Refined of 312-50 exam answers materials and samples for EC-Council certification for IT examinee, Real Success Guaranteed with Updated 312-50 pdf dumps vce Materials. 100% PASS Ethical Hacking and Countermeasures (CEHv6) exam Today!
Online EC-Council 312-50 free dumps demo Below:
NEW QUESTION 1
What are the four steps is used by nmap scanning?
- A. DNS Lookup
- B. ICMP Message
- C. Ping
- D. Reverse DNS lookup
- E. TCP three way handshake
- F. The Actual nmap scan
Answer: ACDF
Explanation:
Nmap performs four steps during a normal device scan. Some of these steps can be modified or disabled using options on the nmap command line.
✑ If a hostname is used as a remote device specification, nmap will perform a DNS
lookup prior to the scan.
✑ Nmap pings the remote device. This refers to the nmap "ping" process, not (necessarily) a traditional ICMP echo request.
✑ If an IP address is specified as the remote device, nmap will perform a reverse DNS lookup in an effort to identify a name that might be associated with the IP address. This is the opposite process of what happens in step 1, where an IP address is found from a hostname specification.
✑ Nmap executes the scan. Once the scan is over, this four-step process is completed. Except for the actual scan process in step four, each of these steps can be disabled or prevented using different IP addressing or nmap options. The nmap process can be as "quiet" or as "loud" as necessary!
NEW QUESTION 2
Nathan is testing some of his network devices. Nathan is using Macof to try and flood the ARP cache of these switches. If these switches' ARP cache is successfully flooded, what will be the result?
- A. The switches will drop into hub mode if the ARP cache is successfully flooded.
- B. If the ARP cache is flooded, the switches will drop into pix mode making it less susceptible to attacks.
- C. Depending on the switch manufacturer, the device will either delete every entry in its ARP cache or reroute packets to the nearest switch.
- D. The switches will route all traffic to the broadcast address created collisions.
Answer: A
NEW QUESTION 3
Which type of hacker represents the highest risk to your network?
- A. script kiddies
- B. grey hat hackers
- C. black hat hackers
- D. disgruntled employees
Answer: D
Explanation:
The disgruntled users have some permission on your database, versus a hacker who might not get into the database. Global Crossings is a good example of how a disgruntled employee -- who took the internal payroll database home on a hard drive -- caused big problems for the telecommunications company. The employee posted the names, Social Security numbers and birthdates of company employees on his Web site. He may have been one of the factors that helped put them out of business.
NEW QUESTION 4
Blane is a network security analyst for his company. From an outside IP, Blane performs an XMAS scan using Nmap. Almost every port scanned does not illicit a response. What can he infer from this kind of response?
- A. These ports are open because they do not illicit a response.
- B. He can tell that these ports are in stealth mode.
- C. If a port does not respond to an XMAS scan using NMAP, that port is closed.
- D. The scan was not performed correctly using NMAP since all ports, no matter what their state, will illicit some sort of response from an XMAS scan.
Answer: A
NEW QUESTION 5
You find the following entries in your web log. Each shows attempted access to either root.exe or cmd.exe. What caused this?
