Ucertify 156-915.77 Questions are updated and all 156-915.77 answers are verified by experts. Once you have completely prepared with our 156-915.77 exam prep kits you will be ready for the real 156-915.77 exam without a problem. We have Latest CheckPoint 156-915.77 dumps study guide. PASSED 156-915.77 First attempt! Here What I Did.
Check 156-915.77 free dumps before getting the full version:
NEW QUESTION 1
Your main internal network 10.10.10.0/24 allows all traffic to the Internet using Hide NAT. You also have a small network 10.10.20.0/24 behind the internal router. You want to configure the kernel to translate the source address only when network 10.10.20.0 tries to access the Internet for HTTP, SMTP, and FTP services. Which of the following configurations will allow this network to access the Internet?
- A. Configure three Manual Static NAT rules for network 10.10.20.0/24, one for each service.
- B. Configure Automatic Static NAT on network 10.10.20.0/24.
- C. Configure one Manual Hide NAT rule for HTTP, FTP, and SMTP services for network 10.10.20.0/24.
- D. Configure Automatic Hide NAT on network 10.10.20.0/24 and then edit the Service column in the NAT Rule Base on the automatic rule.
Answer: C
NEW QUESTION 2
To run GAiA in 64bit mode, which of the following is true?
1) Run set edition default 64-bit.
2) Install more than 4 GB RAM.
3) Install more than 4 TB of Hard Disk.
- A. 1 and 3
- B. 1 and 2
- C. 2 and 3
- D. 1, 2, and 3
Answer: B
NEW QUESTION 3
How are cached usernames and passwords cleared from the memory of a R77 Security Gateway?
- A. By using the Clear User Cache button in SmartDashboard.
- B. Usernames and passwords only clear from memory after they time out.
- C. By retrieving LDAP user information using the command fw fetchldap.
- D. By installing a Security Policy.
Answer: D
NEW QUESTION 4
CORRECT TEXT
Type the command and syntax to view critical devices on a cluster member in a ClusterXL environment.
Solution:
cphaprob -ia list
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 5
Which of the following authentication methods can be configured in the Identity Awareness setup wizard?
- A. Check Point Password
- B. TACACS
- C. LDAP
- D. Windows password
Answer: C
NEW QUESTION 6
You are trying to configure Directional VPN Rule Match in the Rule Base. But the Match column does not have the option to see the Directional Match. You see the following window.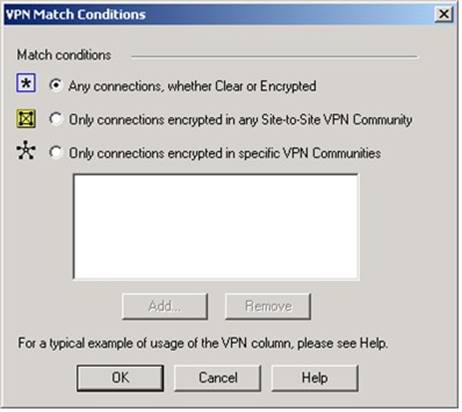
What must you enable to see the Directional Match?
- A. directional_match(true) in the objects_5_0.C file on Security Management Server
- B. VPN Directional Match on the Gateway object’s VPN tab
- C. VPN Directional Match on the VPN advanced window, in Global Properties
- D. Advanced Routing on each Security Gateway
Answer: C
NEW QUESTION 7
How granular may an administrator filter an Access Role with identity awareness? Per:
- A. Specific ICA Certificate
- B. AD User
- C. Radius Group
- D. Windows Domain
Answer: B
NEW QUESTION 8
What command with appropriate switches would you use to test Identity Awareness connectivity?
- A. test_ldap
- B. test_ad_connectivity
- C. test_ldap_connectivity
- D. test_ad
Answer: B
NEW QUESTION 9
Which Check Point address translation method allows an administrator to use fewer ISP- assigned IP addresses than the number of internal hosts requiring Internet connectivity?
- A. Hide
- B. Static Destination
- C. Static Source
- D. Dynamic Destination
Answer: A
NEW QUESTION 10
What happens if the identity of a user is known?
- A. If the user credentials do not match an Access Role, the traffic is automatically dropped.
- B. If the user credentials do not match an Access Role, the system displays a sandbox.
