Ucertify offers free demo for 400-251 exam. "CCIE Security Written Exam", also known as 400-251 exam, is a Cisco Certification. This set of posts, Passing the Cisco 400-251 exam, will help you answer those questions. The 400-251 Questions & Answers covers all the knowledge points of the real exam. 100% real Cisco 400-251 exams and revised by experts!
Also have 400-251 free dumps questions for you:
NEW QUESTION 1
Refer to the exhibit.
R1(config)#parameter-map type inspect param-map R1(config-profile)#sessions maximum 10000 R1(config-profile)#
R1(config-profile)#class-map type inspect match-any class R1(config-cmap)#match protocol tcp
R1(config-cmap)#match protocol udp R1(config-cmap)#match protocol icmp R1(config-cmap)#match protocol ftp R1(config-cmap)#
R1(config-cmap)#policy-map type inspect policy R1(config-cmap)#class type inspect class R1(config-cmap-c)#inspect param-map R1(config-cmap-c)#
R1(config-cmap-c)#zone security z1 R1(config-sec-zone)#zone security z2 R1(config-sec-zone)#
R1(config-sec-zone)#zone-pair security zp source z1 destination z2 R1(config-sec-zone-pair)#service-policy type inspect policy
Which two statements about the given IPv6 ZBF configuration are true? (Choose two)
- A. It passes TCP, UDP, ICMP and FTP traffic on both directions between z1 and z2
- B. It provides backward compatibility with legacy IPv4 inspection
- C. It passes TCP, UDP, ICMP and FTP traffic from z1 and z2
- D. It inspects TCP, UDP, ICMP and FTP traffic from z2 and z1
- E. It provides backward compatibility with legacy IPv6 inspection
- F. It inspects TCP, UDP, ICMP and FTP traffic from z1 and z2
Answer: EF
NEW QUESTION 2
In a Cisco ASA multiple-context mode of operation configuration, what three session types are resourcelimited
by default when their context is a member of the default class? (Choose three.)
- A. SSL VPN sessions
- B. Telnet sessions
- C. TCP session
- D. IPSec sessions
- E. ASDM sessions
- F. SSH sessions
Answer: BDF
NEW QUESTION 3
Which statement is true regarding Private VLAN?
- A. A private VLAN domain can have multiple primary VLANs
- B. Each secondary VLAN in a private VLAN domain needs to have a separate associated primary VLAN
- C. Each port in a private VLAN domain is a member of all the secondary VLANs in the domain
- D. A subdomain in a primary VLAN domain consists of a primary and secondary VLAN pair
- E. In a private VLAN domain a secondary VLAN port needs to be an isolated port for it to be able to communicate with a layer-3 device
- F. In a private VLAN domain a secondary VLAN can have only one promiscuous port
Answer: F
NEW QUESTION 4
Which two characteristics of DTLS are true? (Choose two.)
- A. It supports long data transfers and connectionless data transfers.
- B. It includes a retransmission method because it uses an unreliable datagram transport.
- C. It includes a congestion control mechanism.
- D. It is used mostly by applications that use application layer object-security protocols.
- E. It completes key negotiation and bulk data transfer over a single channel.
- F. It cannot be used if NAT exists along the path.
Answer: BC
NEW QUESTION 5
Which of the following is the correct rule with regards to Zone-Based Firewall implementation?
- A. Interface can be a member of only one zone.
- B. All the interfaces of the device cannot be the part of the same zone.
- C. If interface belongs to a zone then the traffic to and from the interface is always allowed.
- D. By default traffic between the interfaces in the same zone is dropped.
- E. Zone pair cannot have a zone as both source and destination.
- F. If default zone is enabled then traffic from zone interface to non-zone interface will be dropped.
Answer: A
NEW QUESTION 6
Which effect of the crypto key encrypt write rsa command on a router is true?
- A. The device locks the encrypted key the saves it to the NVRAM
- B. The device saves the unlocked encrypted key to the NVRAM
- C. The device locks the encrypted key but the key is lost when the routers is reloaded
- D. The device encrypts and locks key before authenticating it with an external CA server
Answer: B
NEW QUESTION 7
Which definition of Machine Access Restriction is true?
- A. MAR offer security information and event management
- B. MAR provides detailed malware analysis reports
- C. MAR identifies threats on the cisco network by “learning” the topology, configuration and behavior you environment
- D. MAR is feature introduced into ISE and ACS as a way to verify a successful machine authenticated
- E. MAR provides user authentication
Answer: D
NEW QUESTION 8
Which option does a wired MAB appear in ISE RADIUS live logs?
- A. (Radius: Service-Type equals Framed) and (Radius: NAS-Port-Type equals Ethernet)
- B. (Radius: Service-Type equals Call–Check) and (Radius: NAS-Port-Type equals Ethernet)
- C. (Radius: Service-Type equals Call–Check) and (Radius: NAS-Port-Type equals PPPoEoVLAN)
- D. (Radius: Service-Type equals Call–Check) and (Radius: NAS-Port-Type equals PPPoEoVLAN)
Answer: C
NEW QUESTION 9
Refer to the exhibit.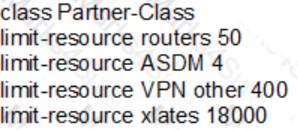
Which effect of this configuration is true?