GET /scripts/root.exe?/c+dir GET /MSADC/root.exe?/c+dir
GET /c/winnt/system32/cmd.exe?/c+dir GET /d/winnt/system32/cmd.exe?/c+dir
GET /scripts/..%5c../winnt/system32/cmd.exe?/c+dir
GET /_vti_bin/..%5c../..%5c../..%5c../winnt/system32/cmd.exe?/c+dir GET /_mem_bin/..%5c../..%5c../..%5c../winnt/system32/cmd.exe?/c+dir GET
/msadc/..%5c../..%5c../..%5c/..xc1x1c../..xc1x1c../..xc1x1c../winnt/system32/cmd.exe?/c+di r
GET /scripts/..xc1x1c../winnt/system32/cmd.exe?/c+dir GET /scripts/..xc0/../winnt/system32/cmd.exe?/c+dir GET /scripts/..xc0xaf../winnt/system32/cmd.exe?/c+dir GET /scripts/..xc1x9c../winnt/system32/cmd.exe?/c+dir GET /scripts/..%35c../winnt/system32/cmd.exe?/c+dir GET /scripts/..%35c../winnt/system32/cmd.exe?/c+dir GET /scripts/..%5c../winnt/system32/cmd.exe?/c+dir GET /scripts/..%2f../winnt/system32/cmd.exe?/c+dir
- A. The Morris worm
- B. The PIF virus
- C. Trinoo
- D. Nimda
- E. Code Red
- F. Ping of Death
Answer: D
Explanation:
The Nimda worm modifies all web content files it finds. As a result, any user browsing web content on the system, whether via the file system or via a web server, may download a copy of the worm. Some browsers may automatically execute the downloaded copy, thereby, infecting the browsing system. The high scanning rate of the Nimda worm may also cause bandwidth denial-of-service conditions on networks with infected machines and allow intruders the ability to execute arbitrary commands within the Local System security context on machines running the unpatched versions of IIS.
NEW QUESTION 6
In the following example, which of these is the "exploit"?
Today, Microsoft Corporation released a security notice. It detailed how a person could bring down the Windows 2003 Server operating system, by sending malformed packets to it. They detailed how this malicious process had been automated using basic scripting. Even worse, the new automated method for bringing down the server has already been used to perform denial of service attacks on many large commercial websites.
Select the best answer.
- A. Microsoft Corporation is the exploit.
- B. The security "hole" in the product is the exploit.
- C. Windows 2003 Server
- D. The exploit is the hacker that would use this vulnerability.
- E. The documented method of how to use the vulnerability to gain unprivileged access.
Answer: E
Explanation:
Explanations:
Microsoft is not the exploit, but if Microsoft documents how the vulnerability can be used to gain unprivileged access, they are creating the exploit. If they just say that there is a hole in the product, then it is only a vulnerability. The security "hole" in the product is called the "vulnerability". It is documented in a way that shows how to use the vulnerability to gain unprivileged access, and it then becomes an "exploit". In the example given, Windows 2003 Server is the TOE (Target of Evaluation). A TOE is an IT System, product or component that requires security evaluation or is being identified. The hacker that would use this vulnerability is exploiting it, but the hacker is not the exploit. The documented method of how to use the vulnerability to gain unprivileged access is the correct answer.
NEW QUESTION 7
Which of the following commands runs snort in packet logger mode?
- A. ./snort -dev -h ./log
- B. ./snort -dev -l ./log
- C. ./snort -dev -o ./log
- D. ./snort -dev -p ./log
Answer: B
Explanation:
Note: If you want to store the packages in binary mode for later analysis use
./snort -l ./log -b
NEW QUESTION 8
Wayne is the senior security analyst for his company. Wayne is examining some traffic logs on a server and came across some inconsistencies. Wayne finds some IP packets from a computer purporting to be on the internal network. The packets originate from
192.168.12.35 with a TTL of 15. The server replied to this computer and received a response from 192.168.12.35 with a TTL of 21. What can Wayne infer from this traffic log?
- A. The initial traffic from 192.168.12.35 was being spoofed.
- B. The traffic from 192.168.12.25 is from a Linux computer.
- C. The TTL of 21 means that the client computer is on wireless.
- D. The client computer at 192.168.12.35 is a zombie computer.
Answer: A
NEW QUESTION 9
What are the six types of social engineering?(Choose six).
- A. Spoofing
- B. Reciprocation
- C. Social Validation
- D. Commitment
- E. Friendship
- F. Scarcity
- G. Authority
- H. Accountability
Answer: BCDEFG
Explanation:
All social engineering is performed by taking advantage of human nature. For in-depth information on the subject review, read Robert Cialdini's book, Influence: Science and Practice.
