It is impossible to pass EC-Council ECSAv10 exam without any help in the short term. Come to Examcollection soon and find the most advanced, correct and guaranteed EC-Council ECSAv10 practice questions. You will get a surprising result by our Up to the minute EC-Council Certified Security Analyst (ECSA) v10 : Penetration Testing practice guides.
EC-Council ECSAv10 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Which of the following documents helps in creating a confidential relationship between the pen tester and client to protect critical and confidential information or trade secrets?
- A. Penetration Testing Agreement
- B. Rules of Behavior Agreement
- C. Liability Insurance
- D. Non-Disclosure Agreement
Answer: D
NEW QUESTION 2
In Linux, what is the smallest possible shellcode?
- A. 800 bytes
- B. 8 bytes
- C. 80 bytes
- D. 24 bytes
Answer: D
NEW QUESTION 3
A penetration test consists of three phases: pre-attack phase, attack phase, and post-attack phase.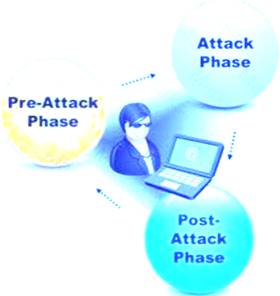
Active reconnaissance which includes activities such as network mapping, web profiling, and perimeter mapping is a part which phase(s)?
- A. Post-attack phase
- B. Pre-attack phase and attack phase
- C. Attack phase
- D. Pre-attack phase
Answer: D
NEW QUESTION 4
An external intrusion test and analysis identify security weaknesses and strengths of the client's systems and networks as they appear from outside the client's security perimeter, usually from the Internet.
The goal of an external intrusion test and analysis is to demonstrate the existence of known vulnerabilities that could be exploited by an external attacker.
During external penetration testing, which of the following scanning techniques allow you to determine a port’s state without making a full connection to the host?
- A. XMAS Scan
- B. SYN scan
- C. FIN Scan
- D. NULL Scan
Answer: B
NEW QUESTION 5
What does ICMP Type 3/Code 13 mean?
- A. Host Unreachable
- B. Port Unreachable
- C. Protocol Unreachable
- D. Administratively Blocked
Answer: D
NEW QUESTION 6
Kimberly is studying to be an IT security analyst at a vocational school in her town. The school offers
many different programming as well as networking languages. What networking protocol language should she learn that routers utilize?
- A. OSPF
- B. BPG
- C. ATM
- D. UDP
Answer: A
NEW QUESTION 7
ESTION NO: 92
In Linux, /etc/shadow file stores the real password in encrypted format for user’s account with added properties associated with the user’s password.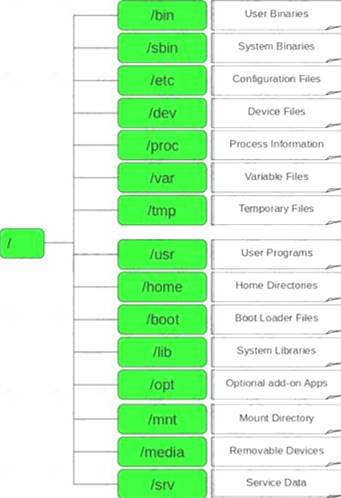
In the example of a /etc/shadow file below, what does the bold letter string indicate? Vivek: $1$fnffc$GteyHdicpGOfffXX40w#5:13064:0:99999:7
- A. Number of days the user is warned before the expiration date
- B. Minimum number of days required between password changes
- C. Maximum number of days the password is valid
- D. Last password changed
Answer: B
NEW QUESTION 8
Paulette works for an IT security consulting company that is currently performing an audit for the firm
ACE Unlimited. Paulette's duties include logging on to all the company's network equipment to ensure IOS versions are up-to-date and all the other security settings are as stringent as possible.
Paulette presents the following screenshot to her boss so he can inform the clients about necessary changes need to be made. From the screenshot, what changes should the client company make?