- C. If the user credentials do not match an Access Role, the gateway moves onto the next rule.
- D. If the user credentials do not match an Access Role, the system displays the Captive Portal.
Answer: C
NEW QUESTION 11
Several Security Policies can be used for different installation targets. The Firewall protecting Human Resources’ servers should have its own Policy Package. These rules must be installed on this machine and not on the Internet Firewall. How can this be accomplished?
- A. A Rule Base is always installed on all possible target
- B. The rules to be installed on a Firewall are defined by the selection in the Rule Base row Install On.
- C. When selecting the correct Firewall in each line of the Rule Base row Install On, only this Firewall is shown in the list of possible installation targets after selecting Policy > Install on Target.
- D. In the menu of SmartDashboard, go to Policy > Policy Installation Targets and select the correct firewall via Specific Targets.
- E. A Rule Base can always be installed on any Check Point Firewall objec
- F. It is necessary to select the appropriate target directly after selecting Policy > Install on Target.
Answer: C
NEW QUESTION 12
You just installed a new Web server in the DMZ that must be reachable from the Internet. You create a manual Static NAT rule as follows:
Source: Any || Destination: web_public_IP || Service: Any || Translated Source: original ||
Translated Destination: web_private_IP || Service: Original
“web_public_IP” is the node object that represents the new Web server’s public IP address. “web_private_IP” is the node object that represents the new Web site’s private IP address. You enable all settings from Global Properties > NAT.
When you try to browse the Web server from the Internet you see the error “page cannot be displayed”. Which of the following is NOT a possible reason?
- A. There is no Security Policy defined that allows HTTP traffic to the protected Web server.
- B. There is no ARP table entry for the protected Web server’s public IP address.
- C. There is no route defined on the Security Gateway for the public IP address to the Web server’s private IP address.
- D. There is no NAT rule translating the source IP address of packets coming from the protected Web server.
Answer: D
NEW QUESTION 13
Which of the following statements accurately describes the command snapshot?
- A. snapshot creates a full OS-level backup, including network-interface data, Check Point product information, and configuration settings during an upgrade of a GAiA Security Gateway.
- B. snapshot creates a Security Management Server full system-level backup on any OS.
- C. snapshot stores only the system-configuration settings on the Gateway.
- D. A Gateway snapshot includes configuration settings and Check Point product information from the remote Security Management Server.
Answer: A
NEW QUESTION 14
An internal host initiates a session to the Google.com website and is set for Hide NAT behind the Security Gateway. The initiating traffic is an example of .
- A. client side NAT
- B. source NAT
- C. destination NAT
- D. None of these
Answer: B
NEW QUESTION 15
MicroCorp experienced a security appliance failure. (LEDs of all NICs are off.) The age of the unit required that the RMA-unit be a different model. Will a revert to an existing snapshot bring the new unit up and running?
- A. There is no dynamic update at reboot.
- B. N
- C. The revert will most probably not match to hard disk.
- D. Ye
- E. Everything is dynamically updated at reboot.
- F. N
- G. At installation the necessary hardware support is selecte
- H. The snapshot saves this state.
Answer: D
NEW QUESTION 16
Which of the following allows administrators to allow or deny traffic to or from a specific network based on the user’s credentials?
- A. Access Policy
- B. Access Role
- C. Access Rule
- D. Access Certificate
Answer: B
NEW QUESTION 17
When migrating the SmartEvent data base from one server to another, the last step is to save the files on the new server. Which of the following commands should you run to save the SmartEvent data base files on the new server?
- A. cp
- B. restore
- C. migrate import
- D. eva_db_restore
Answer: D
NEW QUESTION 18
When do modifications to the Event Policy take effect?
- A. As soon as the Policy Tab window is closed.
- B. When saved on the SmartEvent Server and installed to the Correlation Units.
- C. When saved on the Correlation Units, and pushed as a policy.
- D. When saved on the SmartEvent Client, and installed on the SmartEvent Server.
Answer: B
NEW QUESTION 19
......
P.S. Dumps-hub.com now are offering 100% pass ensure 156-915.77 dumps! All 156-915.77 exam questions have been updated with correct answers: https://www.dumps-hub.com/156-915.77-dumps.html (203 New Questions)