NEW QUESTION 10
The FIN flag is set and sent from host A to host B when host A has no more data to transmit (Closing a TCP connection). This flag releases the connection resources. However, host A can continue to receive data as long as the SYN sequence number of transmitted packets from host B are lower than the packet segment containing the set FIN flag.
- A. True
- B. False
Answer: A
Explanation:
For sequence number purposes, the SYN is considered to occur before the first actual data octet of the segment in which it occurs, while the FIN is considered to occur after the last actual data octet in a segment in which it occurs. So packets receiving out of order will still be accepted.
NEW QUESTION 11
Data is sent over the network as clear text (unencrypted) when Basic Authentication is configured on Web Servers.
- A. True
- B. False
Answer: A
Explanation:
Using HTTP basic authentication will result in your password being sent over the internet as clear text. Don't use this technique unless you understand what the ramifications of this are.
NEW QUESTION 12
If a competitor wants to cause damage to your organization, steal critical secrets, or put you out of business, they just have to find a job opening, prepare someone to pass the interview, have that person hired, and they will be in the organization.
How would you prevent such type of attacks?
- A. It is impossible to block these attacks
- B. Hire the people through third-party job agencies who will vet them for you
- C. Conduct thorough background checks before you engage them
- D. Investigate their social networking profiles
Answer: C
NEW QUESTION 13
You are the IT Manager of a large legal firm in California. Your firm represents many important clients whose names always must remain anonymous to the public. Your boss, Mr. Smith is always concerned about client information being leaked or revealed to the pres or public. You have just finished a complete security overhaul of your information system including an updated IPS, new firewall, email encryption and employee security awareness training. Unfortunately, many of your firm’s clients do not trust technology to completely secure their information, so couriers routinely have to travel back and forth to and from the office with sensitive information.
Your boss has charged you with figuring out how to secure the information the couriers must transport. You propose that the data be transferred using burned CD’s or USB flash drives. You initially think of encrypting the files, but decide against that method for fear the encryption keys could eventually be broken.
What software application could you use to hide the data on the CD’s and USB flash drives?
- A. Snow
- B. File Snuff
- C. File Sneaker
- D. EFS
Answer: A
Explanation:
The Snow software developed by Matthew Kwan will insert extra spaces at the end of each line. Three bits are encoded in each line by adding between 0 and 7 spaces that are ignored by most display programs including web browsers.
NEW QUESTION 14
You are footprinting an organization to gather competitive intelligence. You visit the company’s website for contact information and telephone numbers but do not find it listed there. You know that they had the entire staff directory listed on their website 12 months ago but not it is not there.
How would it be possible for you to retrieve information from the website that is outdated?
- A. Visit google’s search engine and view the cached copy.
- B. Visit Archive.org web site to retrieve the Internet archive of the company’s website.
- C. Crawl the entire website and store them into your computer.
- D. Visit the company’s partners and customers website for this information.
Answer: B
Explanation:
Archive.org mirrors websites and categorizes them by date and month depending on the crawl time. Archive.org dates back to 1996, Google is incorrect because the cache is only as recent as the latest crawl, the cache is over-written on each subsequent crawl. Download the website is incorrect because that's the same as what you see online. Visiting customer partners websites is just bogus. The answer is then Firmly, C, archive.org
NEW QUESTION 15
TCP/IP Session Hijacking is carried out in which OSI layer?
- A. Transport layer
- B. Datalink layer
- C. Physical Layer
- D. Network Layer
Answer: A
NEW QUESTION 16
One of the better features of NetWare is the use of packet signature that includes cryptographic signatures. The packet signature mechanism has four levels from 0 to 3.
In the list below which of the choices represent the level that forces NetWare to sign all packets?
- A. 0 (zero)
- B. 1
- C. 2
- D. 3
Answer: D
Explanation:
0Server does not sign packets (regardless of the client level).