Exhibit:
- A. The banner should not state "only authorized IT personnel may proceed"
- B. Remove any identifying numbers, names, or version information
- C. The banner should include the Cisco tech support contact information as well
- D. The banner should have more detail on the version numbers for the network equipment
Answer: B
NEW QUESTION 9
In a virtual test environment, Michael is testing the strength and security of BGP using multiple routers to mimic the backbone of the Internet. This project will help him write his doctoral thesis on "bringing down the Internet".
Without sniffing the traffic between the routers, Michael sends millions of RESET packets to the routers in an attempt to shut one or all of them down. After a few hours, one of the routers finally shuts itself down.
What will the other routers communicate between themselves?
- A. More RESET packets to the affected router to get it to power back up
- B. RESTART packets to the affected router to get it to power back up
- C. The change in the routing fabric to bypass the affected router
- D. STOP packets to all other routers warning of where the attack originated
Answer: C
NEW QUESTION 10
Software firewalls work at which layer of the OSI model?
- A. Data Link
- B. Network
- C. Transport
- D. Application
Answer: A
NEW QUESTION 11
Transmission control protocol accepts data from a data stream, divides it into chunks, and adds a TCP header creating a TCP segment. The TCP header is the first 24 bytes of a TCP segment that contains the parameters and state of an end-to-end TCP socket. It is used to track the state of communication between two TCP endpoints.
For a connection to be established or initialized, the two hosts must synchronize. The synchronization requires each side to send its own initial sequence number and to receive a confirmation of exchange in an acknowledgment (ACK) from the other side
The below diagram shows the TCP Header format: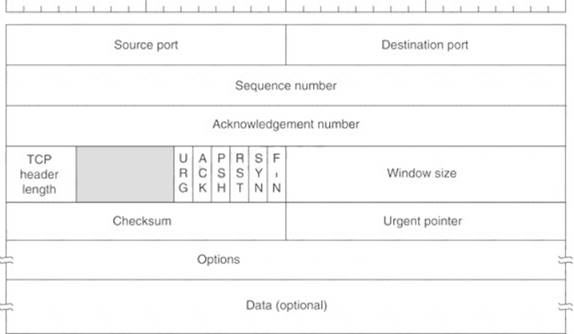
- A. 16 bits
- B. 32 bits
- C. 8 bits
- D. 24 bits
Answer: B
NEW QUESTION 12
The first and foremost step for a penetration test is information gathering. The main objective of this test is to gather information about the target system which can be used in a malicious manner to gain access to the target systems.
Which of the following information gathering terminologies refers to gathering information through social engineering on-site visits, face-to-face interviews, and direct questionnaires?
- A. Active Information Gathering
- B. Pseudonymous Information Gathering
- C. Anonymous Information Gathering
- D. Open Source or Passive Information Gathering
Answer: A
NEW QUESTION 13
What is the maximum value of a “tinyint” field in most database systems?
- A. 222
- B. 224 or more
- C. 240 or less
- D. 225 or more
Answer: D
NEW QUESTION 14
Rule of Engagement (ROE) is the formal permission to conduct a pen-test. It provides top-level guidance for conducting the penetration testing. Various factors are considered while preparing the scope of ROE which clearly explain the limits associated with the security test.
Which of the following factors is NOT considered while preparing the scope of the Rules of Engagment (ROE)?
- A. A list of employees in the client organization
- B. A list of acceptable testing techniques
- C. Specific IP addresses/ranges to be tested
- D. Points of contact for the penetration testing team
Answer: A
NEW QUESTION 15
Snort, an open source network-based intrusion detection sensor, is the most widely installed NIDS in the world. It can be configured to run in the four modes. Which one of the following modes reads the packets off the network and displays them in a continuous stream on the console (screen)?
- A. Packet Sniffer Mode
- B. Packet Logger Mode
- C. Network Intrusion Detection System Mode
- D. Inline Mode
Answer: A
NEW QUESTION 16
Which of the following policy forbids everything with strict restrictions on all usage of the company systems and network?
