we provide Virtual Cisco 210-255 free draindumps which are the best for clearing 210-255 test, and to get certified by Cisco Implementing Cisco Cybersecurity Operations. The 210-255 Questions & Answers covers all the knowledge points of the real 210-255 exam. Crack your Cisco 210-255 Exam with latest dumps, guaranteed!
Online 210-255 free questions and answers of New Version:
NEW QUESTION 1
Refer to the exhibit.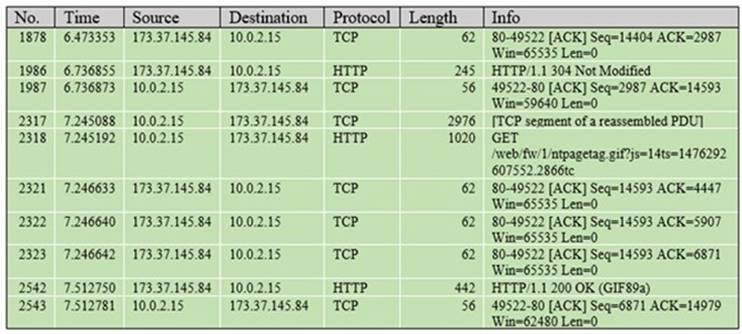
Which packet contains a file that is extractable within Wireshark?
- A. 1986
- B. 2318
- C. 2542
- D. 2317
Answer: C
NEW QUESTION 2
Employees are allowed access to internal websites. An employee connects to an internal website and IDS reports it as malicious behavior. What is this example of?
- A. true positive
- B. false negative
- C. false positive
- D. true negative
Answer: C
NEW QUESTION 3
Which option is the common artifact used to uniquely identify a detected file?
- A. file size
- B. file extension
- C. file timestamp
- D. file hash
Answer: D
NEW QUESTION 4
Refer to the exhibit.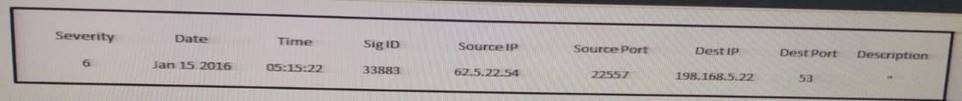
Which type of log is this an example of?
- A. IDS log
- B. proxy log
- C. NetFlow log
- D. syslog
Answer: C
NEW QUESTION 5
Which file system has 32 bits assigned to the address clusters of the allocation table?
- A. FAT32
- B. NTFS
- C. EXT4
- D. FAT16
Answer: A
NEW QUESTION 6
What mechanism does the Linux operating system provide to control access to files?
- A. privileges required
- B. user interaction
- C. file permissions
- D. access complexity
Answer: C
NEW QUESTION 7
Which process is being utilized when IPS events are removed to improve data integrity?
- A. data normalization
- B. data availability
- C. data protection
- D. data signature
Answer: A
Explanation:
Data normalization is the process of intercepting and storing incoming data so it exists in one form only. This eliminates redundant data and protects the data’s integrity.
Link: https://www.helpnetsecurity.com/2013/01/07/the-importance-of-data-normalization-in-ips/
NEW QUESTION 8
Which of the following is not an example of weaponization?
- A. Connecting to a CnC server
- B. Wrapping software with a RAT
- C. Creating a backdoor in an application
- D. Developing an automated script to inject commands on a USB device
Answer: A
NEW QUESTION 9
In addition to cybercrime and attacks, evidence found on a system or network may be presented in a court of law to support accusations of crime or civil action, including which of the following?
- A. Fraud, money laundering, and theft
- B. Drug-related crime
- C. Murder and acts of violence
- D. All of the above
Answer: D
NEW QUESTION 10
Which of the following are examples of some of the responsibility of a corporate CSIRT and the policies it helps create? (Choose four)
- A. Scanning vendor customer network
- B. incident classification and handling
- C. Information classification and protection
- D. Information dissemination
- E. Record retentions and destruction
Answer: BCDE
NEW QUESTION 11
Which precursor example is true?
- A. Admin finds their password has been changed
- B. A log scan indicating a port scan against a host
- C. A network device configuration has been changed
Answer: B
NEW QUESTION 12
Which stakeholder group is responsible for containment, eradication, and recovery in incident handling?
