Proper study guides for Most up-to-date Amazon-Web-Services AWS Certified Solutions Architect - Associate certified begins with Amazon-Web-Services SAA-C01 preparation products which designed to deliver the Precise SAA-C01 questions by making you pass the SAA-C01 test at your first time. Try the free SAA-C01 demo right now.
Online Amazon-Web-Services SAA-C01 free dumps demo Below:
NEW QUESTION 1
A user has enabled the CloudWatch alarm to estimate the usage charges. If the user disables monitoring of the estimated charges but does not delete the billing alert from the AWS account, what will happen?
- A. The user cannot edit the existing billing alarm.
- B. The data collection on estimated charges is stopped.
- C. It is not possible to disable monitoring of the estimated charges.
- D. AWS will stop sending the billing alerts to the use
Answer: C
Explanation:
To create an alarm on the estimated AWS usage charges, a user must enable monitoring of estimated AWS charges. This enables creating the metric data, which will be used to create a billing alarm. Once the estimated charges monitoring is enabled, the user cannot disable it. The user has to delete the alarms to stop receiving any notifications on billing. http://docs.aws.amazon.com/AmazonCloudWatch/latest/DeveloperGuide/gs_monitor_estimated_c harges_with_cloudwatch.html
NEW QUESTION 2
Which of the following are valid statements about Amazon S3? (Choose two.)
- A. S3 provides read-after-write consistency for any type of PUT or DELETE
- B. Consistency is not guaranteed for any type of PUT or DELETE
- C. A successful response to a PUT request only occurs when a complete object is saved.
- D. Partially saved objects are immediately readable with a GET after an overwrite PUT.
- E. S3 provides eventual consistency for overwrite PUTS and DELETE
Answer: CE
Explanation: 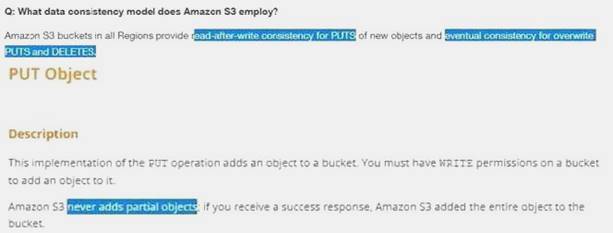
NEW QUESTION 3
A Solutions Architect is designing a mobile application that will capture receipt images to track expenses. The Architect wants to store the images on Amazon S3. However, uploading images through the web server will create too much traffic.
What is the MOST efficient method to store images from a mobile application on Amazon S3?
- A. Upload directly to S3 using a pre-signed URL.
- B. Upload to a second bucket, and have a Lambda event copy the image to the primary bucket.
- C. Upload to a separate Auto Scaling group of servers behind an ELB Classic Load Balancer, and have them write to the Amazon S3 bucket.
- D. Expand the web server fileet with Spot Instances to provide the resources to handle the image
Answer: C
NEW QUESTION 4
Can a 'user' be associated with multiple AWS accounts?
- A. No
- B. Yes
Answer: A
NEW QUESTION 5
_____ is a fast, reliable, scalable, fully managed message queuing service.
- A. AWS Data Pipeline
- B. Amazon SES
- C. Amazon SQS
- D. Amazon SNS
Answer: C
Explanation:
Amazon Simple Queue Service (SQS) is a fast, reliable, scalable, fully managed message queuing service. SQS makes it simple and cost-effective to decouple the components of a cloud application. Decoupling the components of an application? You have a queue of work items and want to track the successful completion of each item independently. Amazon SQS tracks the ACK/FAIL results, so the application does not have to maintain a persistent checkpoint or cursor. After a configured visibility timeout, Amazon SQS deletes acknowledged messages and redelivers failed messages.
Configuring individual message delay? You have a job queue and you need to schedule individual jobs with a delay. With standard queues, you can configure individual messages to have a delay of up to 15 minutes.
Dynamically increasing concurrency or throughput at read time? You have a work queue and want to add more consumers until the backlog is cleared. Amazon SQS requires no pre-provisioning.