- A. Information-Protection Po
- B. Paranoid Policy
- C. Promiscuous Policy
- D. Prudent Policy
Answer: B
NEW QUESTION 17
Identify the type of testing that is carried out without giving any information to the employees or administrative head of the organization.
- A. Unannounced Testing
- B. Double Blind Testing
- C. Announced Testing
- D. Blind Testing
Answer: B
NEW QUESTION 18
In which of the following firewalls are the incoming or outgoing packets blocked from accessing services for which there is no proxy?
- A. Circuit level firewalls
- B. Packet filters firewalls
- C. Stateful multilayer inspection firewalls
- D. Application level firewalls
Answer: D
NEW QUESTION 19
Which one of the following is a command line tool used for capturing data from the live network and copying those packets to a file?
- A. Wireshark: Capinfos
- B. Wireshark: Tcpdump
- C. Wireshark: Text2pcap
- D. Wireshark: Dumpcap
Answer: D
NEW QUESTION 20
A pen tester has extracted a database name by using a blind SQL injection. Now he begins to test the table inside the database using the below query and finds the table:
http://juggyboy.com/page.aspx?id=1; IF (LEN(SELECT TOP 1 NAME from sysobjects where xtype='U')=3) WAITFOR DELAY '00:00:10'-
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),1,1)))=101) WAITFOR DELAY '00:00:10'-
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),2,1)))=109) WAITFOR DELAY '00:00:10'-
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),3,1)))=112) WAITFOR DELAY '00:00:10'—
What is the table name?
- A. CTS
- B. QRT
- C. EMP
- D. ABC
Answer: C
NEW QUESTION 21
Which one of the following log analysis tools is used for analyzing the server’s log files?
- A. Performance Analysis of Logs tool
- B. Network Sniffer Interface Test tool
- C. Ka Log Analyzer tool
- D. Event Log Tracker tool
Answer: C
NEW QUESTION 22
Metasploit framework in an open source platform for vulnerability research, development, and penetration testing. Which one of the following metasploit options is used to exploit multiple systems at once?
- A. NinjaDontKill
- B. NinjaHost
- C. RandomNops
- D. EnablePython
Answer: A
NEW QUESTION 23
Which of the following contents of a pen testing project plan addresses the strengths, weaknesses, opportunities, and threats involved in the project?
- A. Project Goal
- B. Success Factors
- C. Objectives
- D. Assumptions
Answer: D
NEW QUESTION 24
Identify the person who will lead the penetration-testing project and be the client point of contact.
- A. Database Penetration Tester
- B. Policy Penetration Tester
- C. Chief Penetration Tester
- D. Application Penetration Tester
Answer: C
NEW QUESTION 25
What operating system would respond to the following command?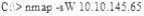
- A. Mac OS X
- B. Windows XP
- C. Windows 95
- D. FreeBSD
Answer: D
NEW QUESTION 26
A framework for security analysis is composed of a set of instructions, assumptions, and limitations to analyze and solve security concerns and develop threat free applications.
Which of the following frameworks helps an organization in the evaluation of the company’s information security with that of the industrial standards?
- A. Microsoft Internet Security Framework
- B. Information System Security Assessment Framework
- C. The IBM Security Framework
- D. Nortell’s Unified Security Framework
Answer: B
NEW QUESTION 27
Besides the policy implications of chat rooms, Internet Relay Chat (IRC) is frequented by attackers and used as a command and control mechanism. IRC normally uses which one of the following TCP ports?
- A. 6566 TCP port
- B. 6771 TCP port
- C. 6667 TCP port
- D. 6257 TCP port
Answer: C
NEW QUESTION 28
......
P.S. Easily pass ECSAv10 Exam with 201 Q&As Dumps-hub.com Dumps & pdf Version, Welcome to Download the Newest Dumps-hub.com ECSAv10 Dumps: https://www.dumps-hub.com/ECSAv10-dumps.html (201 New Questions)