- A. facilitators
- B. practitioners
- C. leaders and managers
- D. decision makers
Answer: C
NEW QUESTION 13
Refer to the exhibit.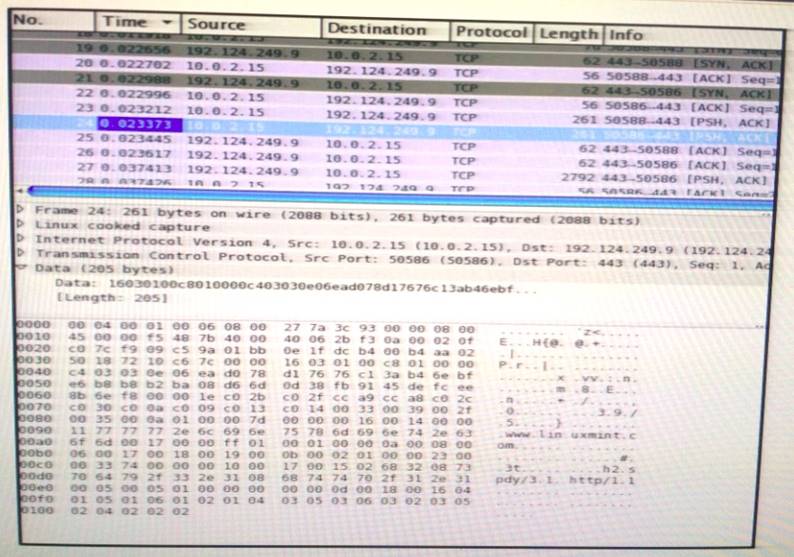
Which application protocol is in this PCAP file?
- A. TCP
- B. SSH
- C. HTTP
- D. SSL
Answer: D
Explanation:
If we are looking at the OSI model then SSL/TLS would sit at the presentation layer as it provides
encryption services, but SSL/TLS also establishes an encrypted communication session therefore SSL/TLS is also seen as part of session layer (layer 5 of the OSI model). It will also guarantee the authenticity of a Server by properly authenticating the required authentication challenges. Authentication works at Layer 7.If we are referring to the TCP/IP model, then it is entirely acceptable that SSL is seen as an application layer protocol as layers 5,6 & 7 of the OSI are mapped to the Application layer in TCP/IP model.TCP is not an application layer protocol – it is seen as the Transport layer protocol in both models.
NEW QUESTION 14
Choose the option that best describes NIST data integrity
- A. use only sha-1
- B. use only md5
- C. you must hash data & backup and compare hashes
- D. no need to hash data & backup and compare hashes
Answer: C
NEW QUESTION 15
Which statement about collecting data evidence when performing digital forensics is true?
- A. Allowing unrestricted access to impacted devices
- B. Not allowing items of evidence to be physically touch
- C. Powering off the device after collecting the data
- D. It must be preserved and integrity checked
Answer: D
NEW QUESTION 16
Which of the following has been used to evade IDS and IPS devices?
- A. SNMP
- B. HTTP
- C. TNP
- D. Fragmentation
Answer: D
NEW QUESTION 17
Which type of intrusion event is an attacker retrieving the robots. txt file from target site?
- A. exploitation
- B. weaponization
- C. scanning
- D. reconnaissance
Answer: D
NEW QUESTION 18
Which string matches the regular expression r(ege)+x?
- A. rx
- B. regeegex
- C. r(ege)x
- D. rege+x
Answer: B
NEW QUESTION 19
Which HTTP header field is usually used in forensics to identify the type of browser used?
- A. accept-language
- B. user-agent
- C. referrer
- D. host
Answer: B
NEW QUESTION 20
Which data type is protected under the PCI compliance framework?
- A. credit card type
- B. primary account number
- C. health conditions
- D. provision of individual care
Answer: B
Explanation:
From PCI security standards, PAN or Primary Account Number is the correct Answer https://www.pcisecuritystandards.org/documents/PCI%20SSC%20Quick%20Reference%20Guide.pdf
NEW QUESTION 21
......
P.S. Exambible now are offering 100% pass ensure 210-255 dumps! All 210-255 exam questions have been updated with correct answers: https://www.exambible.com/210-255-exam/ (160 New Questions)