1Server signs packets if the client is capable of signing (client level is 2 or higher). 2Server signs packets if the client is capable of signing (client level is 1 or higher). 3Server signs packets and requires all clients to sign packets or logging in will fail.
NEW QUESTION 17
Which of the following ICMP message types are used for destinations unreachables?
- A. 3
- B. 11
- C. 13
- D. 17
Answer: B
Explanation:
Type 3 messages are used for unreachable messages. 0 is Echo Reply, 8 is Echo request, 11 is time exceeded, 13 is timestamp and 17 is subnet mask request. Learning these would be advisable for the test.
NEW QUESTION 18
Destination unreachable administratively prohibited messages can inform the hacker to what?
- A. That a circuit level proxy has been installed and is filtering traffic
- B. That his/her scans are being blocked by a honeypot or jail
- C. That the packets are being malformed by the scanning software
- D. That a router or other packet-filtering device is blocking traffic
- E. That the network is functioning normally
Answer: D
Explanation:
Destination unreachable administratively prohibited messages are a good way to discover that a router or other low-level packet device is filtering traffic. Analysis of the ICMP message will reveal the IP address of the blocking device and the filtered port. This further adds the to the network map and information being discovered about the network and hosts.
NEW QUESTION 19
Which of the following countermeasure can specifically protect against both the MAC Flood and MAC Spoofing attacks?
- A. Configure Port Security on the switch
- B. Configure Port Recon on the switch
- C. Configure Switch Mapping
- D. Configure Multiple Recognition on the switch
Answer: A
NEW QUESTION 20
Theresa is an IT security analyst working for the United Kingdom Internet Crimes Bureau in London. Theresa has been assigned to the software piracy division which focuses on taking down individual and organized groups that distribute copyrighted software illegally. Theresa and her division have been responsible for taking down over 2,000 FTP sites hosting copyrighted software. Theresa's supervisor now wants her to focus on finding and taking down websites that host illegal pirated software. What are these sights called that Theresa has been tasked with taking down?
- A. These sites that host illegal copyrighted software are called Warez sites
- B. These sites that Theresa has been tasked to take down are called uTorrent sites
- C. These websites are referred to as Dark Web sites
- D. Websites that host illegal pirated versions of software are called Back Door sites
Answer: A
Explanation:
The Warez scene, often referred to as The Scene (often capitalized) is a term of self- reference used by a community that specializes
in the underground distribution of pirated content, typically software but increasingly including movies and music.
NEW QUESTION 21
What is Cygwin?
- A. Cygwin is a free C++ compiler that runs on Windows
- B. Cygwin is a free Unix subsystem that runs on top of Windows
- C. Cygwin is a free Windows subsystem that runs on top of Linux
- D. Cygwin is a X Windows GUI subsytem that runs on top of Linux GNOME environment
Answer: B
Explanation:
Cygwin is a Linux-like environment for Windows. It consists of two parts:
A DLL (cygwin1.dll) which acts as a Linux API emulation layer providing substantial Linux API functionality.
A collection of tools which provide Linux look and feel.
The Cygwin DLL works with all non-beta, non "release candidate", ix86 32 bit versions of Windows since Windows 95, with the exception of Windows CE.
NEW QUESTION 22
Lori has just been tasked by her supervisor conduct vulnerability scan on the corporate network. She has been instructed to perform a very thorough test of the network to ensure that there are no security holes on any of the machines. Lori’s company does not own any commercial scanning products, so she decides to download a free one off the Internet. Lori has never done a vulnerability scan before, so she is unsure of some of the settings available in the software she downloaded. One of the option is to choose which ports that can be scanned. Lori wants to do exactly what her boos has told her, but she does not know ports should be scanned.
If Lori is supposed to scan all known TCP ports, how many ports should she select in the software?