- A. It allows each context to user all available resources.
- B. It oversubscribes VPN sessions for the given class.
- C. It creates a default class.
- D. It creates a resource class.
Answer: D
NEW QUESTION 10
Which encryption type is used by ESA for implementing the Email Encryption?
- A. PKI
- B. S/MIME Encryption
- C. Identity Based Encryption(IBE)
- D. TLS
- E. SSL Encryption
Answer: B
NEW QUESTION 11
Which two statements about the SeND protocol are true? (Choose two.)
- A. It counters neighbor discovery threats.
- B. It must be enabled before you can configure IPv6 addresses.
- C. It supports numerous custom neighbor discovery messages.
- D. It logs IPv6-related threats to an external log server.
- E. It supports an autoconfiguration mechanism.
- F. It uses IPsec as a baseline mechanism.
Answer: AE
NEW QUESTION 12
Which statement about SSL policy implementation in a Cisco Firepower system is true?
- A. Access control policy is required for the SSL policy implementation
- B. If the Cisco Firepower system cannot decrypt the traffic, it allows the connection.
- C. Access control policy is invoked first before the SSL policy tied to it
- D. Intrusion policy is mandatory to configure the SSL inspection
- E. If SSL policy is not supported by the system, then access control policy handles all the encrypted traffic.
- F. Access control policy is responsible to handle all the encrypted traffic if SSL policy is tried to it.
Answer: A
NEW QUESTION 13
Which three statements about SCEP are true? (Choose three.)
- A. It supports online certification revocation.
- B. Cryptographically signed and encrypted messages are conveyed using PKCS#7
- C. It supports multiple cryptographic algorithms including RSA.
- D. The certificate request format uses PKCS#10.
- E. CRL retrieval is supported through CDP(Certificate Distribution Point) queries.
- F. It supports synchronous granting.
Answer: BDE
Explanation:
Simple Certificate Enrollment Protocol
http://www.cisco.com/c/en/us/support/docs/security-vpn/public-key-infrastructure-pki/116167-technotescep-00.html
NEW QUESTION 14
Which three statements about VXLAN are true? (Choose three.)
- A. It can converge topology without STP.
- B. It enables up to 24 million VXLAN segments to coexist in the same administrative domain.
- C. It uses encrypted TCP/IP packets to transport data over the physical network.
- D. The VTEP encapsulates and de-encapsulates VXLAN traffic by adding or removing several fields, including a 16-bit VXLAN header.
- E. It uses a 24-bit VXLAN network identifier to provide layer 2 isolation between LAN segments.
- F. It can migrate a virtual machine from one Layer 2 domain to another over a Layer 3 network.
Answer: ADE
NEW QUESTION 15
Refer to the exhibit.
***Missing Exhibit***
AMP cloud is configured to report AMP connector scan events from windows machine
belonging to "Audit" group to FMC, but the scanned events are not showing up in FMC. What could be the possible cause?
- A. AMP cloud is pointing to incorrect FMC address
- B. Possible issues with certificate download form AMP cloud fro FMC integration
- C. Incorrect group is selected for the events export in AMP cloud for FMC
- D. Event should be viewed as "Malware" event in FMC
- E. DNS address is misconfigured on FMC
- F. FMC is pointing to incorrect AMP cloud address
Answer: D
NEW QUESTION 16
Which statement about EAP chaining is true?
- A. It supports RADIUS and TACACS+ authentication
- B. It performs authentication on a device-only basis
- C. It locks a unique certificate to BYOD devices to differentiate them from corporate-owned devices
- D. It requires EAP-FAST authentication
- E. By default devices on which EAP chaining is not supported are immediately denied access to the network
- F. It can be deployed in an agentless environment
Answer: D
NEW QUESTION 17
You are considering using RSPAN to capture traffic between several switches. Which two configuration aspects do you need to consider? (Choose two.)
- A. All switches need to be running the same IOS version.
- B. All distribution switches need to support RSPAN.
- C. Not all switches need to support RSPAN for it to work.
- D. The RSPAN VLAN need to be blocked on all trunk interfaces leading to the destination RSPAN switch.
- E. The RSPAN VLAN need to be allow on all trunk interfaces leading to the destination RSPAN switch.
Answer: BE
NEW QUESTION 18
Which three ESMTP extensions are supported by the Cisco ASA?Choose three
- A. NOOP
- B. PIPELINING
- C. SAML
- D. 8BITMIME
- E. STARTTLS
- F. ATRN
Answer: ACE
NEW QUESTION 19
Which statement is true regarding SSL policy implementation in a Firepower system?
- A. Access control policy is optional for the SSL policy implementation
- B. If Firepower system cannot decrypt the traffic, it allows the connection
- C. Intrusion policy is mandatory to configure the SSL inspection
- D. Access control policy is responsible to handle all the encrypted traffic if SSL policy is tied to it
- E. Access control policy is invoked first before the SSL policy tied to it
- F. IF SSL policy is not supported by the system, then access control policy handles all the encrypted traffic
Answer: E
NEW QUESTION 20
Which three options are fields in a CoA Request Response code packet? (Choose three.)