Scaling transparently? Your buffer requests and the load changes as a result of occasional load spikes or the natural growth of your business. Because Amazon SQS can process each buffered request independently, Amazon SQS can scale transparently to handle the load without any provisioning instructions from you.
http://aws.amazon.com/sqs/
NEW QUESTION 6
Which of the following does Amazon S3 provide?
- A. A virtual server in the cloud
- B. A highly-scalable cloud storage
- C. A highly encrypted virtual disk in the cloud
- D. A transient storage in the cloud
Answer: B
Explanation:
Amazon S3 provides Scalable Storage in the Cloud. Amazon Simple Storage Service (Amazon S3) is object storage with a simple web service interface to store and retrieve any amount of data from anywhere on the web. It is designed to deliver 99.999999999% durability, and scale past trillions of objects worldwide.
https://aws.amazon.com/s3/
NEW QUESTION 7
If I modify a DB Instance or the DB parameter group associated with the instance, should I reboot the instance for the changes to take effect?
- A. No
- B. Yes
Answer: B
NEW QUESTION 8
You have a Cassandra cluster running in private subnets in an Amazon VPC. A new application in a different Amazon VPC needs access to the database.
How can the new application access the database?
- A. Set up a dual-homed instance with ENIs in both Amazon VPCs.
- B. Set up a VPC peering connection between the two Amazon VPCs.
- C. Set up a NAT Gateway in the database’s Amazon VPC.
- D. Set up a NAT Gateway in the application’s Amazon VPC.
Answer: C
NEW QUESTION 9
What does a "Domain" refer to in Amazon SWF?
- A. A security group in which only tasks inside can communicate with each other
- B. A special type of worker
- C. A collection of related Workflows
- D. The DNS record for the Amazon SWF service
Answer: C
Explanation:
Domains provide a way of scoping Amazon SWF resources within your AWS account. All the components of a workflow, such as the workflow type and activity types, must be specified to be in a domain. It is possible to have more than one workflow in a domain; however, workflows in different domains cannot interact with each other. http://docs.aws.amazon.com/amazonswf/latest/developerguide/swf-dev-domain.html
NEW QUESTION 10
You have multiple VPN connections and want to provide secure communication between sites using the AWS VPN CloudHub. Which statement is the most accurate in describing what you must do to set this up correctly?
- A. Create a virtual private gateway with multiple customer gateways, each with unique Border Gateway Protocol (BGP) Autonomous System Numbers (ASNs)
- B. Create a virtual private gateway with multiple customer gateways, each with a unique set of keys
- C. Create a virtual public gateway with multiple customer gateways, each with a unique Private subnet
- D. Create a virtual private gateway with multiple customer gateways, each with unique subnet id
Answer: A
Explanation:
If you have multiple VPN connections, you can provide secure communication between sites using
the AWS VPN CloudHub. The VPN CloudHub operates on a simple hub-and-spoke model that you can use with or without a VPC. This design is suitable for customers with multiple branch offices and existing Internet connections who'd like to implement a convenient, potentially low-cost hub-andspoke model for primary or backup connectivity between these remote offices. To use the AWS VPN CloudHub, you must create a virtual private gateway with multiple customer gateways, each with unique Border Gateway Protocol (BGP) Autonomous System Numbers (ASNs). Customer gateways advertise the appropriate routes (BGP prefixes) over their VPN connections. These routing advertisements are received and re-advertised to each BGP peer, enabling each site to send data to and receive data from the other sites. The routes for each spoke must have unique ASNs and the sites must not have overlapping IP ranges. Each site can also send and receive data from the VPC as if they were using a standard VPN connection.
NEW QUESTION 11
A Solutions Architect is about to deploy an API on multiple EC2 instances in an Auto Scaling group behind an ELB. The support team has the following operational requirements:
1 They get an alert when the requests per second go over 50,000 2 They get an alert when latency goes over 5 seconds
3 They can validate how many times a day users call the API requesting highly-sensitive data Which combination of steps does the Architect need to take to satisfy these operational requirements? (Select two.)
- A. Ensure that CloudTrail is enabled.
- B. Create a custom CloudWatch metric to monitor the API for data access.
- C. Configure CloudWatch alarms for any metrics the support team requires.
- D. Ensure that detailed monitoring for the EC2 instances is enabled.
