer: C
NEW QUESTION 5
A penetration tester is looking for a vulnerability that enables attackers to open doors via a specialized TCP service that is used for a physical access control system. The service exists on more than 100 different hosts, so the tester would like to automate the assessment. Identification requires the penetration tester to: Have a full TCP connection
Have a full TCP connection  Send a “hello” payload
Send a “hello” payload Walt for a response
Walt for a response Send a string of characters longer than 16 bytes
Send a string of characters longer than 16 bytes
Which of the following approaches would BEST support the objective?
- A. Run nmap –Pn –sV –script vuln <IP address>.
- B. Employ an OpenVAS simple scan against the TCP port of the host.
- C. Create a script in the Lua language and use it with NSE.
- D. Perform a credentialed scan with Nessus.
Answer: C
NEW QUESTION 6
A penetration tester ran a ping –A command during an unknown environment test, and it returned a 128 TTL packet. Which of the following OSs would MOST likely return a packet of this type?
- A. Windows
- B. Apple
- C. Linux
- D. Android
Answer: A
NEW QUESTION 7
A security company has been contracted to perform a scoped insider-threat assessment to try to gain access to the human resources server that houses PII and salary data. The penetration testers have been given an internal network starting position.
Which of the following actions, if performed, would be ethical within the scope of the assessment?
- A. Exploiting a configuration weakness in the SQL database
- B. Intercepting outbound TLS traffic
- C. Gaining access to hosts by injecting malware into the enterprise-wide update server
- D. Leveraging a vulnerability on the internal CA to issue fraudulent client certificates
- E. Establishing and maintaining persistence on the domain controller
Answer: B
NEW QUESTION 8
A penetration tester has been given eight business hours to gain access to a client’s financial system. Which of the following techniques will have the highest likelihood of success?
- A. Attempting to tailgate an employee going into the client's workplace
- B. Dropping a malicious USB key with the company’s logo in the parking lot
- C. Using a brute-force attack against the external perimeter to gain a foothold
- D. Performing spear phishing against employees by posing as senior management
Answer: C
NEW QUESTION 9
During a penetration-testing engagement, a consultant performs reconnaissance of a client to identify potential targets for a phishing campaign. Which of the following would allow the consultant to retrieve email addresses for technical and billing contacts quickly, without triggering any of the client’s cybersecurity tools? (Choose two.)
- A. Scraping social media sites
- B. Using the WHOIS lookup tool
- C. Crawling the client’s website
- D. Phishing company employees
- E. Utilizing DNS lookup tools
- F. Conducting wardriving near the client facility
Answer: BC
NEW QUESTION 10
Running a vulnerability scanner on a hybrid network segment that includes general IT servers and industrial control systems:
- A. will reveal vulnerabilities in the Modbus protocol.
- B. may cause unintended failures in control systems.
- C. may reduce the true positive rate of findings.
- D. will create a denial-of-service condition on the IP networks.
Answer: B
NEW QUESTION 11
A company conducted a simulated phishing attack by sending its employees emails that included a link to a site that mimicked the corporate SSO portal. Eighty percent of the employees who received the email clicked the link and provided their corporate credentials on the fake site. Which of the following recommendations would BEST address this situation?
- A. Implement a recurring cybersecurity awareness education program for all users.
- B. Implement multifactor authentication on all corporate applications.
- C. Restrict employees from web navigation by defining a list of unapproved sites in the corporate proxy.
- D. Implement an email security gateway to block spam and malware from email communications.
Answer: A
NEW QUESTION 12
Which of the following describe the GREATEST concerns about using third-party open-source libraries in application code? (Choose two.)
- A. The libraries may be vulnerable
- B. The licensing of software is ambiguous
- C. The libraries’ code bases could be read by anyone
- D. The provenance of code is unknown
- E. The libraries may be unsupported
- F. The libraries may break the application
Answer: AC
NEW QUESTION 13
A penetration tester is starting an assessment but only has publicly available information about the target company. The client is aware of this exercise and is preparing for the test.
Which of the following describes the scope of the assessment?
- A. Partially known environment testing
- B. Known environment testing
- C. Unknown environment testing
- D. Physical environment testing
Answer: C
NEW QUESTION 14
A company is concerned that its cloud service provider is not adequately protecting the VMs housing its software development. The VMs are housed in a datacenter with other companies sharing physical resources. Which of the following attack types is MOST concerning to the company?
- A. Data flooding
- B. Session riding
- C. Cybersquatting
- D. Side channel
Answer: B
NEW QUESTION 15
Which of the following should a penetration tester attack to gain control of the state in the HTTP protocol after the user is logged in?
- A. HTTPS communication
- B. Public and private keys
- C. Password encryption
- D. Sessions and cookies
Answer: D
NEW QUESTION 16
Which of the following expressions in Python increase a variable val by one (Choose two.)
- A. val++
- B. +val
- C. val=(val+1)
- D. ++val
- E. val=val++
- F. val+=1
Answer: DF
NEW QUESTION 17
A penetration tester performs the following command: curl –I –http2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?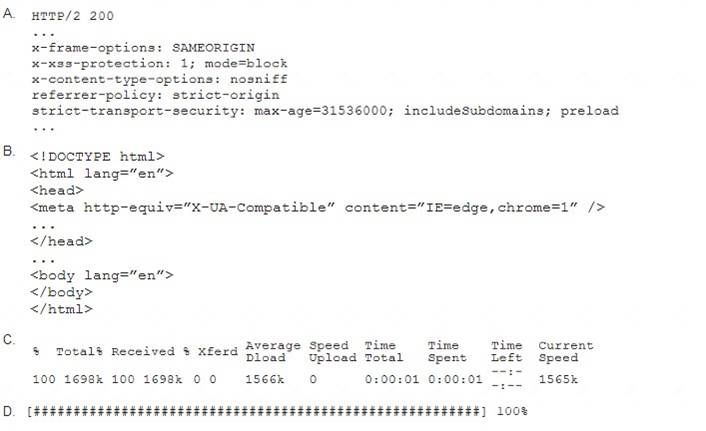
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: A
NEW QUESTION 18
......
P.S. Easily pass PT0-002 Exam with 110 Q&As Dumps-files.com Dumps & pdf Version, Welcome to Download the Newest Dumps-files.com PT0-002 Dumps: https://www.dumps-files.com/files/PT0-002/ (110 New Questions)