- A. Length
- B. Acct-session-ID
- C. Calling-station-ID
- D. Identifier
- E. Authenticator
- F. State
Answer: BCF
NEW QUESTION 21
Which of the following is true regarding failover link when ASAs are configured in the failover mode?
- A. It is not recommended to use secure communication over failover link when ASA is terminating the VPN tunnel
- B. Only the configuration replication sent across the link can be secured using a failover key
- C. The information sent over the failover link can only be in clear text
- D. The information sent over the failover link can be send in clear text, or it could be secured communication using a failover key
- E. Failover key is not required for the secure communication over the failover link
- F. The information sent over the failover link can only be sent as a secured communication
Answer: C
NEW QUESTION 22
Which three statement about SXP are true? (Choose three)
- A. It resides in the control plane, where connections can be initiated from a listener.
- B. Packets can be tagged with SGTs only with hardware support.
- C. Each VRF support only one CTS-SXP connection.
- D. To enable an access device to use IP device tracking to learn source device IP addresses, DHCP snooping must be configured.
- E. The SGA ZBFW uses the SGT to apply forwarding decisions.
- F. Separate VRFs require different CTS-SXP peers , but they can use the same source IP addresses.
Answer: BCE
NEW QUESTION 23
Which of the following is true regarding OSPFv2 configuring on ASA?
- A. It does not support stub area and not-so-stubby area
- B. ASA can exist as ABR but not as ASBR
- C. It supports virtual links
- D. It only supports MD5 authentication with the peers
- E. Routing decision is based on the hop counts to the destination
- F. It allows to configure only one routing process
Answer: C
NEW QUESTION 24
Which statement about Social Engineering attack is true?
- A. It is a method of extracting non-confidential information
- B. It can be done by a person who is inside or outside of the organization
- C. It is always done by having malicious ads on untrusted websites for the users to browse
- D. It is always performed through an email from a person that you know
- E. The phishing technique cannot be used to launch the attack
- F. It uses the reconnaissance method for exploitation
Answer: B
NEW QUESTION 25
Which two options are benefits of global ACLs? (Choose two)
- A. They save memory because they work without being replicated on each interface.
- B. They are more efficient because they are processed before interface access rules.
- C. They are flexible because they match source and destination IP addresses for packets that arrive on any interface.
- D. They only operate on logical interfaces.
- E. They can be applied to multiple interfaces.
Answer: AC
NEW QUESTION 26
Which two options are unicast address types for IPv6 addressing? (Choose two.)
- A. static
- B. link-local
- C. established
- D. dynamic
- E. global
Answer: BE
NEW QUESTION 27
Which two statements about Cisco ASA authentication using LDAP are true? (Choose two.)
- A. It is a closed standard that manages directory-information services over distributed networks.
- B. It can combine AD attributes and LDAP attributes to configure group policies on the Cisco ASA.
- C. It uses attribute maps to map the AD memberOf attribute to the Cisco ASAGroup-Policy attribute.
- D. It can assign a group policy to a user based on access credentials.
- E. It uses AD attribute maps to assign users to group policies configured under the WebVPN context.
- F. The Cisco ASA can use more than one AD memberOf attribute to match a user to multiple group policies.
Answer: CE
NEW QUESTION 28
An organization plans to upgrade its Internet-facing ASA running version 8.2 on an older HW platform to 5585/X version 9.6. The configuration was backed up and submitted for review before the migration takes
place. Which three changes must be made before the configuration is applied to the new ASA firewall?
(Choose three.)
- A. Static NAT statements are changed to xlate statements
- B. NAT control must be disabled so that traffic is allowed through the ASA
- C. Inbound ACLs must contain the pre-NAT IP instead the post-NAT IP
- D. NAT Control must be enabled so that traffic is allowed through the ASA
- E. Static NAT statements are changed to NAT statements
- F. Inbound ACLs must contain the post-NAT IP instead of the pre-NAT IP
Answer: ACD
NEW QUESTION 29
Which IETF standard is the most efficient messaging protocol used in a toT network?
- A. CoAP
- B. Man
- C. SNMP
- D. KTTP
Answer: A
NEW QUESTION 30
In which two ways does the Open DNS infrastructure ensure reliability? (Choose two)
- A. It ensures redundancy by using at least two telecom carters at each site
- B. it limits caching to reduce the Incidence of state and dead links
- C. ft uses a self-healing network to protect against individual failures
- D. Its networks are geographical^ integrated to reduce the potential impact of local issues.
- E. Regional sites load-balance among one another to prevent bottlenecks
- F. ft uses multicast routing to ensure that requests are routes to the nearest data center
- G. ft uses a specialized form of multicast addressing called Geo cast ensure the most efficient when a local site goes down
Answer: AG
NEW QUESTION 31
......
Thanks for reading the newest 400-251 exam dumps! We recommend you to try the PREMIUM Certstest 400-251 dumps in VCE and PDF here: https://www.certstest.com/dumps/400-251/ (448 Q&As Dumps)