- E. Create an application to export and save CloudWatch metrics for longer term trending analysi
Answer: BD
NEW QUESTION 12
Your company is getting ready to do a major public announcement of a social media site on AWS. The website is running on EC2 instances deployed across multiple Availability Zones with a Multi-AZ RDS MySQL Extra Large DB Instance. The site performs a high number of small reads and writes per second and relies on an eventual consistency model. After comprehensive tests you discover that
there is read contention on RDS MySQL. Which are the best approaches to meet these requirements? (Choose two.)
- A. Deploy ElasticCache in-memory cache running in each availability zone
- B. Implement sharding to distribute load to multiple RDS MySQL instances
- C. Increase the RDS MySQL Instance size and Implement provisioned IOPS
- D. Add an RDS MySQL read replica in each availability zone
Answer: AD
NEW QUESTION 13
A Solutions Architect is designing solution with AWS Lambda where different environments require different database passwords.
What should the Architect do to accomplish this in a secure and scalable way?
- A. Create a Lambda function for each individual environment.
- B. Use Amazon DynamoDB to store environmental variables.
- C. Use encrypted AWS Lambda environmental variables.
- D. Implement a dedicated Lambda function for distributing variable
Answer: C
NEW QUESTION 14
A root AWS account owner has created three IAM users: Bob, John and Michael. Michael is the IAM administrator. Bob and John are not the super users, but users with some pre-defined policies. John does not have access to modify his password. Thus, he asks Bob to change his password. How can Bob change John's password?
- A. This statement is fals
- B. Only Michael can change the password for John
- C. This is possible if Michael can add Bob to a group which has permissions to modify the IAM passwords
- D. It is not possible for John to modify his password
- E. Provided Bob is the manager of John
Answer: B
Explanation:
Generally, with IAM users, the password can be modified in two ways. The first option is to define the IAM level policy which allows each user to modify their own passwords. The other option is to create a group and create a policy for the group which can change the passwords of various IAM users. http://docs.aws.amazon.com/IAM/latest/UserGuide/HowToPwdIAMUser.html
NEW QUESTION 15
An EC2 instance has one additional EBS volume attached to it. How can a user attach the same volume to another running instance in the same AZ?
- A. Detach the volume first and attach to new instance
- B. Attach the volume as read only to the second instance
- C. Terminate the first instance and only then attach to the new instance
- D. No need to detac
- E. Just select the volume and attach it to the new instance, it will take care of mapping internally
Answer: A
Explanation:
If an EBS volume is attached to a running EC2 instance, the user needs to detach the volume from the original instance and then attach it to a new running instance.
The user doesn't need to stop / terminate the original instance. http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ebs-detaching-volume.html
NEW QUESTION 16
A customer owns a simple API for their website that receives about 1,000 requests each day and has an average response time of 50 ms. It is currently hosted on one c4 large instance.
Which changes to the architecture will provide high availability at the LOWEST cost?
- A. Create an Auto Scaling group with a minimum of one instance and a maximum of two instances, then use an Application Load Balancer to balance the traffic.
- B. Recreate the API using Amazon API Gateway and use AWS Lambda as the service backend.
- C. Create an Auto Scaling group with a maximum of two instances, then use an Application Load Balancer to balance the traffic.
- D. Recreate the API using Amazon API Gateway and integrate the new API with the existing backend service.
Answer: A
NEW QUESTION 17
Amazon S3 provides;
- A. Unlimited File Size for Objects
- B. Unlimited Storage
- C. A great place to run a No SQL database from
- D. The ability to act as a web server for dynamic content (i.
- E. can query a database)
Answer: B
NEW QUESTION 18
What is Oracle SQL Developer?
- A. An AWS developer who is an expert in Amazon RDS using both the Oracle and SQL Server DB engines
- B. A graphical Java tool distributed without cost by Oracle.
- C. It is a variant of the SQL Server Management Studio designed by Microsoft to support Oracle DBMS functionalities
- D. A different DBMS released by Microsoft free of cost
Answer: B
Explanation:
http://www.oracle.com/technetwork/developer-tools/sql-developer/what-is-sqldev-093866.html
NEW QUESTION 19
Can the string value of 'Key' be prefixed with: aws:"?