- A. 65536
- B. 1024
- C. 1025
- D. Lori should not scan TCP ports, only UDP ports
Answer: A
Explanation:
In both TCP and UDP, each packet header will specify a source port and a destination port, each of which is a 16-bit unsigned integer (i.e. ranging from 0 to 65535).
NEW QUESTION 23
NSLookup is a good tool to use to gain additional information about a target network. What does the following command accomplish?
nslookup
> server <ipaddress>
> set type =any
> ls -d <target.com>
- A. Enables DNS spoofing
- B. Loads bogus entries into the DNS table
- C. Verifies zone security
- D. Performs a zone transfer
- E. Resets the DNS cache
Answer: D
Explanation:
If DNS has not been properly secured, the command sequence displayed above will perform a zone transfer.
NEW QUESTION 24
Which is the Novell Netware Packet signature level used to sign all packets ?
- A. 1
- B. 2
- C. 3
Answer: D
Explanation:
Level 0 is no signature, Level 3 is communication using signature only.
NEW QUESTION 25
In TCP communications there are 8 flags; FIN, SYN, RST, PSH, ACK, URG, ECE, CWR. These flags have decimal numbers assigned to them:
FIN = 1
SYN = 2
RST = 4
PSH = 8
ACK = 16
URG = 32
ECE = 64
CWR = 128
Jason is the security administrator of ASPEN Communications. He analyzes some traffic using Wireshark and has enabled the following filters.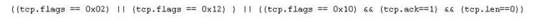
What is Jason trying to accomplish here?
- A. SYN, FIN, URG and PSH
- B. SYN, SYN/ACK, ACK
- C. RST, PSH/URG, FIN
- D. ACK, ACK, SYN, URG
Answer: B
NEW QUESTION 26
What type of attack is shown here?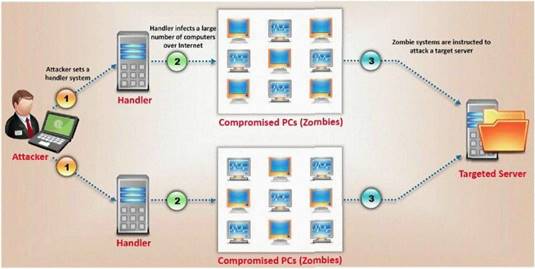
- A. Bandwidth exhaust Attack
- B. Denial of Service Attack
- C. Cluster Service Attack
- D. Distributed Denial of Service Attack
Answer: B
NEW QUESTION 27
Carl has successfully compromised a web server from behind a firewall by exploiting a vulnerability in the web server program. He wants to proceed by installing a backdoor program. However, he is aware that not all inbound ports on the firewall are in the open state.
From the list given below, identify the port that is most likely to be open and allowed to reach the server that Carl has just compromised.
- A. 53
- B. 110
- C. 25
- D. 69
Answer: A
Explanation:
Port 53 is used by DNS and is almost always open, the problem is often that the port is opened for the hole world and not only for outside DNS servers.
NEW QUESTION 28
A simple compiler technique used by programmers is to add a terminator 'canary word' containing four letters NULL (0x00), CR (0x0d), LF (0x0a) and EOF (0xff) so that most string operations are terminated. If the canary word has been altered when the function returns, and the program responds by emitting an intruder alert into syslog, and then halts what does it indicate?
- A. The system has crashed
- B. A buffer overflow attack has been attempted
- C. A buffer overflow attack has already occurred
- D. A firewall has been breached and this is logged
- E. An intrusion detection system has been triggered
Answer: B
Explanation:
Terminator Canaries are based on the observation that most buffer overflows and stack smash attacks are based on certain string operations which end at terminators. The reaction to this observation is that the canaries are built of NULL terminators, CR, LF, and -1. The undesirable result is that the canary is known.
NEW QUESTION 29
......
100% Valid and Newest Version 312-50 Questions & Answers shared by Allfreedumps.com, Get Full Dumps HERE: https://www.allfreedumps.com/312-50-dumps.html (New 765 Q&As)