- A. Only in GovCloud
- B. Only for S3 not EC2
- C. Yes
- D. No
Answer: D
Explanation:
"The tag key is the required name of the tag. The string value can be from 1 to 128 Unicode characters in length and cannot be prefixed with "aws:" or "rds:"." http://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/USER_Tagging.html http://docs.aws.amazon.com/cli/latest/reference/rds/list-tags-for-resource.html
NEW QUESTION 20
Which DNS name can only be resolved within Amazon EC2?
- A. Internal DNS name
- B. External DNS name
- C. Global DNS name
- D. Private DNS name
Answer: D
Explanation:
To view DNS hostnames for an instance using the console
1. Open the Amazon EC2 console at https://console.aws.amazon.com/ec2/.
2. In the navigation pane, choose Instances.
3. Select your instance from the list.
4. In the details pane, the Public DNS (IPv4) and Private DNS fields display the DNS hostnames, if applicable.
NEW QUESTION 21
In the context of AWS Security Best Practices for RDS, if you require encryption or data integrity authentication of data at rest for compliance or other purposes, you can add protection at the _____ using SQL cryptographic functions.
- A. physical layer
- B. security layer
- C. application layer
- D. data-link layer
Answer: C
Explanation:
Amazon RDS leverages the same secure infrastructure as Amazon EC2. You can use the Amazon RDS service without additional protection, but if you require encryption or data integrity authentication
of data at rest for compliance or other purposes, you can add protection at the application layer, or at the platform layer using SQL cryptographic functions.
https://d0.awsstatic.com/whitepapers/aws-security-best-practices.pdf
NEW QUESTION 22
Your company has multiple IT departments, each with their own VPC. Some VPCs are located within the same AWS account, and others in a different AWS account. You want to peer together all VPCs to enable the IT departments to have full access to each other’s' resources. There are certain limitations placed on VPC peering. Which of the following statements is incorrect in relation to VPC peering?
- A. Private DNS values cannot be resolved between instances in peered VPCs.
- B. You can have up to 3 VPC peering connections between the same two VPCs at the same time.
- C. You cannot create a VPC peering connection between VPCs in different regions.
- D. You have a limit on the number active and pending VPC peering connections that you can have per VPC.
Answer: B
Explanation:
To create a VPC peering connection with another VPC, you need to be aware of the following limitations and rules:
You cannot create a VPC peering connection between VPCs that have matching or overlapping CIDR blocks.
You cannot create a VPC peering connection between VPCs in different regions. You have a limit on the number active and pending VPC peering connections that you can have per VPC. VPC peering does not support transitive peering relationships; in a VPC peering connection, your VPC will not have access to any other VPCs that the peer VPC may be peered with. This includes VPC peering connections that are established entirely within your own AWS account. You cannot have more than one VPC peering connection between the same two VPCs at the same time. The Maximum
Transmission Unit (MTU) across a VPC peering connection is 1500 bytes. A placement group can span peered VPCs; however, you will not get full-bisection bandwidth between instances in peered VPCs. Unicast reverse path forwarding in VPC peering connections is not supported. You cannot reference a security group from the peer VPC as a source or destination for ingress or egress rules in your
security group. Instead, reference CIDR blocks of the peer VPC as the source or destination of your security group's ingress or egress rules.
Private DNS values cannot be resolved between instances in peered VPCs. References:
NEW QUESTION 23
Your application provides data transformation services. Files containing data to be transformed are first uploaded to Amazon S3 and then transformed by a fileet of spot EC2 instances. Files submitted by your premium customers must be transformed with the highest priority. How should you implement such a system?
- A. Use a DynamoDB table with an attribute defining the priority leve
- B. Transformation instances will scan the table for tasks, sorting the results by priority level.
- C. Use Route 53 latency based-routing to send high priority tasks to the closest transformation instances.
- D. Use two SQS queues, one for high priority messages, the other for default priorit
- E. Transformation instances first poll the high priority queue; if there is no message, they poll the default priorityqueue.
- F. Use a single SQS queu
- G. Each message contains the priority leve
- H. Transformation instances poll high-priority messages first.
Answer: C
NEW QUESTION 24
A popular e-commerce application runs on AWS. The application encounters performance issues. The database is unable to handle the amount of queries and load during peak times. The database is running on the RDS Aurora engine on the largest instance size available.
What should an administrator do to improve performance?
- A. Convert the database to Amazon Redshift.
- B. Create a CloudFront distribution.
- C. Convert the database to use EBS Provisioned IOPS.
- D. Create one or more read replica
Answer: C
NEW QUESTION 25
Which of the following statements is true of Amazon EC2 security groups?
- A. You can change the outbound rules for EC2-Classi
- B. Also, you can add and remove rules to a group at any time.
- C. You can modify an existing rule in a grou
- D. However, you can't add and remove rules to a group.
- E. None of the statements are correct.
- F. You can't change the outbound rules for EC2-Classi
- G. However, you can add and remove rules to a group at any time.
Answer: D
Explanation:
When dealing with security groups, bear in mind that you can freely add and remove rules from a group, but you can't change the outbound rules for EC2-Classic. If you're using the Amazon EC2 console, you can modify existing rules, and you can copy the rules from an existing security group to a new security group.
NEW QUESTION 26
You are a solutions architect working for a large digital media company. Your company is migrating their production estate to AWS and you are in the process of setting up access to the AWS console using Identity Access Management (IAM). You have created 5 users for your system administrators. What further steps do you need to take to enable your system administrators to get access to the AWS console?
- A. Generate an Access Key ID & Secret Access Key, and give these to your system administrators.
- B. Enable multi-factor authentication on their accounts and define a password policy.
- C. Generate a password for each user created and give these passwords to your systemadministrators.
- D. Give the system administrators the secret access key and access key id, and tell them to use these credentials to log in to the AWS console.
Answer: C
NEW QUESTION 27
Can you change the security groups associated with the primary network interface (eth0) of an EC2 instance running inside a VPC?
- A. Yes
- B. Only if the instance is stopped
- C. Only when the instance is launched
- D. No
Answer: A
Explanation:
After you launch an instance in a VPC, you can change its security groups. Security groups are associated with network interfaces. Changing an instance's security groups changes the security groups associated with the primary network interface (eth0).
http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/using-network-security.html#vpc-securitygroups
NEW QUESTION 28
A Solutions Architect is designing a new application that needs to access data in a different AWS account located within the same region. The data must not be accessed over the Internet.
Which solution will meet these requirements with the LOWEST cost?
- A. Add rules to the security groups in each account.
- B. Establish a VPC Peering connection between accounts.
- C. Configure Direct Connect in each account.
- D. Add a NAT Gateway to the data accoun
Answer: B
NEW QUESTION 29
You are setting up a VPC and you need to set up a public subnet within that VPC. Which following requirement must be met for this subnet to be considered a public subnet?
- A. Subnet's traffic is not routed to an internet gateway but has its traffic routed to a virtual private gateway.
- B. Subnet's traffic is routed to an internet gateway.
- C. Subnet's traffic is not routed to an internet gateway.
- D. None of these answers can be considered a public subne
Answer: B
Explanation:
A virtual private cloud (VPC) is a virtual network dedicated to your AWS account. It is logically isolated from other virtual networks in the AWS cloud. You can launch your AWS resources, such as Amazon EC2 instances, into your VPC. You can configure your VPC: you can select its IP address range, create subnets, and configure route tables, network gateways, and security settings. A subnet is a range of IP addresses in your VPC. You can launch AWS resources into a subnet that you select. Use a public subnet for resources that must be connected to the Internet, and a private subnet for resources that won't be connected to the Internet.
If a subnet's traffic is routed to an internet gateway, the subnet is known as a public subnet. If a subnet doesn't have a route to the internet gateway, the subnet is known as a private subnet. If a subnet doesn't have a route to the internet gateway, but has its traffic routed to a virtual private gateway, the subnet is known as a VPN-only subnet.
NEW QUESTION 30
......
P.S. prep-labs.com now are offering 100% pass ensure SAA-C01 dumps! All SAA-C01 exam questions have been updated with correct answers: https://www.prep-labs.com/dumps/SAA-C01/ (288 New Questions)
